Verifiable database encryption retrieval method and system based on secret sharing
A secret sharing and database technology, applied in digital transmission systems, transmission systems, digital data protection, etc., can solve problems such as cumbersome methods, low efficiency, and troublesome inspections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
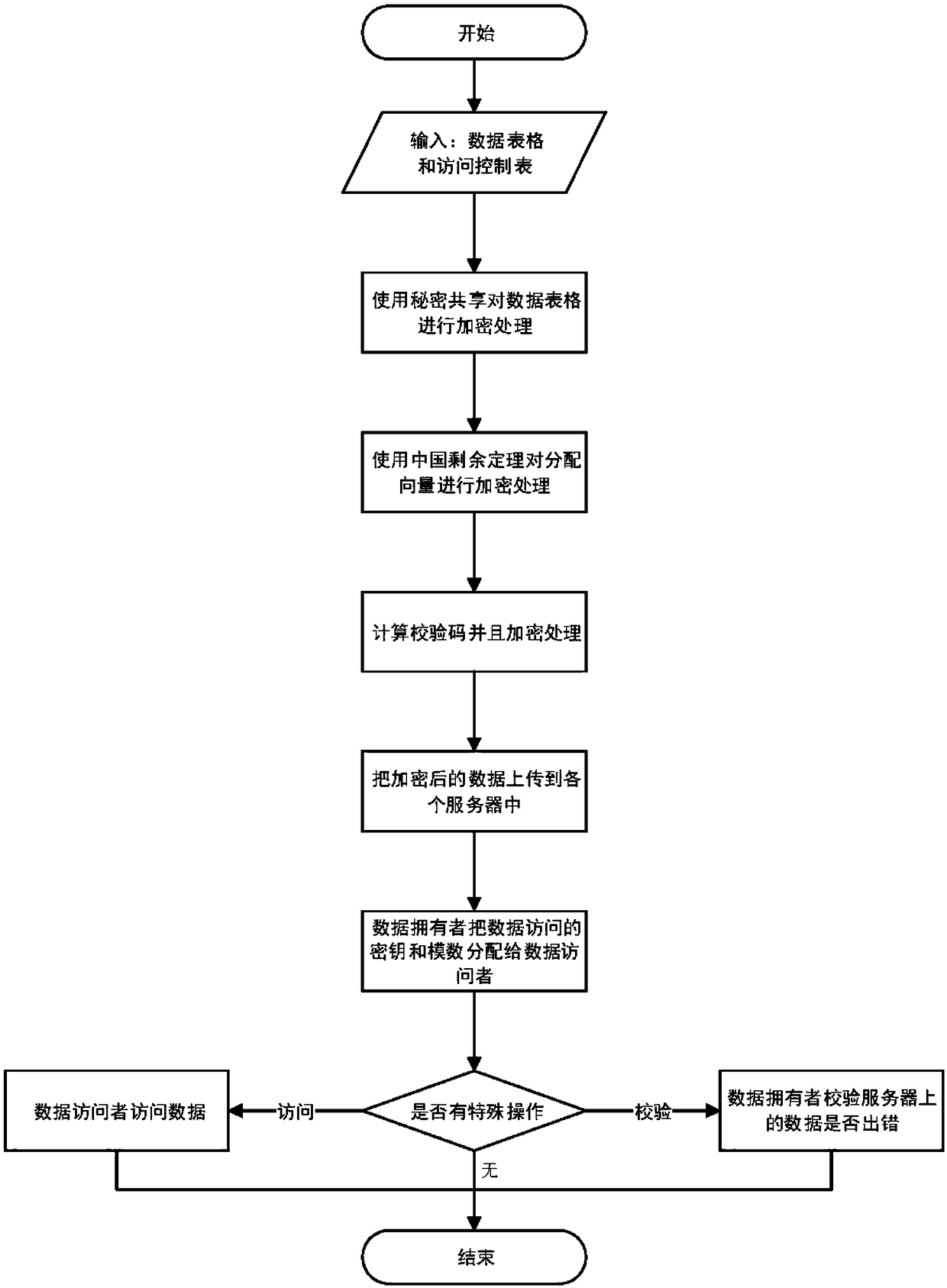
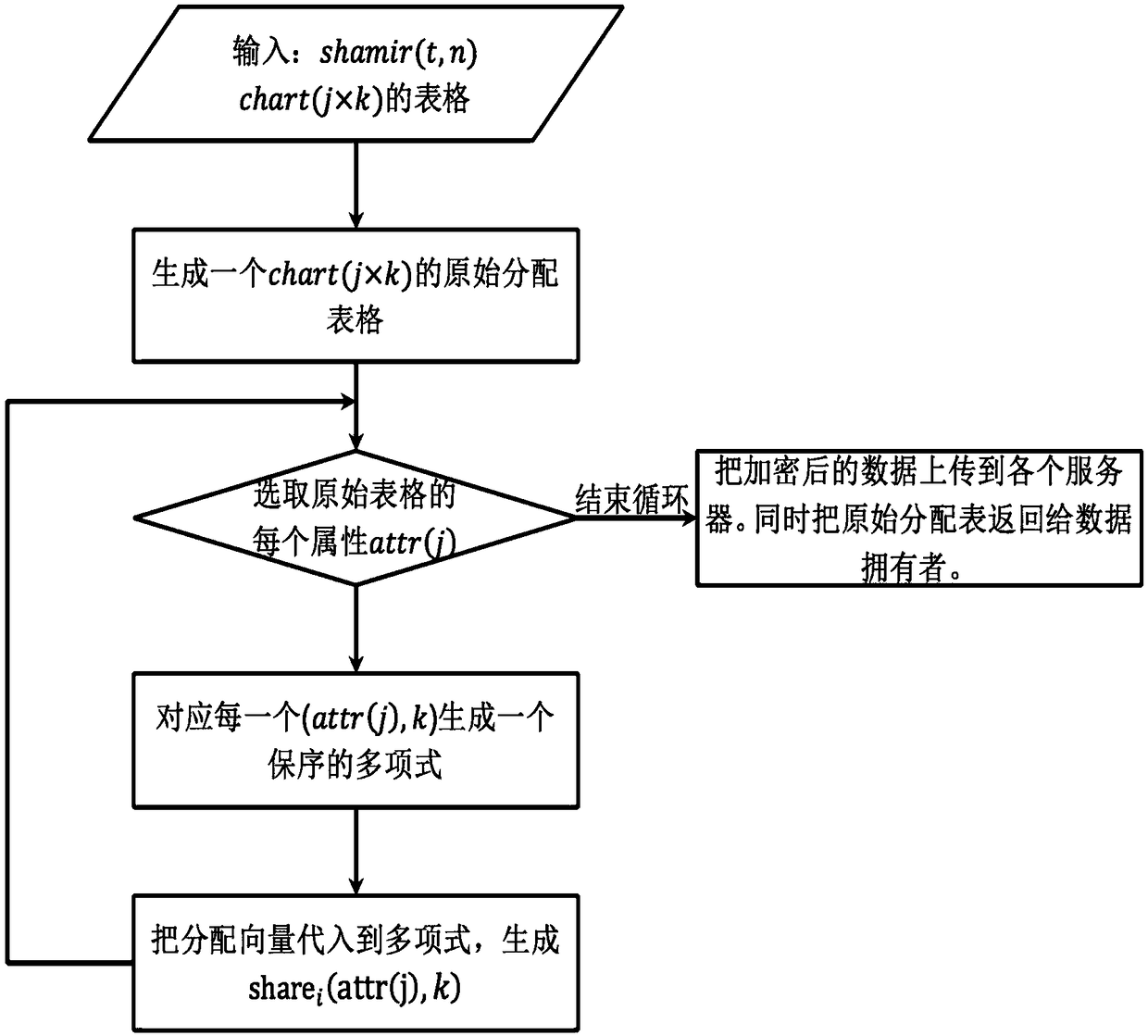
[0193] Using n=3, t=2 secret sharing, process a student information table, as shown in the following table:
[0194]
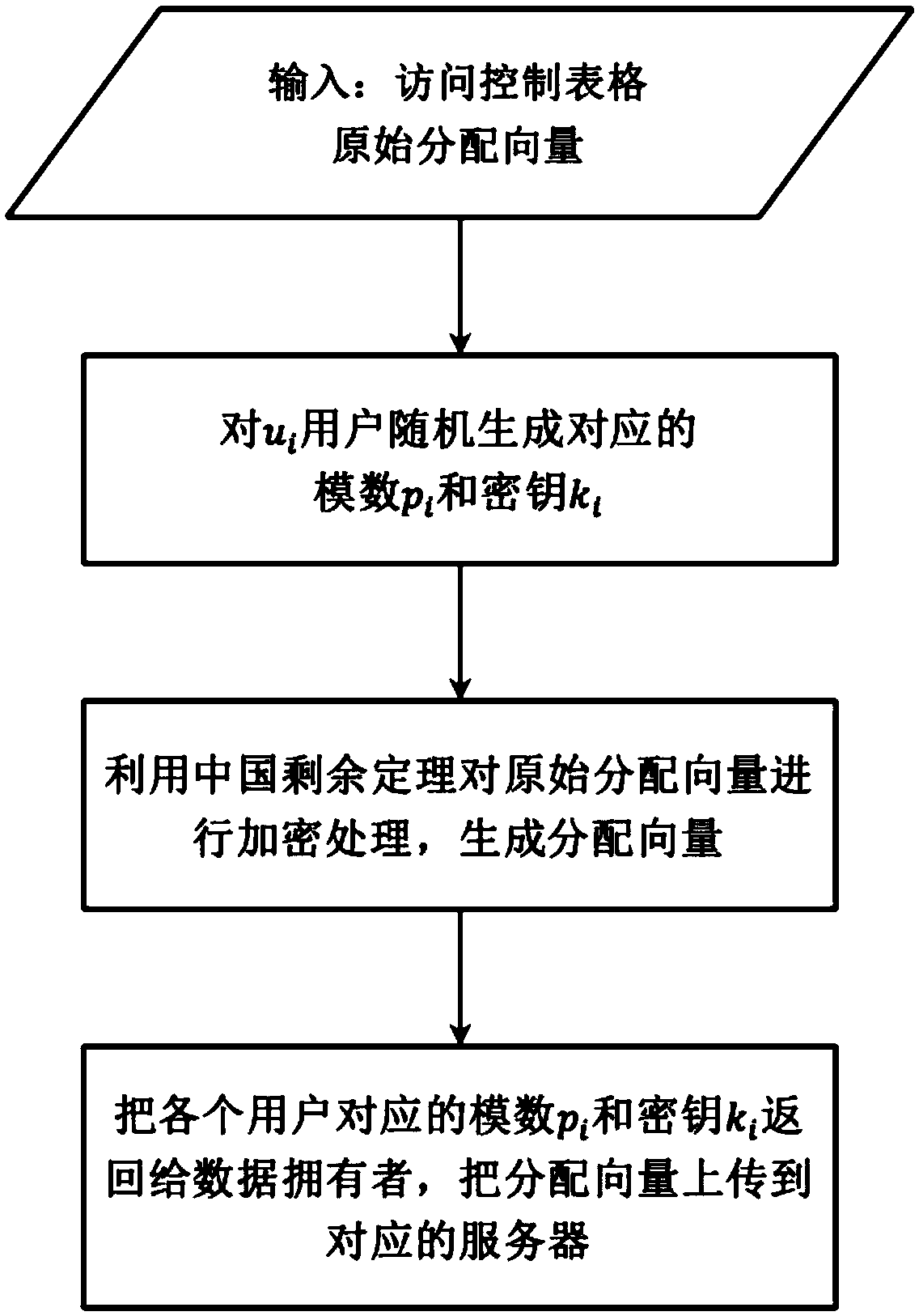
[0195] Then, the server randomly generates a raw allocation vector table:
[0196]
[0197] At the same time, for the data attr of the same attribute, if attr i >attr j , the coefficient a of the polynomial corresponding to the data must also have a i >a j ; then, generate the following polynomial, as shown in the following table:
[0198]
[0199] Afterwards, according to the original allocation vector table, data encryption on different servers is realized. For example: the allocation vector of server 1 is (2, 3, 3), all, server 1 mainly stores the following contents (the same applies to other servers), as shown in the following table:
[0200]
[0201] The data owner uploads a list of user access rights, encrypts the original assignment, and uploads it to a different server.
[0202] Now there are mainly 3 users, and the access permission ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com