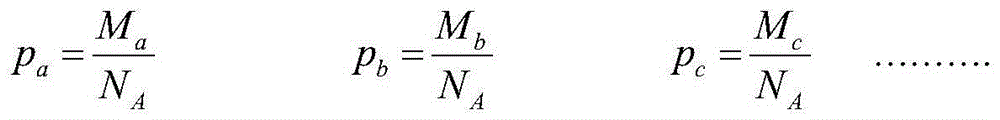Patents
Literature
40 results about "Demand modeling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Demand modeling uses statistical methods and business intelligence inputs to generate accurate demand forecasts and effectively address demand variability. Demand modeling is becoming more important because forecasting and inventory management are being complicated by the increasing number of slow-moving items, the so-called “long-tail” of the product range, many of which have unpredictable demand patterns in which the typical “normal distribution” assumption used by traditional models is totally inadequate. In these scenarios, successfully managing forecasts and inventories requires advanced demand and inventory modeling technologies in order to reliably support high service levels.
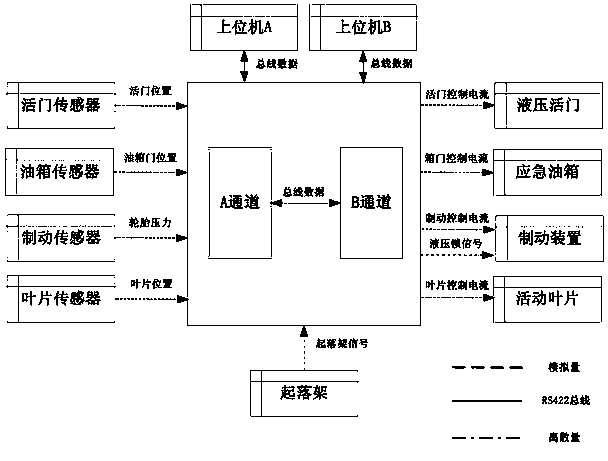
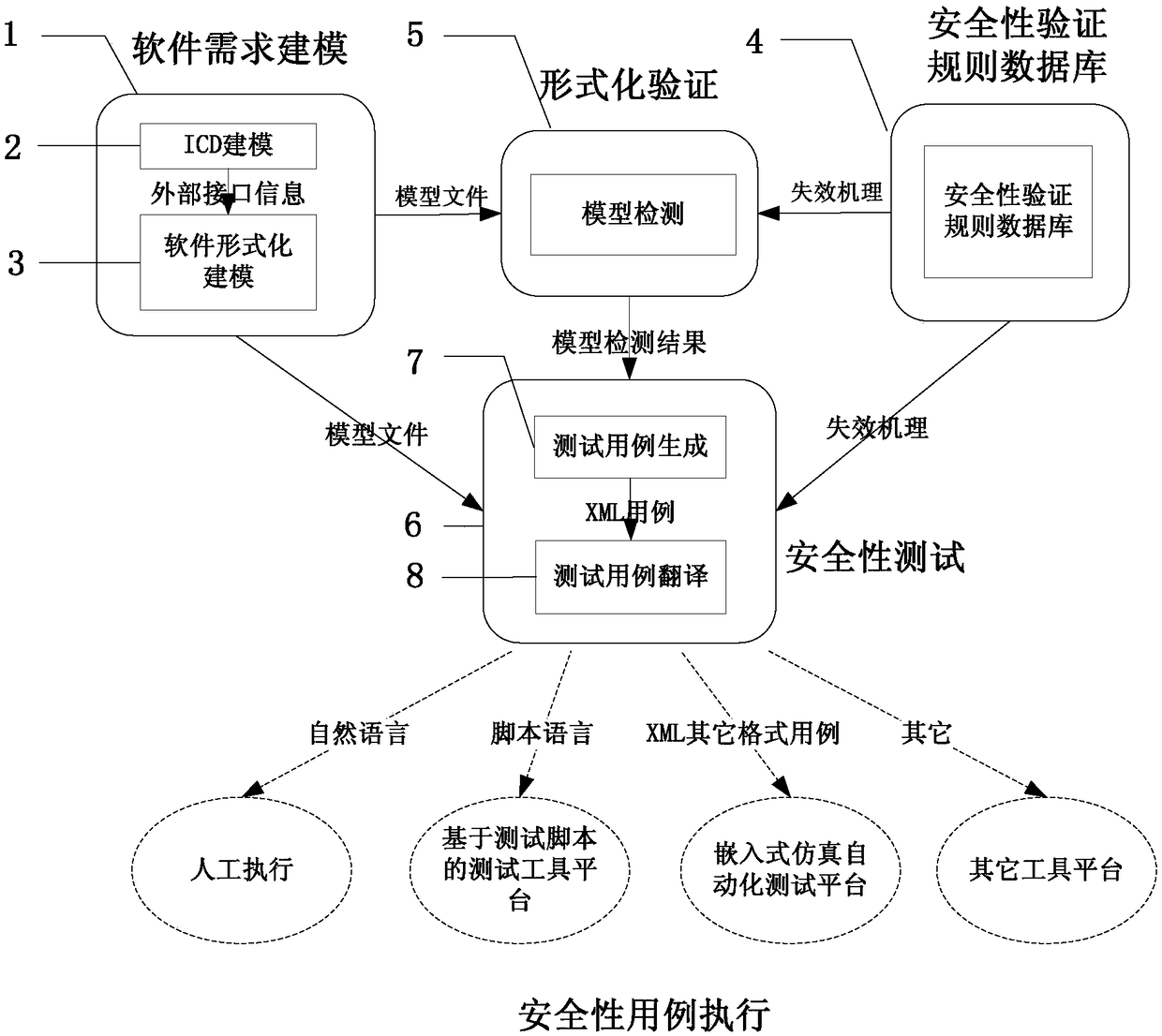
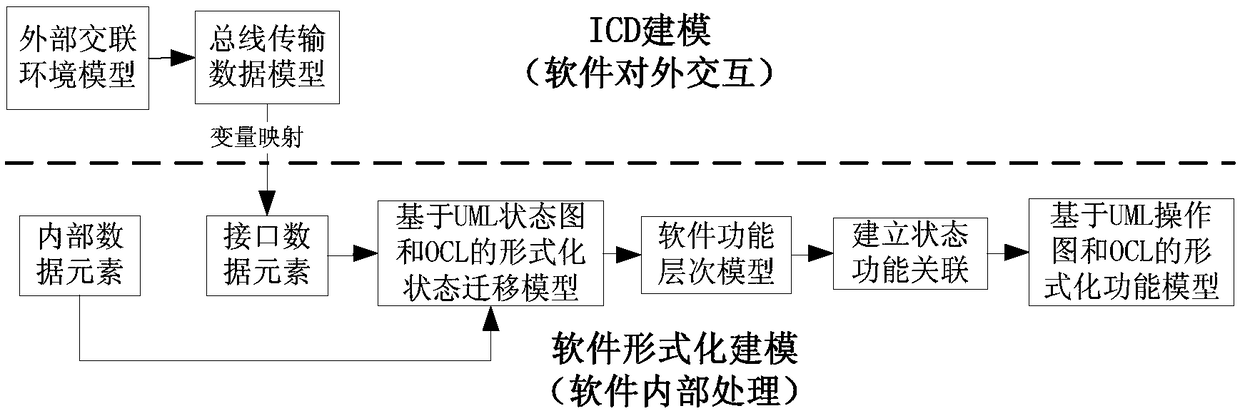
Embedded software security automation verification system and verification method thereof
ActiveCN106528407AImprove sufficiencyLower barriers to useSoftware testing/debuggingCross-linkValidation methods
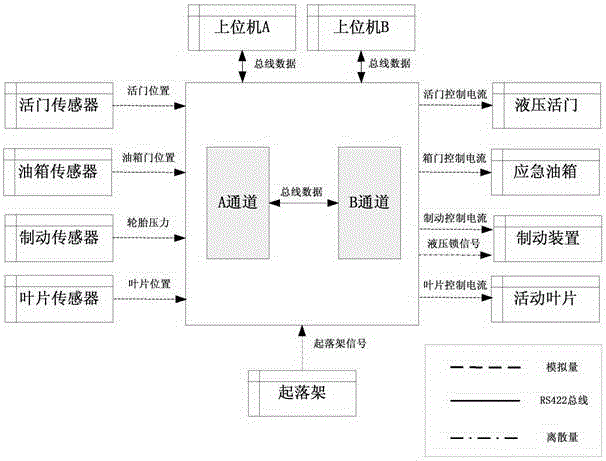
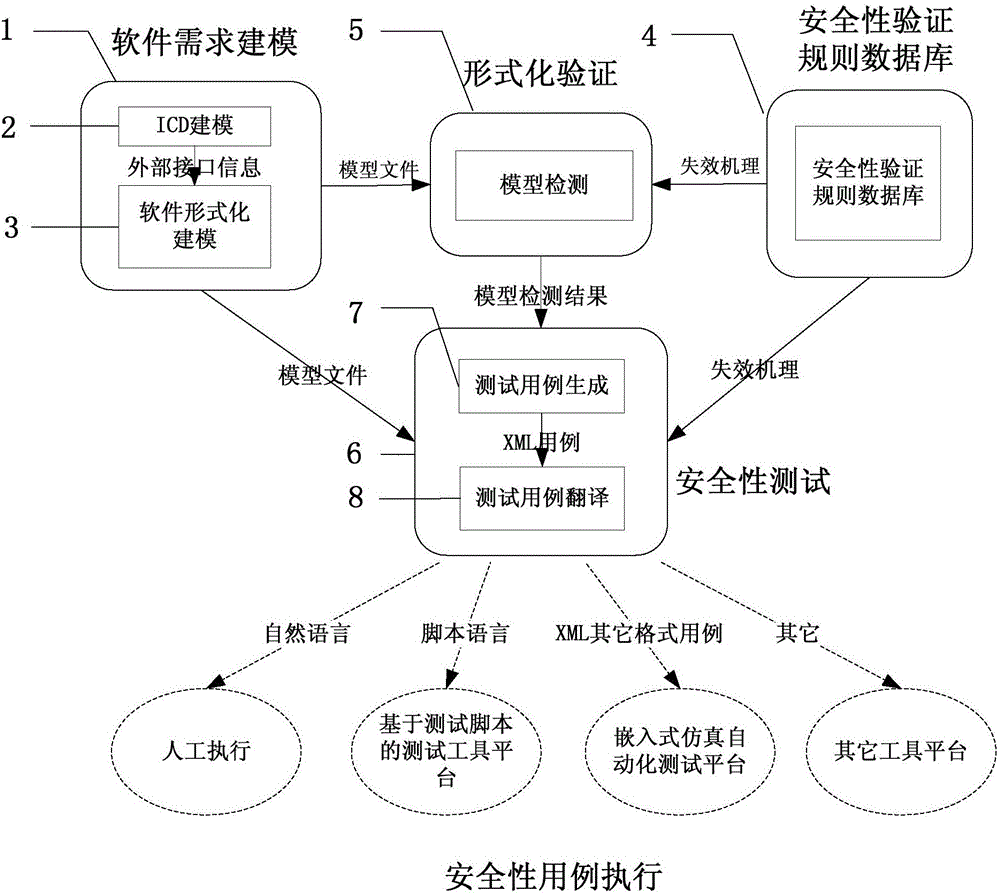
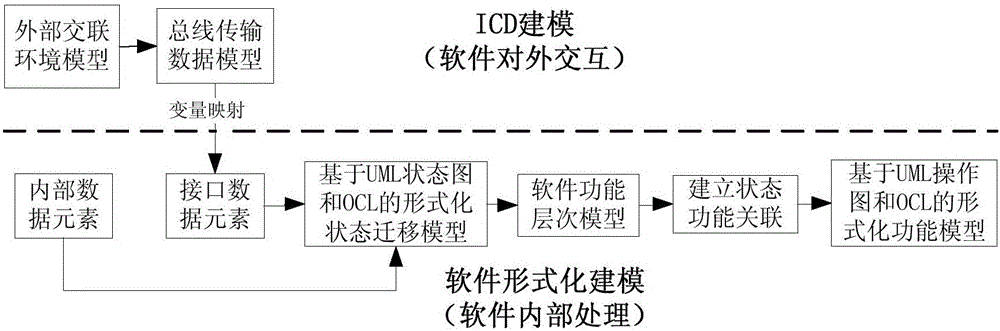
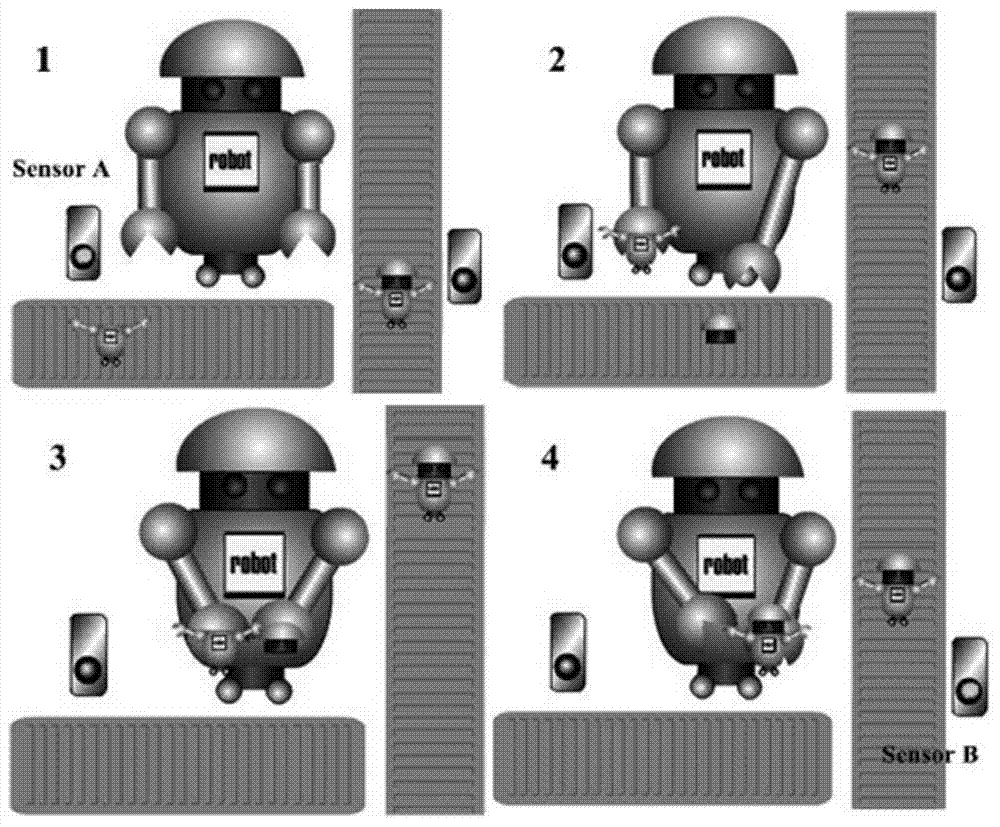
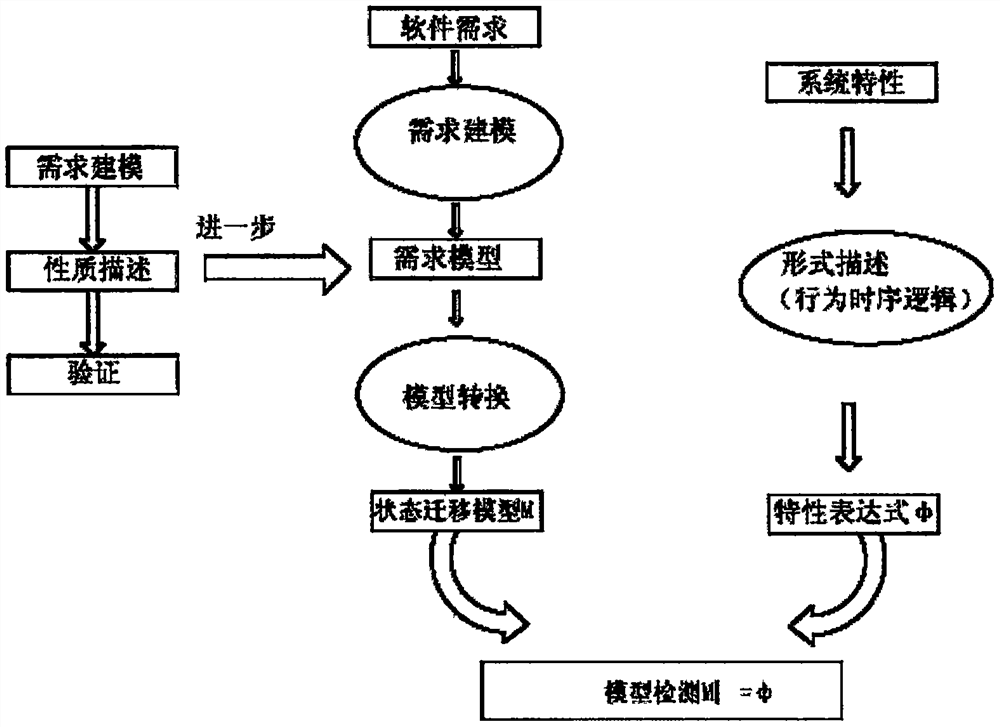
The invention discloses an embedded software security automation verification system and a verification method thereof. According to the technical scheme, double verification of software security is realized in combination with a model checking-based formal verification technology and a model-based software test technology. The automation verification system disclosed by the invention comprises four parts, which are a software demand modeling module, a security verification rule database, a formal verification module, and a security test module respectively. The software demand modeling module comprises two sub-modules, wherein the ICD modeling module describes a software external cross-linking environment, and the formal modeling module describes a software internal behavior. The security verification rule database is constructed and used for storing security verification rules. The formal verification module is constructed and used for performing model verification on a software demand based on the security verification rules and a model detection algorithm. The software detection module comprises two modules, wherein the test case generation module is used for generating an executable security case, and a test case translation module performs format conversion on the generated case.
Owner:CHINA AERO POLYTECH ESTAB
Business application software development system and method
ActiveCN110058846AQuality improvementImprove efficiencySoftware testing/debuggingSoftware designSoftware development processHigh level model
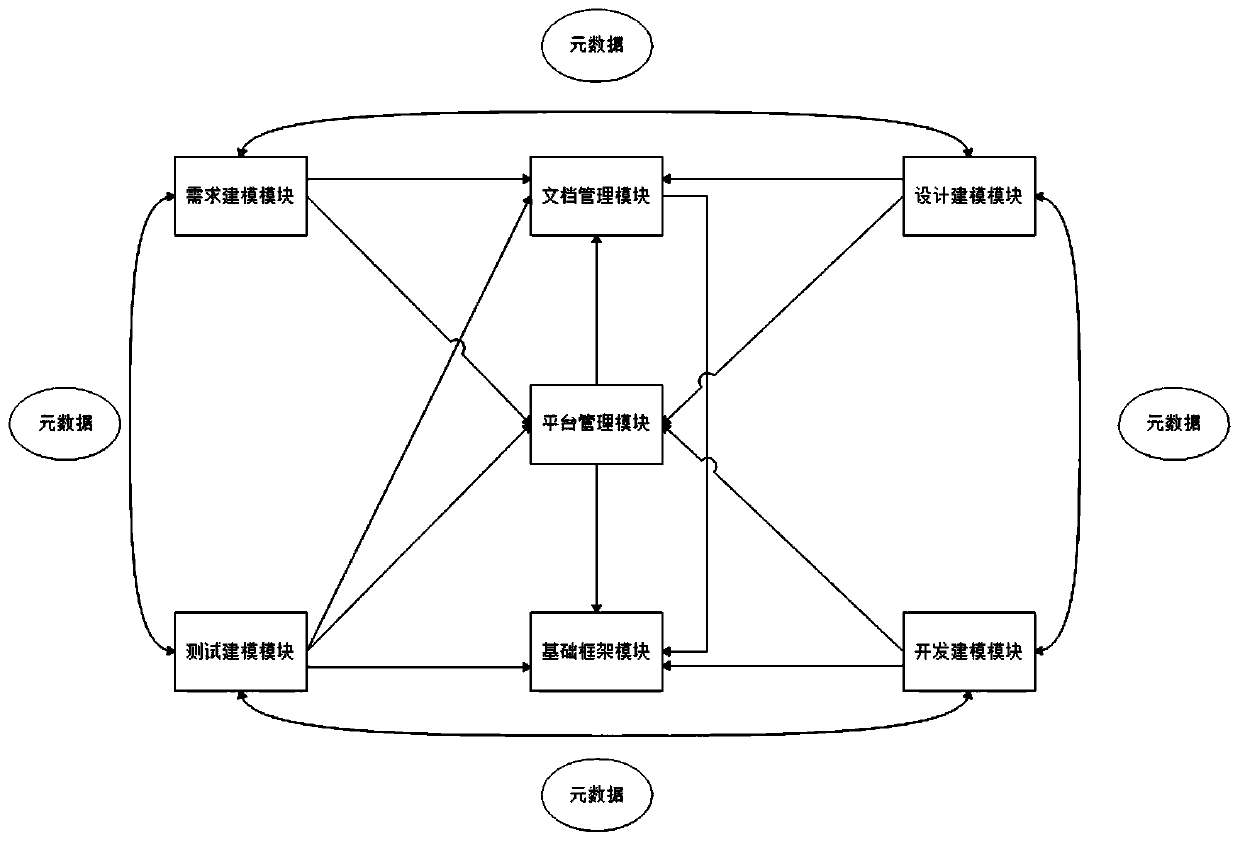
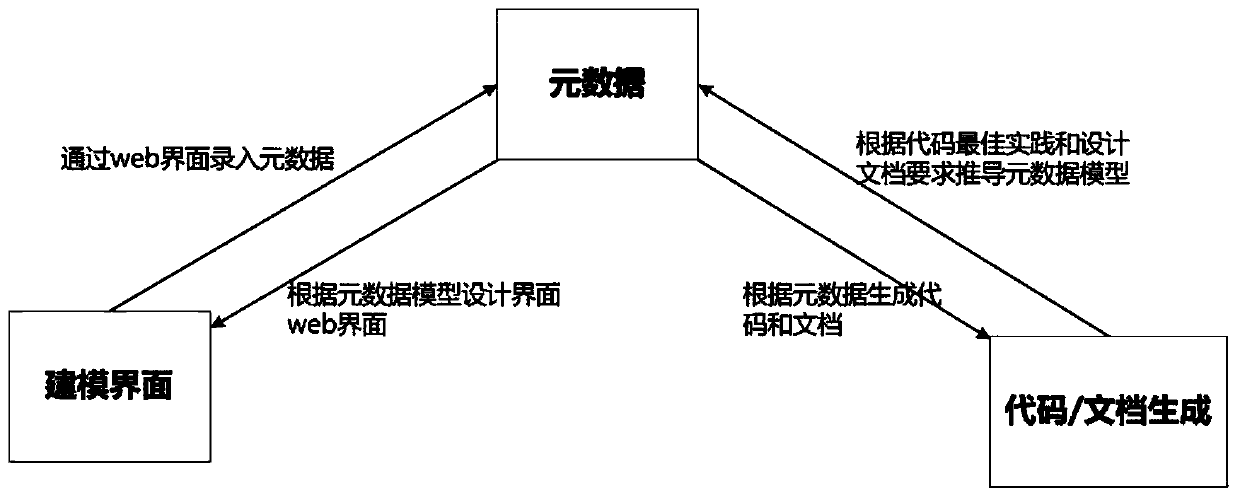
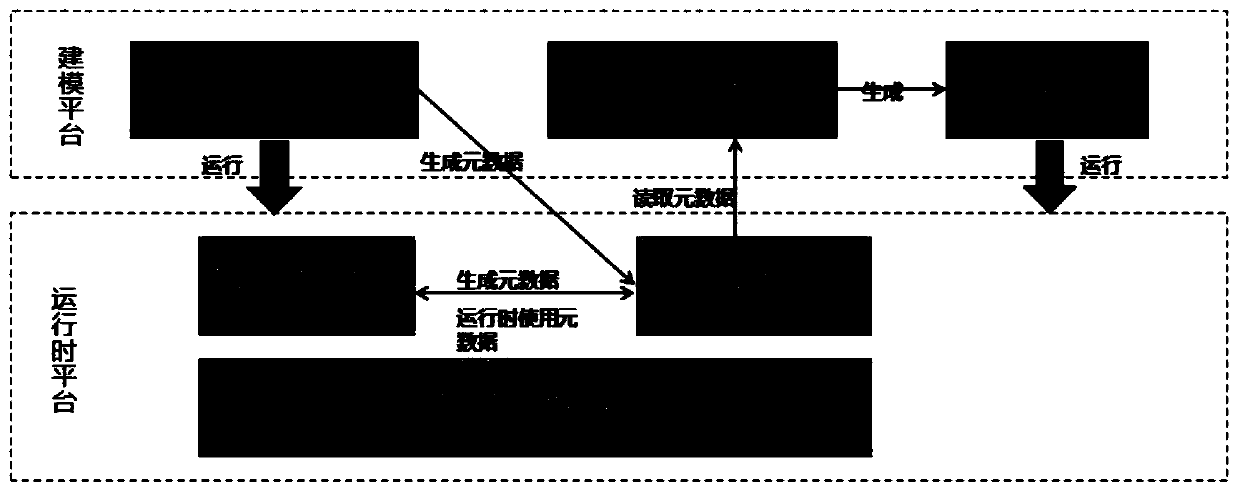
The invention provides a business application software development system and method, and the system is based on a model drive architecture (MDA) idea, and comprises a demand modeling module, a designmodeling module, a development modeling module, a test modeling module, a system management module, a basic framework module, and a document management module. Through the modules, the software development process comprises the steps of demand analysis, design, development and testing, the high-level models of all the steps are stored in a metadata mode and converted among all the steps, and through engineering model developed by software, an operation interface configured through visual modeling, and a standard practice template, one-key generation of operable target software is realized. According to the invention, the software development quality and efficiency are improved, and the professional knowledge requirements of software designers and the design difficulty of software development are reduced.
Owner:SHENZHEN COMTOP INFORMATION TECH
Value driving service software development method based on data map, information map and knowledge map framework
InactiveCN106990973ALow costSolve knowledge redundancySoftware designSpecific program execution arrangementsRequirements analysisDesign activities
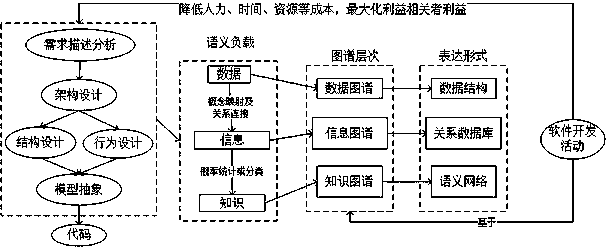
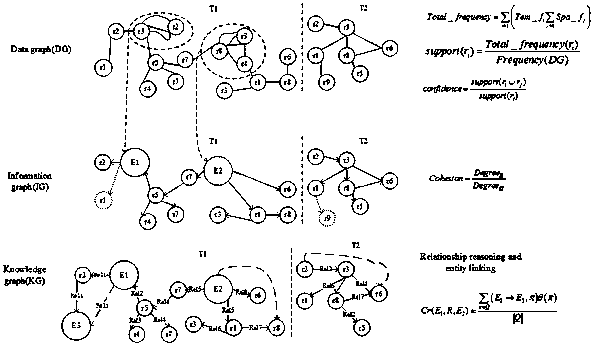
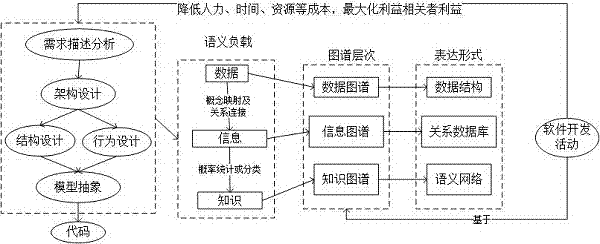
For challenge of an existing value driving data, information and knowledge life cycle evaluating method, the invention provides a value driving service software development method based on data map, information map and knowledge map framework aiming at the bidirectional evaluation and control over design action efficiency between the detailed design activity and service modeling, and belongs to the technical intersecting field of distributed computation and software engineering. On the basis of data maps, data observation and collection in software development activity demand analysis are analyzed. Information maps are used for solving the problem of incorrect information flow control and information loss in design activity. In demand modeling of the detailed design activity, and advantages, including completeness of demand expression and coverage range, of knowledge maps in demand expression compared with UML are elaborated.
Owner:HAINAN UNIVERSITY
Method and device for analyzing test coverage automatically aiming at automatic test system
InactiveCN101894058AImprove work efficiencyImprove accuracyDetecting faulty computer hardwareDemand modelingAutomatic testing
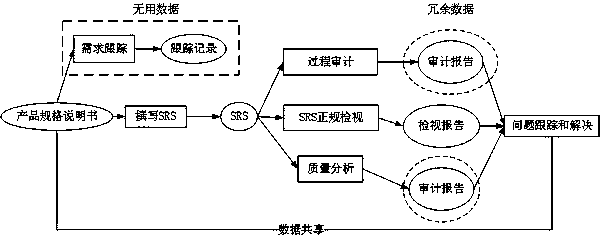
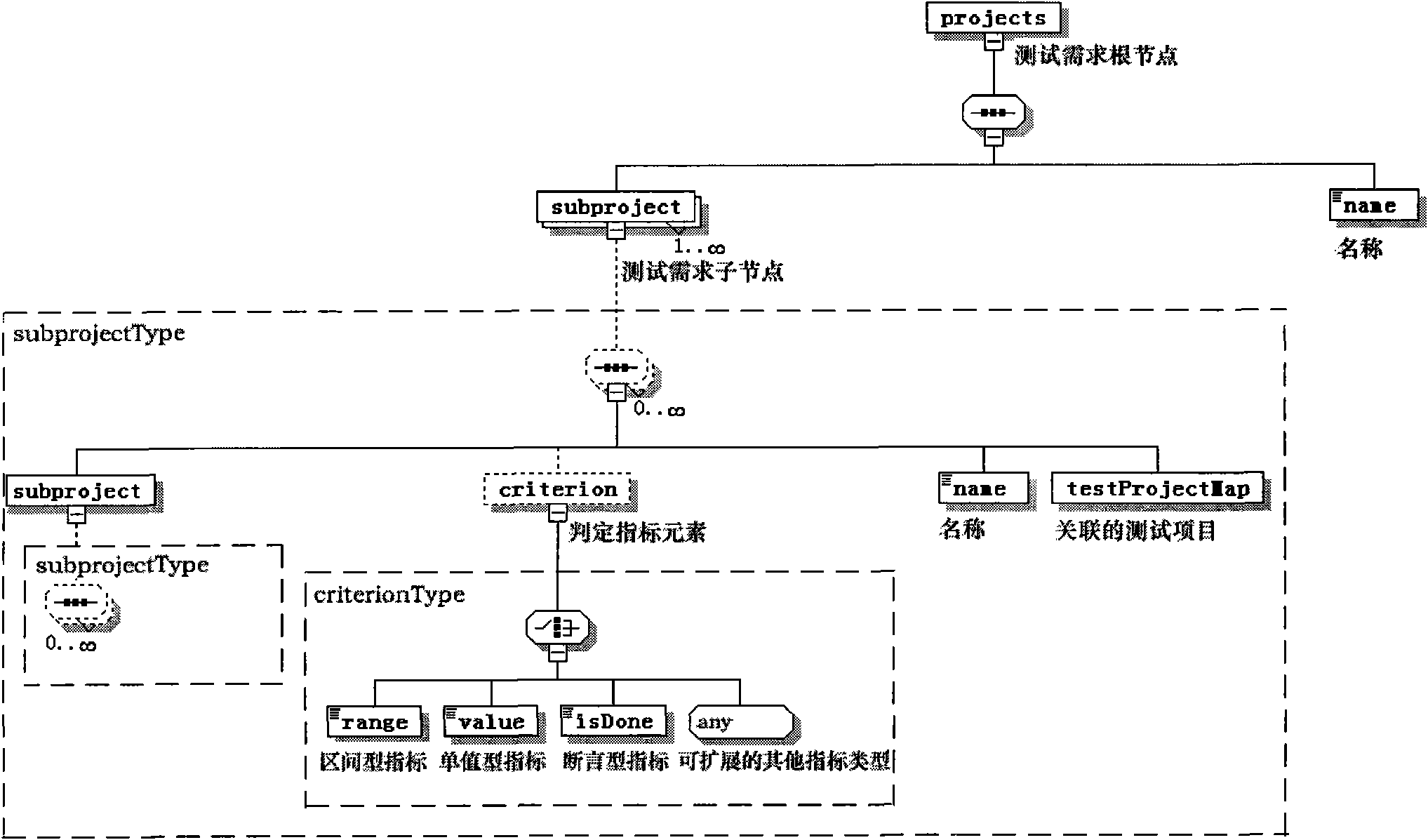
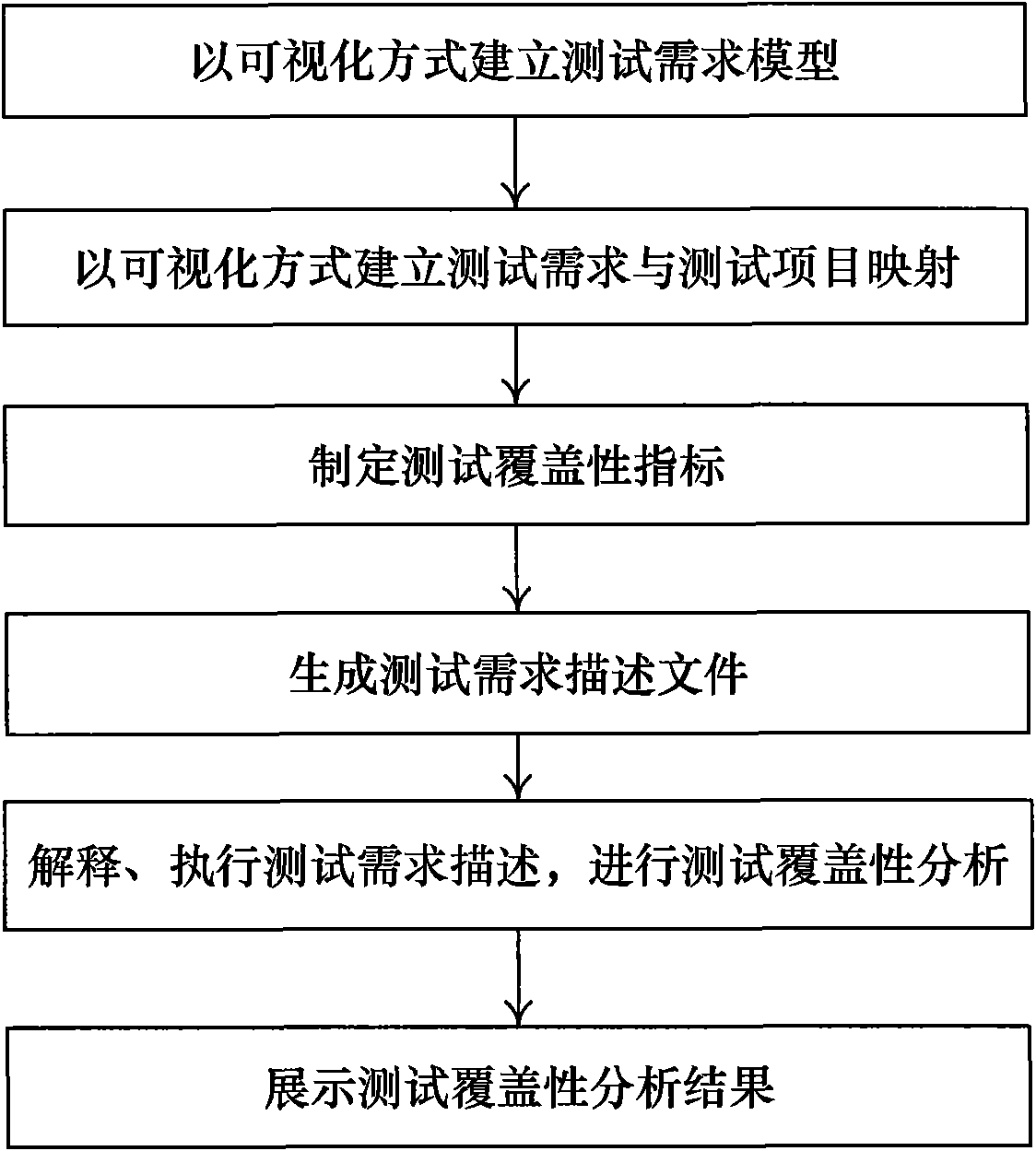
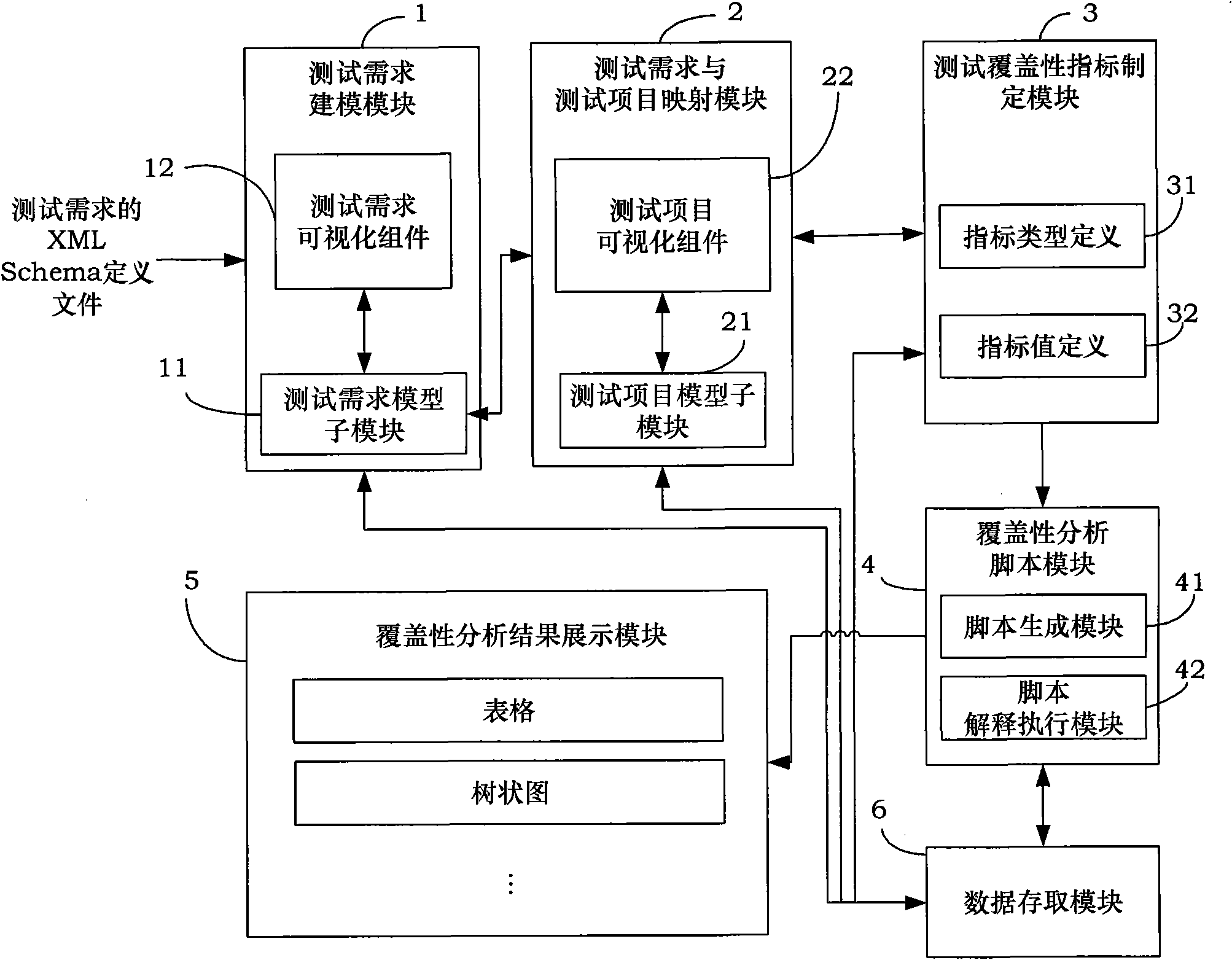
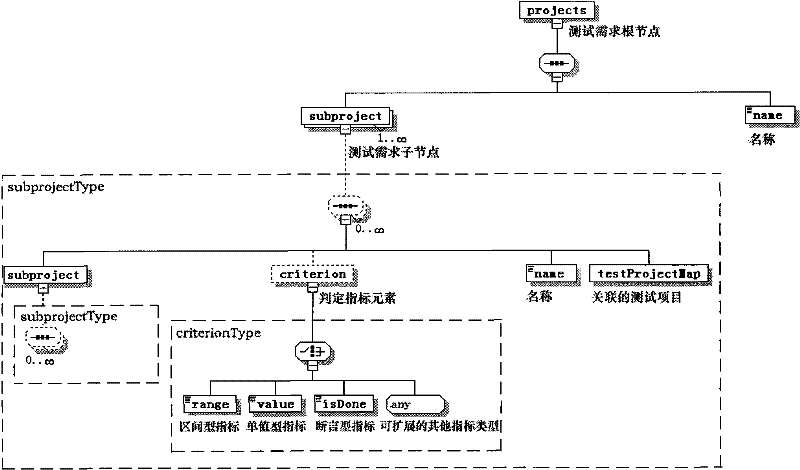
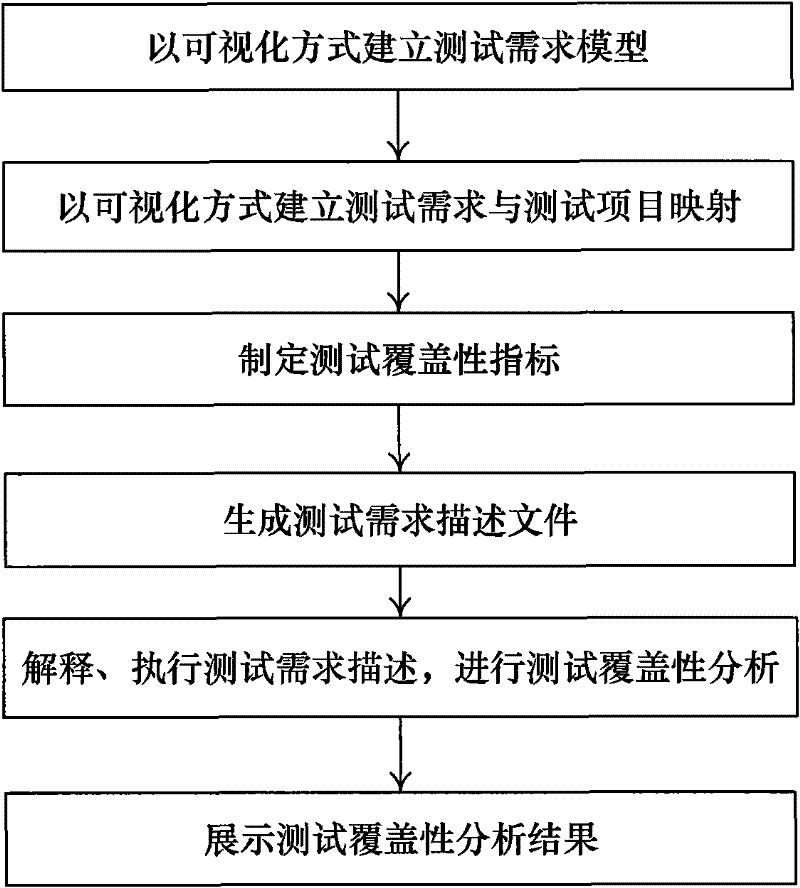
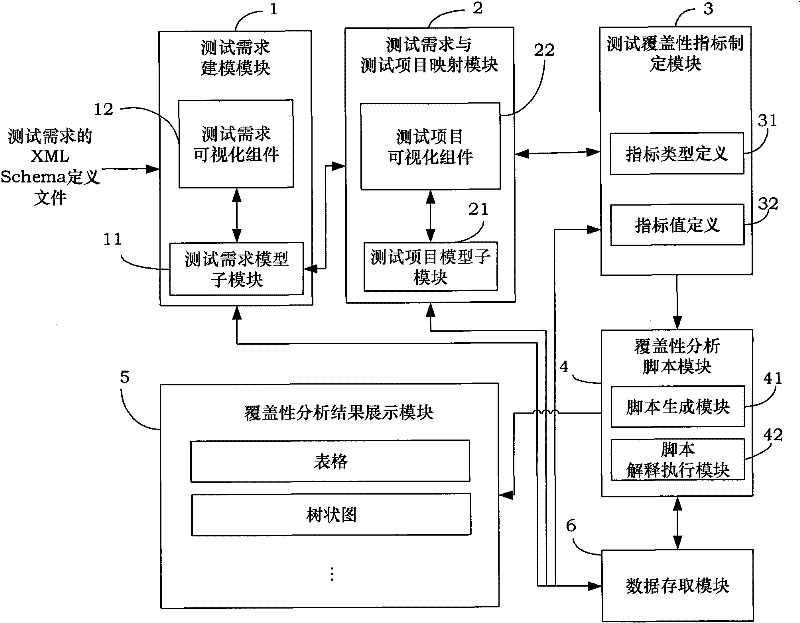
The invention provides a method and a device for analyzing test coverage automatically aiming at an automatic test system. The method for analyzing the test coverage automatically mainly comprises the following steps of: establishing a test demand model through visualization; formulating the mapping relation of test items and test demands and test coverage indexes by users; converting the test demand model into a test demand description XML file; and finally, resolving the file to analyze the test coverage. The device for analyzing the test coverage automatically mainly comprises a test demand modeling module, a test demand and test item mapping module, a test coverage index formulating module, a coverage analysis script module and the like, supports the visual modeling on the XML test demands, establishes the mapping relation of the test items and the test demands and the test coverage indexes, and realizes the automatic analysis of the test coverage. The method and the device can assist analysts in analyzing the test coverage automatically and improve working efficiency and the accuracy of analytical results, and the adopted visual operation is simple, quick and convenient.
Owner:BEIHANG UNIV
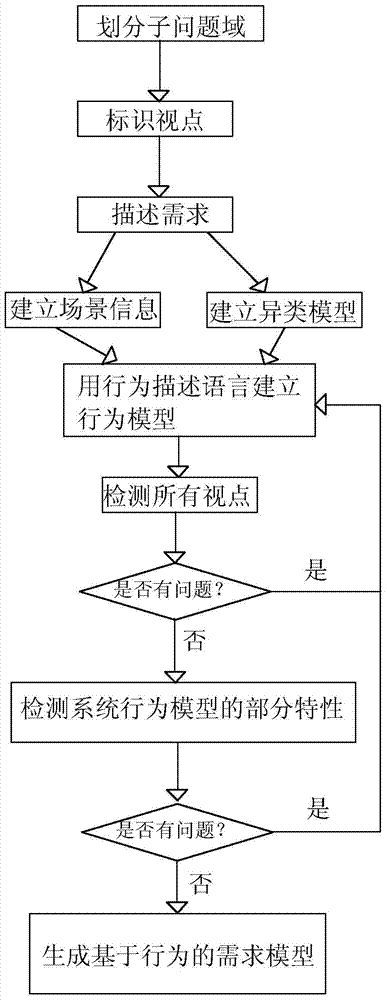
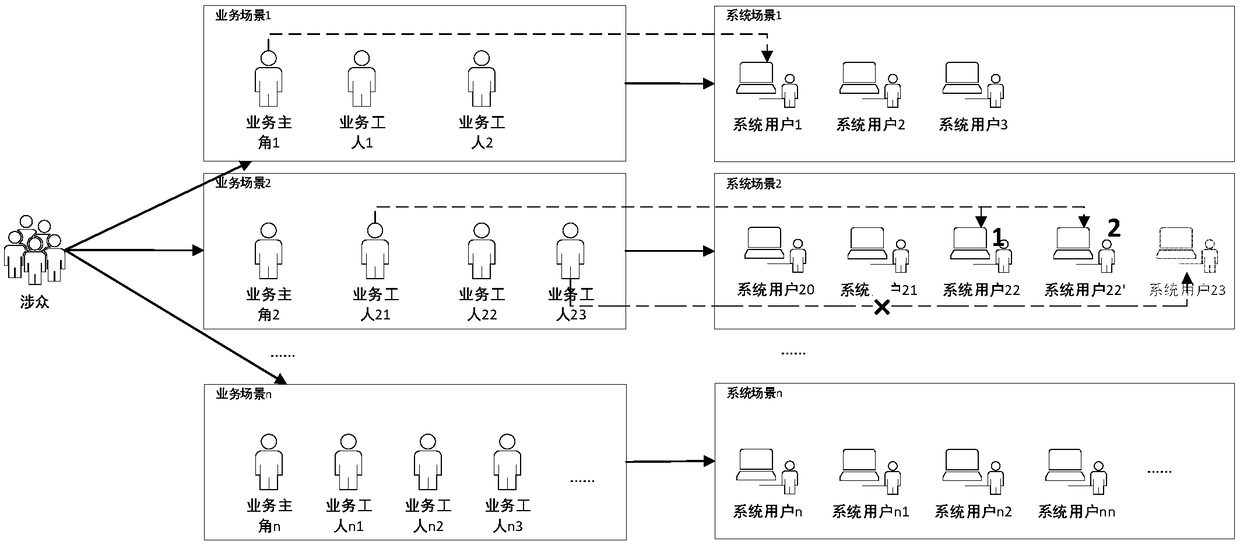
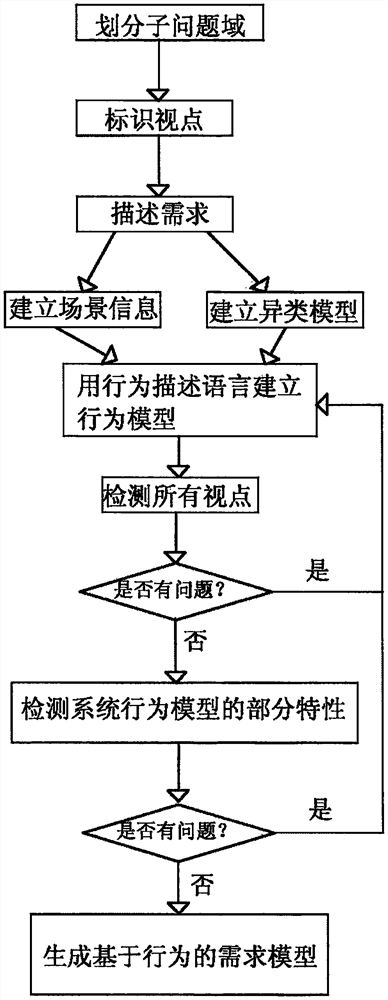
Scene-based demand modeling system and method, and information data processing terminal
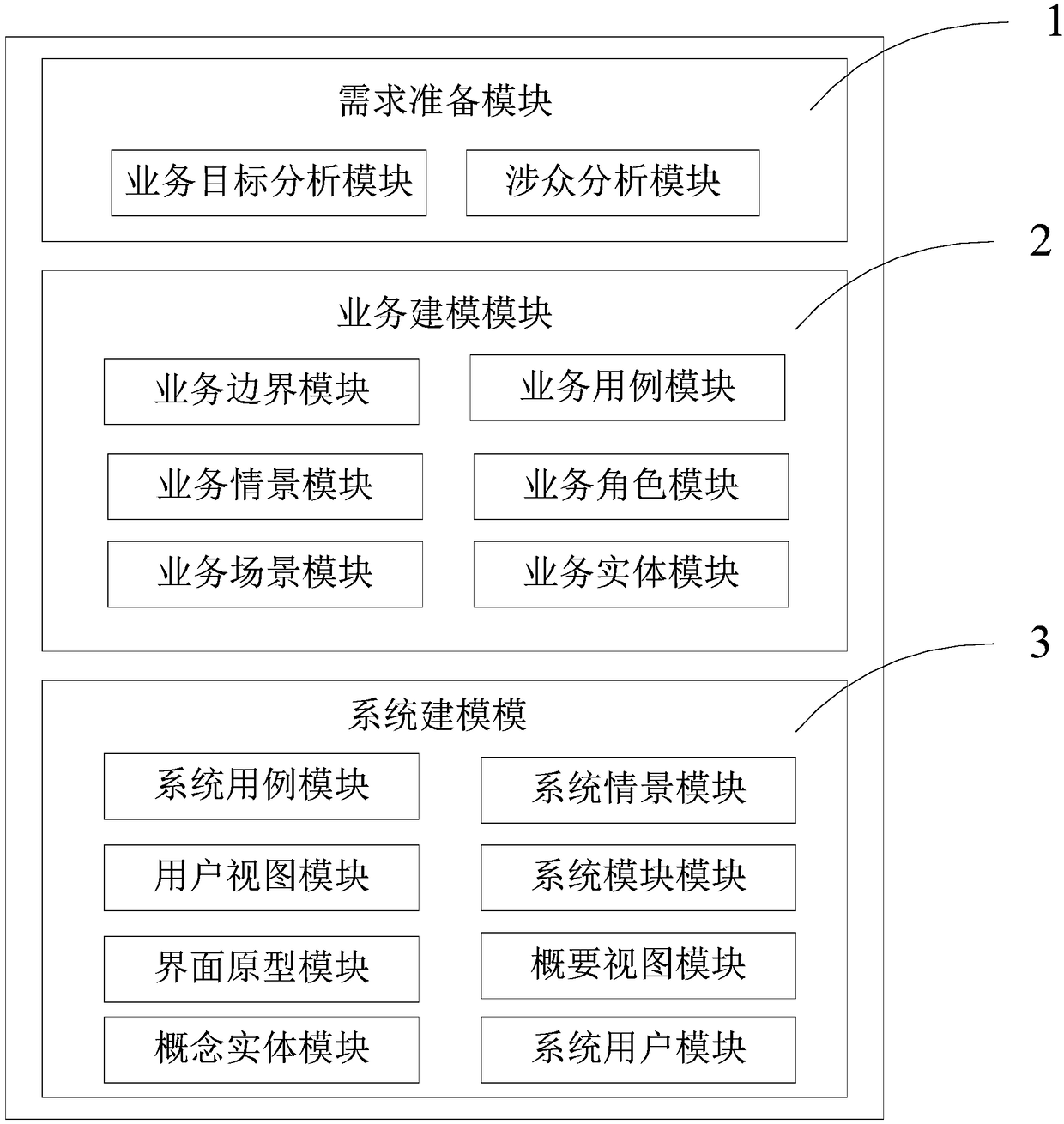
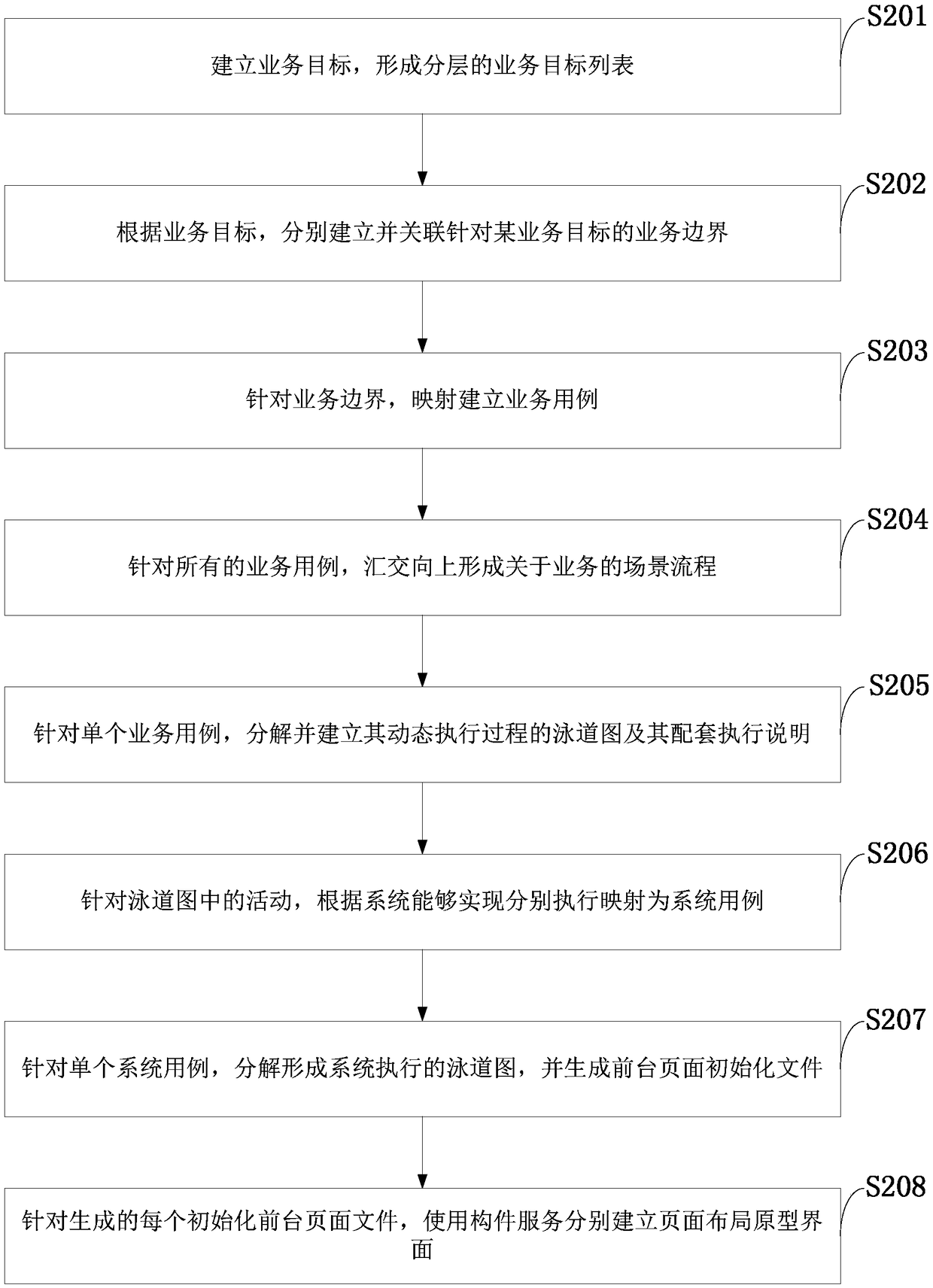
The invention belongs to the technical field of devices for executing special programs, and discloses a scene-based demand modeling system and method, and an information data processing terminal, andthe system comprises a demand preparation module, a business modeling module, and a system modeling module. According to the method, the process of converting the business document and the report intothe business entity is realized, and the business entity forms a derivation clue of the conceptual entity with the association relationship through analysis; the crowd analysis derives and converts from a business scene to a business role, and the business role derives an evolution line of the system user from the computer execution angle; a step-by-step basis, derivation and evolution are provided for transition from service current situation description to computerized description.
Owner:CHENGDU UNIV OF INFORMATION TECH
Individualized travel information screening method matching user characteristics
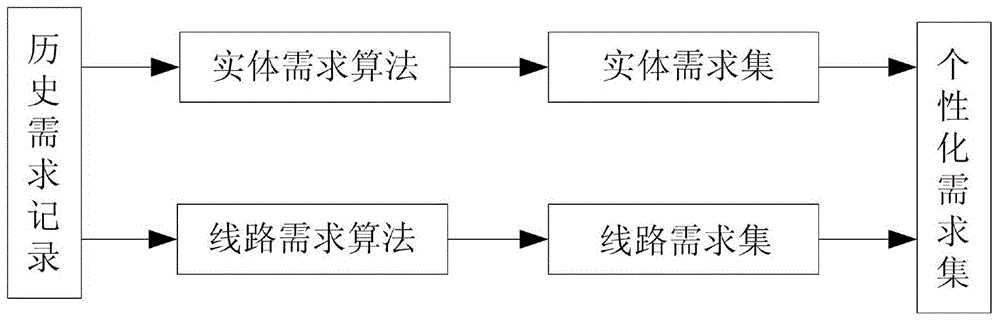
InactiveCN104965883ASmall individual needsMeet individual needsRelational databasesSpecial data processing applicationsPersonalizationGranularity
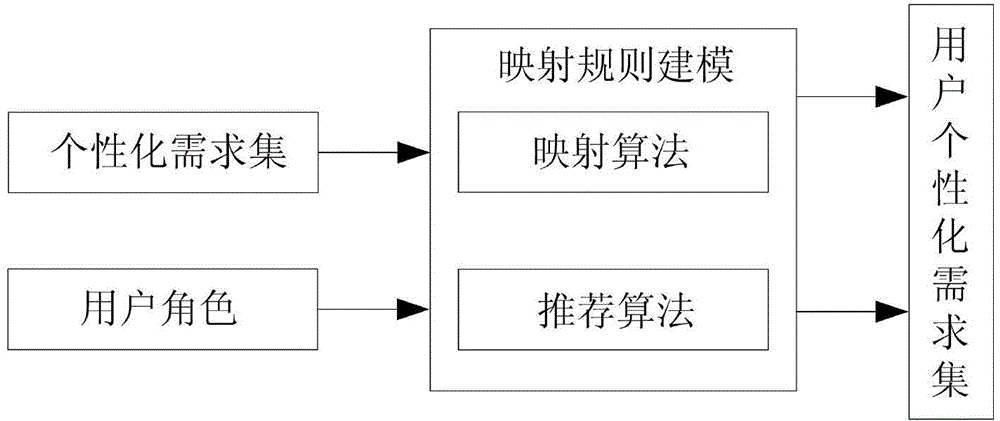
The invention provides an individualized travel information screening method matching user characteristics. The individualized travel information screening method comprises individualized demand modeling and mapping rule modeling. The individualized requirement modeling comprises entity demand modeling and line demand modeling, wherein the entity demand modeling adopts a two-layer granularity classification method to carry out classification processing on entity demand parameters and the line demand modeling adopts a three-layer granularity classification method to carry out classification processing on all line demands. The mapping rule modeling comprises a mapping algorithm and a recommended algorithm. According to the individualized travel information screening method provided by the invention, an individualized algorithm matching the user characteristics is designed to aim at the characteristics that the total user quantity of travel industries is great, the total historical data quantity is abundant, the single user data quantity is small and the like: after a user logs in a system, no parameters are needed to be input; and travel services which are the most needed can be initiatively recommended to the user according to the user characteristics, so that the individualized demands of the user are satisfied and a lot of time of the user is shortened.
Owner:HAINAN UNIVERSITY
Spot market profit optimization system
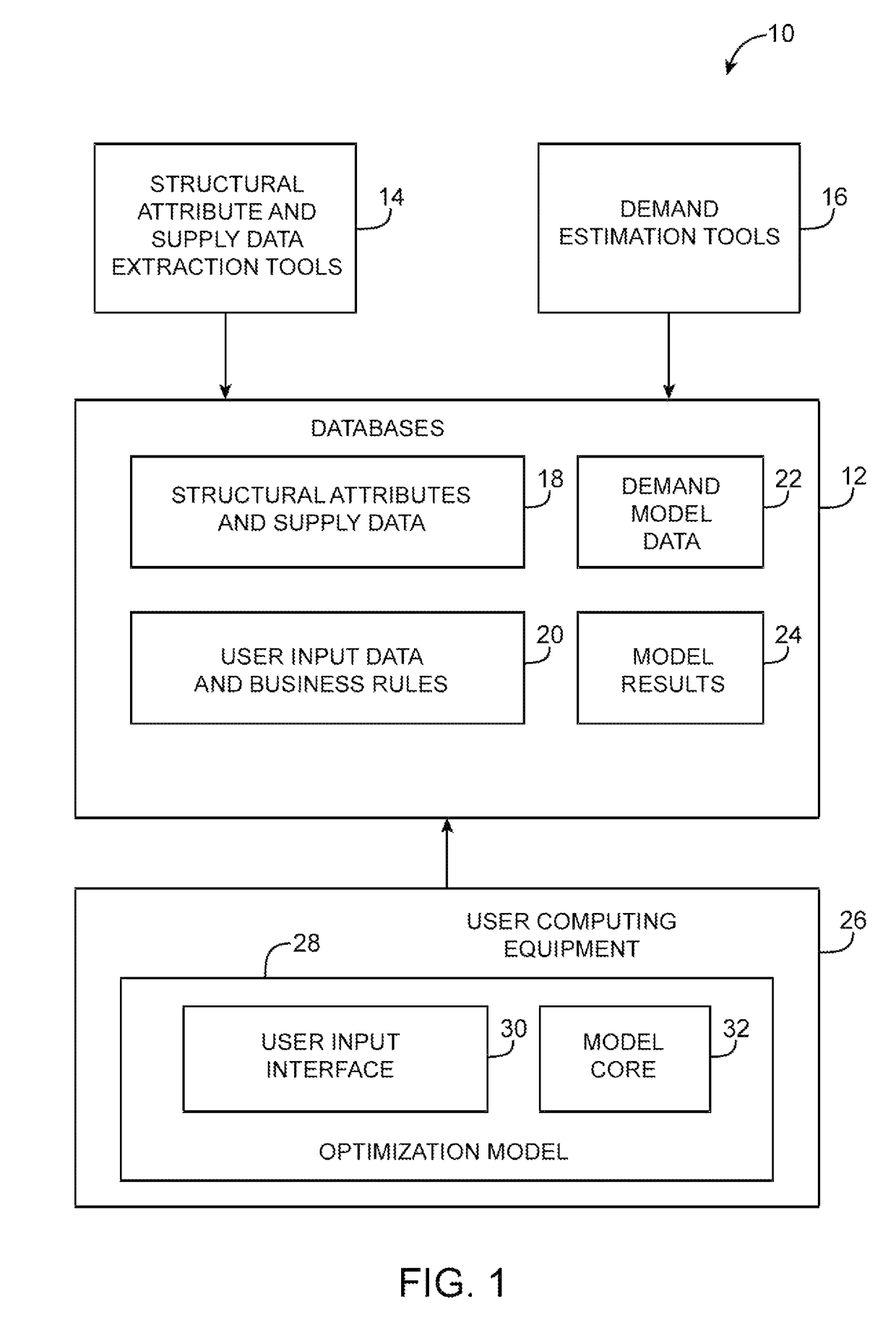
A profit optimization system takes account of supply-side and demand-side factors in optimizing profit for an organization. The profit optimization system uses an optimization model to optimize profit in a spot market. The model takes into account which parts the organization uses to assemble various products. Demand curves are used to characterize the quantity of each product that will be demanded as a function of price on the spot market. Supply model data is used to determine which mix of products can be sold in view of parts availability. Using the demand model and supply model data, the optimization model can recommend a set of prices to use for selling the organization's products. The model ensures that the organization has sufficient resources available to produce the products and enforces user-supplied business rules and other constraints.
Owner:PROS
Element multi-dimensional frequency correlation calculation-based semantic modeling method for data mapping, information mapping and knowledge mapping frameworks
InactiveCN107092705AMaximize profitabilityLow costSpecial data processing applicationsText database clustering/classificationSoftware developmentLabeled data
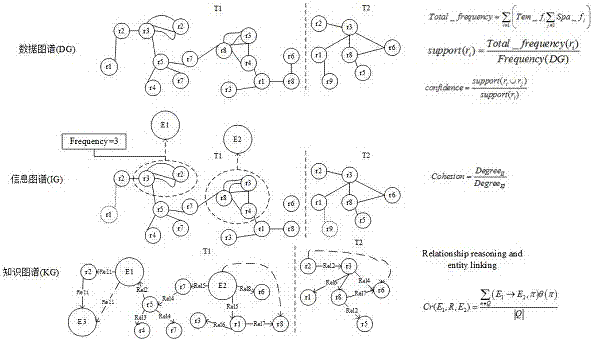
In order to improve the economic benefit and obtain maximum values of benefit enhancement and strategic investment practice from efficiency enhancement and strategic investment practice, the invention discloses an element multi-dimensional frequency correlation calculation-based semantic modeling method for data mapping, information mapping and knowledge mapping frameworks, and belongs to the technological cross fields of distributed computation and software engineering. According to the method, data observation and collection in software development activity demand analysis are analyzed on the basis of data mappings, and structure frequencies, time frequencies and space frequencies of data are marked. According to the method, information mappings are used for recording the frequencies of interactions between entities, and the problems of incorrect information flow control and information loss in design activities are solved. In demand modeling of detailed design activities, the method disclosed by the invention states the advantage of knowledge mappings relative to UML in the aspect of demand expression, such as integrity and coverage area of semantic expressions in the demands.
Owner:HAINAN UNIVERSITY
Information privacy protection method based on data map, information map and knowledge map
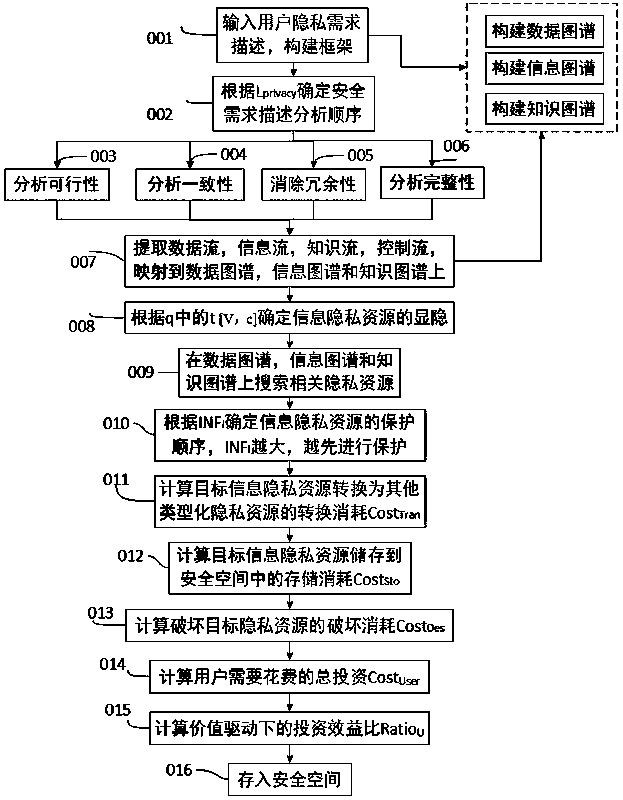
InactiveCN108804945AImprove consistencyImprove integrityDigital data protectionKnowledge representationUser needsData stream
The invention relates to a typed resource demand modeling and information resource privacy protection method based on a data map, an information map and a knowledge map, and belongs to the field of intersection of distributed calculation and software engineering. The typed resource demand modeling and information resource privacy protection method is mainly used for carrying out feasibility analysis, integrity analysis, consistency analysis and redundancy analysis on a demand of a user and extracting corresponding data stream, information stream, knowledge stream and control stream in each step of analysis to map to the data map, the information map and the knowledge map. Then, on the basis of the demand of the user, information resources are classified into implicit and explicit cases according to existence of the information resources in a search space; and for implicit and explicit information privacy resources, the information privacy resources are converted into other types of privacy resources according to a sequence of influence sizes and all the related typed privacy resources are stored into a security space to carry out protection.
Owner:HAINAN UNIVERSITY
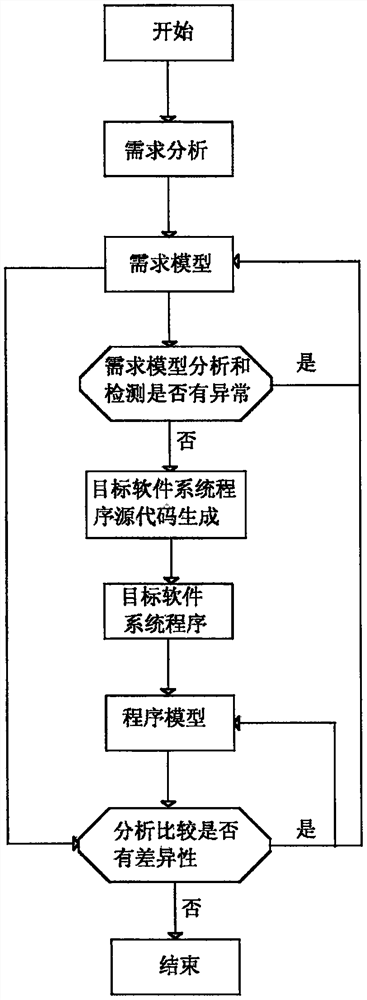
Development method of embedded software system program
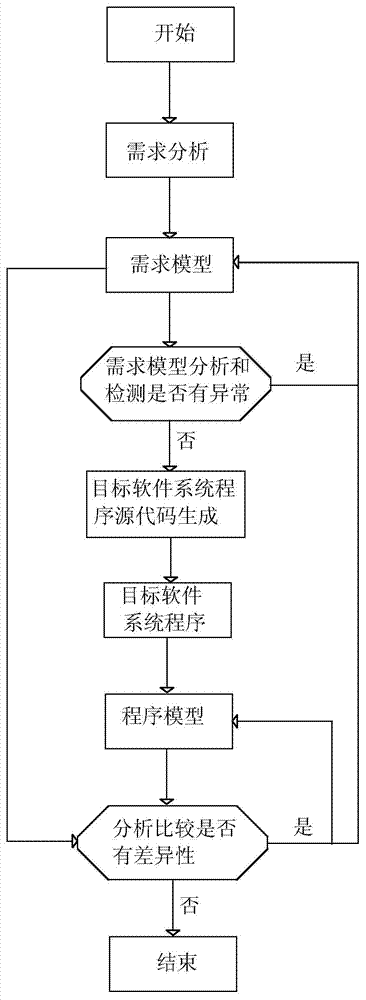
InactiveCN104216703AReduce the difficulty of requirement modelingIncrease productivitySpecific program execution arrangementsRequirements modelSoftware system
The invention relates to a development method of an embedded software system program. The development method comprises the steps of analyzing and establishing a demand model of the embedded system program to be developed according to the demand of the embedded software system program; analyzing and detecting the demand model, and simultaneously generating a source code required by a target software system program, and thus generating the target software system program; analyzing the target software system program to obtain a program model, comparing and analyzing the program model and the demand model to discover the difference, if the difference is discovered, repairing the generated target software system program or demand module. The demand modeling technical scheme suitable for the embedded software system program is provided for the characteristics of the embedded software system program, so that the demand for natural language expression of users is converted into scene and behavioral expression, and a good foundation is laid for whether the demand for automatically detecting a software system is accurate or complete.
Owner:SHENZHEN RES INST OF WUHAN UNIVERISTY
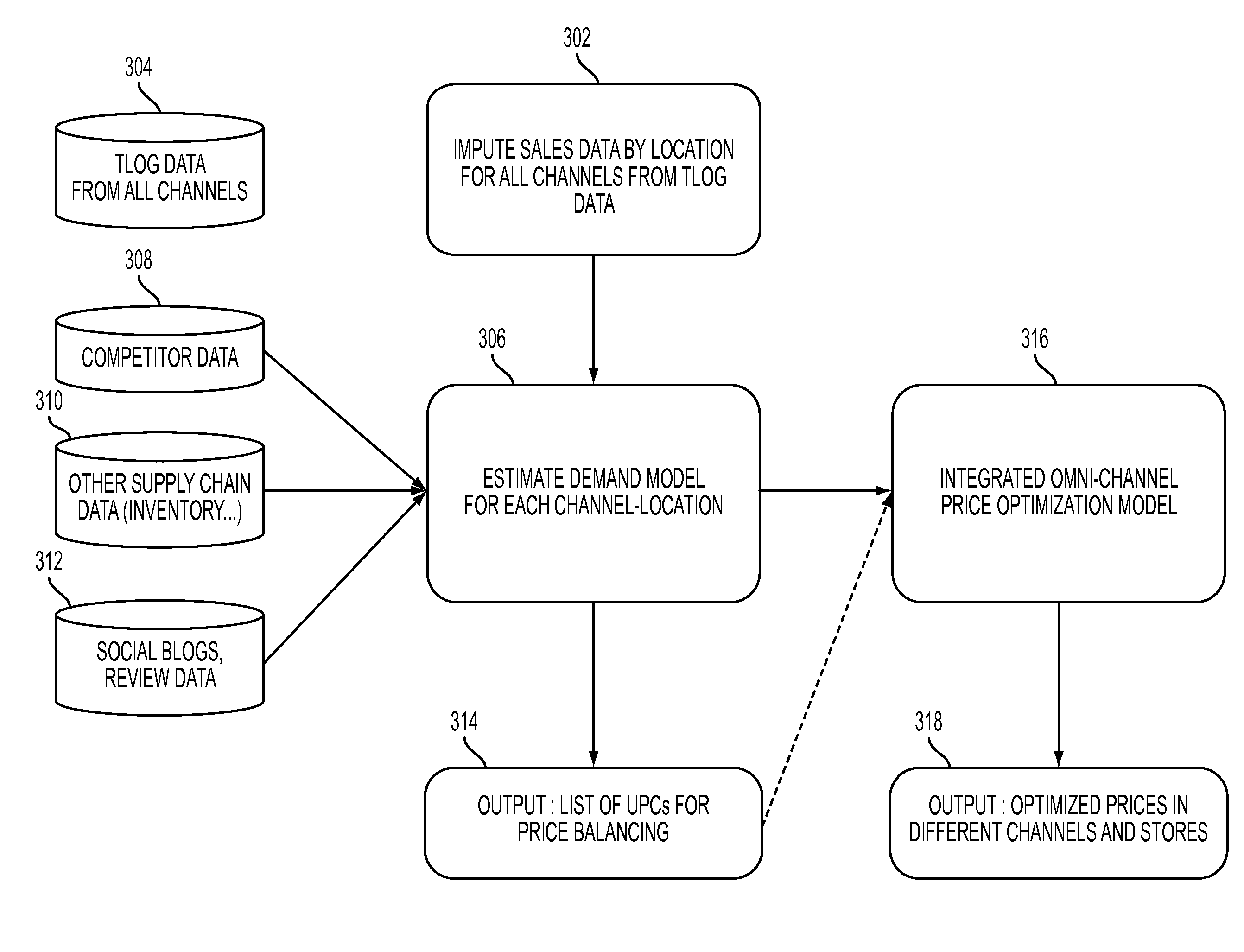
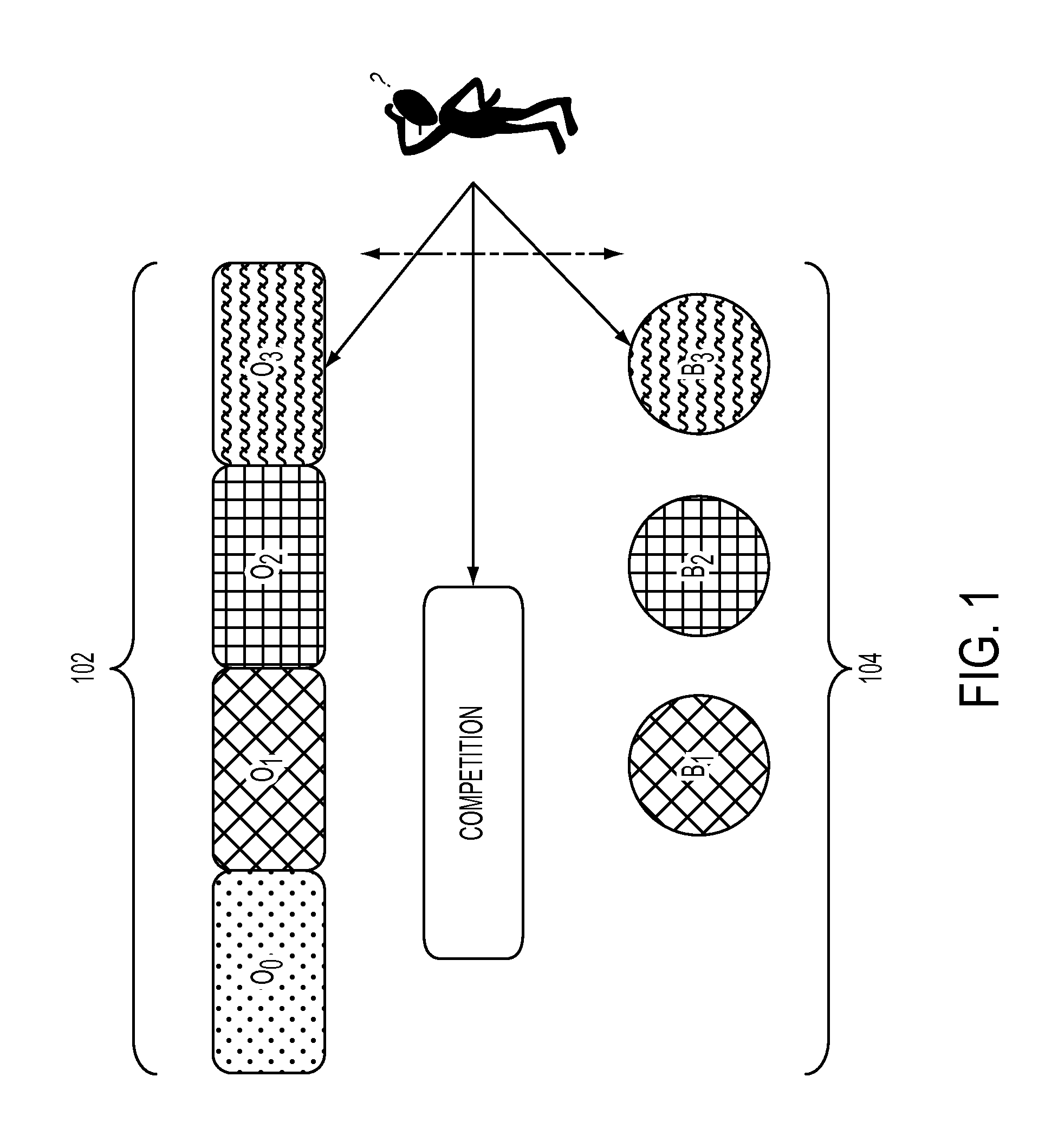
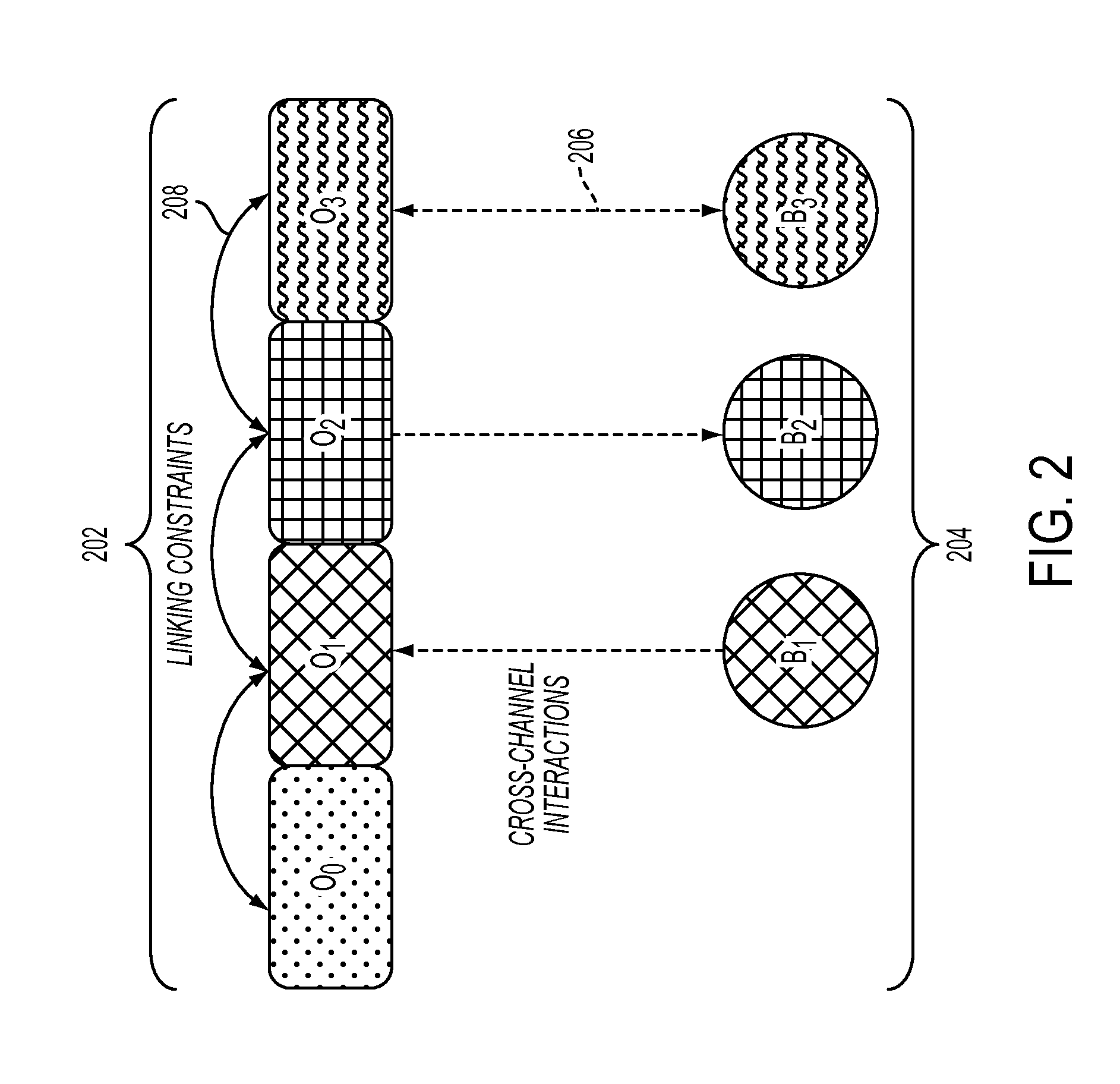
Omni-channel demand modeling and price optimization
Predicting demand of a product offered in multiple channels for a seller that has a plurality of physical store channels and one or more virtual channels, may comprise obtaining transaction log data having records of sales transactions with location identifiers in the one or more virtual channels. The one or more virtual channels may be segmented by locations based on locations of the physical stores and the location identifiers in the transaction log data. A demand model may be estimated by location that incorporates demand for the multiple channels in that location and captures cross-effect of said multiple channels in the same location based on historic sales and transaction data. Integrated price optimization may be performed across all channels and locations that compute one or more prices for each virtual channel and one price for each location in the other channels while also satisfying a plurality of inter-channel and inter-locations constraints.
Owner:IBM CORP
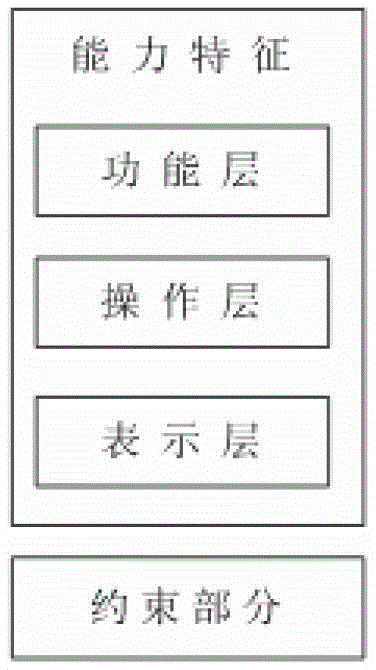
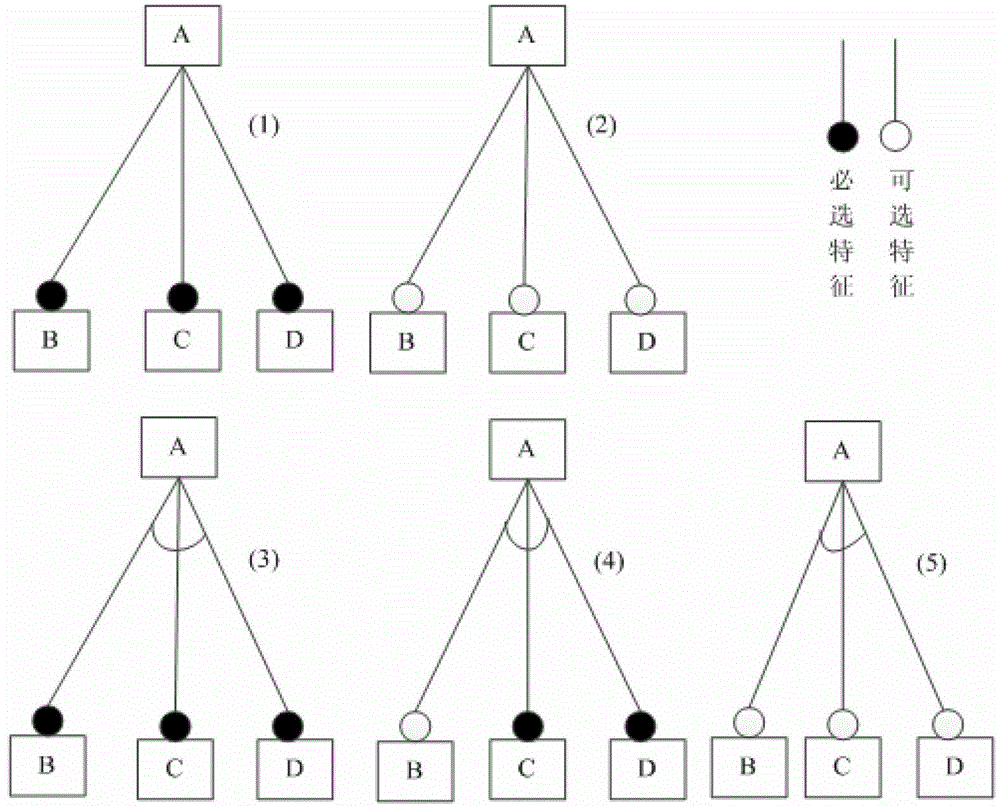
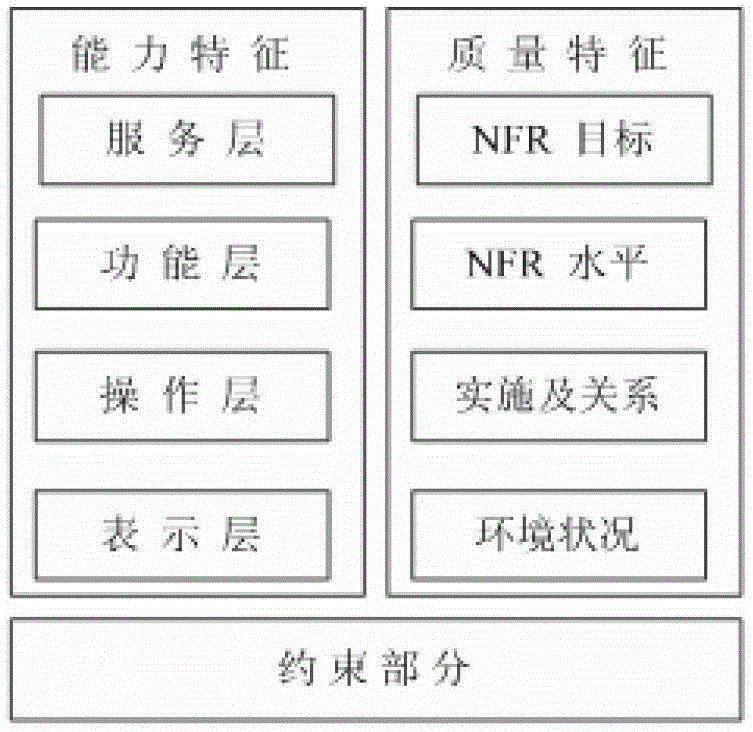
Requirement modeling method based on new characteristic model and model transformation method
ActiveCN103164230AResolve ambiguityDetailed featuresSpecific program execution arrangementsRequirements modelAlgorithm
The invention discloses a requirement modeling method based on a new characteristic model and a model transformation method. A model is established by the new characteristic model through a hierarchical structure of expansion of ability characteristics along with addition of a 'service layer' and a quality characteristic with addition of four hierarchical structures. Five types of conditions of the characteristic model are simplified to two types of conditions through introduction of a 'selectable set'. A requirement modeling technological process is designed according to the new characteristic model. A characteristic pattern is converted into a unified modeling language (UM) class pattern and a UML case using pattern. The requirement modeling method based on the new characteristic model is capable of greatly promoting reusability of software requirement assets and improving production efficiency and quality of software. The model transformation method is joined with the requirement modeling method based on the characteristic model and a UML pattern modeling method.
Owner:XIDIAN UNIV
Software quality demand modeling and inference method
InactiveCN103399740AEasy to storeEasy to editSpecific program execution arrangementsSemanticsDemand modeling
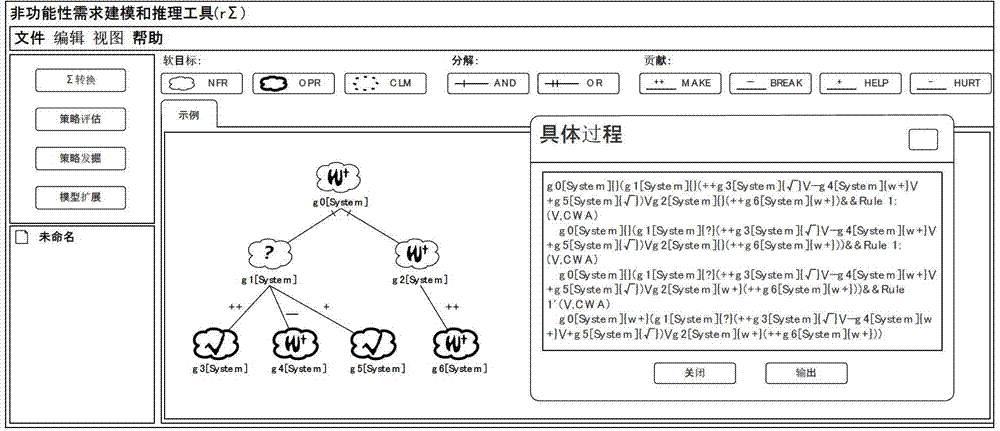
The invention provides a software quality demand modeling and inference method which is used for providing software quality demand oriented formalized modeling, automatic inference and an analysis platform r sigma. The method includes the following steps: setting a related concept, performing graphical modeling, clicking an r sigma drawing area, selecting a corresponding modeling element, clicking a canvas to generate the corresponding modeling element, performing formalized modeling, designing according to semantics and grammar of a target modeling language sigma orienting to software quality demand, performing strategy assessment to determine whether an implementation strategy is an acceptable strategy or not, performing strategy exploration to check all possible combinations of design options and classify strategies according to satisfied states of root nodes, and performing model extension to capture incidence relations among different modeling results. By the method, quality demand modeling results in a text format can be generated; no man-machine interaction is needed; in addition, multi-objective decisions of a quality demand implementation strategy are supported, and mutual dependent relationships among models can be captured.
Owner:PEKING UNIV
Field demand modeling method and device for driving open ecological cloud ERP
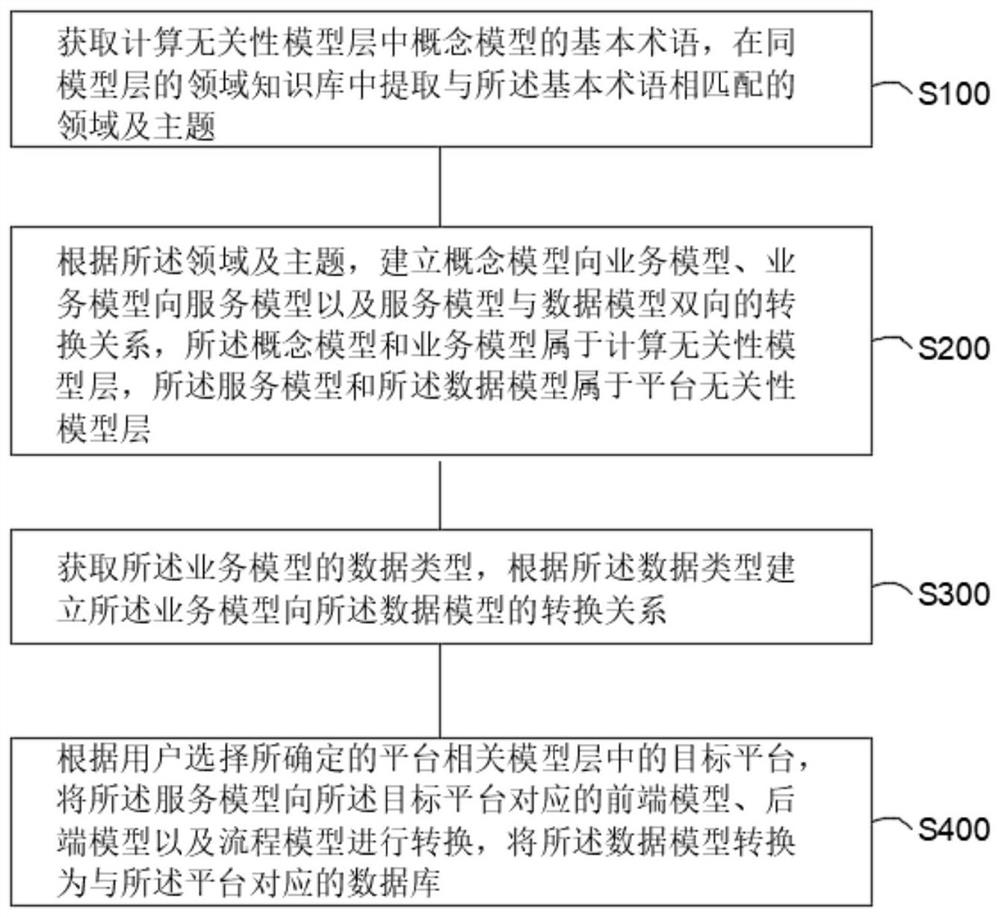
PendingCN113190212ASolve the real problemBreak down "barriers"Software designRequirement analysisService modelEngineering
The invention relates to the technical field of cloud native platform services, in particular to a field demand modeling method and device for driving an open ecological cloud ERP, and the method comprises the steps: obtaining basic terms, and extracting fields and themes from a field knowledge base; according to the field and the theme, establishing a bidirectional conversion relation from a conceptual model to a business model, from the business model to a service model and from the service model to a data model; acquiring a data type of a business model, and establishing a conversion relation from the business model to the data model; and determining a target platform, converting the service model into a front-end model, a rear-end model and a process model, and converting the data model into a database corresponding to the platform, thereby solving the problems existing in a traditional ERP system, breaking the barrier between enterprises, and enabling the ERP system to enter a more open and interconnected ecological system.
Owner:深圳易伙科技有限责任公司
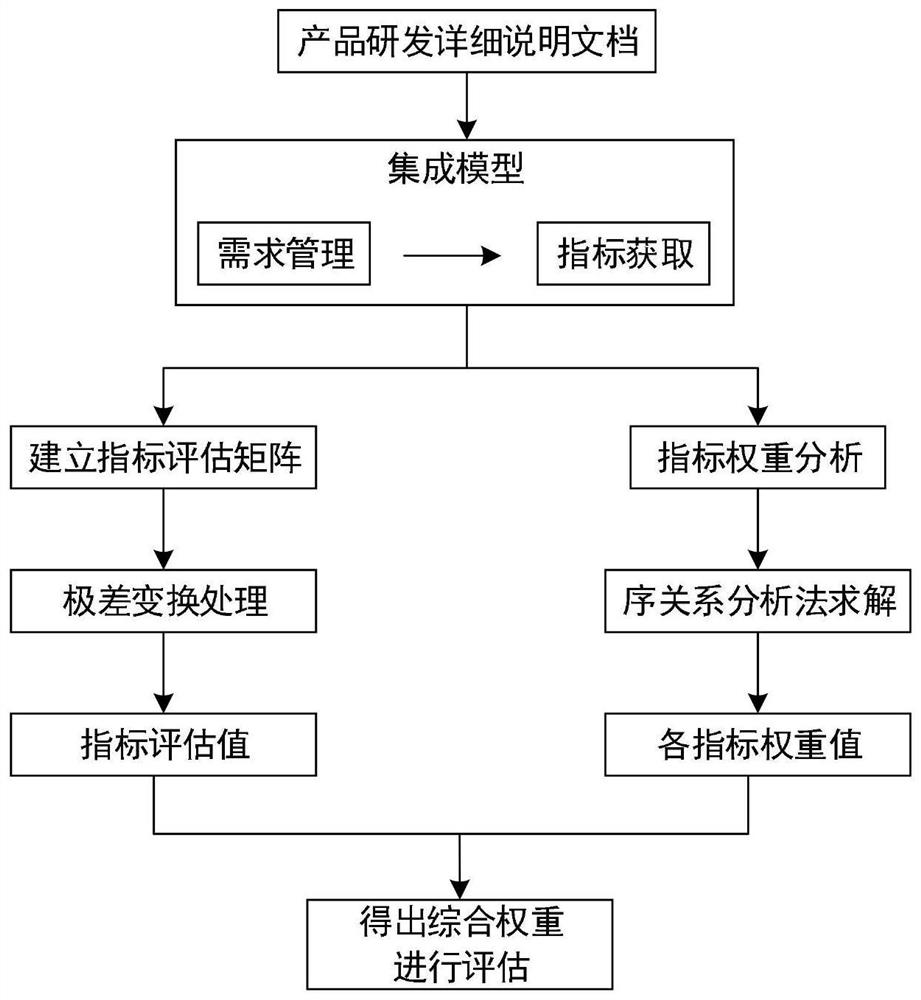
Product scheme multi-index evaluation method considering order relation analysis
The invention discloses a product scheme multi-index evaluation method considering order relation analysis. The method comprises the following steps: firstly, collecting a data source, establishing a traceable relationship between demands of a demand model, and controllably transmitting the demands; carrying out functional decomposition on the demand model until multifunctional indexes which can be used for scheme design by designers are obtained; According to the invention, a multi-index weight evaluation design scheme is adopted, an index evaluation matrix is established, normalization processing is carried out to eliminate non-university, an order relation analysis method is adopted to solve index weights, and a comprehensive evaluation value of each scheme is calculated. According to the method, innovative demand modeling and analysis specifications can be formed in product research and development, scheme evaluation can be simply and quickly carried out in the initial stage of product scheme design, and many practical problems which cannot be evaluated from the technical level can be conveniently solved.
Owner:HANGZHOU DIANZI UNIV
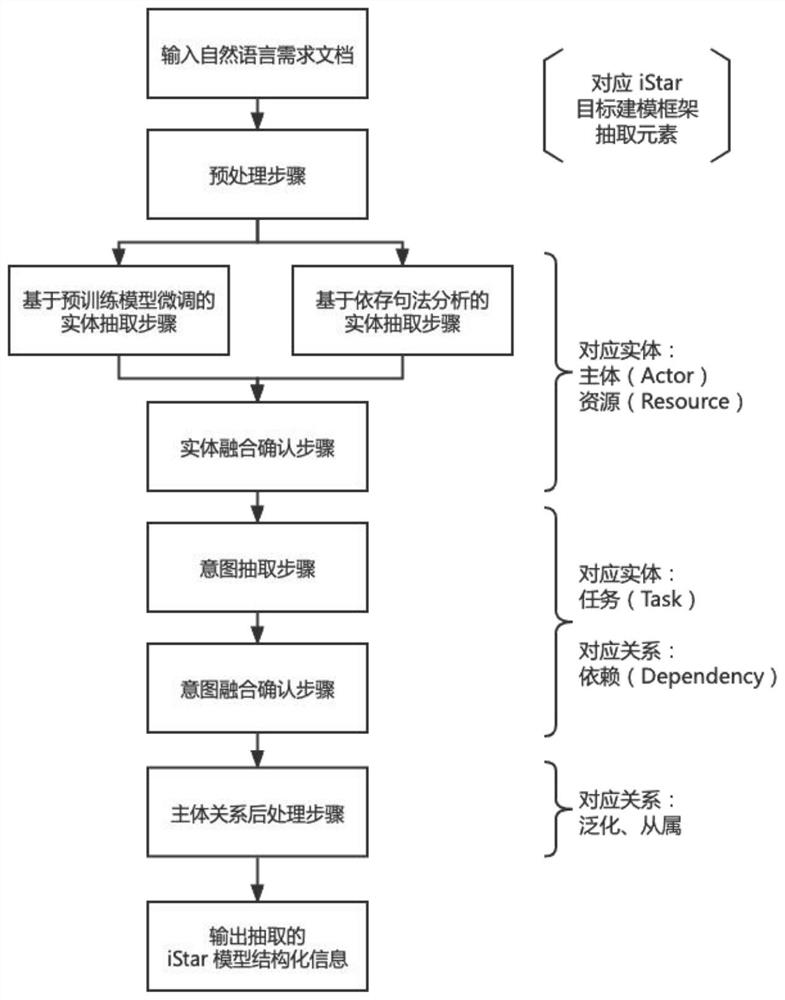
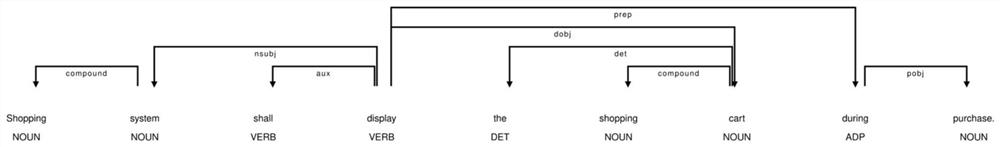
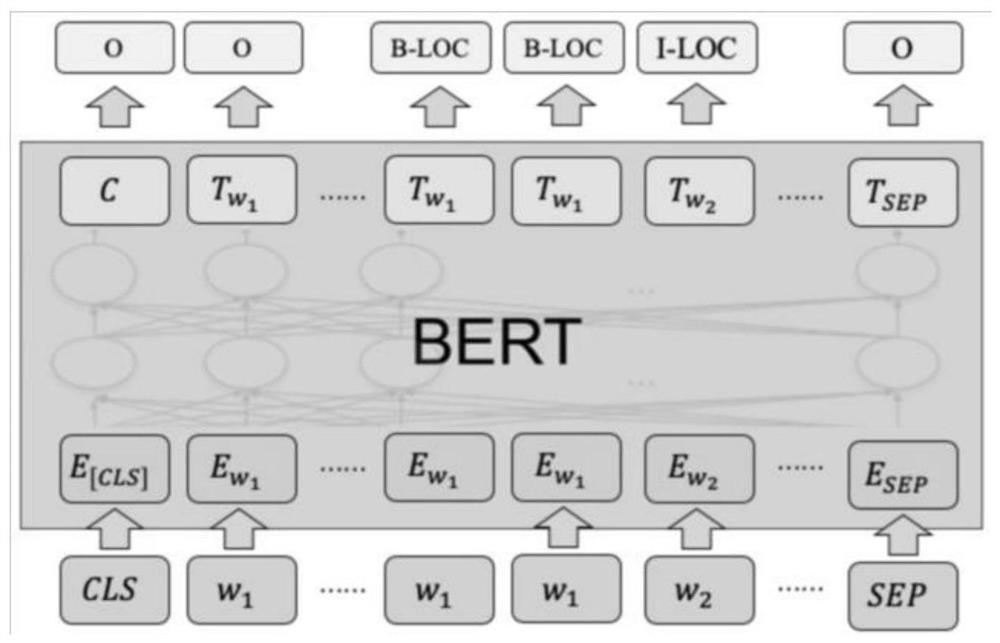
Semi-automatic demand extraction method based on pre-training language fine tuning and dependency features
PendingCN114217766AImprove interpretabilityImprove reliabilityDatabase management systemsNatural language data processingData setModelSim
The invention discloses a semi-automatic demand extraction method based on pre-training language fine tuning and dependency features. The semi-automatic demand extraction method comprises the following steps of preprocessing, entity extraction, entity fusion confirmation, intention extraction, intention fusion confirmation, subject relation post-processing and output modeling. According to the semi-automatic demand extraction method provided by the invention, the advantages of a pre-training language fine tuning model and dependency analysis characteristics are fused: on one hand, rules are designed for the field problem of software demand modeling, and the interpretability and reliability of the system are improved through field knowledge; and on the other hand, proper fine adjustment is performed by utilizing the generalization convenience of the pre-training language model, and additional large-scale data set labeling training cannot be paid for the accuracy premium.
Owner:BEIJING UNIV OF TECH
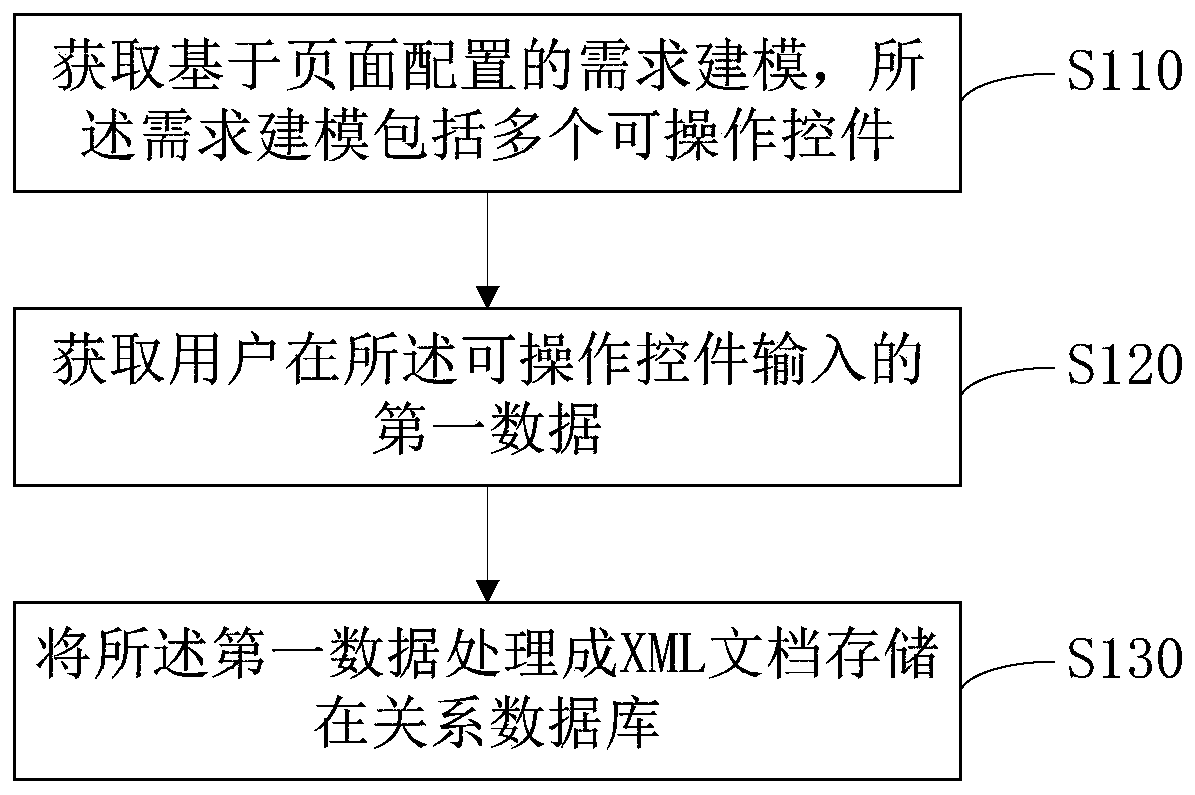
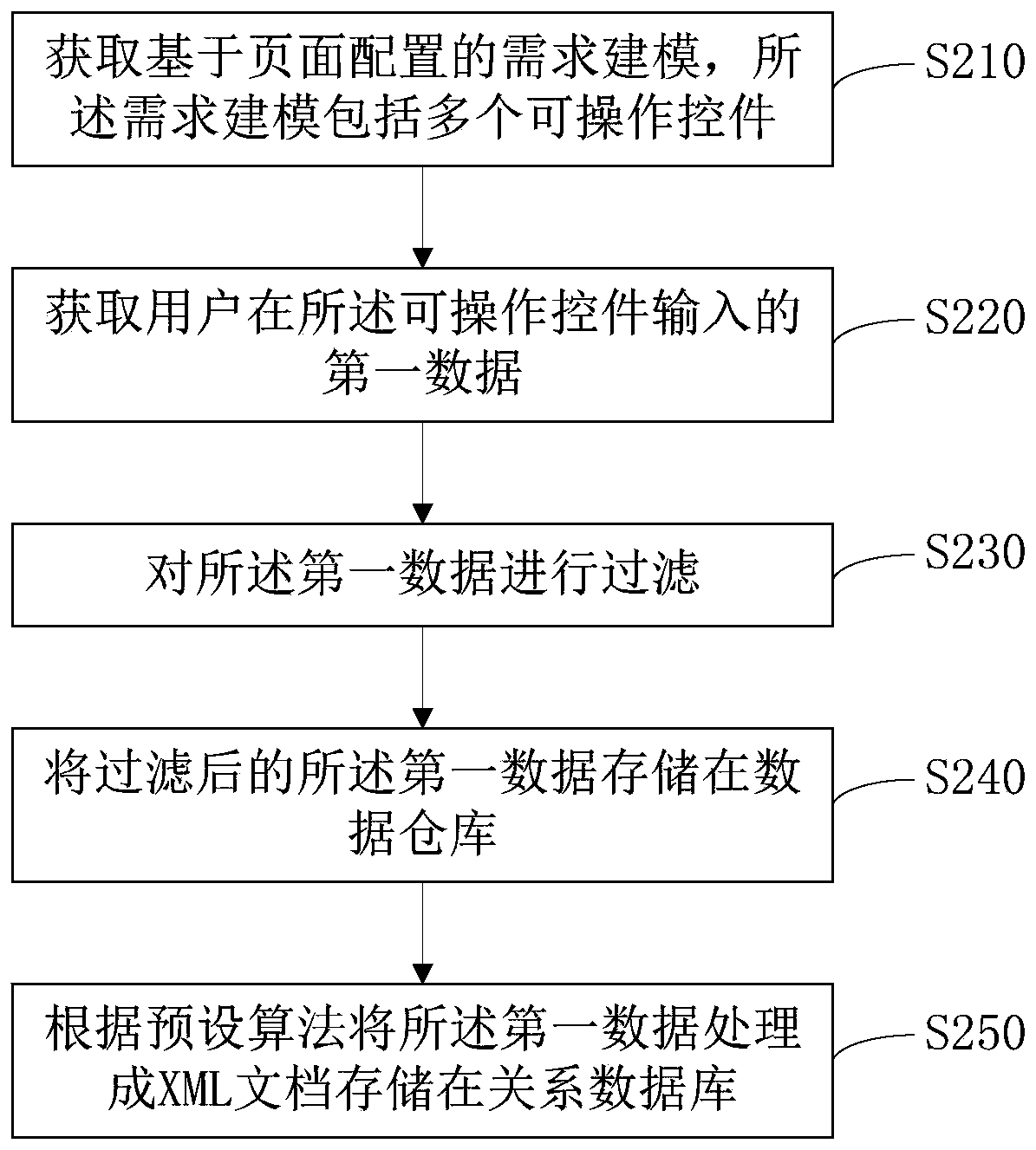
XML-based data association method and device, server and storage medium
ActiveCN110889013AIntuitive Data ServiceCompact Data ServiceRelational databasesSemi-structured data indexingRelational databaseDocumentation
The invention discloses an XML-based data association method and device, a server and a storage medium, and the method comprises the steps: obtaining demand modeling based on page configuration, wherein the demand modeling comprises a plurality of operable controls, the operable controls are connected to form a control chain, and the connection is a corresponding relation between data; obtaining first data input by a user in the operable control; and processing the first data into an XML document and storing the XML document in a relational database. According to the technical scheme, the effects of providing visual and concise data services for users and improving the modeling reuse rate are achieved.
Owner:RUN TECH CO LTD BEIJING
Hardware logic design-oriented demand modeling and verification method
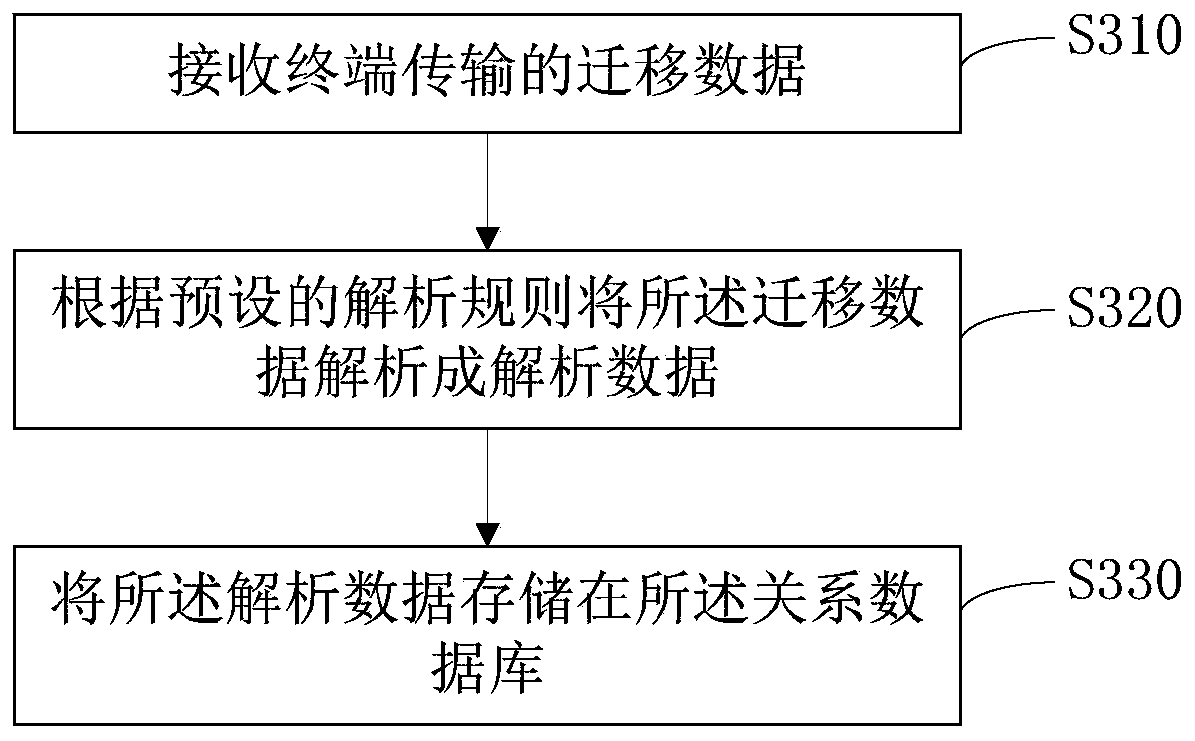
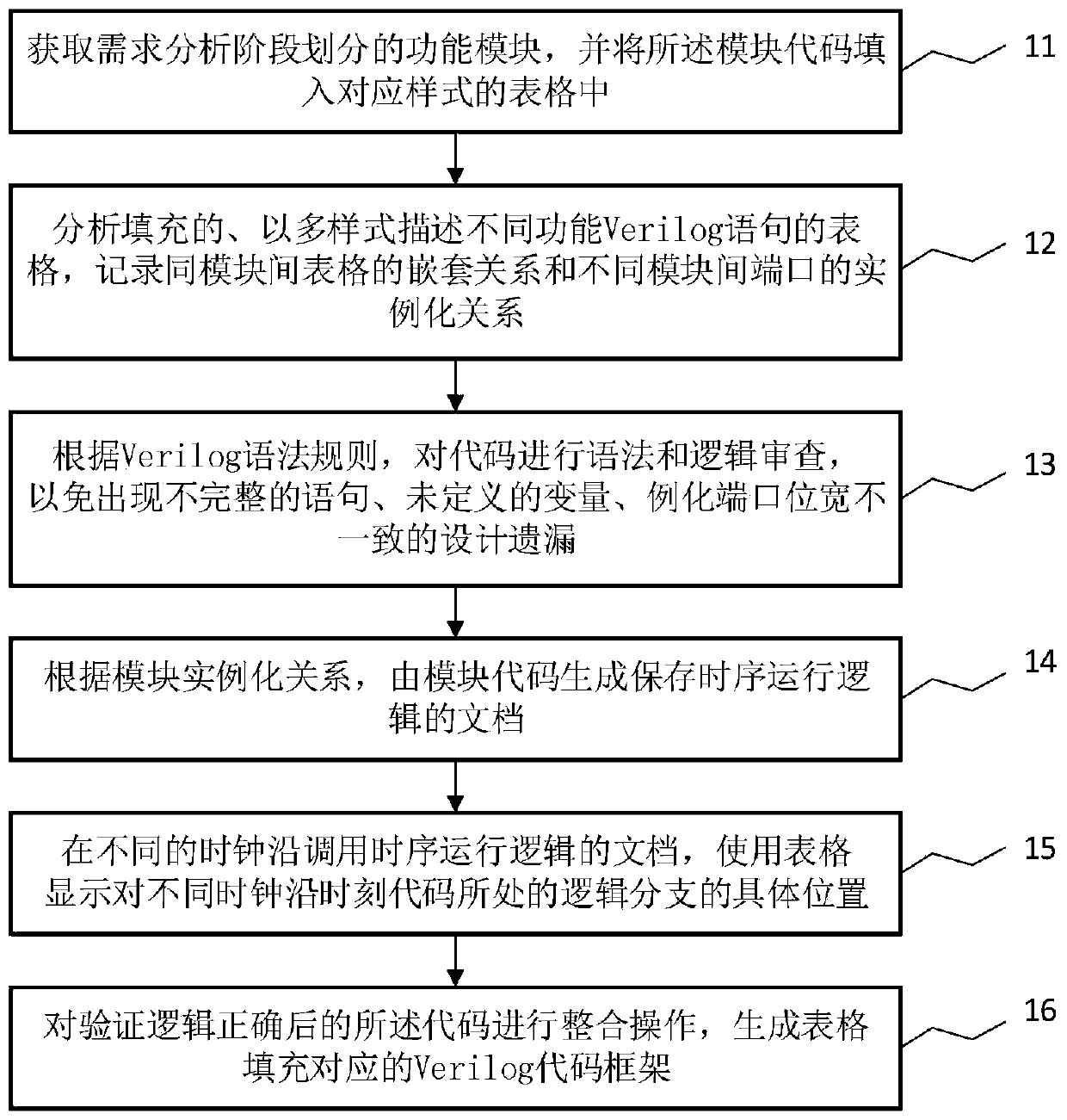
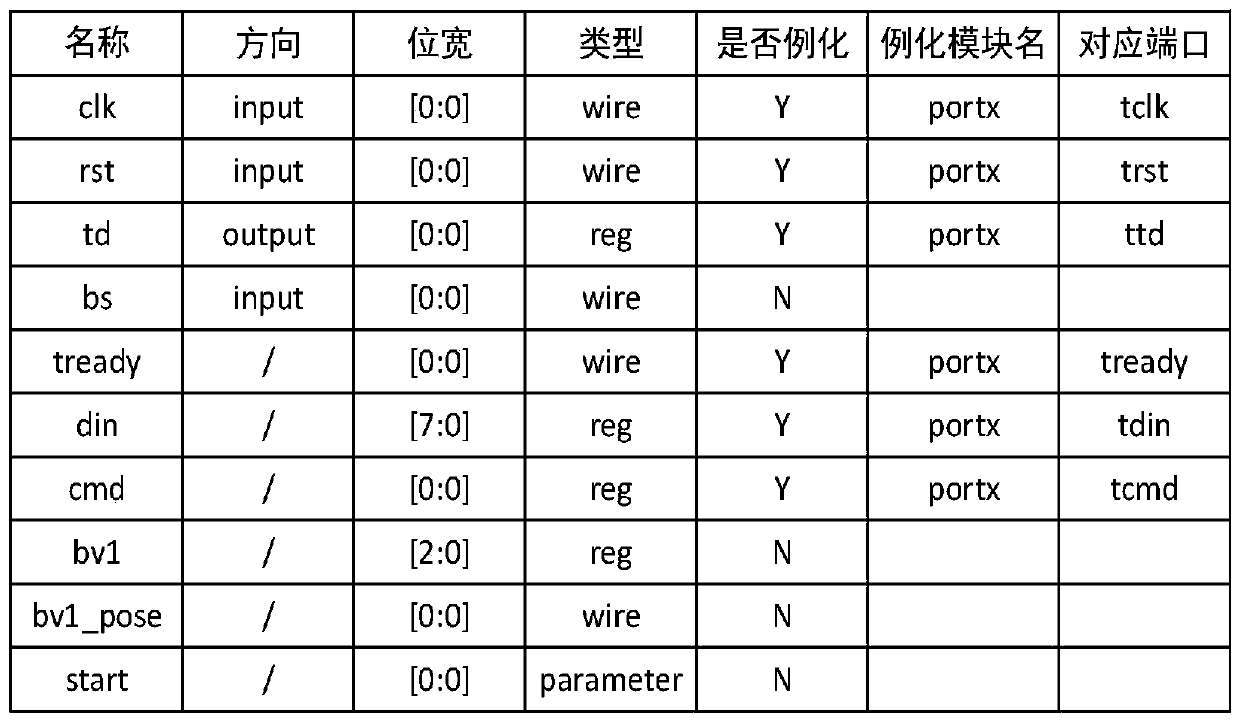
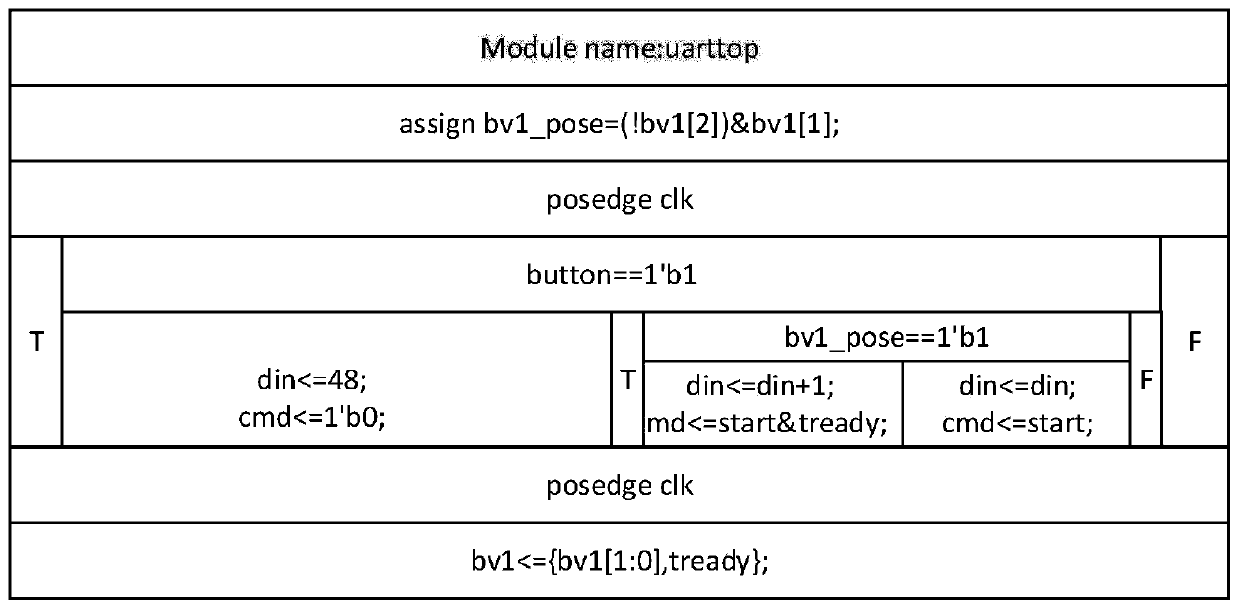
ActiveCN110941932AIntuitive display of branch directionEffective test accuracyCAD circuit designCode generationModelSim
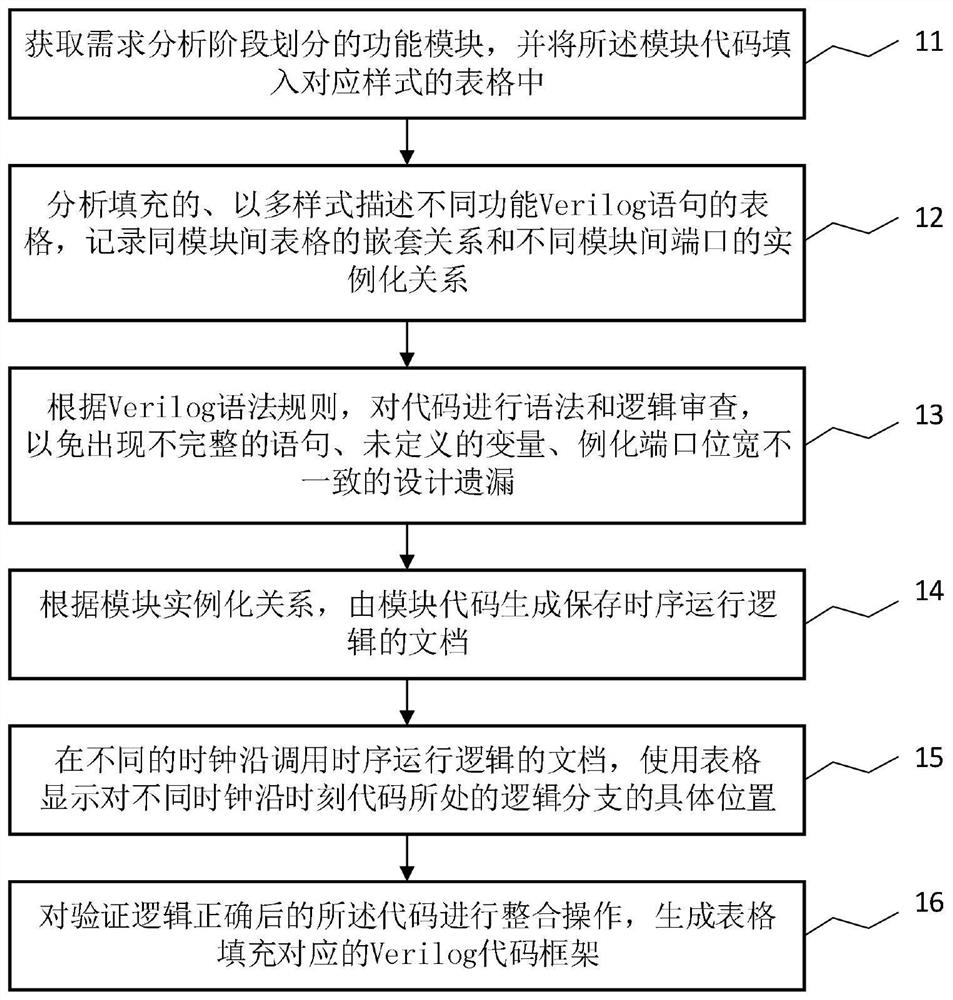
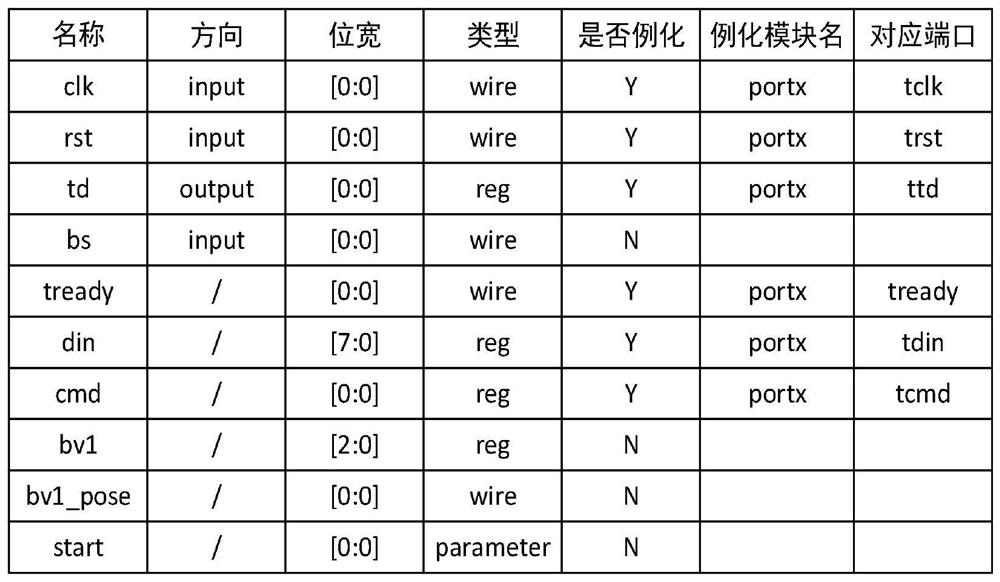
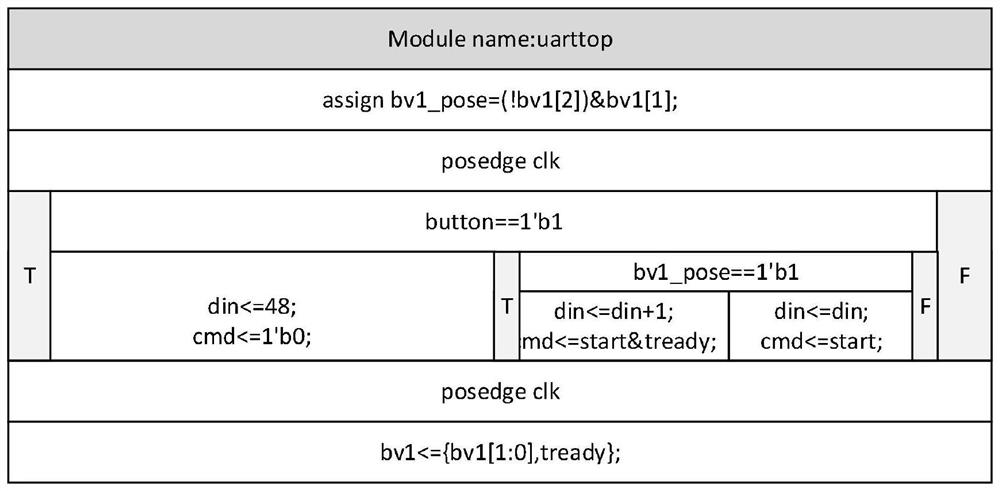
The invention discloses a hardware logic design-oriented demand modeling and verification method, which comprises the following steps of: 1, obtaining function modules divided in a demand analysis stage, and filling codes of the function modules into a table of a corresponding style; step 2, analyzing the filled forms which describe Verilog HDL statements with different functions in multiple styles, and recording a nested relationship of the forms between the same modules and an instantiation relationship of ports between different modules; 3, carrying out grammar and logic review on the codes; 4, generating a document for storing time sequence running logic by the module code; step 5, calling the documents of the time sequence operation logic at different clock edges, and displaying specific positions of logic branches where codes are located at different clock edge moments by using a table; and step 6, performing integration operation on the code after the verification logic is correct, and generating a Verilog HDL code framework corresponding to table filling. According to the method, logic can be automatically verified in a simple form filling mode, and the effect of pre-verification is achieved.
Owner:DALIAN UNIV OF TECH
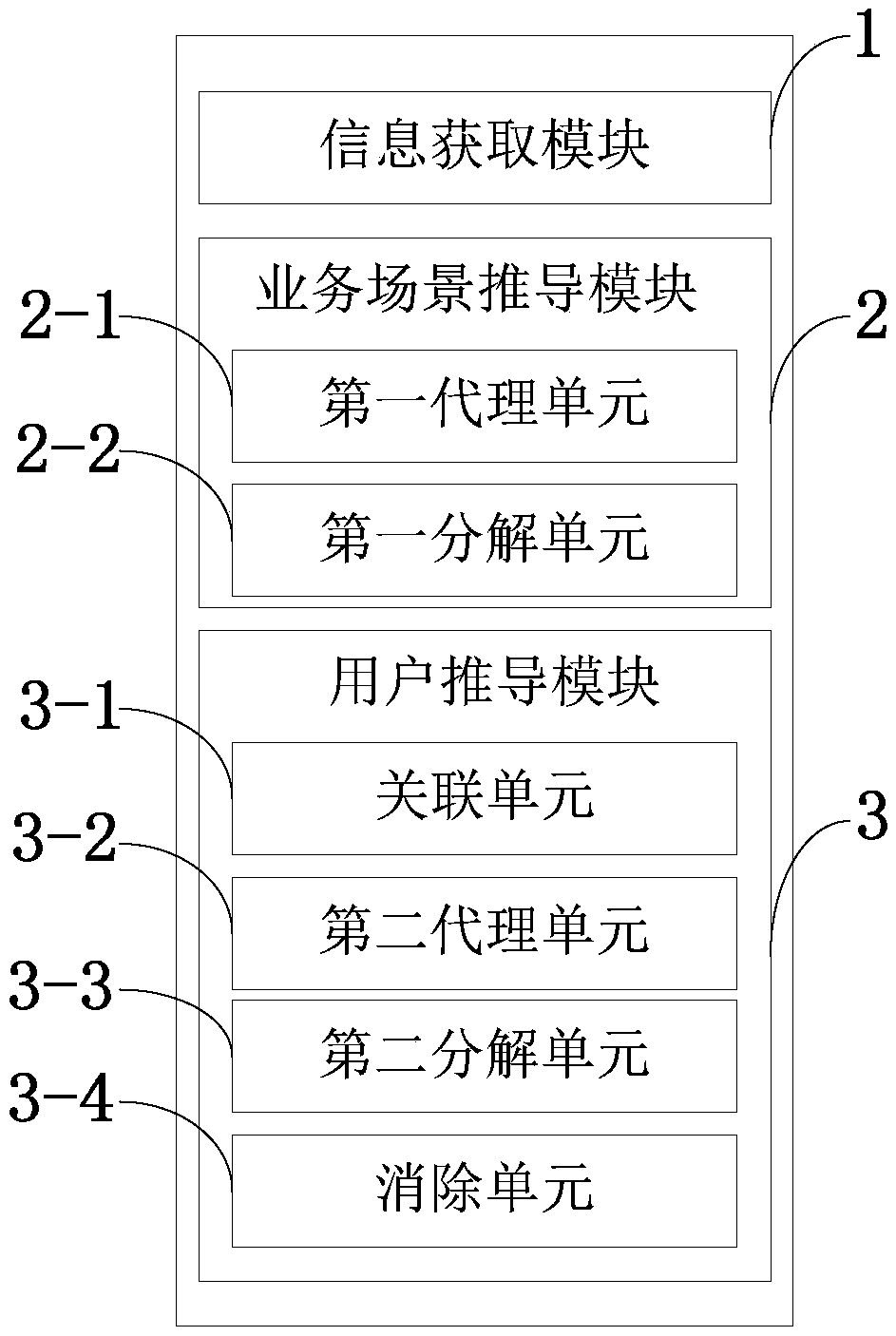
Requirement modeling process personnel evolution system and method, processor and terminal
InactiveCN109408031AUniqueness guaranteedGuaranteed singularityRequirement analysisBusiness PersonnelThird party
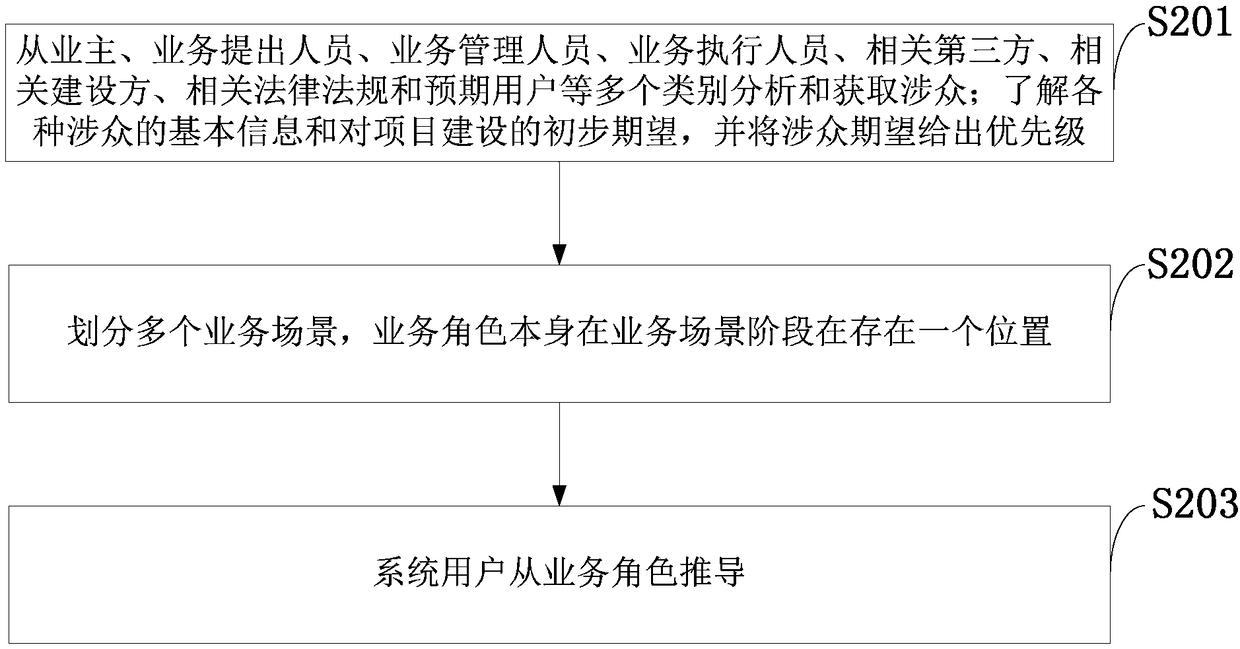
The invention belongs to the technical field of computer aided design. The invention discloses a requirement modeling process personnel evolution system and method, a processor, a terminal and an information obtaining module, which are used for obtaining basic information and expectations from owners, service proposers, service managers, service executives, relevant third parties, relevant builders, relevant laws and regulations, expected users and the like; a service scenario derivation module, which is used for dividing the service scenario and confirming the execution result; the user derivation module is used for realizing the derivation of service roles. A method for derive and evolving personnel in that process of requirement modeling is provided, and a relatively simple but principled and operable method is use for guiding from the obtaining of personnel in the requirement investigation stage to the classification and role of service personnel in the process to the division of system user personnel in the requirement specification stage; completing analysis of multiple categories and capture stakeholders; prioritizing stakeholder expectations; While ensuring the uniqueness and singularity of data sources.
Owner:CHENGDU UNIV OF INFORMATION TECH
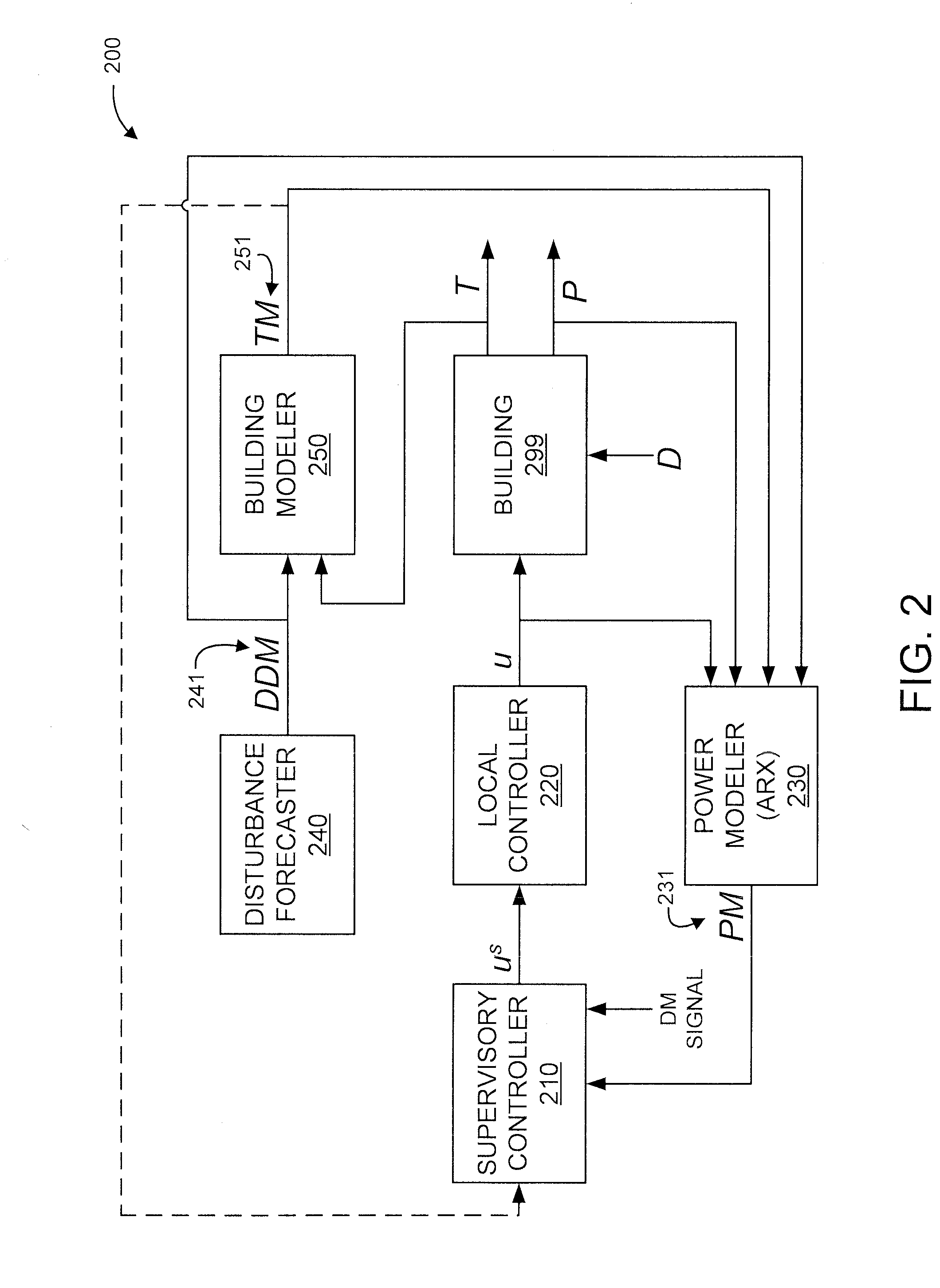
Power modeling based building demand management system
InactiveUS20150268650A1Programme controlMechanical power/torque controlRequirements managementManagement system
A method and system are provided. The method includes generating a power model, modeling power demands of at least one of a building and subsystems thereof, responsive to measured power-related inputs specific to the building and forecasted power-related inputs. The method further includes controlling, by a processor-based supervisory controller, power consumption of at least one of the building and the subsystems responsive to the power demands modeled by the power model.
Owner:NEC LAB AMERICA
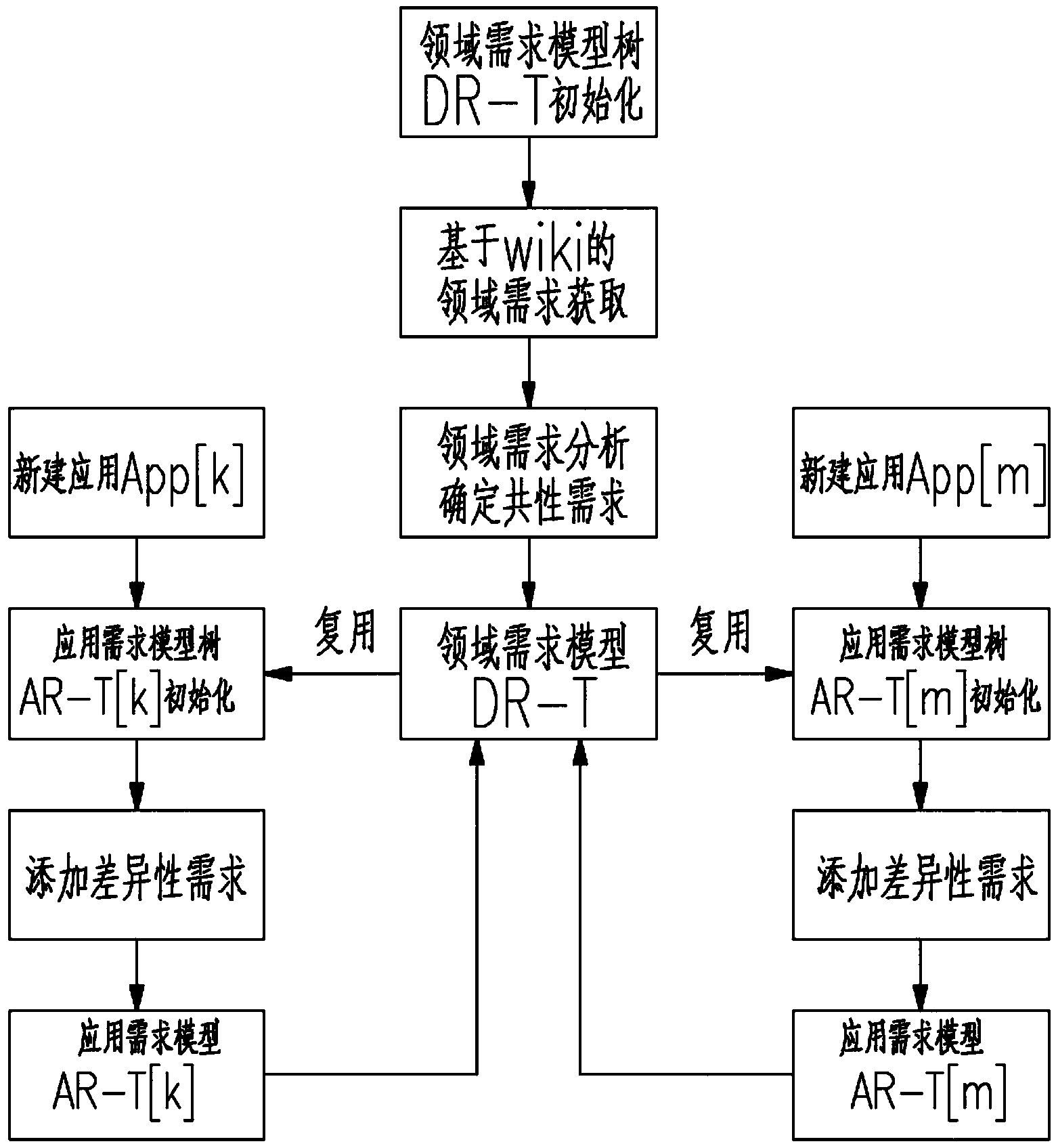
Reuse-oriented software demand modeling and evolving method
The invention discloses a reuse-oriented software demand modeling and evolving method. The method comprises the following steps: (1) firstly, initializing a field demand model tree DR-T; (2) adopting a wiki way to obtain field demands, and collecting the field demands described by a natural language through a wiki system; (3) determining a common demand, and building a field demand model; (4) initializing an application demand model AR-T [m] of a new application App [m]; (5) adding difference demand nodes to the AR-T [m], so as to form a complete App [m] application demand model; (6) evolving the application demand model AR-T [m] to the field demand model DR-T; and (7) evolving the command demand in the field demand model DR-T to be a non-common demand. A software enterprise can build a demand model of some business field step by step by adopting the reuse-oriented software demand modeling and evolving method, so as to form the important intangible assets of the software enterprise. When new software needs to be built in the field, a protocol in the field demand model can be reused to quickly form a requirement specification and a demand model.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
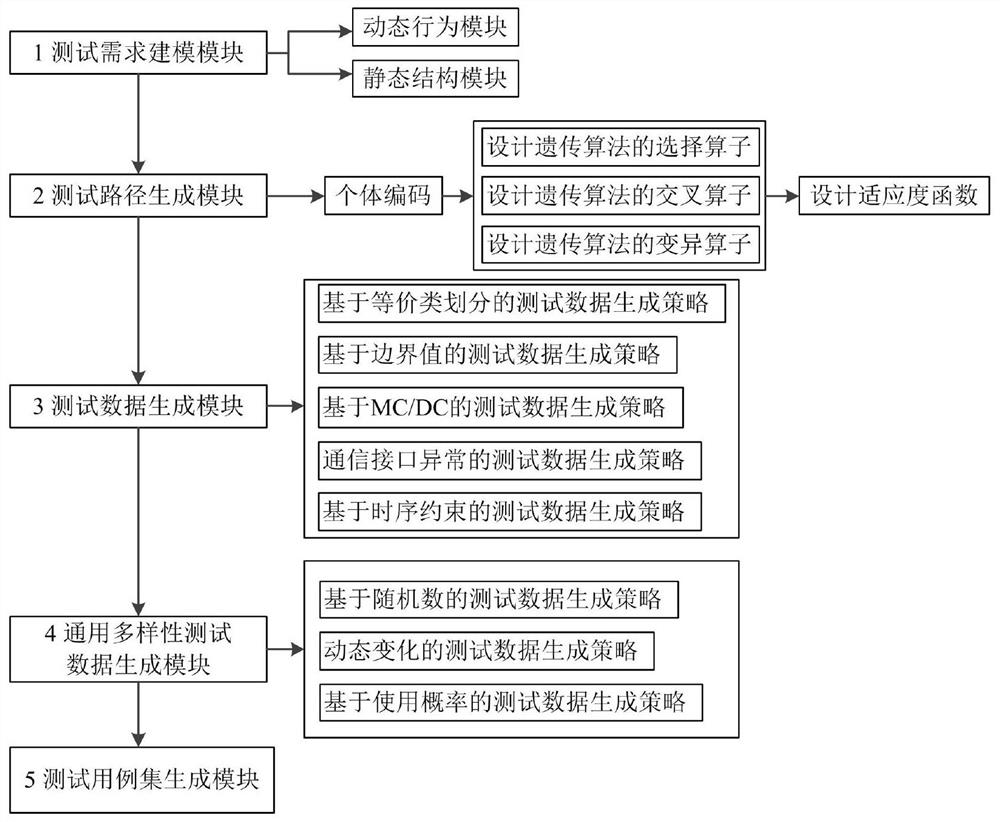
Model-based embedded software test case generation model
ActiveCN113806232AIntegrity guaranteedGuaranteed accuracySoftware testing/debuggingEnergy efficient computingTest qualityPath generation
The invention provides a model-based embedded software test case generation model. The model comprises a test demand modeling module, a test path generation module, a test data generation module, a universal diversity test data generation module and a test case set generation module. The test demand modeling module constructs a dynamic behavior test demand model and a static structure test demand model; the test path generation module generates a test path set by using a heuristic search genetic algorithm; the test data generation module generates test data of the test path set; the universal diversity test data generation module generates universal diversity test data; and the test case set generation module encapsulates the corresponding test path set and the test data into a complete test case. According to the invention, embedded software test demand modeling and test case generation based on the test demand model are adopted, so that the integrity and accuracy of software test demand description are ensured, the test efficiency of embedded software is improved, and the software test quality is ensured.
Owner:CHINA AERO POLYTECH ESTAB
Aviation equipment field programmable logic device software security analysis method
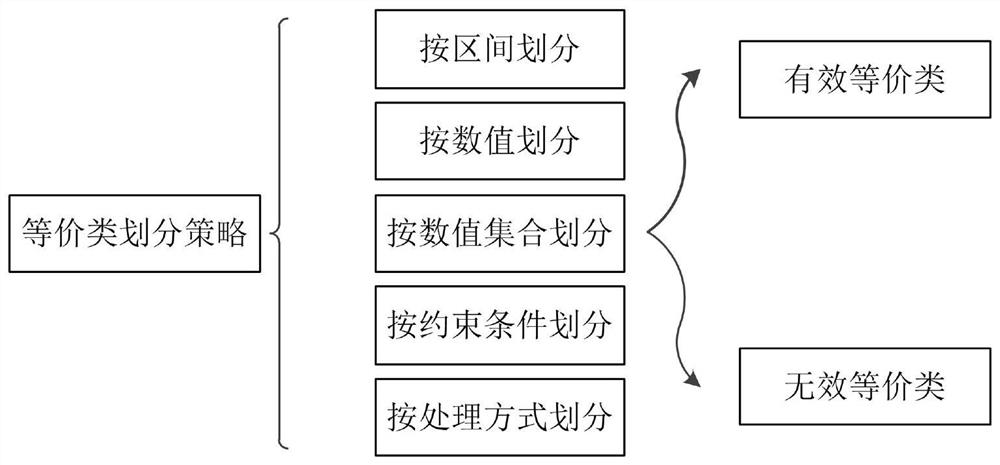
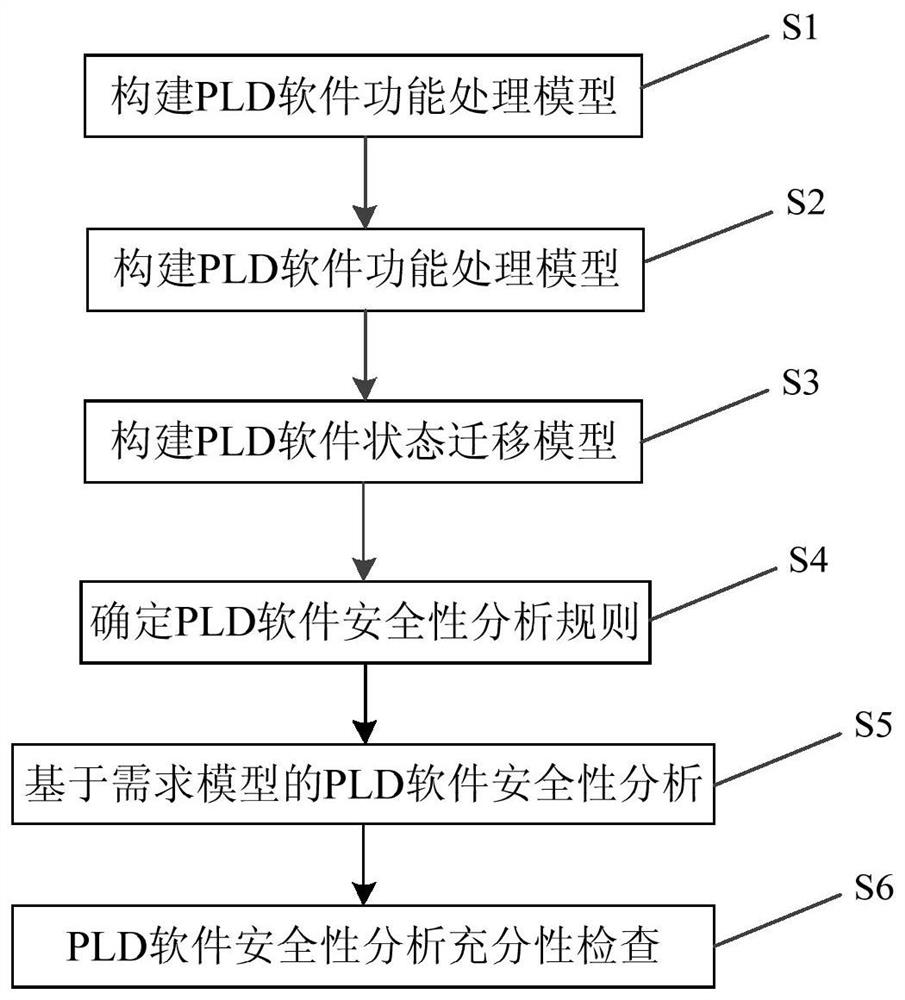
ActiveCN112612241AAvoid lack of objectivityPracticalProgramme control in sequence/logic controllersAviationRequirements model
The invention provides an aviation equipment field programmable logic device software security analysis method, which comprises the following steps: forming a security analysis-oriented demand modeling method for an external cross-linking environment model, a function processing model and a working state migration model; according to the demand model, forming an aviation equipment PLD software security analysis rule from an external input interface, an external output interface, a function processing process and a working state angle; and on the basis of the demand model, determining a potential PLD software failure mode in the demand according to a PLD software security analysis rule, analyzing reasons and influences of the failure mode, formulating corresponding control measures, and determining PLD software security requirements. By means of the aviation equipment PLD software requirement modeling oriented to safety analysis and the aviation equipment PLD software safety analysis technology based on the requirement model, the aviation equipment PLD software safety analysis method is standardized, and the safety and the quality level of aviation equipment PLD software are improved.
Owner:CHINA AERO POLYTECH ESTAB
Method and device for analyzing test coverage automatically aiming at automatic test system
InactiveCN101894058BImprove work efficiencyImprove accuracyDetecting faulty computer hardwareAutoanalysisDemand modeling
Owner:BEIHANG UNIV
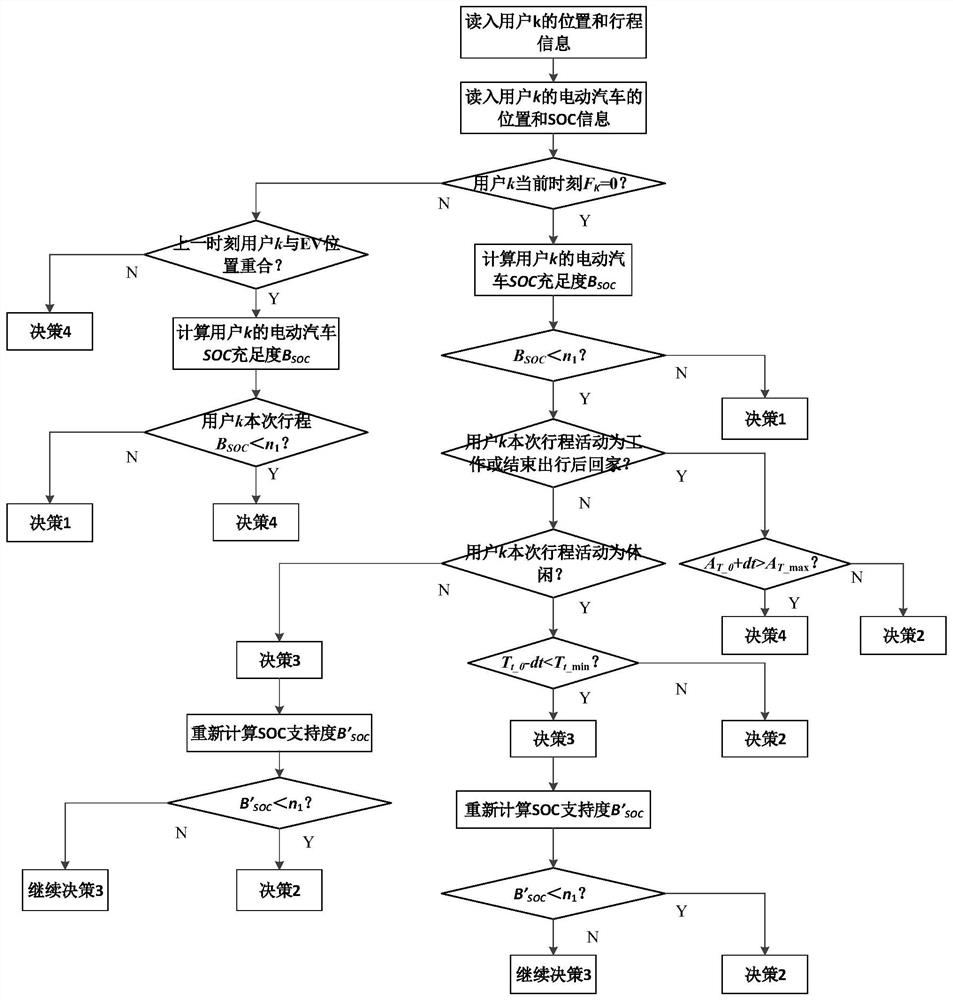
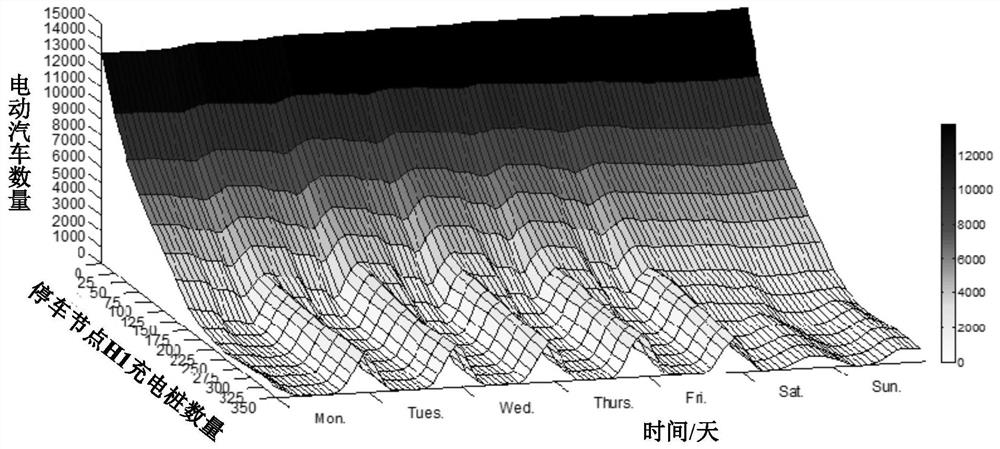
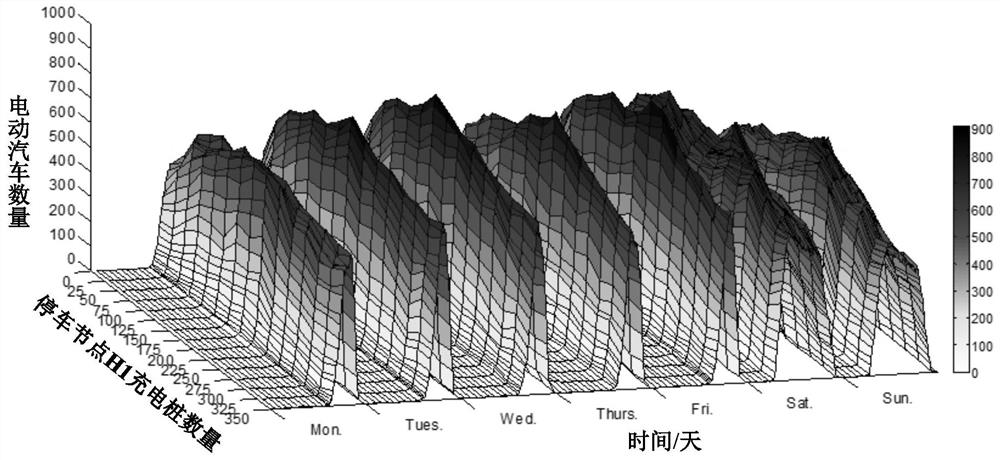
An analysis method for electric vehicle travel and charging demand considering charging feedback effect
Owner:TIANJIN UNIV
An embedded software security automatic verification system and verification method thereof
ActiveCN106528407BImprove sufficiencyLower barriers to useSoftware testing/debuggingCross-linkValidation methods
The invention discloses an embedded software security automation verification system and a verification method thereof. According to the technical scheme, double verification of software security is realized in combination with a model checking-based formal verification technology and a model-based software test technology. The automation verification system disclosed by the invention comprises four parts, which are a software demand modeling module, a security verification rule database, a formal verification module, and a security test module respectively. The software demand modeling module comprises two sub-modules, wherein the ICD modeling module describes a software external cross-linking environment, and the formal modeling module describes a software internal behavior. The security verification rule database is constructed and used for storing security verification rules. The formal verification module is constructed and used for performing model verification on a software demand based on the security verification rules and a model detection algorithm. The software detection module comprises two modules, wherein the test case generation module is used for generating an executable security case, and a test case translation module performs format conversion on the generated case.
Owner:CHINA AERO POLYTECH ESTAB
A Requirement Modeling and Model Transformation Method Based on New Feature Model
ActiveCN103164230BResolve ambiguityDetailed featuresSpecific program execution arrangementsAlgorithmTheoretical computer science
Owner:XIDIAN UNIV
A Requirement Modeling and Verification Method for Hardware Logic Design
ActiveCN110941932BIntuitive display of branch directionEffective test accuracyCAD circuit designCode generationParallel computing
The invention discloses a requirement modeling and verification method oriented to hardware logic design, which includes step 1: obtaining the functional modules divided by the requirement analysis stage, and filling the functional module codes into a table of the corresponding style; step 2: analyzing Filled tables that describe Verilog HDL statements of different functions in multiple styles, record the nesting relationship of tables between the same modules and the instantiation relationship of ports between different modules; Step 3: Review the syntax and logic of the code; Step 4: By the module Code generation saves the document of timing operation logic; Step 5: Call the document of timing operation logic at different clock edges, and use the table to display the specific position of the logic branch of the code at different clock edge times; Step 6: After verifying that the logic is correct The codes are integrated to generate the corresponding Verilog HDL code framework for table filling. This method can automatically verify the logic in a simple way of filling the form, and achieve the effect of prior verification.
Owner:DALIAN UNIV OF TECH
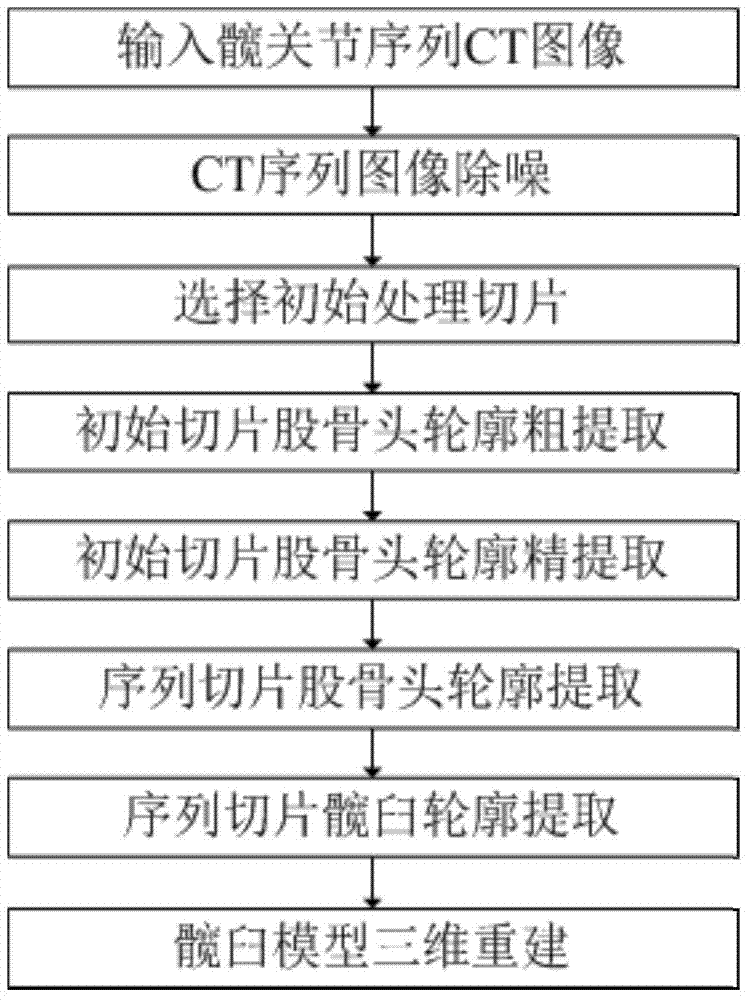
Acetabular tissue model reconstruction method for serialized hip joint CT images
Owner:DALIAN UNIV OF TECH
Embedded software development system
PendingCN112835557AReduce the difficulty of requirement modelingImprove efficiencyProgramming languages/paradigmsRequirement analysisRequirements modelSoftware system
The invention relates to an embedded software development system. The method comprises the following steps: establishing a demand model of an embedded system program to be developed according to demand analysis of the embedded software system program; analyzing and detecting the demand model, generating source codes required by the target software system program at the same time, and further generating the target software system program; performing program analysis on the target software system program to obtain a program model, performing comparative analysis on the program model and the demand model to find difference, and if difference is found, repairing the generated target software system program or demand model. Aiming at the characteristics of the embedded software system program, a demand modeling technical scheme suitable for the embedded software system program is provided, the demand expressed by a user by using a natural language is converted into a scene and behavior expression, and a good foundation is laid for automatically detecting whether the demand of a software system is correct and complete or not.
Owner:十堰企兴企业管理顾问有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com