Information privacy protection method based on data map, information map and knowledge map
A technology of knowledge graph and privacy protection, applied in the intersection of distributed computing and software engineering, it can solve the problem that it is difficult to effectively support data layer, query, abstraction, privacy addition and deletion cannot be carried out effectively, and there is no distinction between typed resources, etc. problems, to achieve the effect of enhancing integrity, eliminating redundancy, and enhancing consistency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
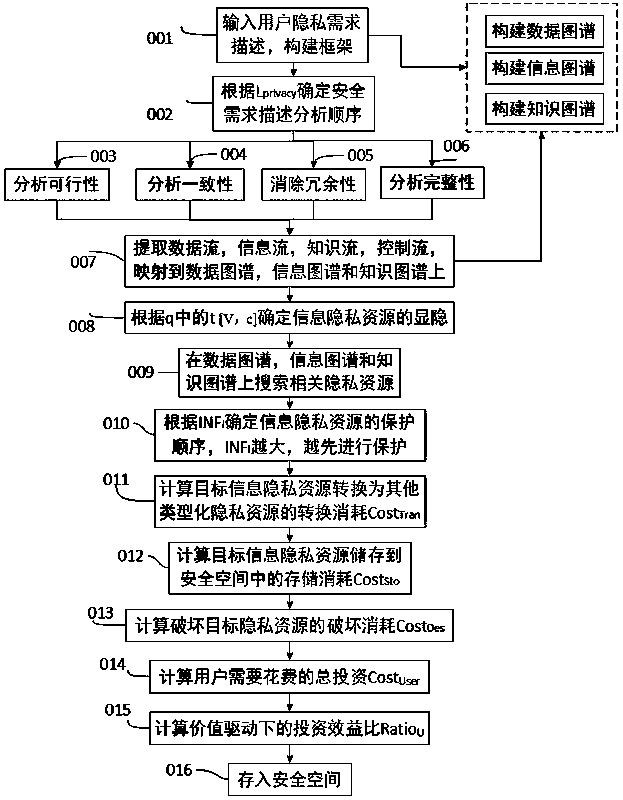
[0048] The specific process of an information privacy protection method based on data graph, information graph and knowledge graph is as follows:
[0049] Step 1) corresponds to figure 1 As shown in 001, according to the needs of users, a framework based on data graphs, information graphs, and knowledge graphs is established;
[0050] Step 2) correspond to figure 1 As shown in 002, according to formula 1, the privacy level L of information privacy resources Privacy Determine the sequence of requirement description analysis;
[0051] Step 3) correspond to figure 1 As shown in 003, combine formula 2 and algorithm 1 to analyze the feasibility of privacy requirement description;
[0052] Step 4) correspond to figure 1 As shown in 004, combine formula 3 and algorithm 2 to analyze the consistency of privacy requirement description;
[0053] Step 5) correspond to figure 1 As shown in 005, combine formula 4 and algorithm 3 to analyze the redundancy of the privacy requirement de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com