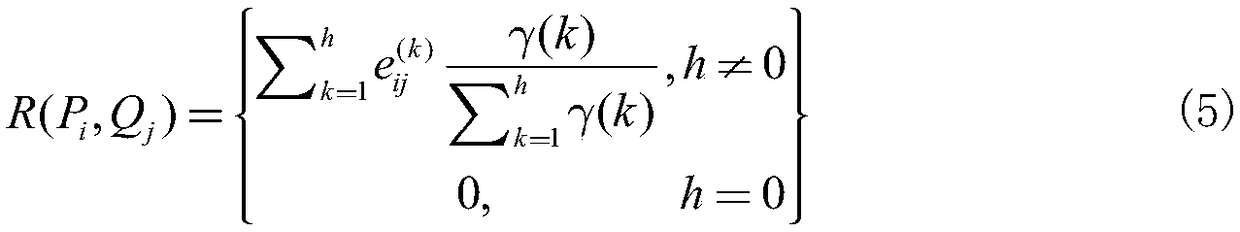Privacy protection method for trust state evaluation
A privacy protection and dynamic evaluation technology, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve the problems of ignoring the privacy and reliability of participants, high computational overhead, and difficult mobile terminal operation, etc. Achieving the effect of balancing privacy protection and perceived quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
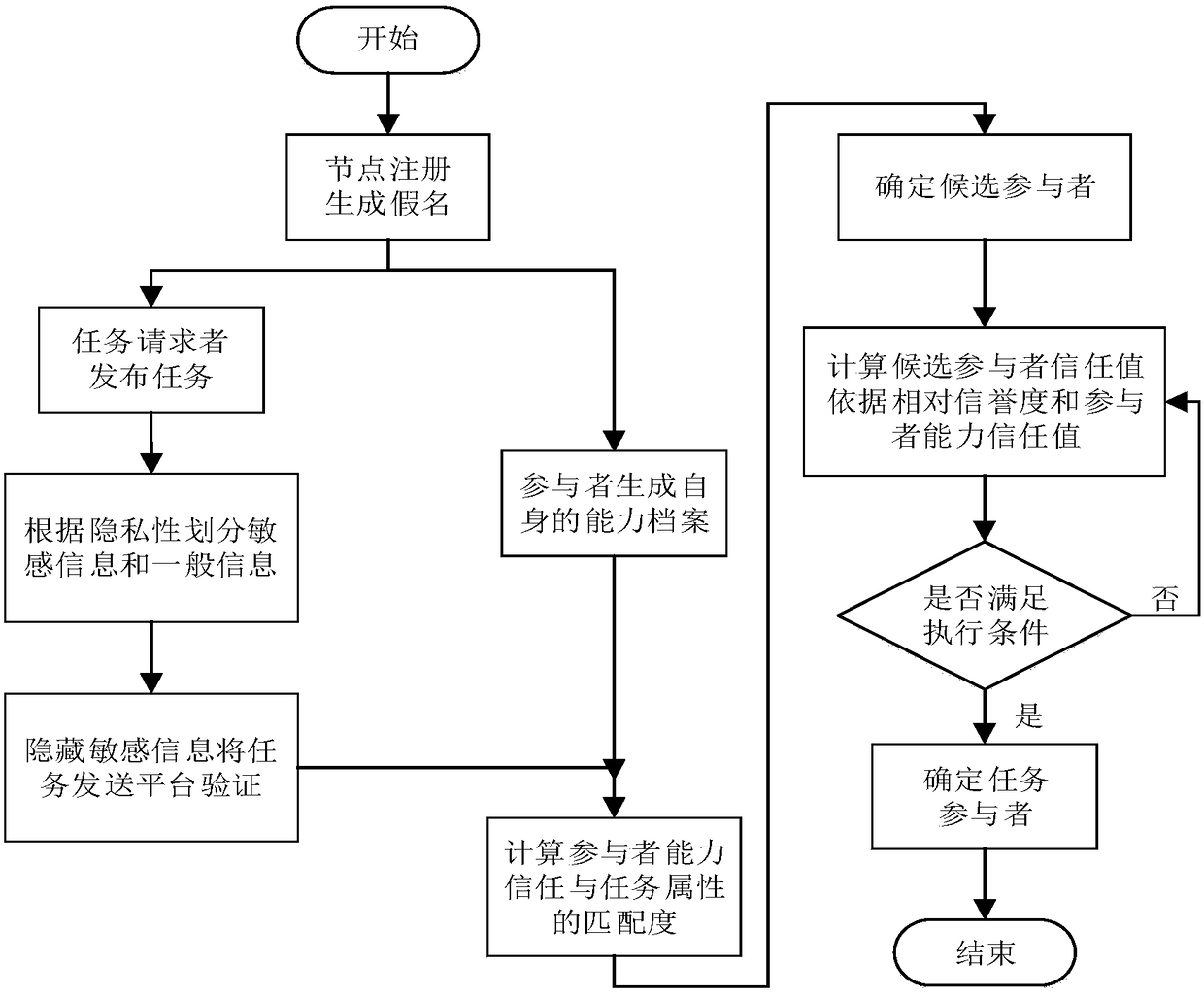
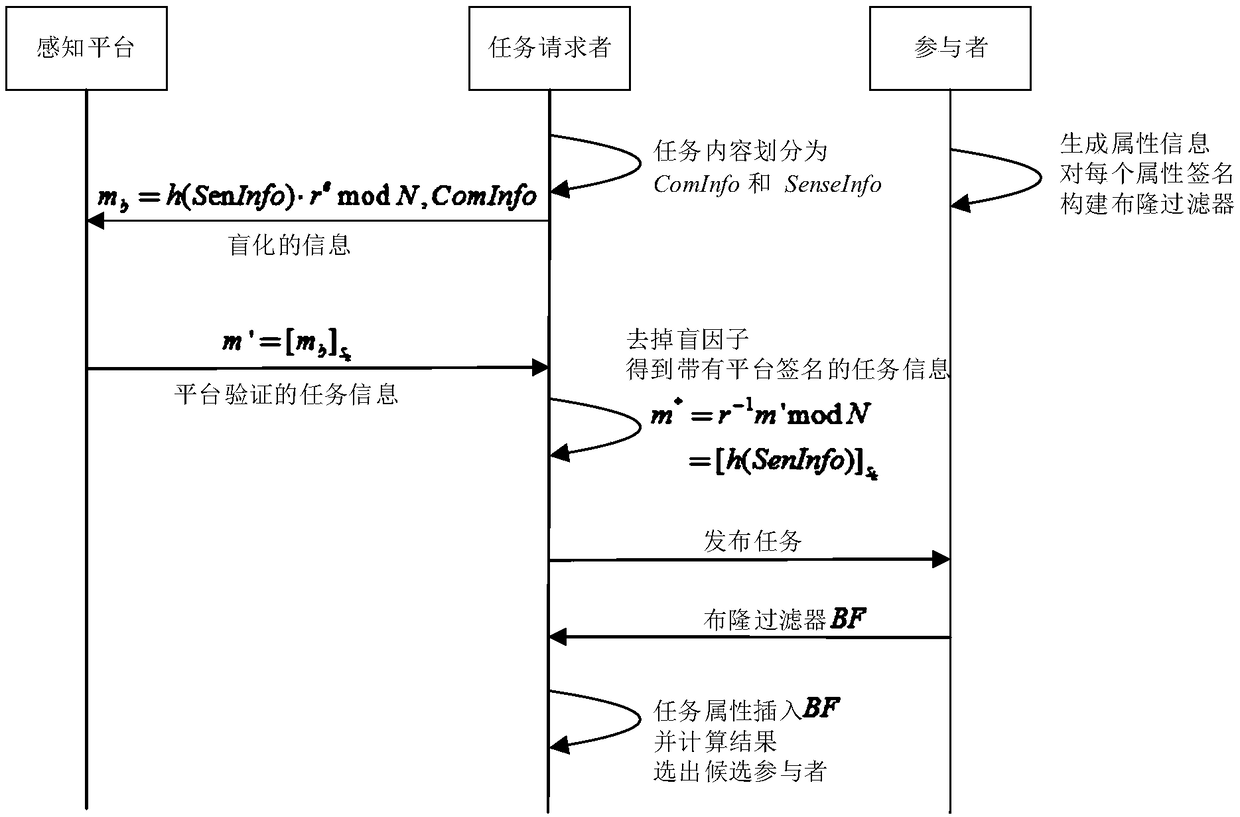
[0011] The implementation of the present invention will be specifically described below in conjunction with the accompanying drawings and specific examples.
[0012] For task assignment with privacy protection in crowd sensing, the usual practice in the prior art is to assume that each user has a set of attributes such as location, occupation, interest, and specialty. When the task issuer requests the sensing task, the requirements of the sensing task are also listed in a set of task attributes, such as task sensing location, required time, sensing type, etc. Before the task is released, the attribute set of the evaluation node of the perception platform matches the task attribute set, and the more common elements of the two sets, the higher the suitability of the user for the task. The whole process does not reveal the user's personal attribute information, but these solutions have certain limitations: the matching function only considers the number of common attributes, igno...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com