Communication monitoring method and device
A technology for monitoring and monitoring strategies during calls, applied in the field of communications, can solve the problem of insufficient interception of harassing calls, and achieve the effect of improving monitoring and prevention capabilities and improving the interception rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
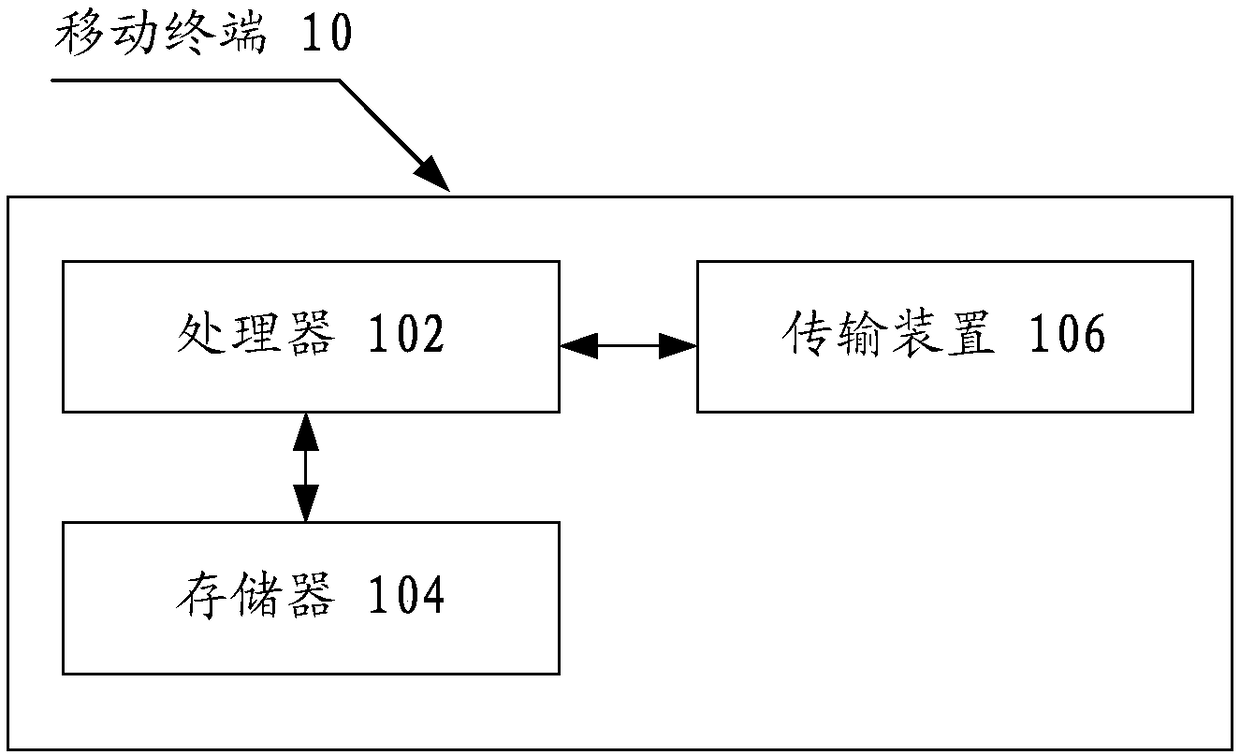
[0030] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Taking running on a mobile terminal as an example, figure 1 It is a hardware structural block diagram of a mobile terminal of a call monitoring method according to an embodiment of the present invention. like figure 1 As shown, the mobile terminal 10 may include one or more (only one is shown in the figure) processor 102 (the processor 102 may include but not limited to a processing device such as a microprocessor MCU or a programmable logic device FPGA, etc.), for A memory 104 for storing data, and a transmission device 106 for communication functions. Those of ordinary skill in the art can understand that, figure 1 The shown structure is only for illustration, and it does not limit the structure of the above-mentioned electronic device. For example, the mobile terminal 10 may also include figure 1 more...
Embodiment 2
[0058] In this embodiment, a call monitoring device is also provided, which is used to implement the above embodiments and preferred implementation modes, and those that have been explained will not be repeated here. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
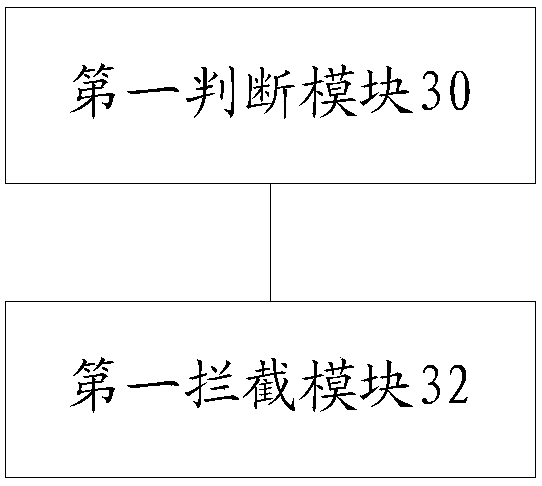
[0059] image 3 is a structural block diagram of a call monitoring device according to an embodiment of the present invention, such as image 3 As shown, the device includes:
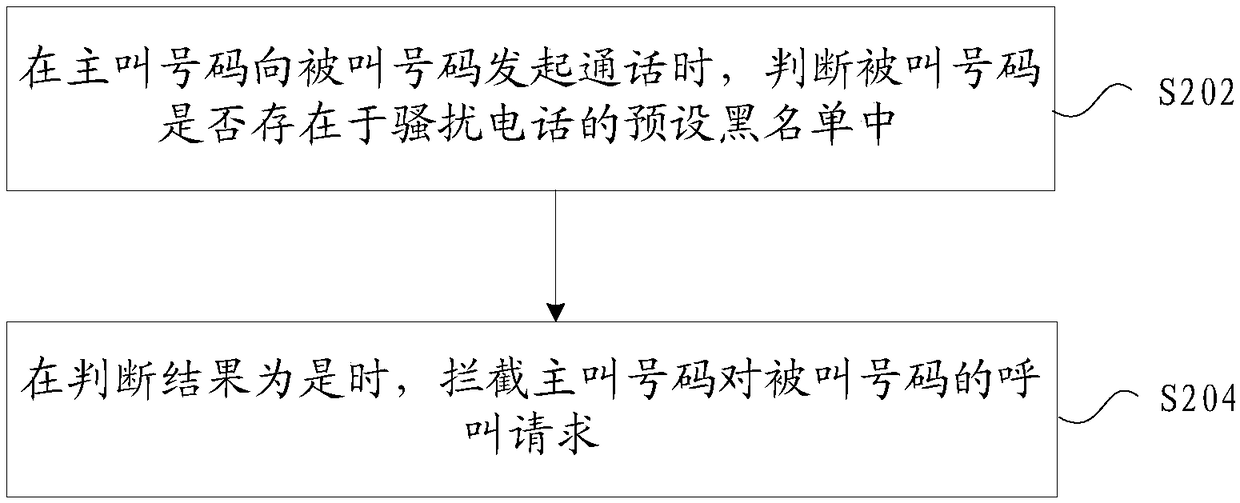
[0060] The first judging module 30 is used to judge whether the called number exists in the preset blacklist of harassing calls when the calling number initiates a call to the called number;
[0061] The first interception module 32 is configured to intercept the...
Embodiment 3
[0068] This embodiment is an optional embodiment according to the present invention, and is used to describe the application in detail in conjunction with specific examples:
[0069] The scheme of this embodiment can further improve the accuracy of harassing call interception, prevent problems before they happen, supplement and improve the current harassing call monitoring method, and use the monitored harassing source information to monitor the harassing source number in an all-round way. It is forbidden for ordinary users to call back and get through the harassment source number.
[0070] This embodiment provides a method for monitoring harassing calls based on the state analysis of the called user. During the monitoring process, before analyzing the characteristics of the calling call, the state information of the called user is searched, and whether the called user is black or not based on the feedback from the storage module List users to distinguish whether this call is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com