Web intrusion detection technology based on machine learning
An intrusion detection and machine learning technology, applied in electrical components, transmission systems, etc., can solve problems such as labor-intensive, difficult to identify attacks, and pattern matching algorithms affecting detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The technical framework of the invention will be described below in conjunction with the accompanying drawings.
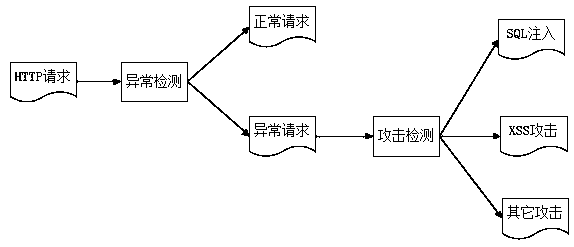
[0014] figure 1 It is a framework diagram of the technical process of the present invention.
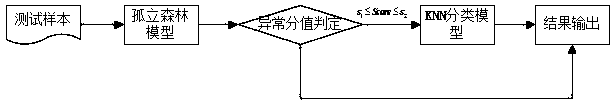
[0015] First, the iForest algorithm is used to identify abnormal requests. The iForest algorithm cannot effectively detect local outliers. When the local outliers in the sample set are covered by normal clusters with similar densities, the local outliers are not easily isolated by isolated trees, resulting in poor anomaly detection results. The invention proposes an iForest-KNN hybrid algorithm, by setting the threshold of the abnormal score, and using the KNN algorithm to perform secondary detection on the abnormal points.
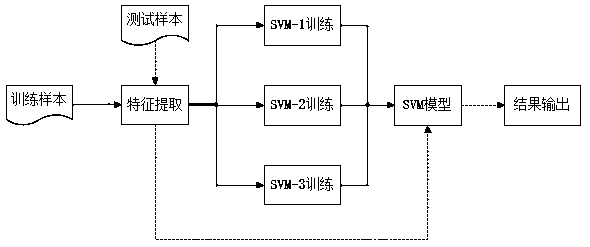
[0016] Then, the SVM algorithm is used to identify the attack type of the abnormal request. The SVM algorithm gives all the features the same weight. In the process of building the feature matrix, it is very likely to be mixed with features ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com