Internet of Things device identity verification method
An identity verification method and IoT device technology, applied in the field of Internet of Things identity verification, can solve problems such as forged, tampered or intercepted device data, and achieve the effects of saving construction costs, solving access problems, and ensuring legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
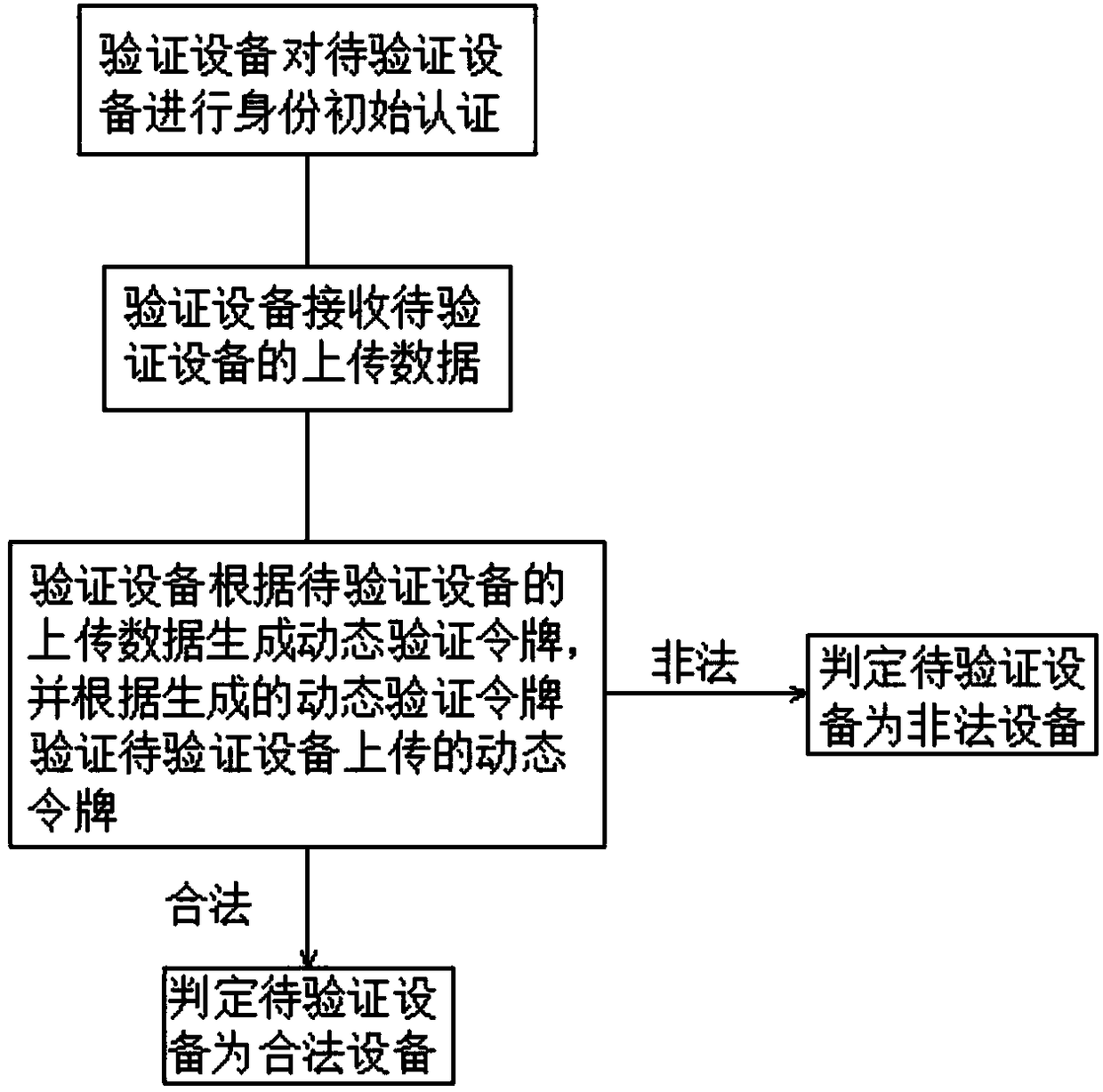
[0045] Such as figure 1 As shown, this embodiment provides a method for authenticating an IoT device, including:
[0046] S1: The verifying device conducts initial authentication of the identity of the device to be verified;
[0047] S2: The verification device receives the uploaded data of the device to be verified, and the uploaded data of the device to be verified includes a dynamic token;
[0048] S3: The verification device generates a dynamic verification token according to the uploaded data of the device to be verified, and verifies whether the dynamic token uploaded by the device to be verified is legal according to the generated dynamic verification token, and if so, determines that the device to be verified is a legal device, otherwise, It is determined that the device to be verified is an illegal device.
[0049] What needs to be explained here is that this embodiment can be used on a data collection platform, and can also be used on other data interaction platfor...
Embodiment 2
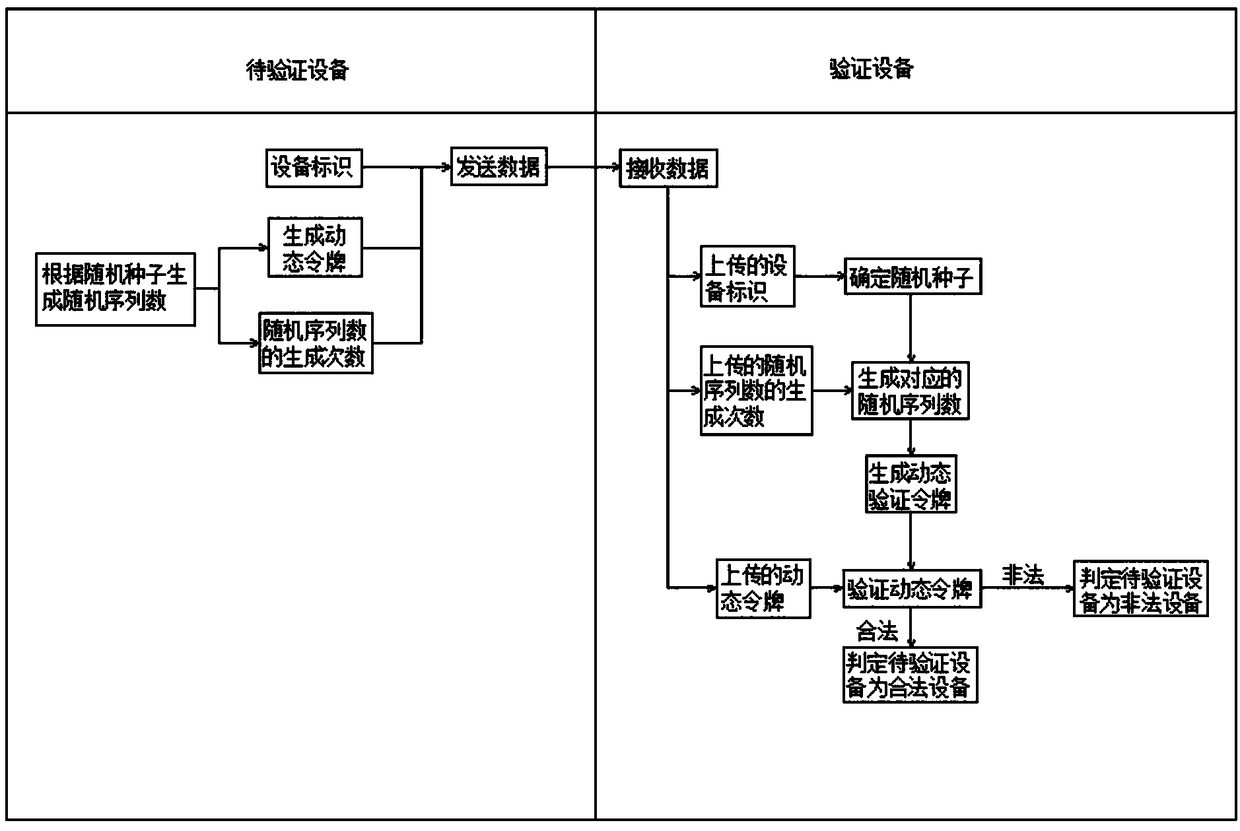
[0070] Such as Figure 4 As shown, this embodiment provides an IoT device identity verification method. Compared with the method provided in Embodiment 1, this method has more encryption links, specifically including:
[0071] P1: The verification device conducts initial authentication of the identity of the device to be verified;
[0072] P2: The verification device receives the uploaded data of the device to be verified, and the uploaded data of the device to be verified includes an encrypted data packet;
[0073] P3: The verification device generates a dynamic decryption token based on the uploaded data of the device to be verified, and uses the dynamic decryption token to decrypt the encrypted data packet uploaded by the device to be verified, and verifies whether the decrypted information is legal. If so, determine that the device to be verified is If the device is legal, otherwise, it is determined that the device to be verified is an illegal device.
[0074] What need...
Embodiment 3
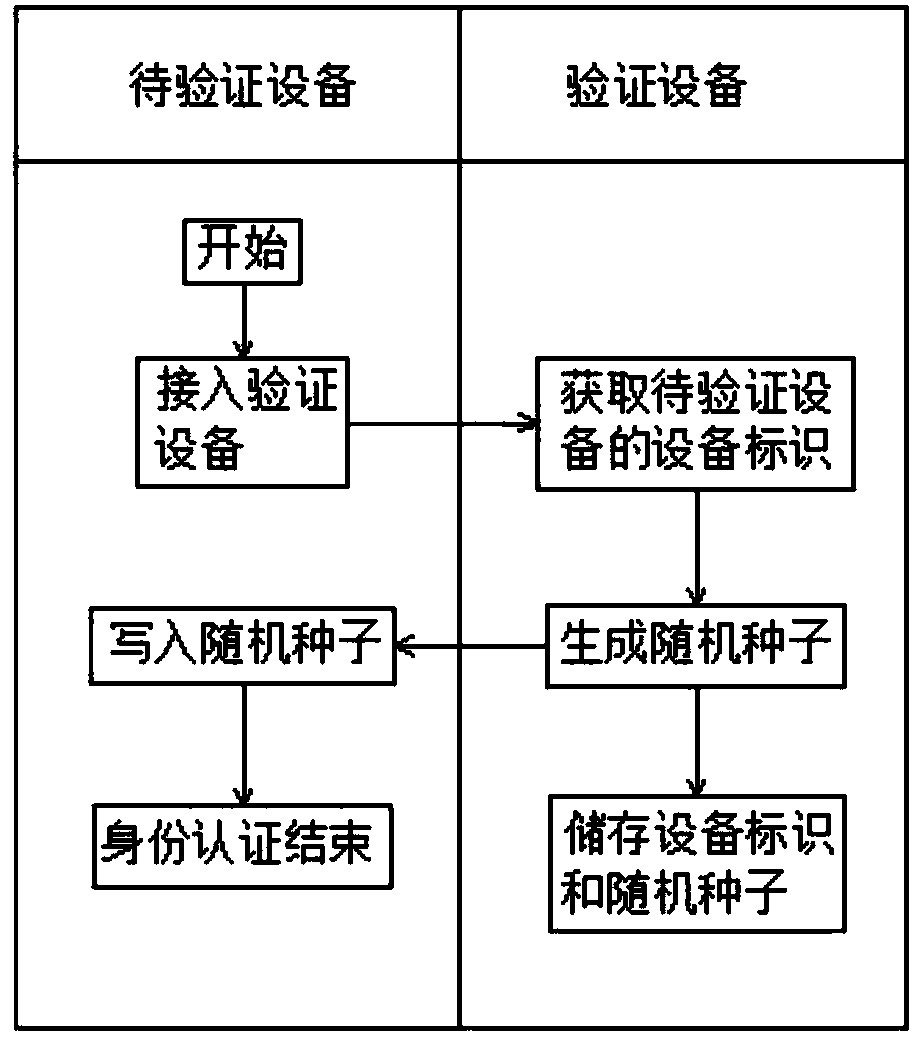
[0096] Such as image 3 As shown, this embodiment provides an IoT device identity verification system, including a verification device and a device to be verified, and the verification device includes:
[0097] The first data communication unit: used to read the information of the device to be verified, and also used for the verification device to write information to the device to be verified;
[0098] The first data storage unit: used to store the information read by the data communication unit and the information generated by the authentication unit;
[0099] Device authentication unit: used to generate relevant information according to the information read by the data communication unit, write the generated relevant information into the device to be verified through the data communication unit, and store the generated relevant information in the data storage unit;
[0100] Device verification unit: used to dynamically verify whether the device to be verified is legal acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com