Network attack alarming method and system
A network attack and alarm information technology, applied in the field of network security, can solve the problem of high operation and maintenance processing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
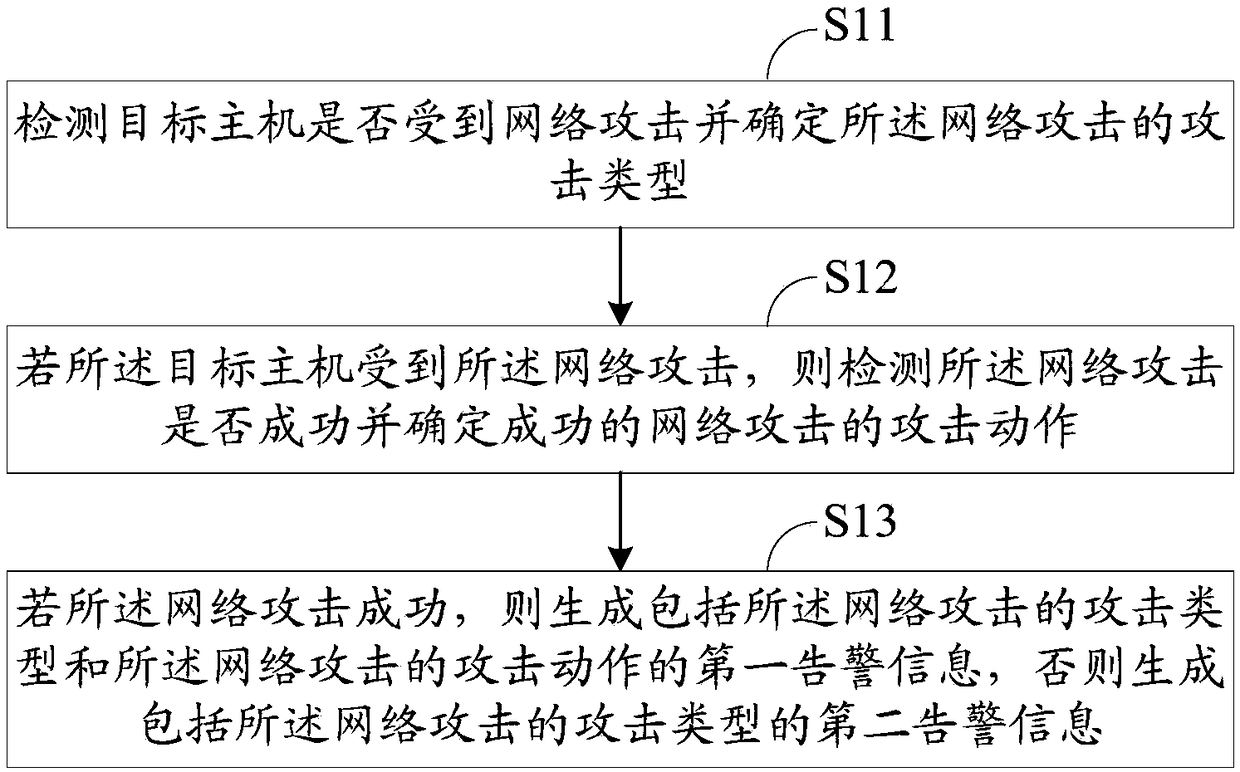
[0143] This embodiment provides a network attack warning method, figure 1 It is a schematic flow chart of the network attack warning method, and the network attack warning method includes:
[0144] Step S11, detecting whether the target host is under a network attack and determining the attack type of the network attack;
[0145] Step S12, if the target host is under the network attack, then detect whether the network attack is successful and determine the attack action of the successful network attack;
[0146] Step S13, if the network attack is successful, generate first alarm information including the attack type of the network attack and the attack action of the network attack, otherwise generate second alarm information including the attack type of the network attack.
[0147] The target host may be a server providing various services, a personal computer capable of realizing specific functions, or other network devices capable of providing network services. The target ...
Embodiment 2
[0192] Embodiment 1 adopts an alarm mode in which one network attack corresponds to one alarm message, that is, a corresponding alarm message is generated when a network attack is detected. However, isolated alarm information cannot accurately reflect the security status of the target host, and this kind of attack display cannot grasp the attack process as a whole. Therefore, this embodiment provides another network attack warning method. Compared with the network attack warning method provided in Embodiment 1, after generating the first warning information or the second warning information, this embodiment further includes:
[0193] Adding a corresponding attack chain label to the first alarm information or the second alarm information according to the alarm content, wherein the attack chain label is used to represent the attack stage of the network attack in the attack chain;
[0194] Count each attack chain label of the same attack event, and obtain the total number of net...
Embodiment 3
[0206] This embodiment provides a network attack warning system, the network attack warning system includes: a first detection module, used to detect whether the target host is under a network attack and determine the attack type of the network attack; a second detection module, used to When the target host is subjected to the network attack, detect whether the network attack is successful and determine the attack action of the successful network attack; the alarm information generation module is used to generate information including the network attack when the network attack is successful The attack type of the network attack and the first warning information of the attack action of the network attack, otherwise, the second warning information including the attack type of the network attack is generated.
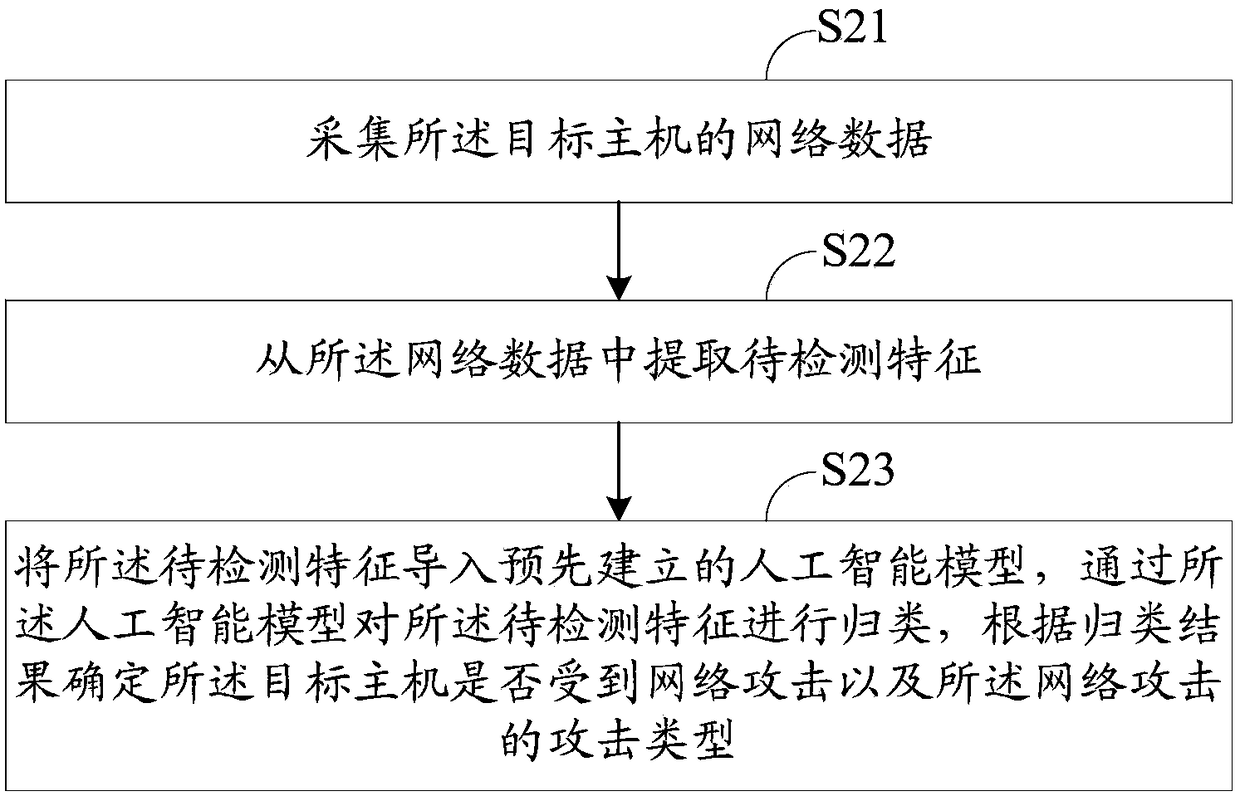
[0207]Further, the first detection module includes: a collection module, used to collect the network data of the target host; a first extraction module, used to extract fea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com