A Bluetooth fast networking method
A networking and network technology, which is applied in the field of rapid networking and networking of Bluetooth devices, can solve problems such as low efficiency of Bluetooth networking, and achieve the effect of shortening the time of networking, improving the efficiency of networking, and reducing the cost of networking time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
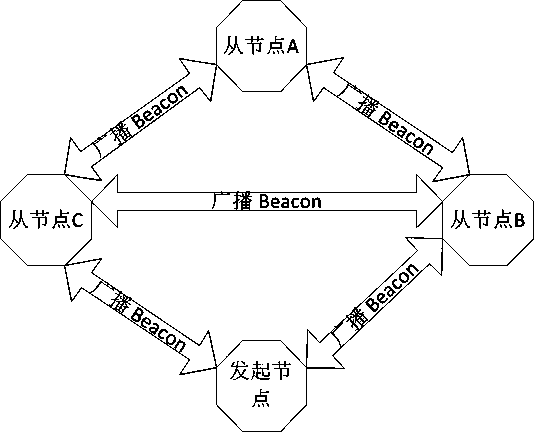
[0036] Whether the SIG MESH network is through PB-ADV or GATT, three keys must be set for a single node: device key, network key and application key. The device key is a unique key for each node that is different from other nodes, and can be used to set some important attributes. The network key is used to connect the mesh between nodes, and the application key is used to authenticate whether the command received by the node needs to be executed. If the authentication fails, the command cannot be executed. Therefore, for a node, there may only be one device key, and this device key is only known by the node itself and the initiating node for networking. But nodes can have multiple network keys and application keys. Nodes in the same mesh network share the same network key and application key. Each node can send and listen to broadcast beacon packets and mesh beacon packets.
[0037] figure 1 Send a schematic diagram of a broadcast Beacon network for the initiating node of th...
Embodiment 2
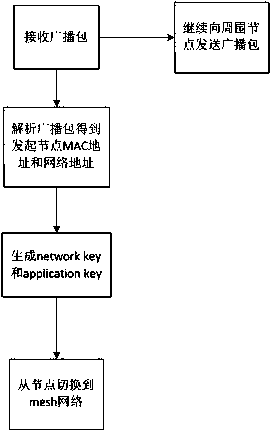
[0043] image 3 It is a schematic diagram of node networking in the present invention. Such as image 3 As shown, switch to the slave node in the MESH network and start sending a point-to-point communication networking request packet to the initiating node. The networking request packet includes the mac address of the slave node itself and the current network address of the slave node. In addition, the networking The request packet is encrypted on the slave node side using the generated network key and application key.
[0044] After the initiating node receives the networking request packet, it uses the network key and application key to analyze the networking request packet. In addition, when communicating between nodes in the mesh network, the generated network key and application key will be used for encryption and decryption. The initiating node saves the parsed mac address of the slave node locally, and reassigns a new network address for the slave node. The initiatin...
Embodiment 3
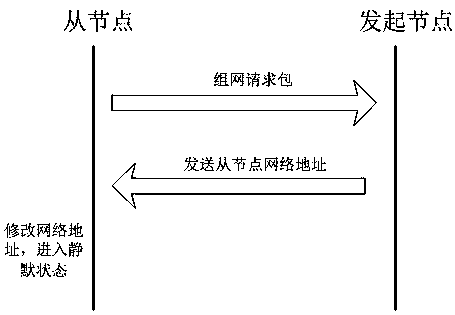
[0048] Figure 4 A schematic diagram of a method for networking the initiating node of the present invention, such as Figure 4 As shown, firstly, the initiating node broadcasts its own mac address and network address by broadcasting beacon packets; secondly, the initiating node receives the networking request packet sent by the slave node, which includes the slave node’s own mac address and the current Network address; then, the initiating node saves the received mac address of the slave node locally, and at the same time, generates and saves the device key of the slave node according to the obtained mac address of the slave node according to the device key generation method of SIG MESH; Finally, the initiating node assigns a unique network address for the entire mesh network to the slave node, and sends the network address to the slave node. So far, the networking process on the initiating node side ends.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com