Teaching and training reader control method for protecting RFID labels
A technology of RFID tags and control methods, applied in the control field of teaching and training readers, can solve the problems of RFID card failure, unfavorable movement, time-consuming and labor-intensive, etc., to protect RFID tags, increase the average service life, and reduce management work. amount of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
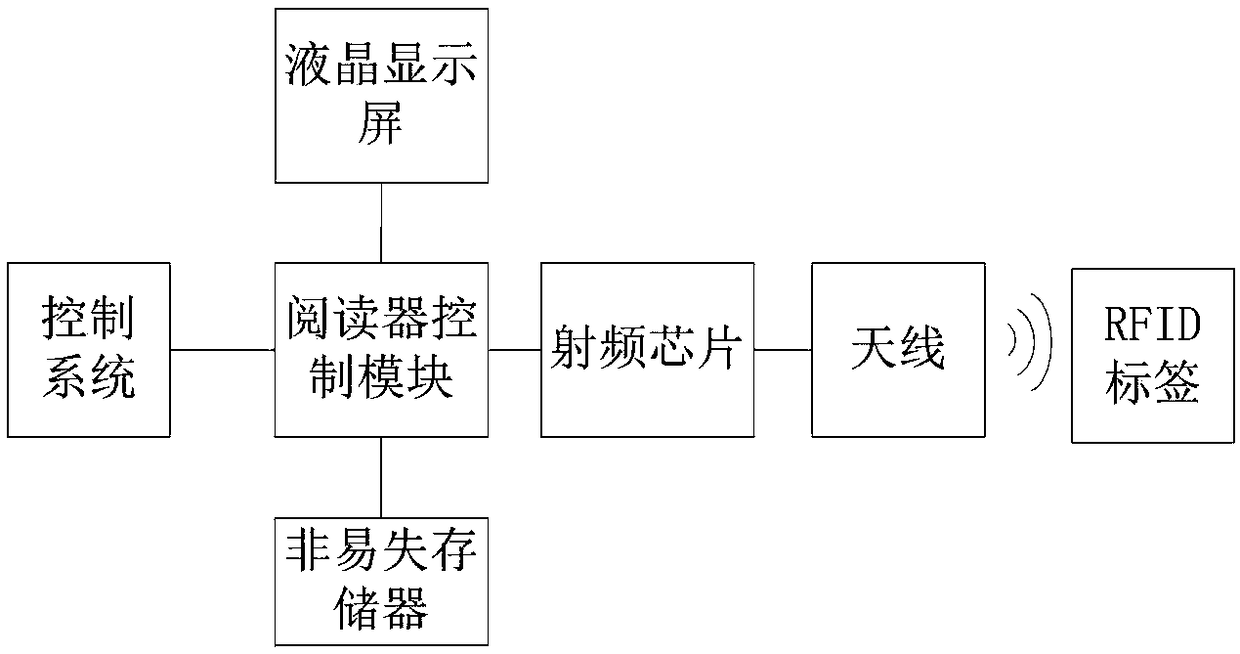
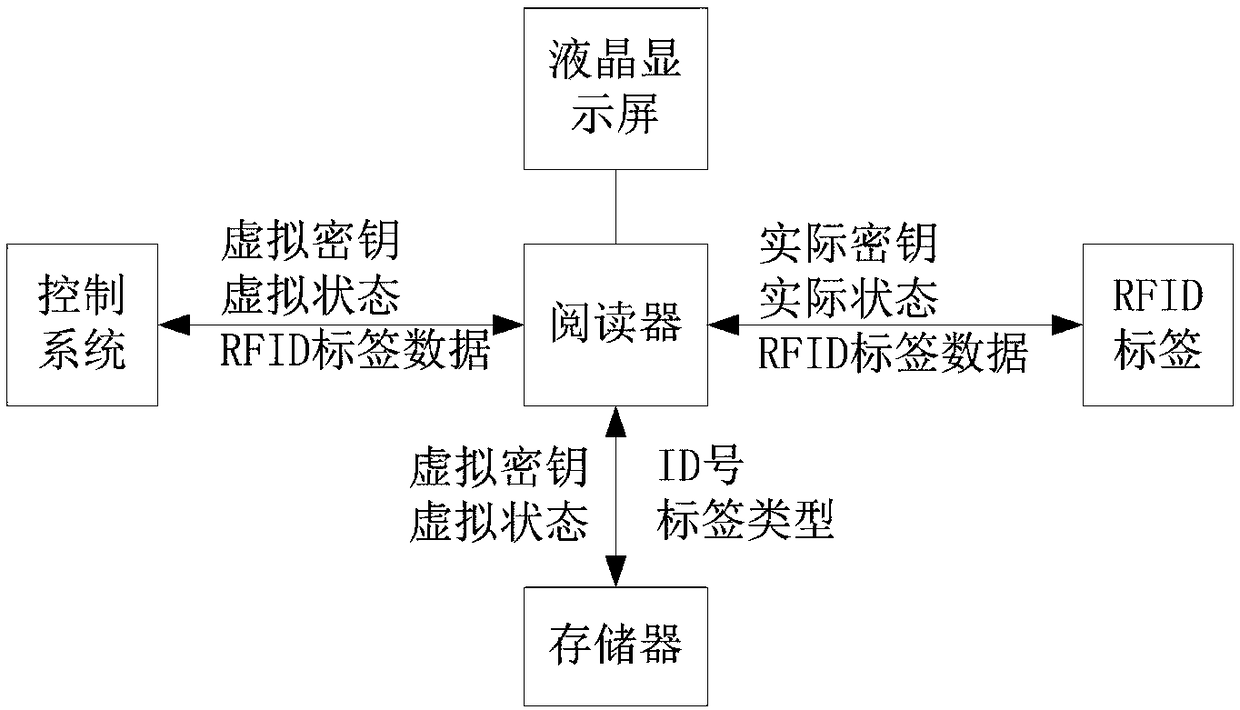
[0045] Such as figure 1 and figure 2 As shown, a control method for teaching and training readers that protect RFID tags. Before the experiment starts, the control system generates the data structure corresponding to the tag record according to the type of RFID tag tested and sends it to the reader. The data structure initializes the memory, and the RFID tag in the memory is accessed as the initial tag record; accessing the RFID tag includes the following steps:
[0046] Step 10, read tag operation
[0047] After the control system sends the command to read the tag, the reader controls the RFID reading chip to perform the tag reading operation, and the RFID tag in the antenna responds to the command of the control system; finally, the reader parses the result and sends it to the control system;
[0048] Step 20, anti-collision operation
[0049] The control system sends anti-collision commands, and the reader controls the RFID reading chip to perform anti-collision operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com