Automatic vulnerability detection plugin generation method and system for industrial control system
A technology for industrial control systems and vulnerability detection, which is applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc. It can solve problems that may take ten minutes or even ten hours, verification time is uncontrollable, and restart time and problems Problems such as poor control can be achieved to improve the efficiency of vulnerability mining, reduce the time required for recurrence, and reduce the time for vulnerability mining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
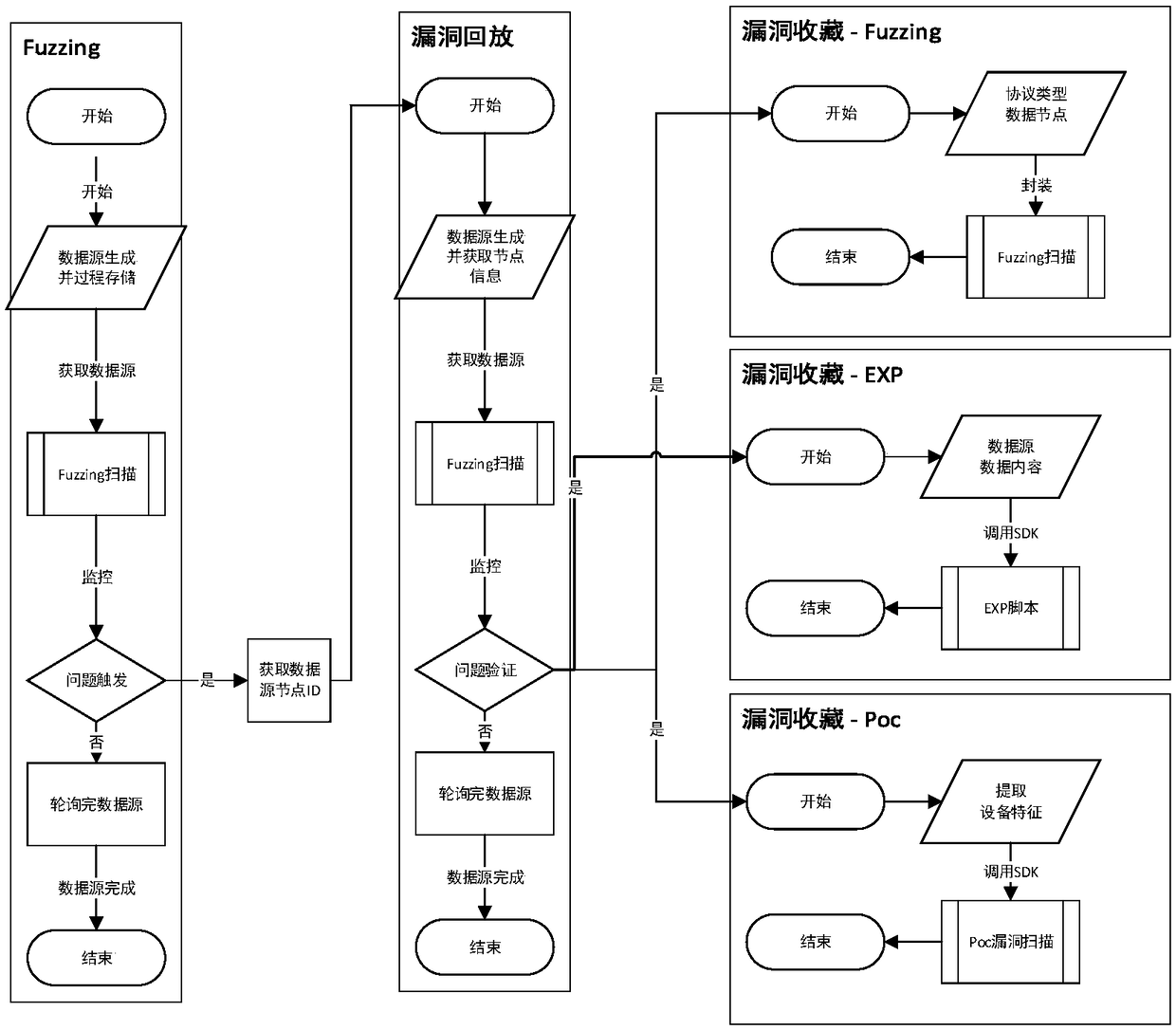
[0035] This embodiment provides a method for generating an industrial control system automation vulnerability detection plug-in, such as figure 1 As shown, it includes the Fuzzing test link, the vulnerability replay link and the vulnerability collection link.
[0036] The steps of the Fuzzing test link (that is, the vulnerability mining link) are as follows: construct a data source and store the data; obtain the data source, start the Fuzzing scan, and mine the vulnerability; monitor the mining process; if all the data sources are polled, there is no problem If triggered, the mining process will end; if there is a problem triggered, the data source node ID will be obtained and enter the loophole playback link;
[0037] The steps of the vulnerability playback link are as follows: generate a data source and obtain node information; obtain the data source and start Fuzzing scanning; verify that there is no problem, then end, if there is a problem, then enter the vulnerability col...
Embodiment 2
[0047] This embodiment provides a plug-in generation system for automatic vulnerability detection of an industrial control system, which includes a vulnerability mining module, a vulnerability playback module and a vulnerability collection module.
[0048]The working process of the vulnerability mining module is as follows: constructing a data source and storing the data; obtaining the data source, starting Fuzzing scanning, and mining the vulnerability; monitoring the mining process; if all the data sources are polled and no problem is triggered, the mining is ended process; if a problem is triggered, obtain the data source node ID and enter the vulnerability playback module;
[0049] The working process of the vulnerability playback module is as follows: generate a data source and obtain node information; obtain the data source and start Fuzzing scanning; verify that there is no problem, then end, if there is a problem, then enter the vulnerability collection module;
[0050...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com