A LDoS attack detection method in SDN environment
An attack detection and environment technology, applied in electrical components, transmission systems, etc., can solve the problem that there is little research on LDoS attack detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
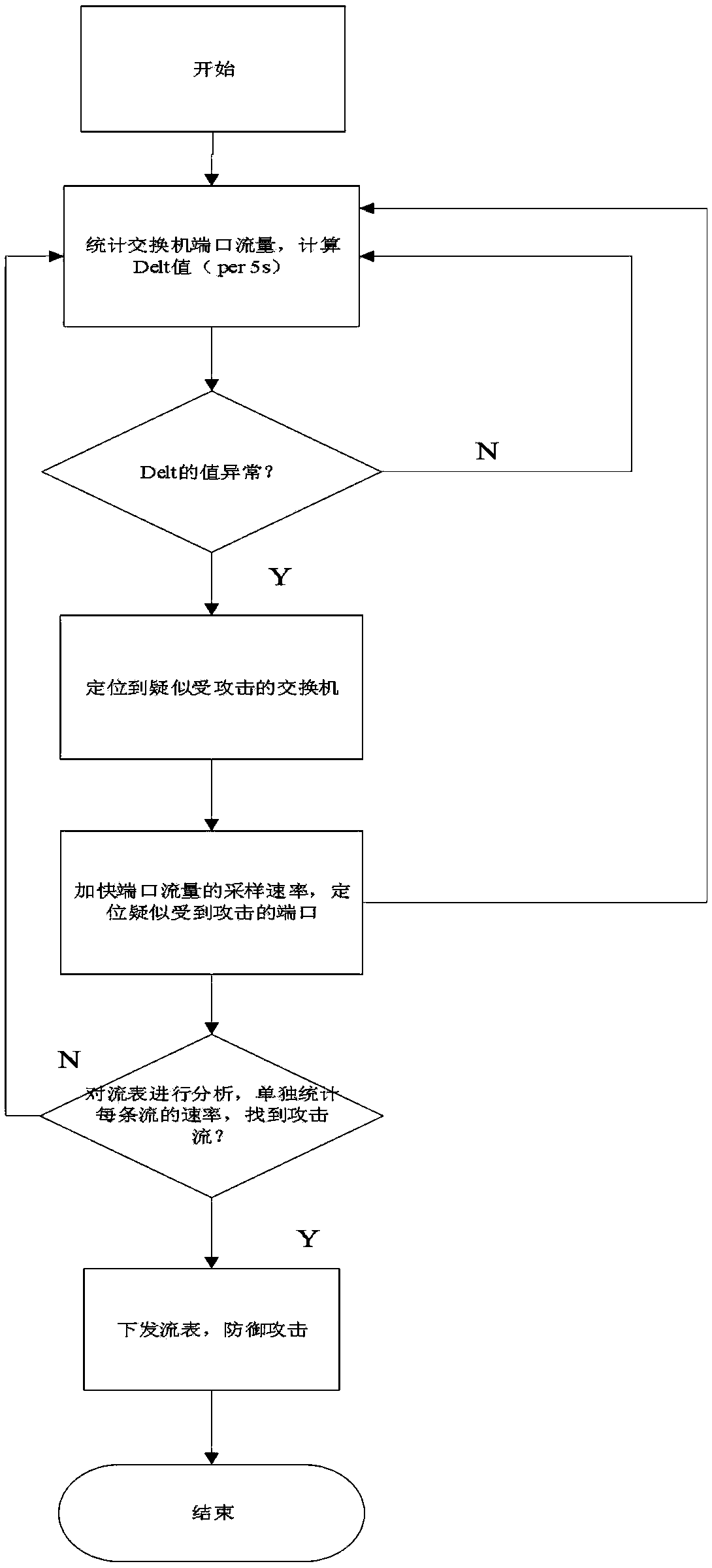
[0019] (1) Locate the suspected switch by analyzing the Delta value. where Delt=in_package-out_package,
[0020] in_package is the number of data packets flowing into the switch per unit time, and out_package is the number of data packets flowing out of the switch. Under normal circumstances, the difference between the two should be small, that is, the inflow and outflow are in a relatively balanced state. When a short-term high-rate LDoS attack traffic flows in, a large number of data packets flood into the switch, causing the value of Delt to increase sharply. Therefore, this value can be used as a condition for pre-judging whether the switch is under an LDoS attack.
[0021] (2) Analyze the port flow of the suspected attacked switch located in step (1), and locate the suspected attacked port. The specific steps are: set a threshold s, sample the rate of each port of the switch, and the sampling period is T, and record the time t when the sampling value obtained by port sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com