Method and system for securely logging in computer communication based on internet
A technology of communication security and login method, applied in the fields of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of account information and login passwords being easily stolen by others, low security of computing login, etc., to enhance the difficulty of cracking , the effect of convenient calculation and operation, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] Embodiment 1: Internet-based computer communication security login method, such as figure 1 and figure 2 shown, including the following steps:
[0036] Step 1: Input the user identity information and encrypted verification code through the user login access unit 1 , and transmit the user identity information to the first processing unit 12 and the encrypted verification code to the second processing unit 15 .
[0037] Step 2: after the first processing unit 12 retrieves the login access matching information stored in the storage unit 11, it is judged whether the user identity information matches the login access comparison information; if it is judged to be yes, a dynamic verification code is sent to the dynamic verification unit 13 Generate a command; if the judgment is no, it will display that the user login and access failed.
[0038] Step 3: After receiving the dynamic verification code generation command, the dynamic verification unit 13 generates a dynamic veri...
Embodiment 2
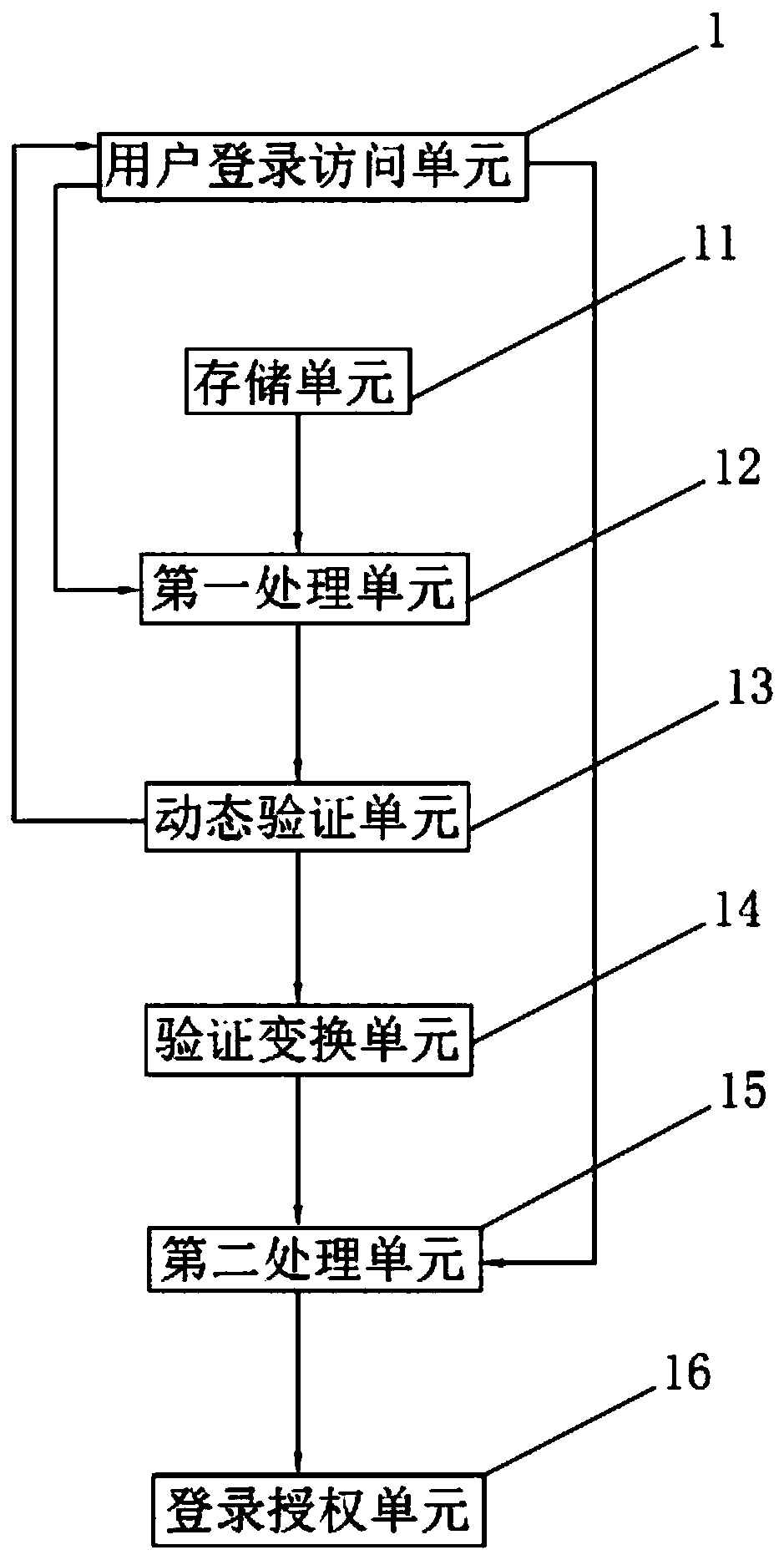
[0046] Embodiment 2: Internet-based computer communication security login system, such as figure 2 As shown, it includes a user login access unit 1 , a storage unit 11 , a first processing unit 12 , a dynamic verification unit 13 , a verification conversion unit 14 , a second processing unit 15 and a login authorization unit 16 .
[0047] Such as figure 2 As shown, the user login access unit 1 is used to input user identity information and encrypted verification code, and transmit the user identity information to the first processing unit 12 and the encrypted verification code to the second processing unit 15 .
[0048] Such as figure 2 As shown, the storage unit 11 stores login access matching information.
[0049] Such as figure 2 As shown, the first processing unit 12 is used to determine whether the user identity information matches the login access comparison information after calling the login access matching information; If it is not, it will display that the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com