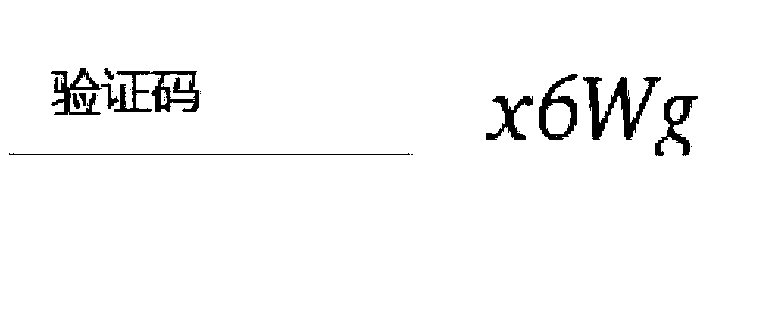Authentication code implementation method, apparatus, system, computing device and storage medium
An implementation method and verification code technology, applied in the fields of computing equipment and storage media, systems, devices, and verification code implementation methods, can solve problems such as friendliness being discounted, and achieve enhanced semantic complexity, reduced cognitive difficulty, and reduced Effects of Interaction and Cognitive Difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] Hereinafter, preferred embodiments of the present disclosure will be described in more detail with reference to the accompanying drawings. Although the drawings show preferred embodiments of the present disclosure, it should be understood that the present disclosure can be implemented in various forms and should not be limited by the embodiments set forth herein. On the contrary, these embodiments are provided to make the present disclosure more thorough and complete, and to fully convey the scope of the present disclosure to those skilled in the art.
[0054] As mentioned earlier, the design of the verification code should consider interaction friendly and convenient for users to complete the verification, and at the same time it needs to be difficult to be cracked to counter robots or automated tools. Among the existing various verification codes, most of the verification codes with better interactive experience have been cracked, and most of the verification codes that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com