An embedded software security automatic verification system and verification method thereof
An automatic verification and embedded software technology, applied in software testing/debugging, instrumentation, error detection/correction, etc., can solve problems such as limited coverage, low popularity, execution uncertainty, etc., to reduce the difficulty of project implementation, The effect of enhancing the guiding role and lowering the threshold of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The technical scheme of the present invention will be described in further detail below in conjunction with accompanying drawing and embodiment:
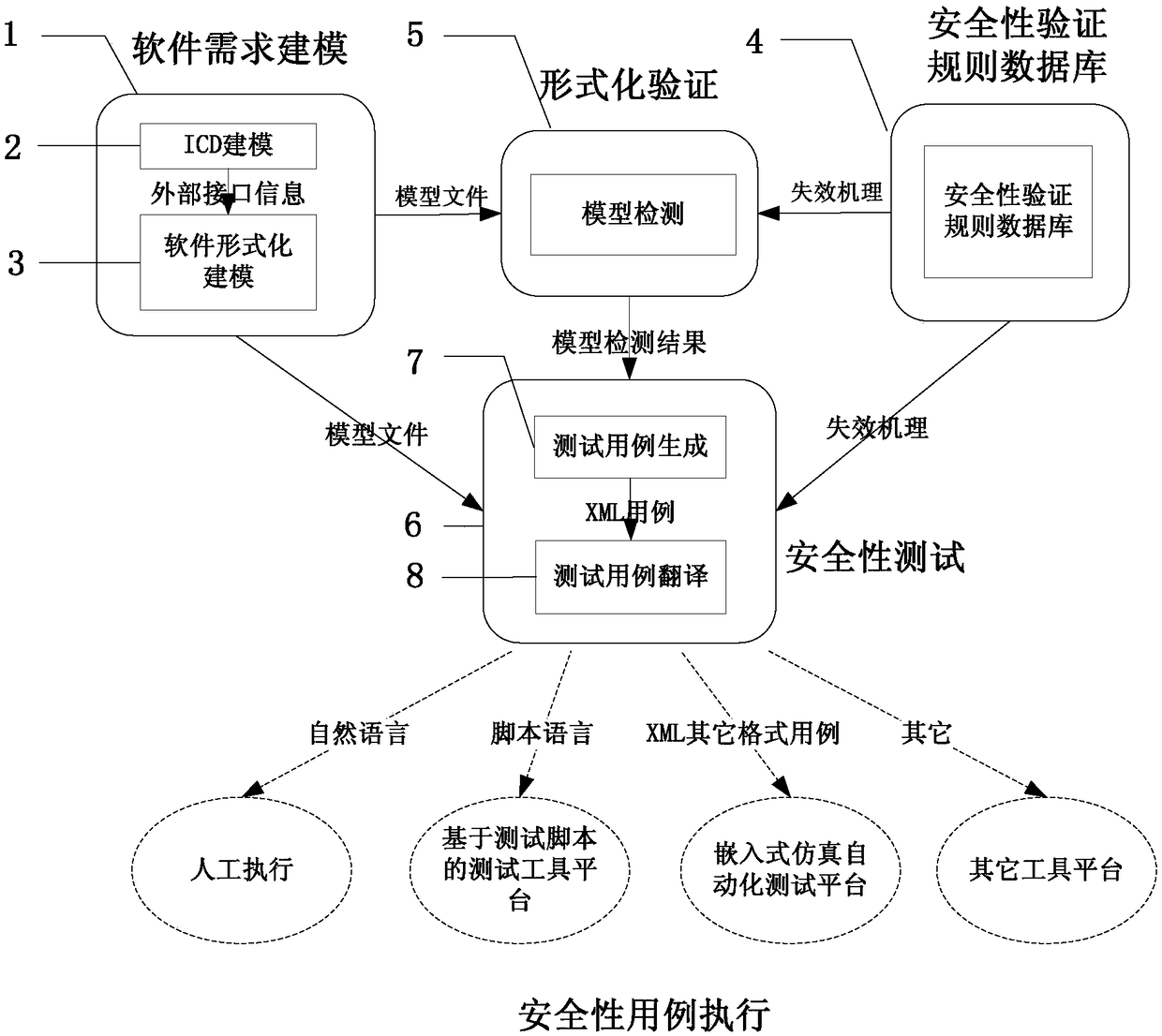
[0041] See attached figure 1 As shown, the embedded software safety automatic verification system described in the technical solution of the present invention is characterized in that: the system includes:
[0042] A software requirement modeling module 1, its function is to formally describe the software to be verified according to the ICD file and requirement specification of the software to be verified, and form a software requirement model file. The software requirement modeling module 1 includes:
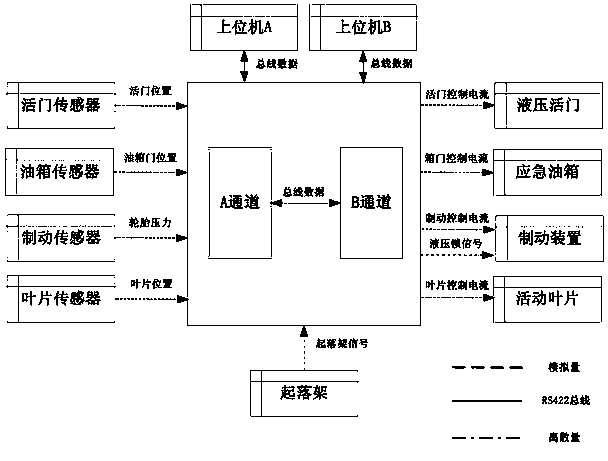
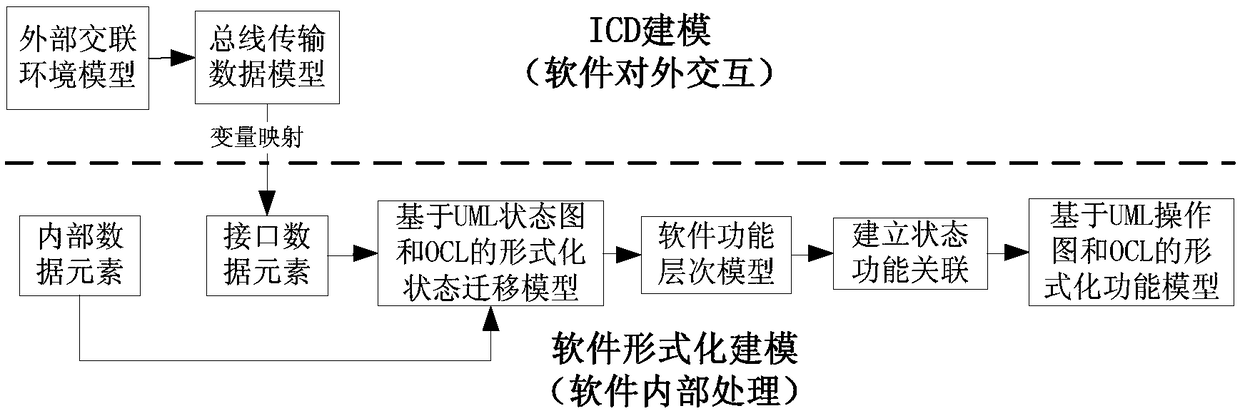
[0043] ICD modeling module 2, its function is to describe the external cross-linking environment of the software to be verified, including the cross-linking relationship with external devices, bus type and communication protocol, and form ICD model data;
[0044] Software formal modeling module 3, its function is to use OCL for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com