Chaos theory-based information label encryption method and system thereof
An information tag and chaos theory technology, applied in the field of information tag encryption method and its system based on chaos theory, can solve the problems of poor decryption and decreased decryption effect, and achieve simple design, good encryption effect and strong key sensitivity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
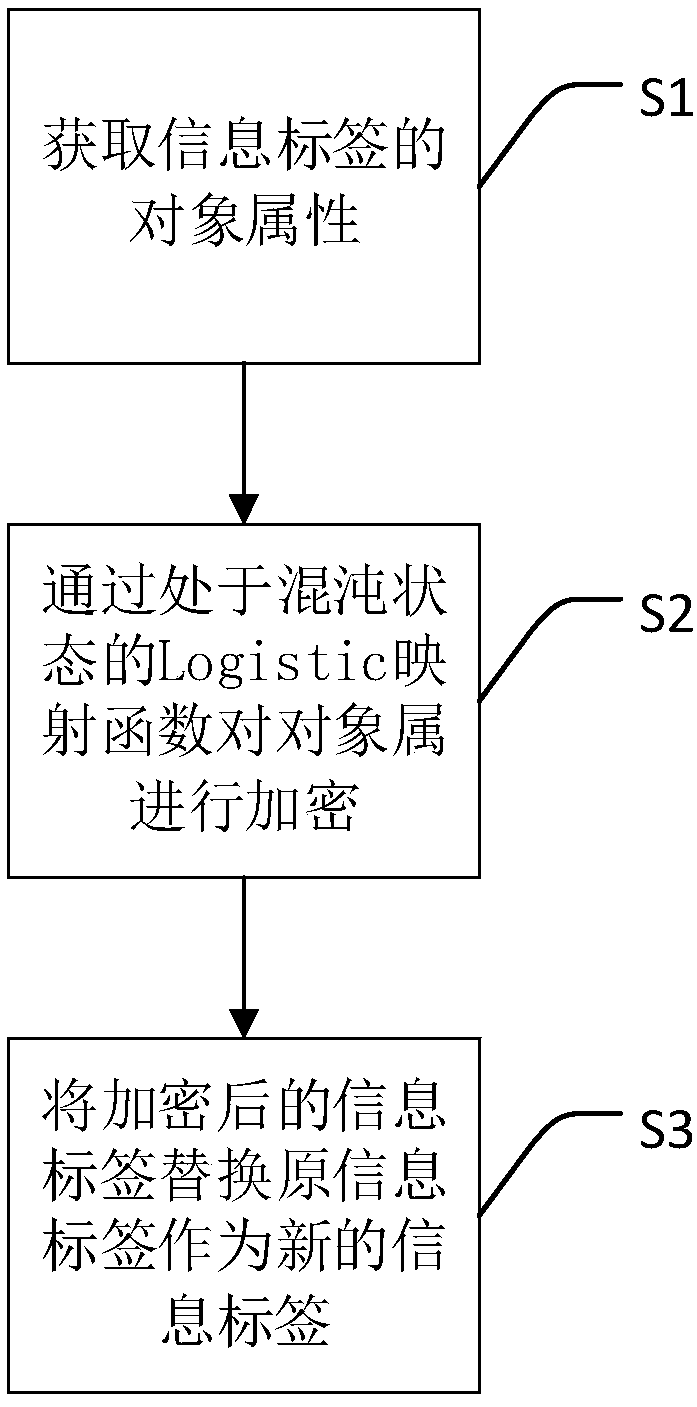
[0024] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings, but the present invention can be implemented in many different ways defined and covered by the claims.
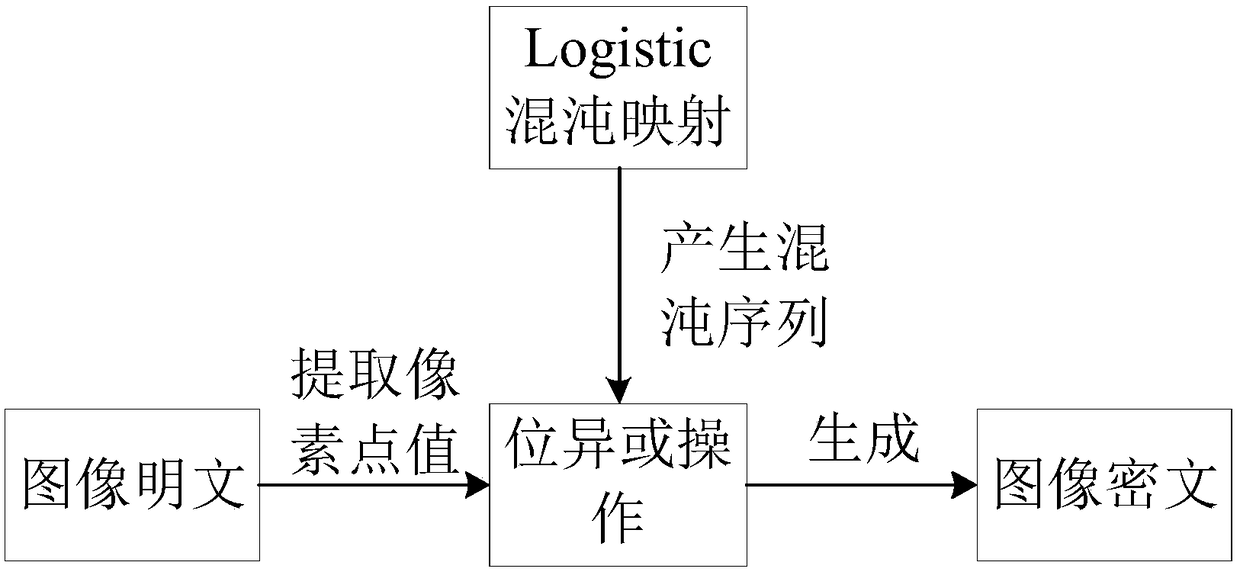
[0025] Logistic mapping is a typical one-dimensional chaotic system, and its formula is defined as follows:
[0026] x k+1 =μχ k (1-χ k )
[0027] Among them: μ is the branch parameter, k is the number of iterations, 0≤μ≤4, χ k ∈(0,1). When 3.569≤...≤μ≤4, the Logistic map is in a chaotic state, and the bifurcation of the chaotic state is similar to random but not random, showing a disordered, unpredictable, and chaotic phenomenon. In addition, there is no periodicity. Its parameters The relationship with the mapping value is as follows Figure 4 shown. When it is used in the encryption field, the randomly generated mapping value can only be cracked through the parameters given by the encryptor.
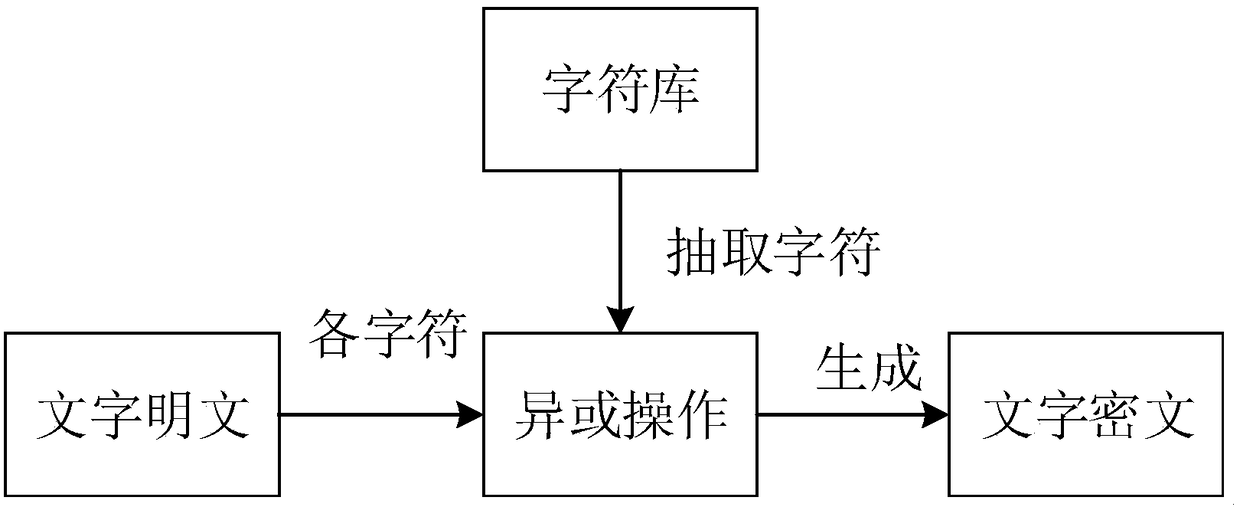
[0028] The present invention firstly provides...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com