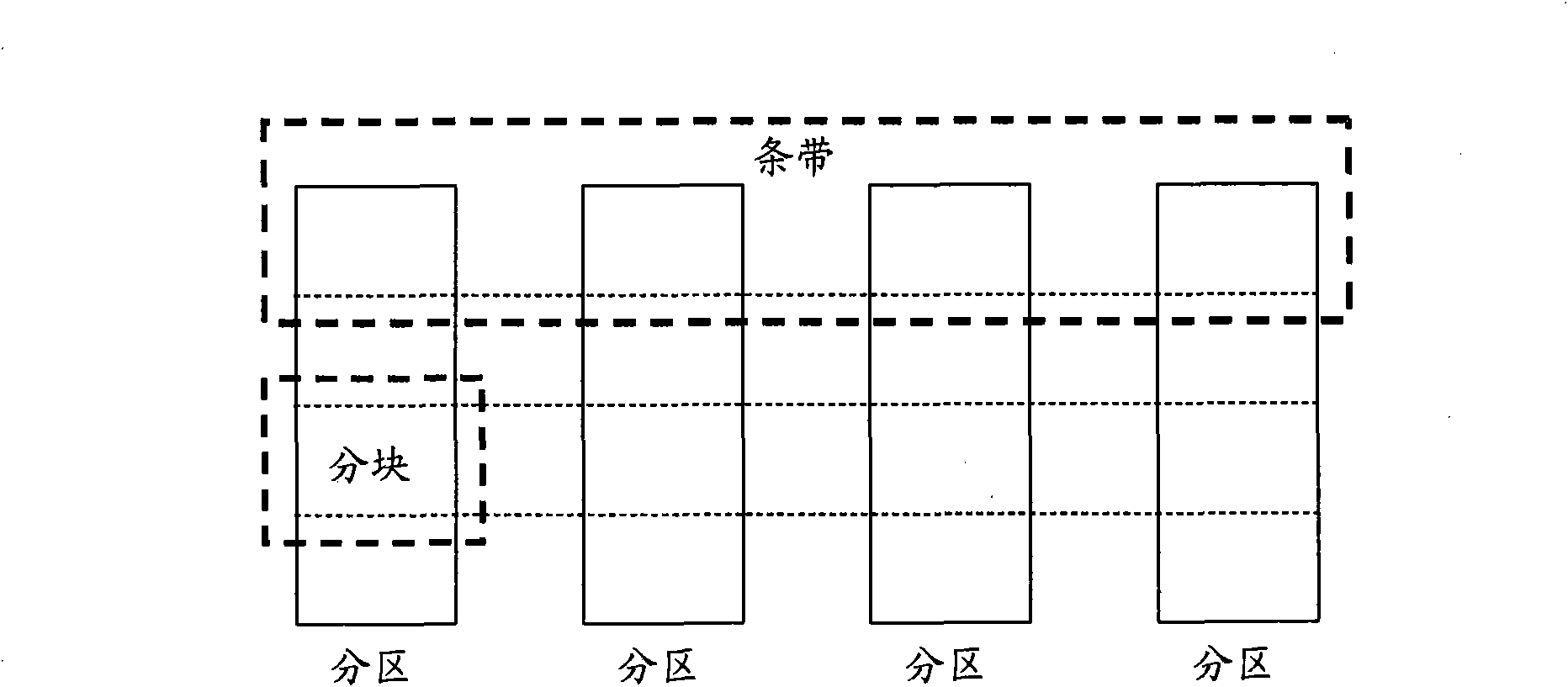
Patents
Literature
583results about How to "Prevent loss" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
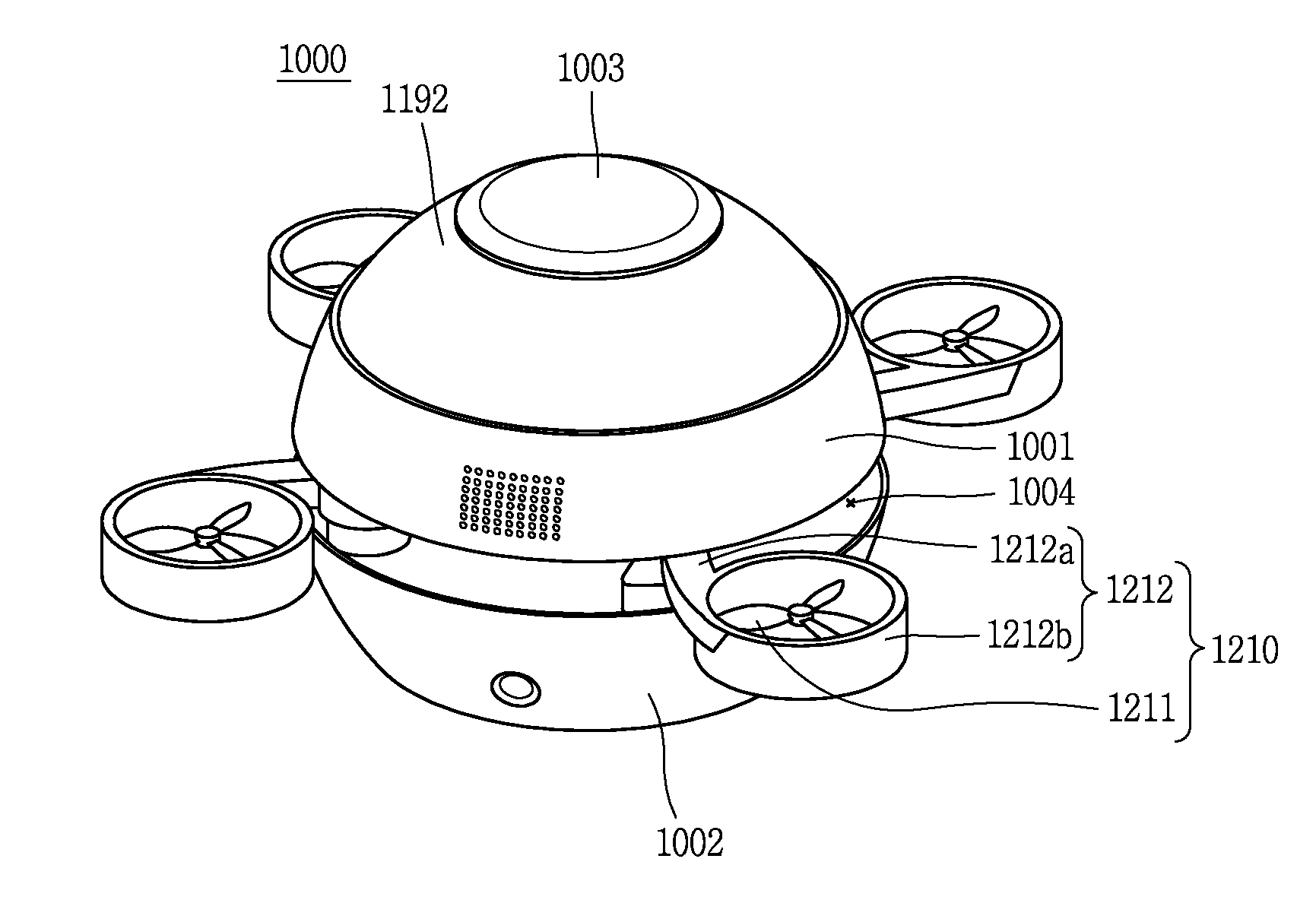
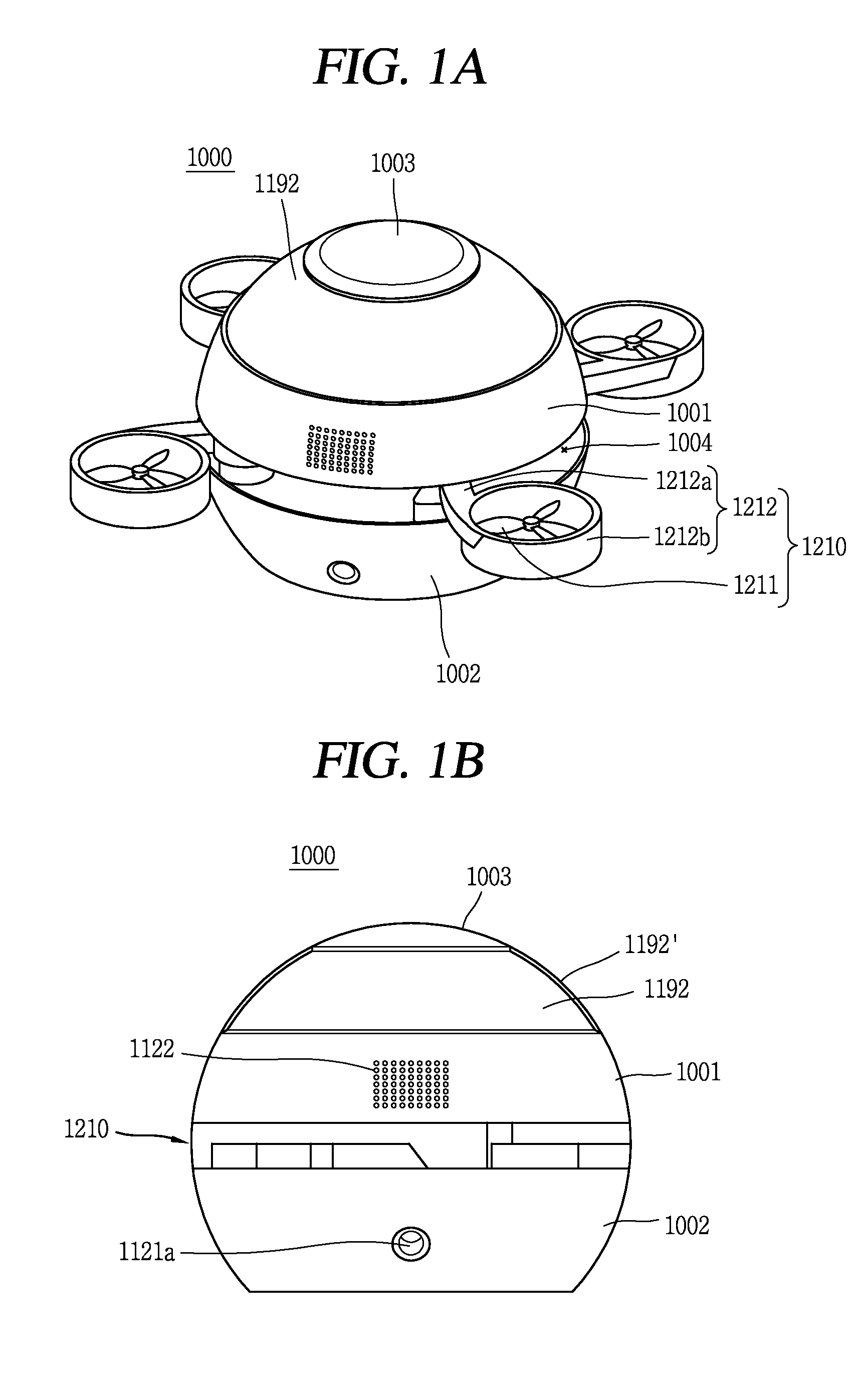
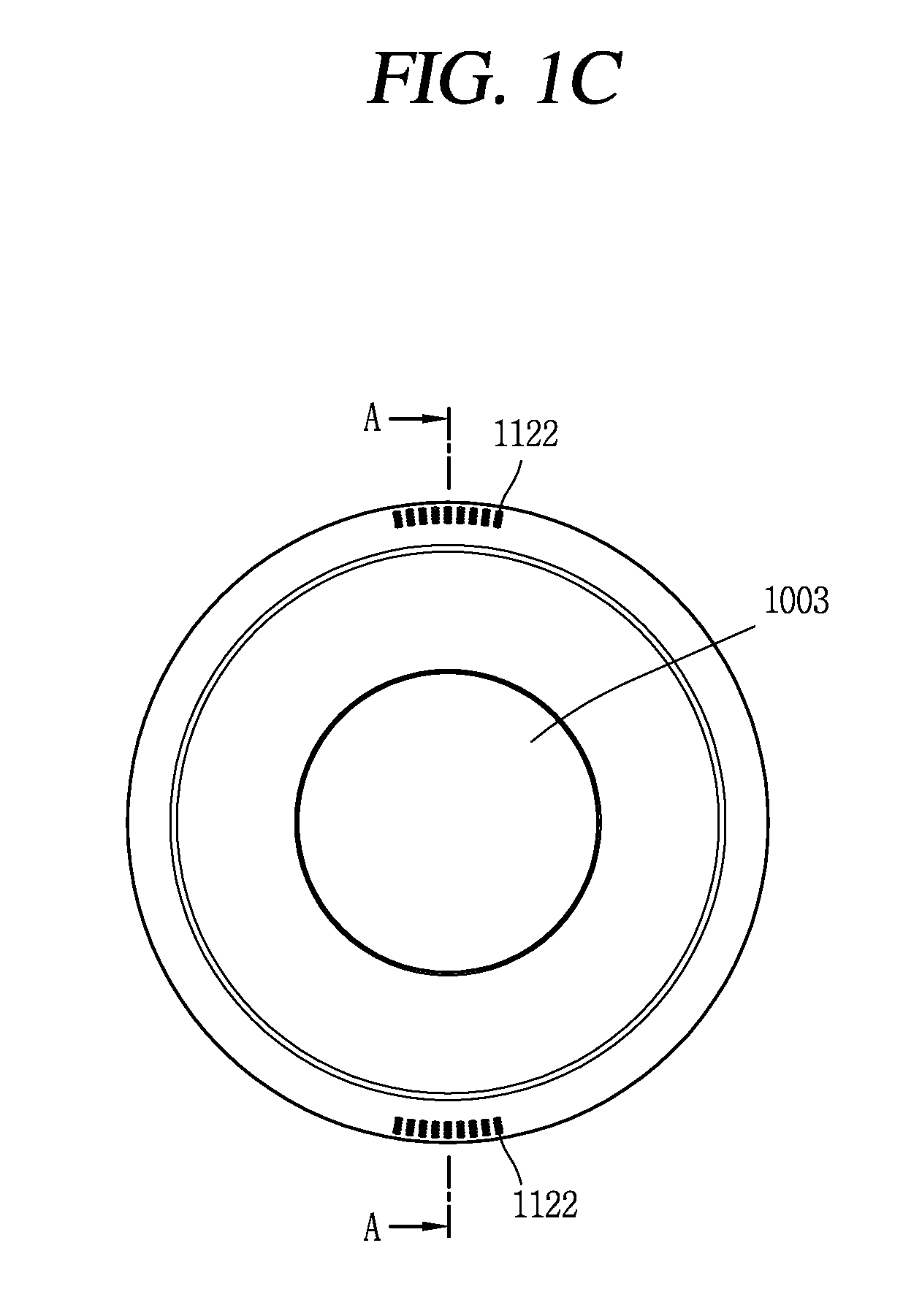
Unmanned aerial vehicle and method of controlling the same
InactiveUS20160272317A1Facilitate handlingPrevent lossAutonomous decision making processArrangements for variable traffic instructionsFlight vehicleUnmanned spacecraft
Owner:LG ELECTRONICS INC
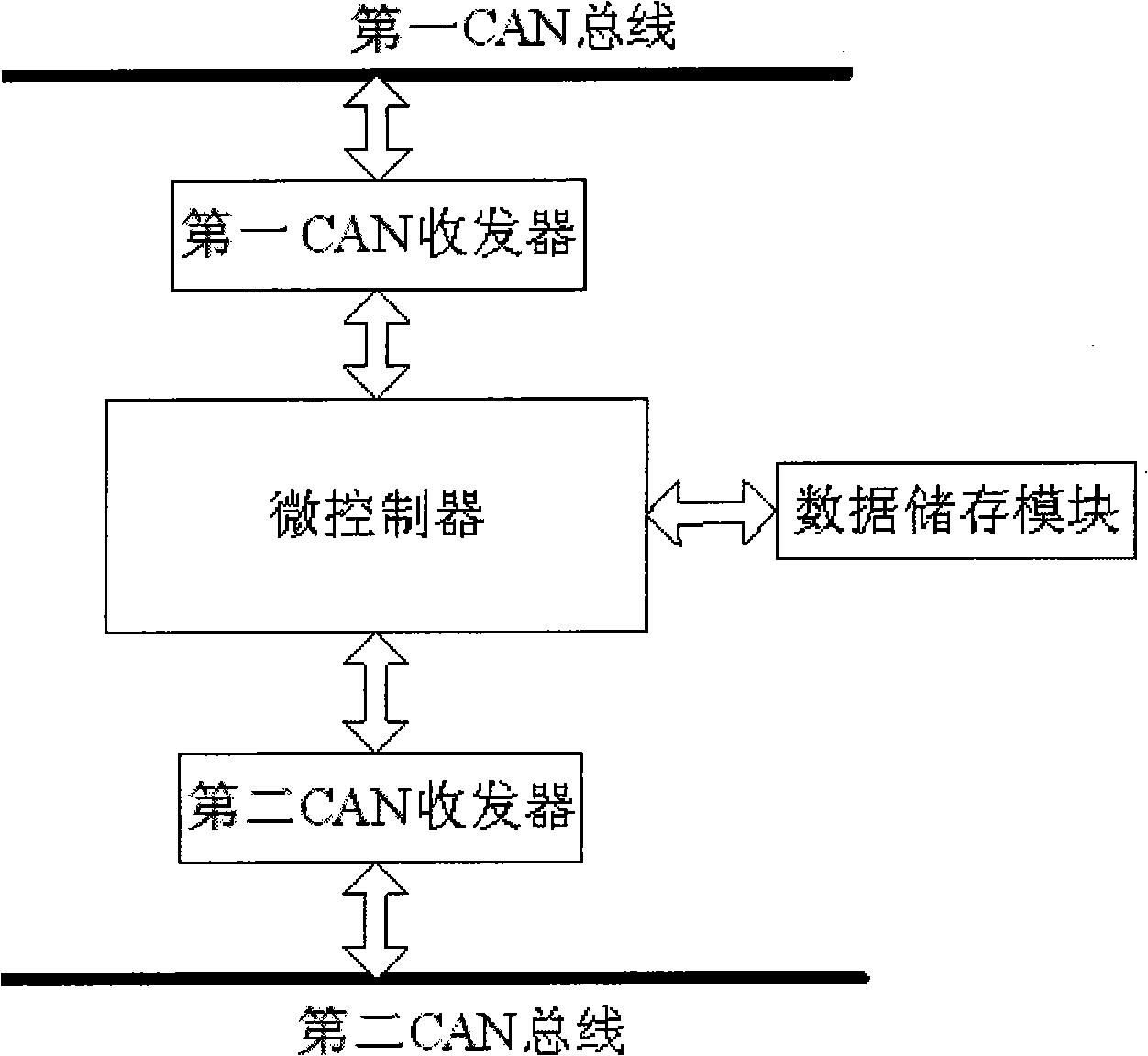
CAN bus gateway controller and data transmission method between CAN buses
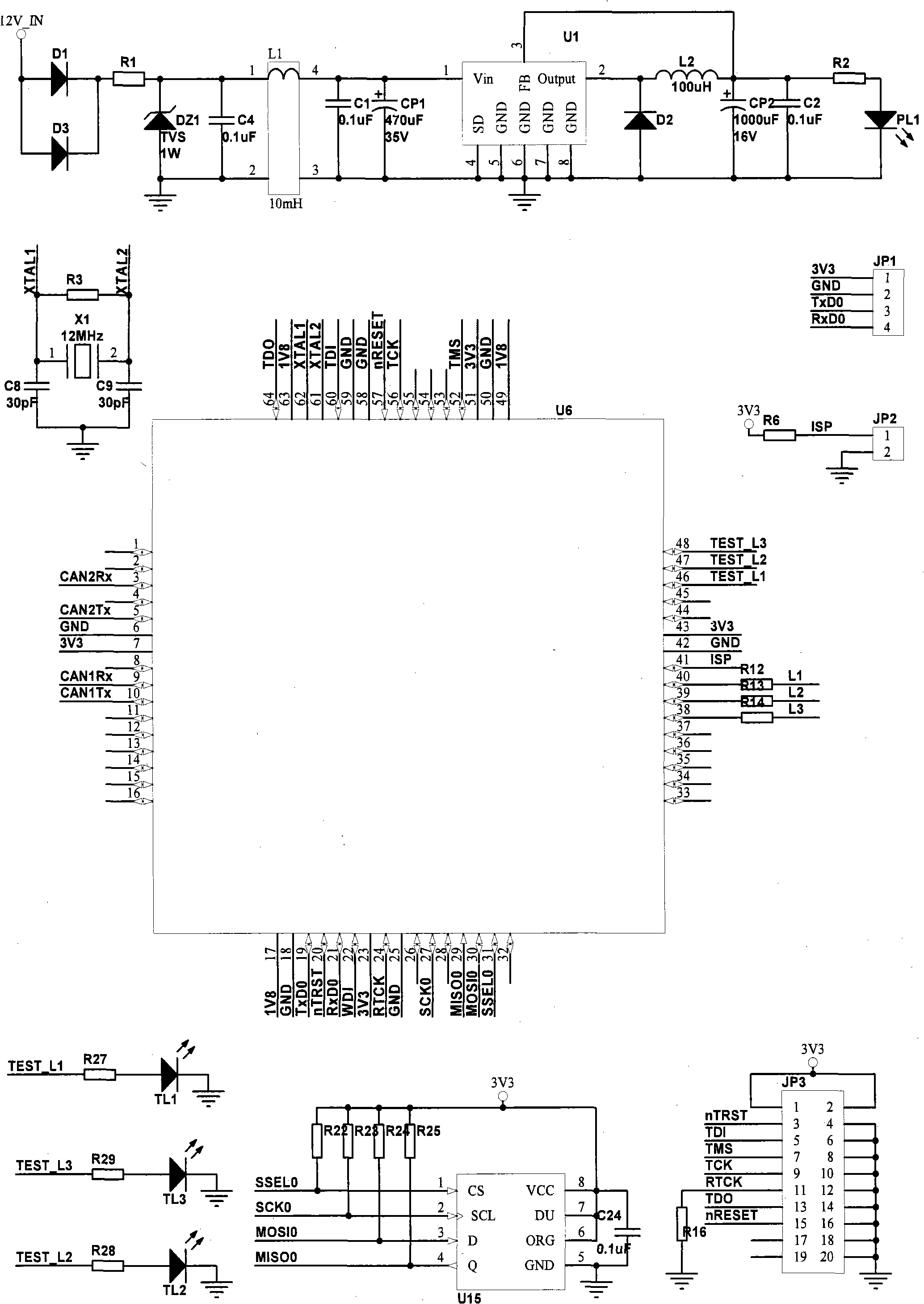
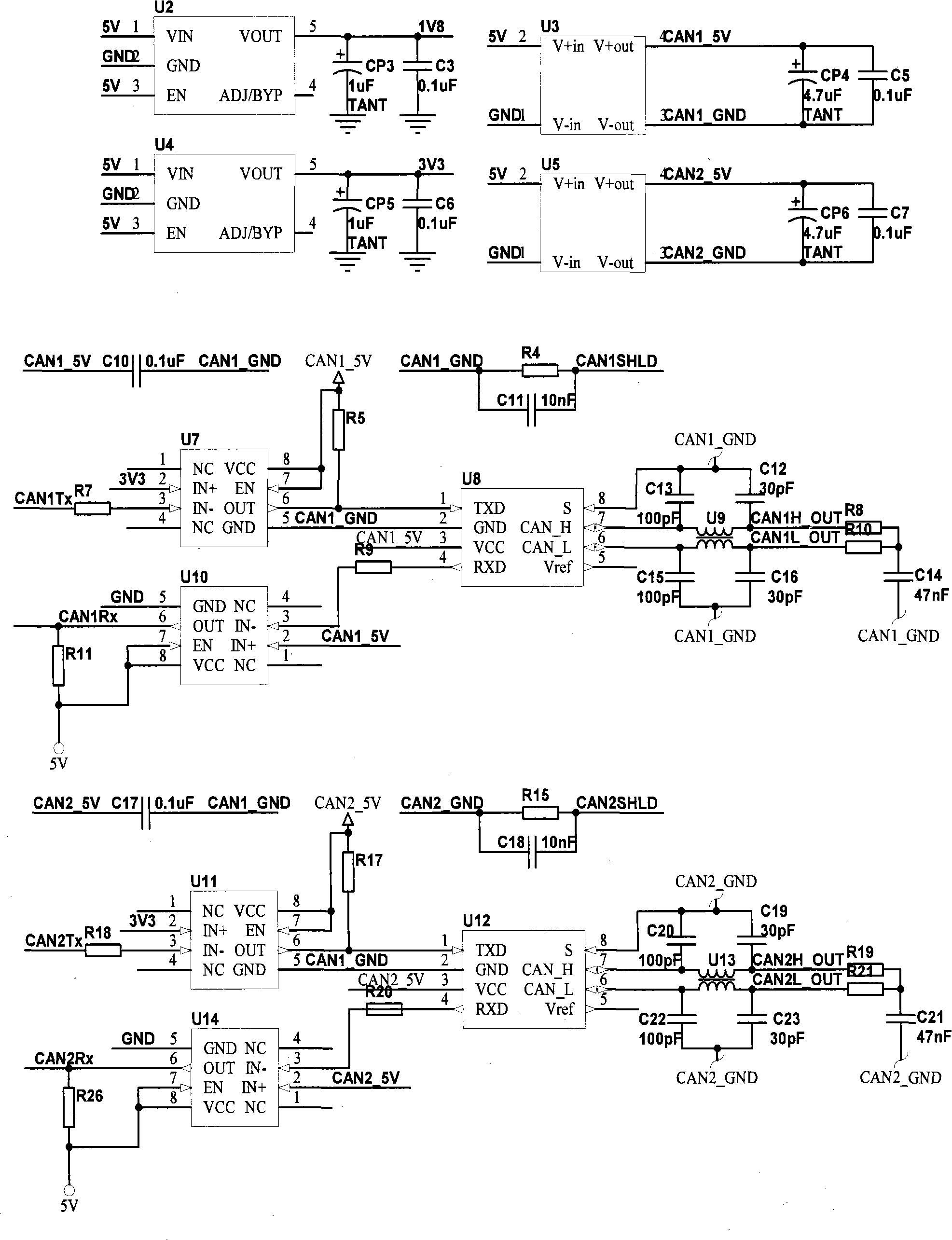
InactiveCN101360036AAvoid packet lossImprove reliabilityElectric/fluid circuitBus networksData transmissionTransceiver
The invention discloses a CAN bus gateway controller and a data transmission method of CAN buses, and the gateway controller comprises a first CAN transceiver, a second CAN transceiver, a microcontroller and a data storage module, and the first CAN transceiver, the second CAN transceiver and the data storage module are respectively connected with the microcontroller. The method can effectively prevent the condition of data packet loss caused by inconsistent protocol and velocity of two CAN buses and improve the reliability of data transmission through the forwarding control and arrangement of data buffering; meanwhile, communication status diagnosis results of each node can be sent out periodically, then each node on the CAN buses can know the network status of other nodes, and the real-time monitoring is simple, so as to favor the development of network communications and facilitate the fault detection and data analysis. The CAN bus gateway controller only need two identical CAN transceivers, the hardware configuration is simple, the compatibility problem does not exist, and the reliability is higher.
Owner:BYD CO LTD
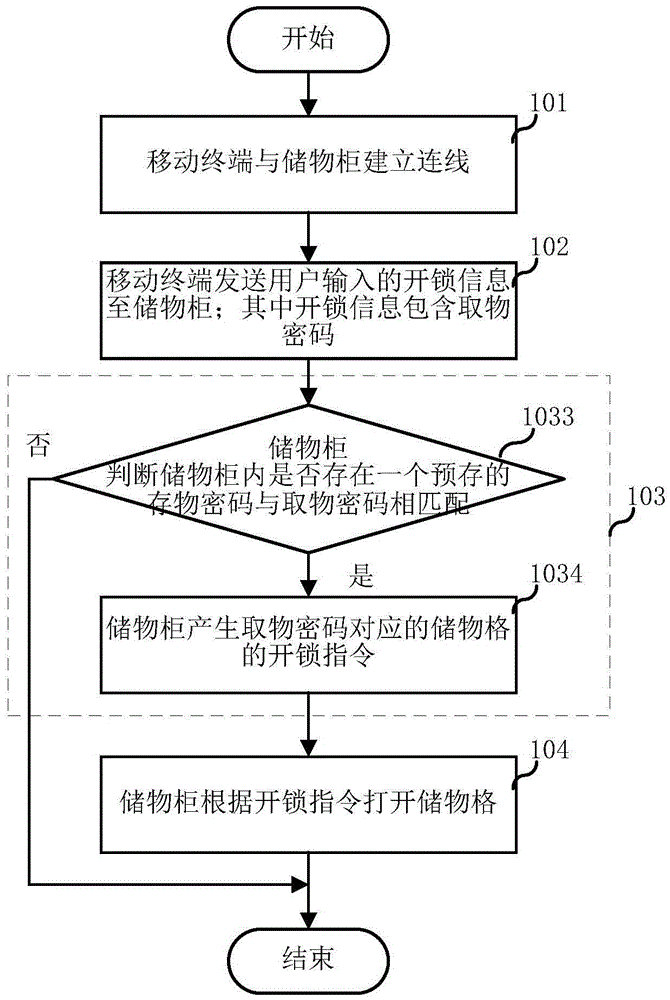
Storage cabinet, mobile terminal and storage cabinet control method and system
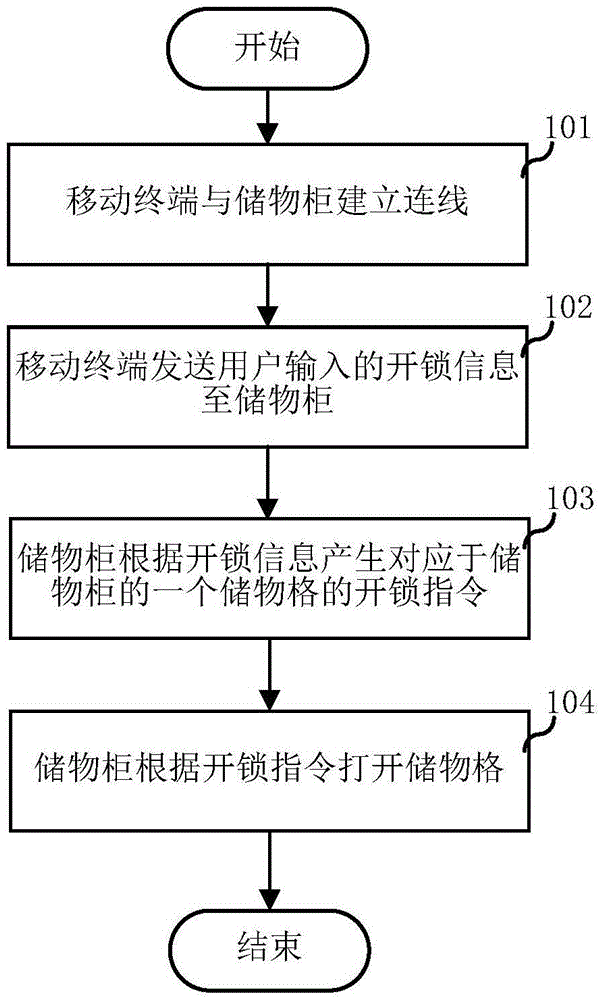
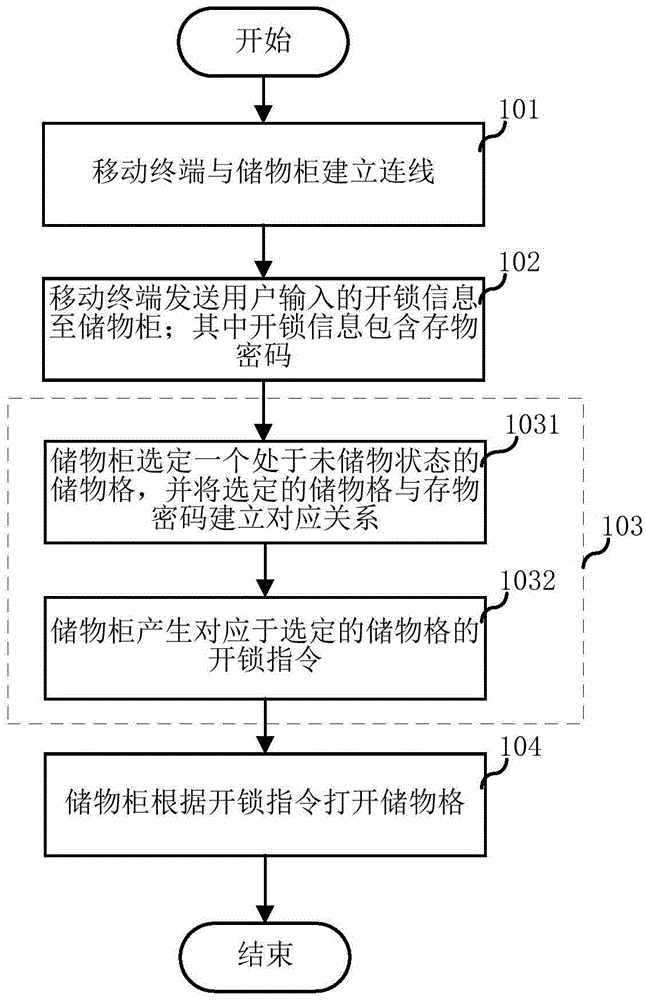
InactiveCN105469508ARealize unlock controlReduce use costApparatus for meter-controlled dispensingIndividual entry/exit registersControl systemUser input
The invention relates to the field of intelligent control and discloses a storage cabinet, a mobile terminal and a storage cabinet control method and system. The storage cabinet control method comprises the following steps that the mobile terminal and the storage cabinet are wired; the mobile terminal sends unlocking information input by a user to the storage cabinet; the storage cabinet generates an unlocking instruction corresponding to one storage box of the storage cabinet according to the unlocking information; the storage cabinet unlocks the storage box according to the unlocking instruction. By means of the storage cabinet, the mobile terminal and the storage cabinet control method and system, the user can store an article into the storage cabinet or take an article out of the storage cabinet through the mobile terminal carried with the user, queuing is not needed, and operation is easy and convenient; in addition, the use cost of the storage cabinet is reduced.
Owner:SHANGHAI CHUANGGONG COMM TECH
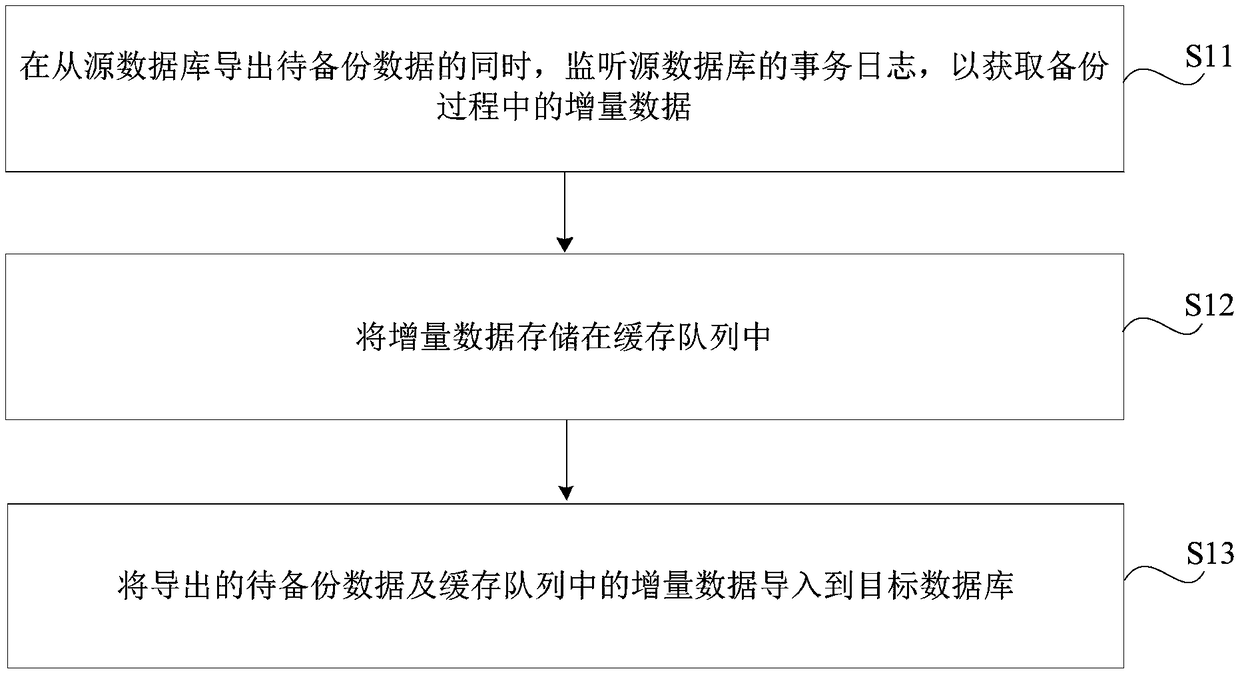
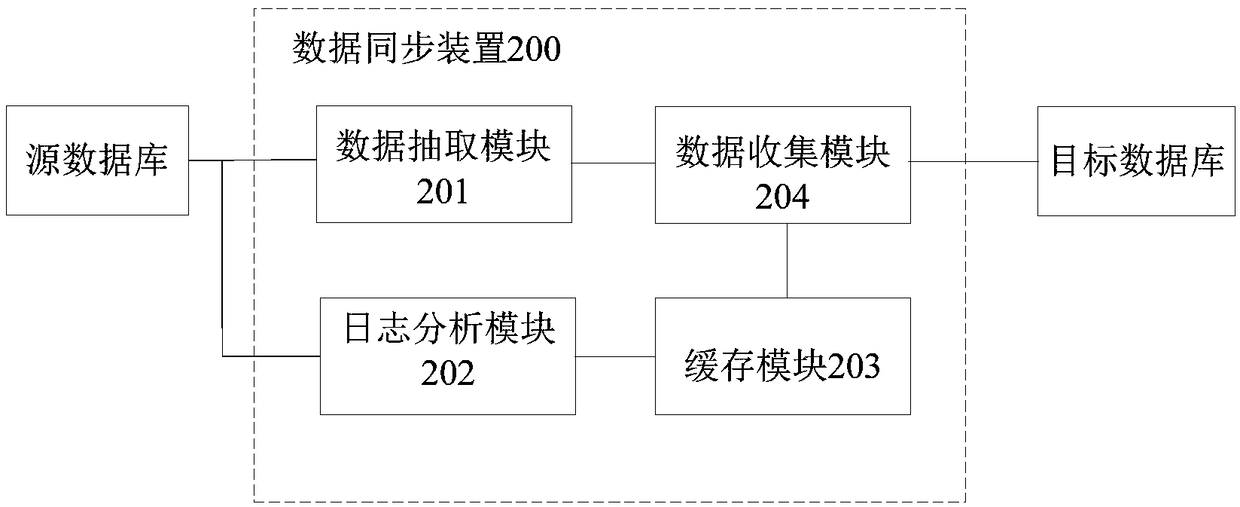
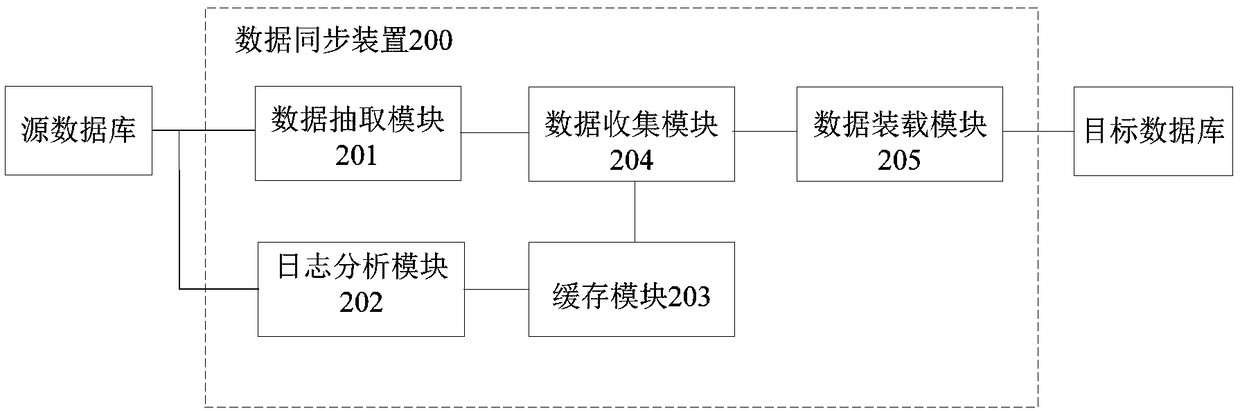
Data synchronization method, apparatus, storage medium, and electronic apparatus
ActiveCN109241175AAvoid lossSimplify the data synchronization processDatabase updatingDatabase distribution/replicationIncremental backupData synchronization
The invention relates to a data synchronization method, a device, a storage medium and an electronic device, which can simultaneously carry out steps of data initialization and incremental synchronization, simplifies the process of the whole database synchronization, and avoids incremental synchronization errors caused by cleaning transaction logs. The method comprises the following steps: while the data to be backed up is derived from the source database, the transaction log of the source database is monitored to obtain incremental data in the backup process; storing the incremental data in acache queue; the exported data to be backed up and the incremental data in the cache queue are imported to the target database.
Owner:NEUSOFT CORP
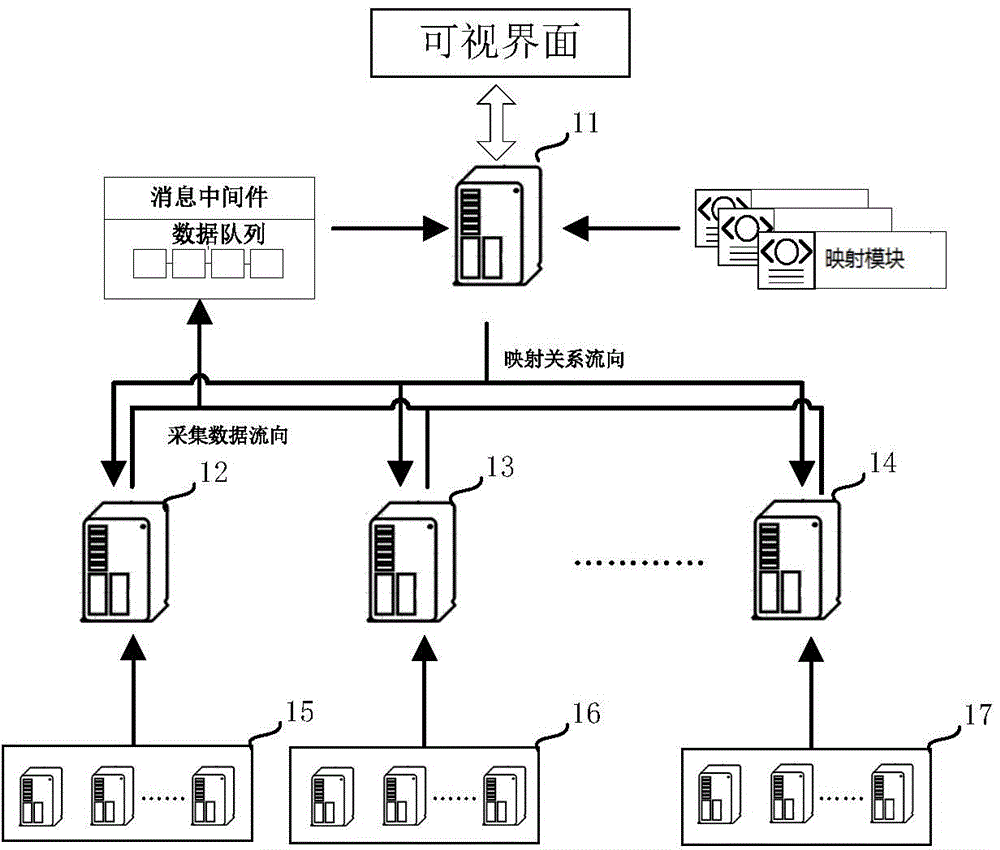
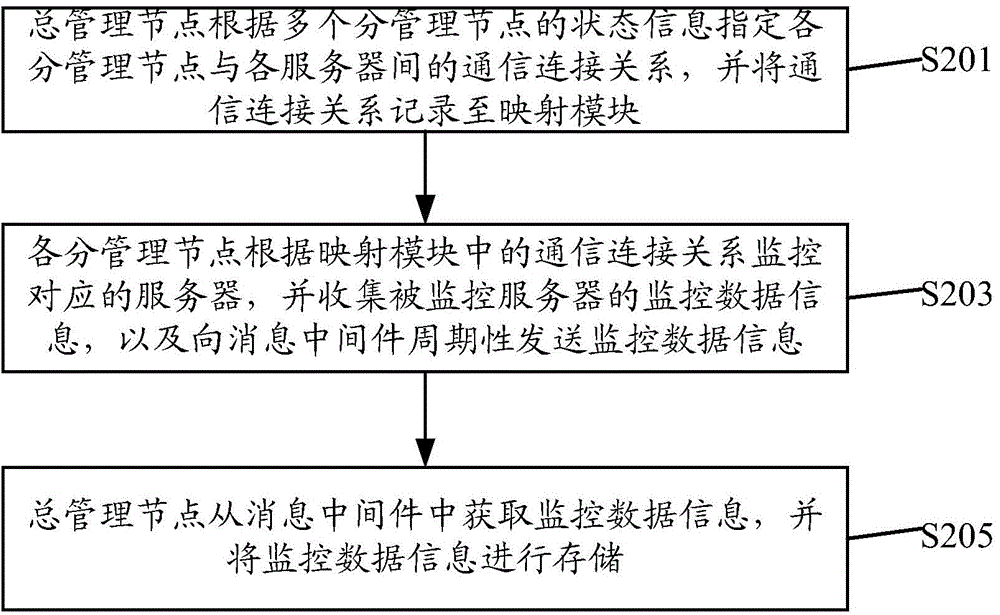
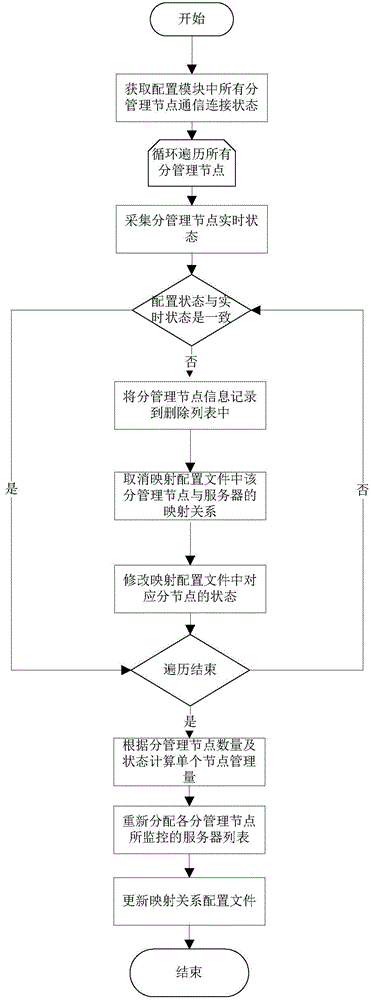
Distributed monitoring system and method
ActiveCN104935482AEfficient asynchronous data transferPrevent lossData switching networksMonitoring dataMonitoring status
The invention discloses a distributed monitoring system and method. The system comprises a main management node and sub management nodes, wherein the main management node is used for monitoring status information of sub management nodes and appointing a communication connection relation between each sub management node and each server according to the status information, and recording the communication connection relation to a mapping module; the main management node is further used for acquiring monitor data information of the server sent by each sub management node and stored in message-oriented middleware, and storing the monitor data information; the sub management node is used for monitoring the server communicated with the sub management node according to the communication connection relation in the mapping module, and collecting the monitor data information of the monitored server, and then periodically sending the monitor data information to the message-oriented middleware.
Owner:DAWNING INFORMATION IND BEIJING +1
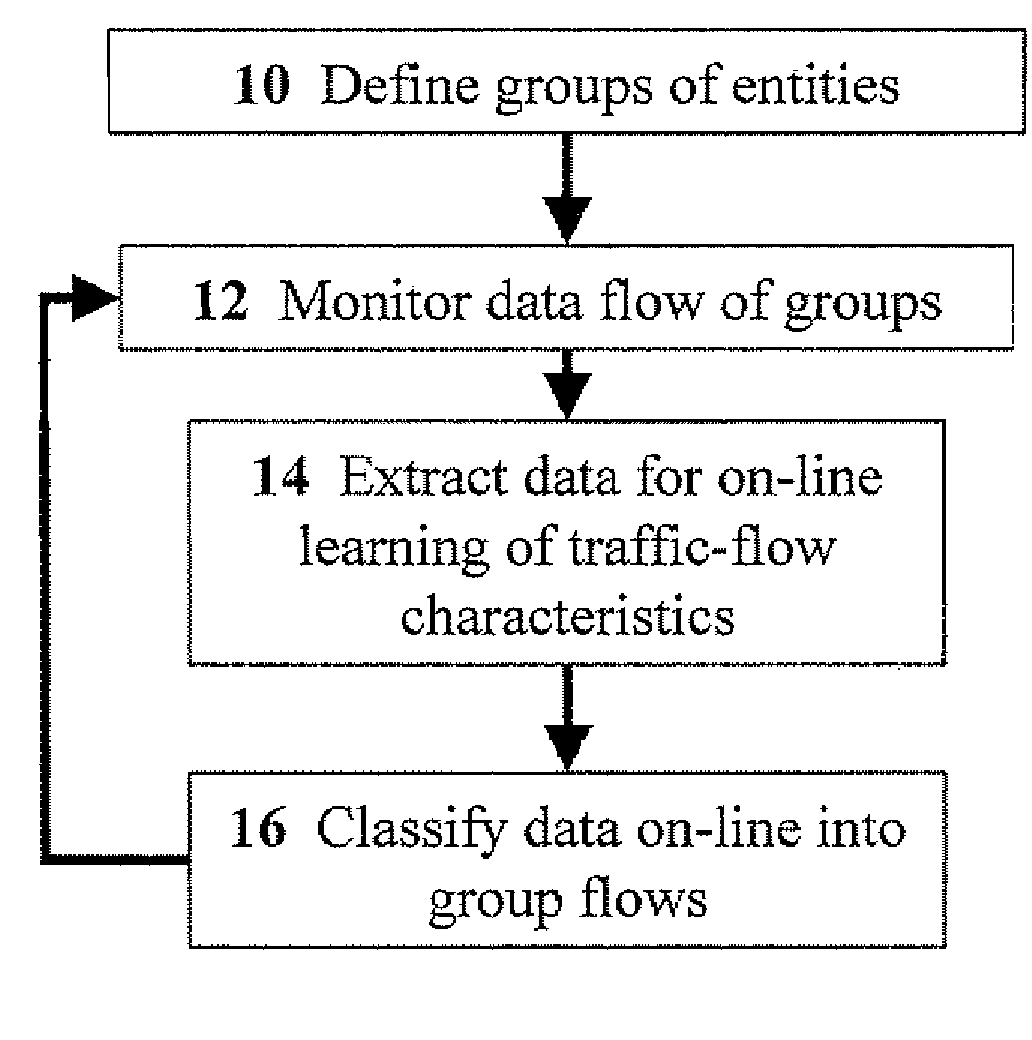
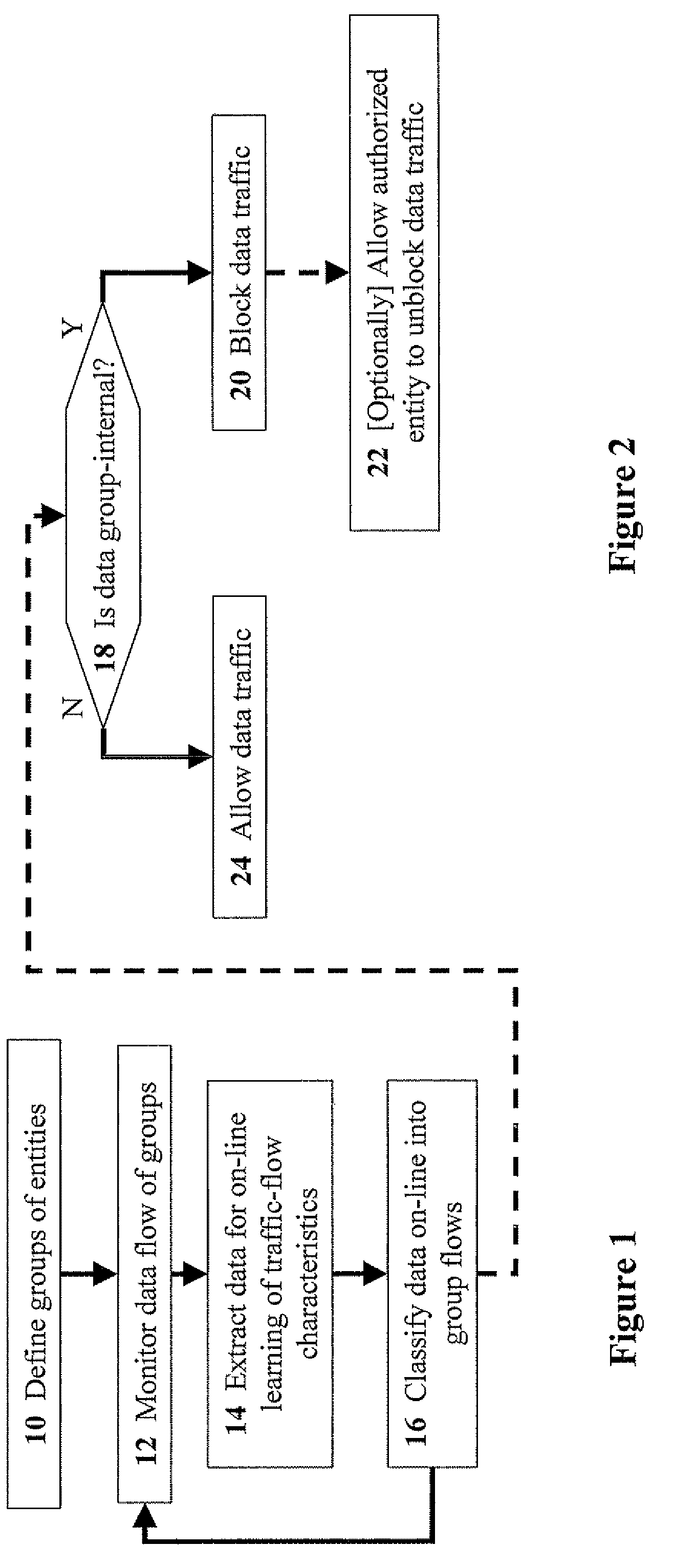
Methods for automatic categorization of internal and external communication for preventing data loss
ActiveUS20100161830A1Prevent lossAvoid data lossEnergy efficient ICTMultiple digital computer combinationsTraffic volumeTraffic capacity
Disclosed are methods for automatic categorization of internal and external communication, the method including the steps of: defining groups of entities that transmit data; monitoring data flow of the groups; extracting the data, from the data flow, for learning traffic-flow characteristics of the groups; classifying the data into group flows; upon the data being transmitted, checking the data to determine whether the data is designated as group-internal; and blocking data traffic for data that is group-internal. Preferably, the step of monitoring includes assigning data weights to the data using Bayesian methods. Most preferably, the step of classifying includes classifying the data using Bayesian methods for evaluating the data weights. Preferably, the step of blocking includes blocking data traffic between members of two or more groups. Preferably, the method further includes the step of: enabling an authorized entity to unblock the data traffic.
Owner:CHECK POINT SOFTWARE TECH LTD
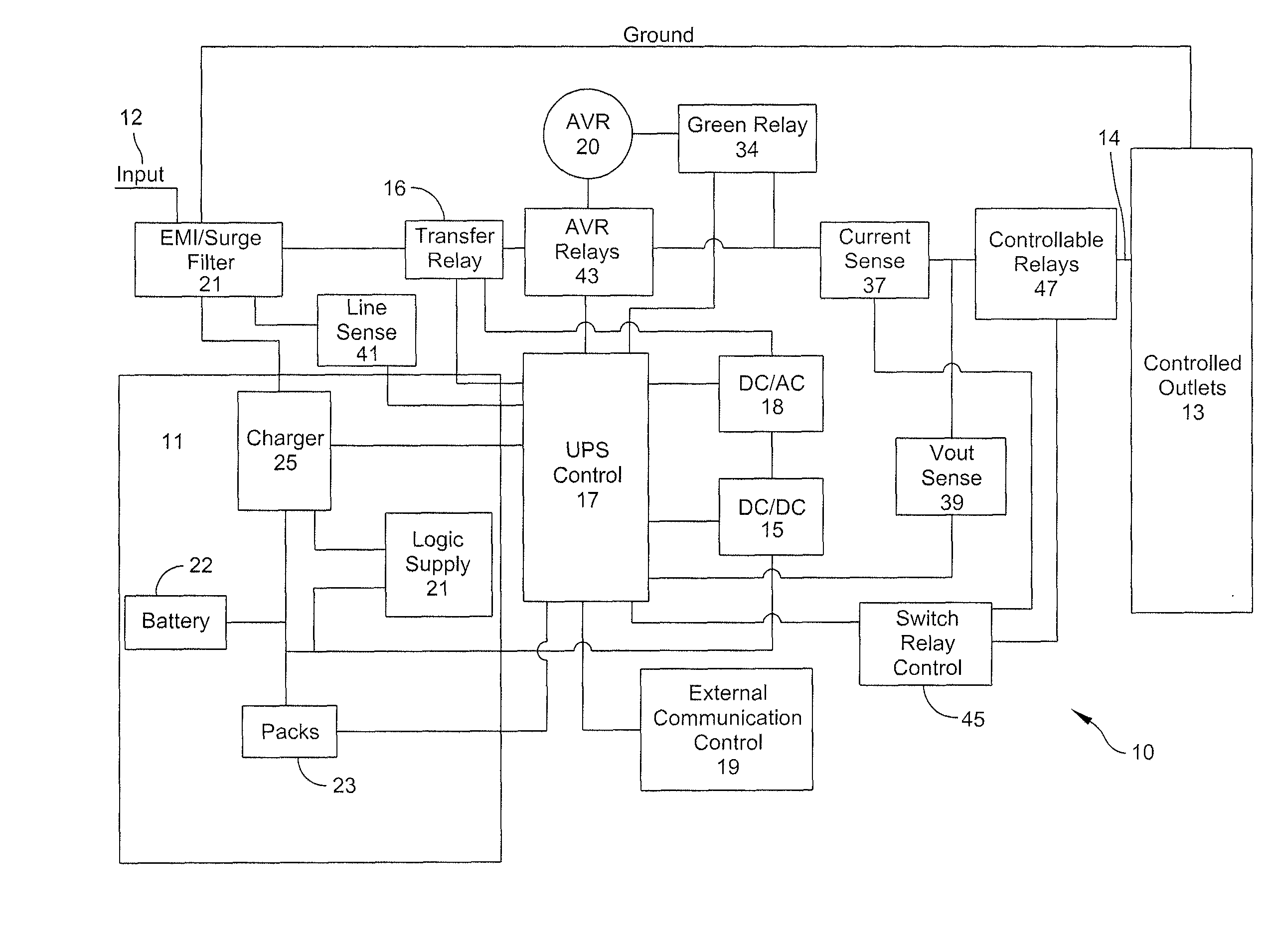
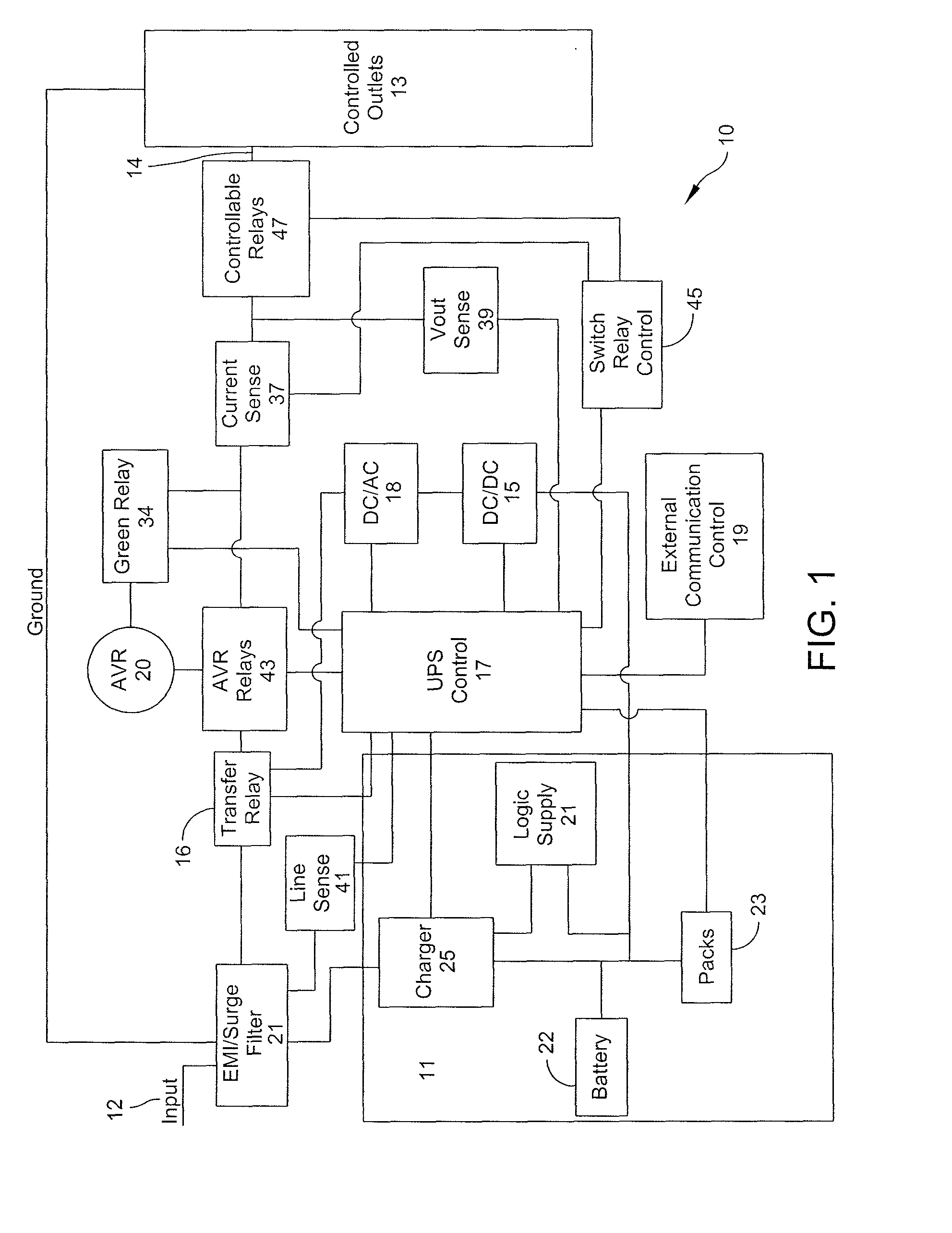
System and method for limiting losses in an uninterruptible power supply
ActiveUS20100188066A1Reduce energy lossPrevent lossBatteries circuit arrangementsElectric powerVoltage regulationUninterruptible power supply
Aspects of the invention are directed to systems and method for limiting losses in an uninterruptible power supply. In one aspect, the present invention provides an uninterruptible power supply (UPS) comprising an input to receive input power having an input voltage, an output to provide output power having an output voltage, a neutral line, an automatic voltage regulation (AVR) transformer coupled to the input and the output of the UPS and having an input, an output, a core and at least one switch controllably coupled to at least one of the core, the input and the output, and a means for isolating the core of the AVR transformer from the neutral line when the input voltage is substantially equal to a defined output voltage.
Owner:SCHNEIDER ELECTRIC IT CORP
Data storage method and device, terminal equipment and storage medium
ActiveCN109597568APrevent lossIntegrity guaranteedInput/output to record carriersData synchronizationTerminal equipment
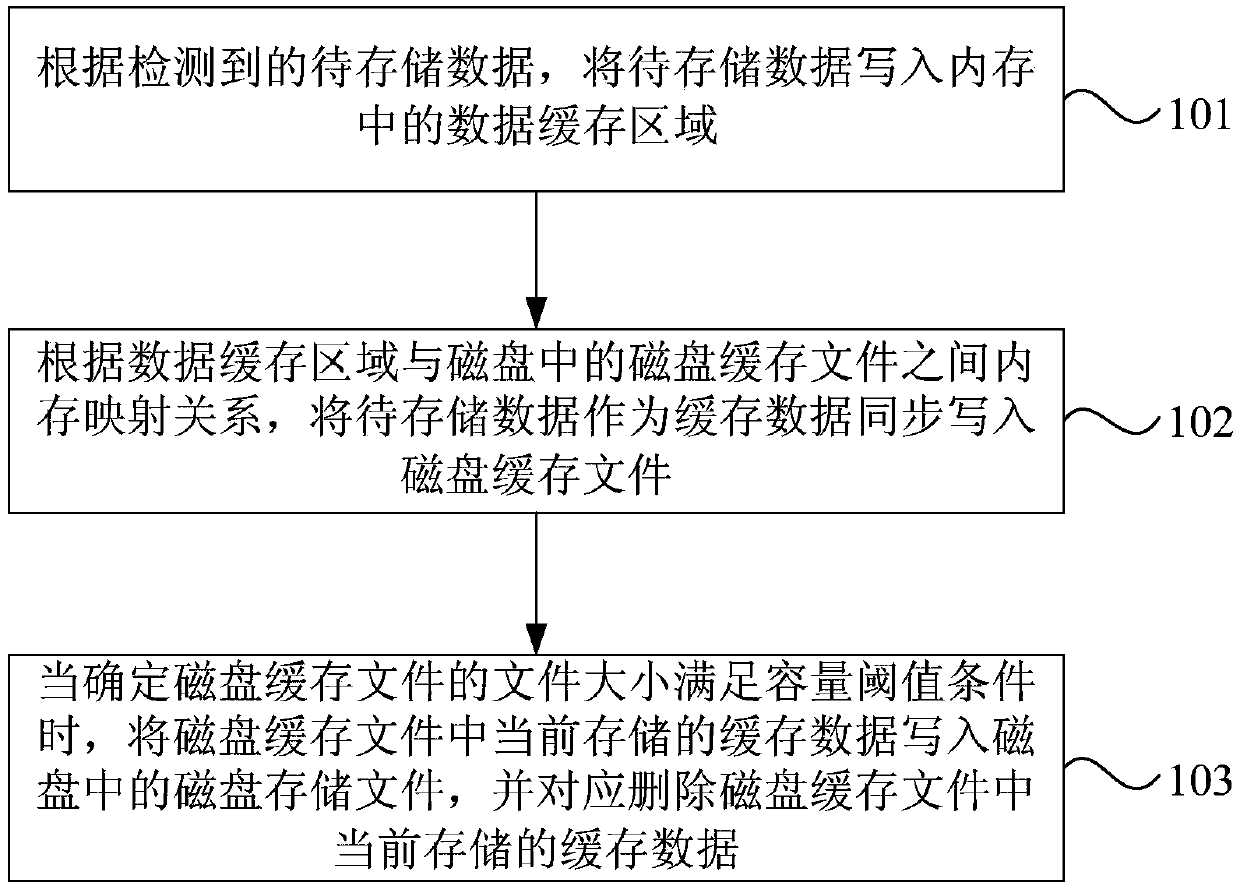
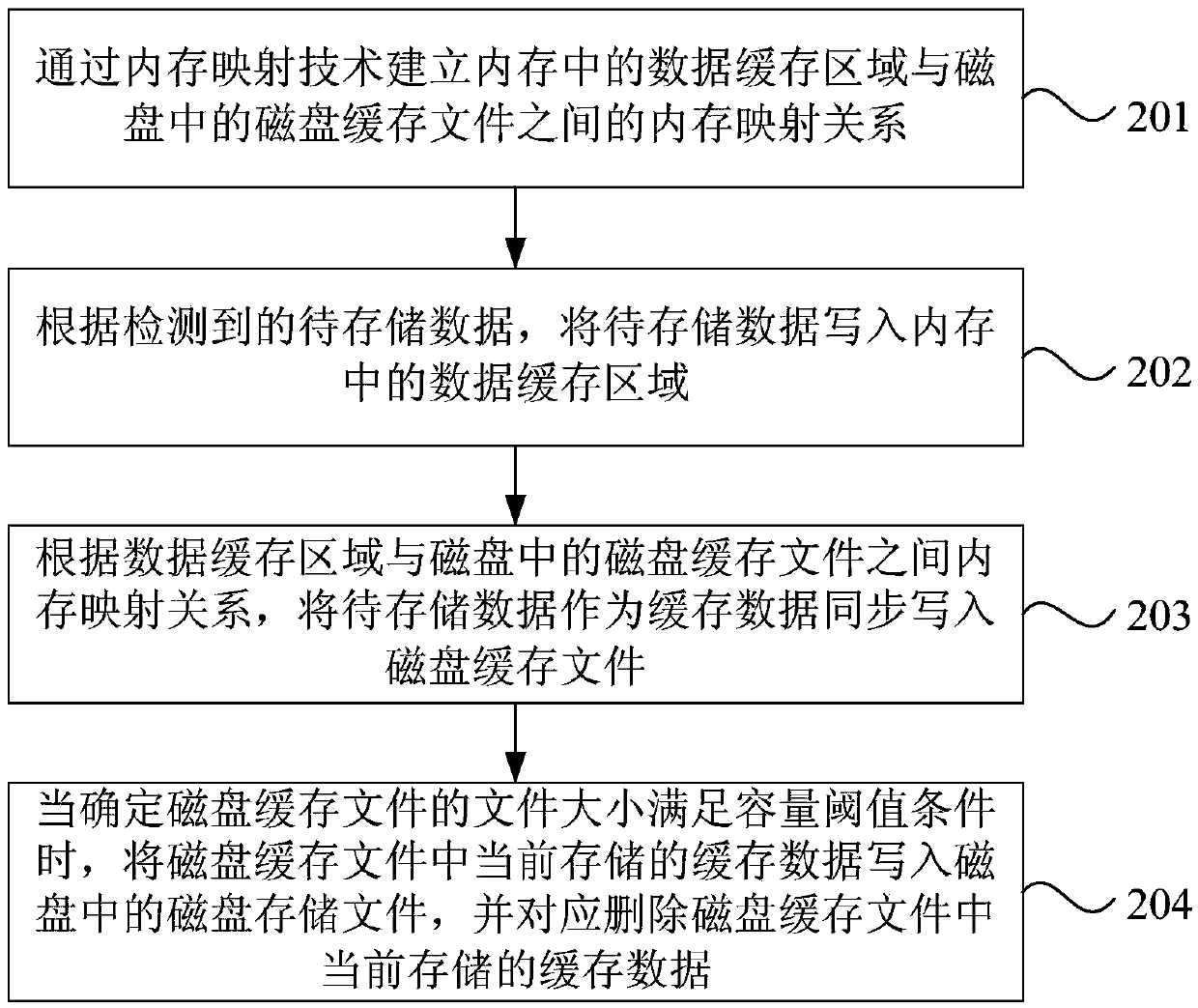
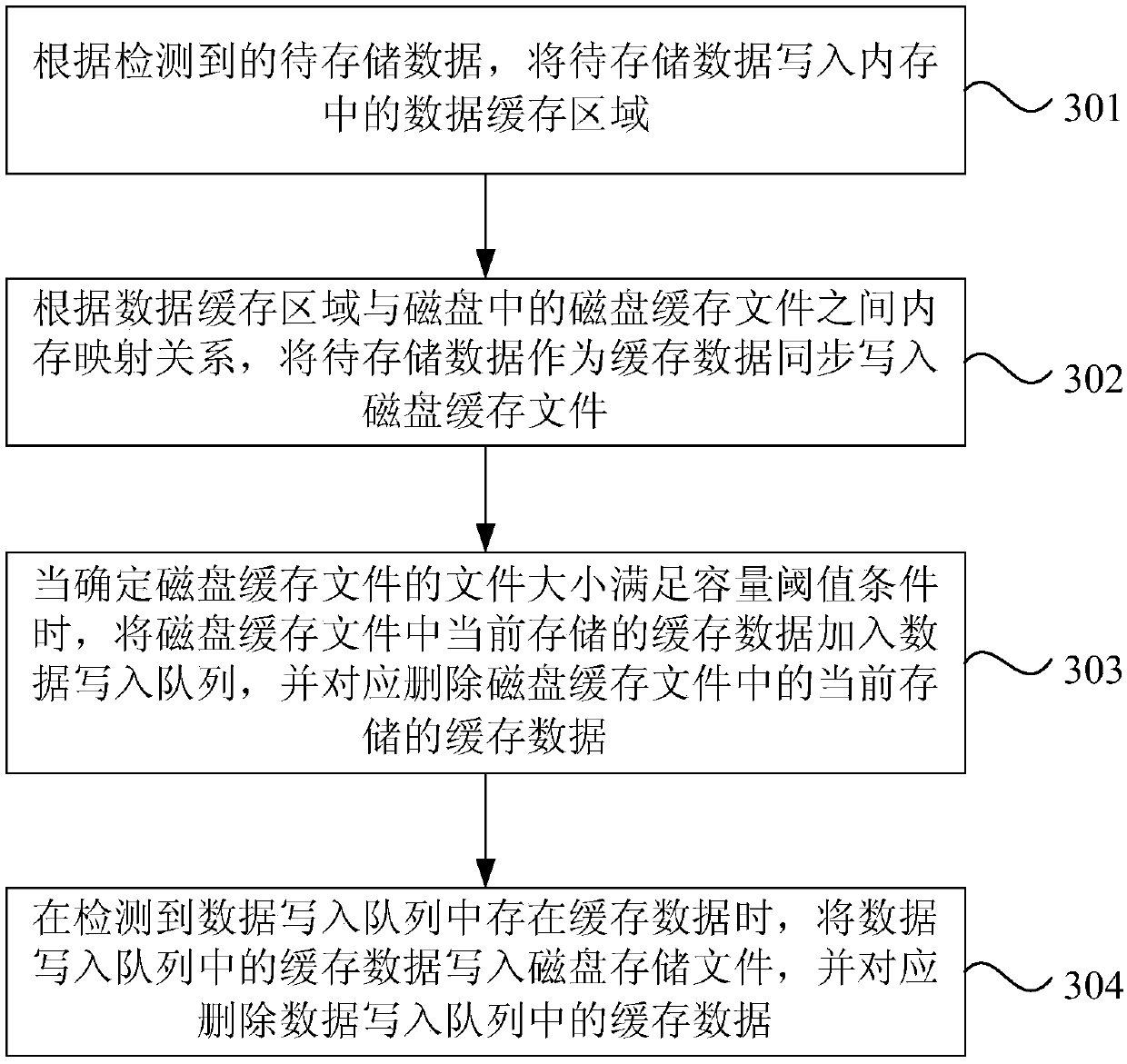
The invention discloses a data storage method and device, terminal equipment and a storage medium. The method comprises the steps that according to detected to-be-stored data, writting the to-be-stored data into a data caching area in a memory; Synchronously writing the to-be-stored data as cache data into a disk cache file according to a memory mapping relation between the data cache area and thedisk cache file in the disk; And when it is determined that the data size of the disk cache file meets the capacity threshold condition, writing the cache data currently stored in the disk cache fileinto a disk storage file in a disk, and correspondingly deleting the cache data currently stored in the disk cache file. The embodiment of the invention can avoid the condition of data loss caused byusing a memory caching technology in the prior art, and can effectively reduce the frequency of input / output operation, reduce the system power consumption and improve the system performance while ensuring the integrity of the data.
Owner:脸萌技术(深圳)有限公司
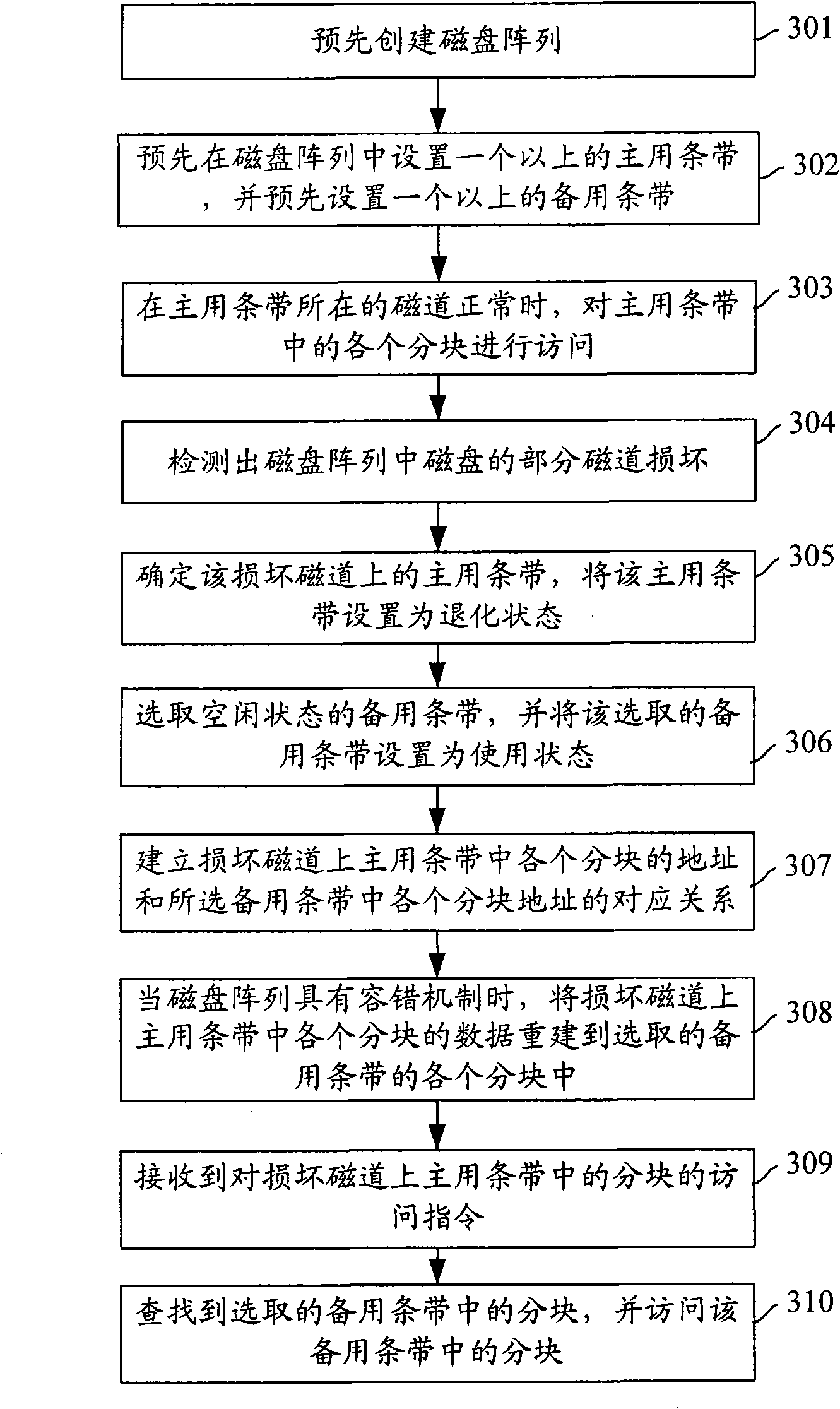
Method for improving usability of disk and disk array controller
InactiveCN101567211AImprove usabilityAvoid replacementInput/output to record carriersError detection/correctionDisk controllerParallel computing
The invention discloses a method for improving the usability of a disk and a disk array controller. The method comprises the following steps of: arranging a main data memory space in a disk array; arranging more than one backup data memory spaces; determining a first main data memory space on the damaged track when detecting the damage of part track of the disk in the disk array; selecting an idle first backup data memory space; establishing a corresponding relationship between the block addresses contained by the first main data memory space and the block addresses contained by the first backup data memory space; receiving the visiting instructions of the block contained by the first main data memory space; querying the blocks contained by the first backup data memory space according to the block address in the visiting instructions and the corresponding relationship; and visiting the block contained by the first backup data memory space. The method and the disk array controller can improve the usability of the disk in the disk array.
Owner:NEW H3C TECH CO LTD
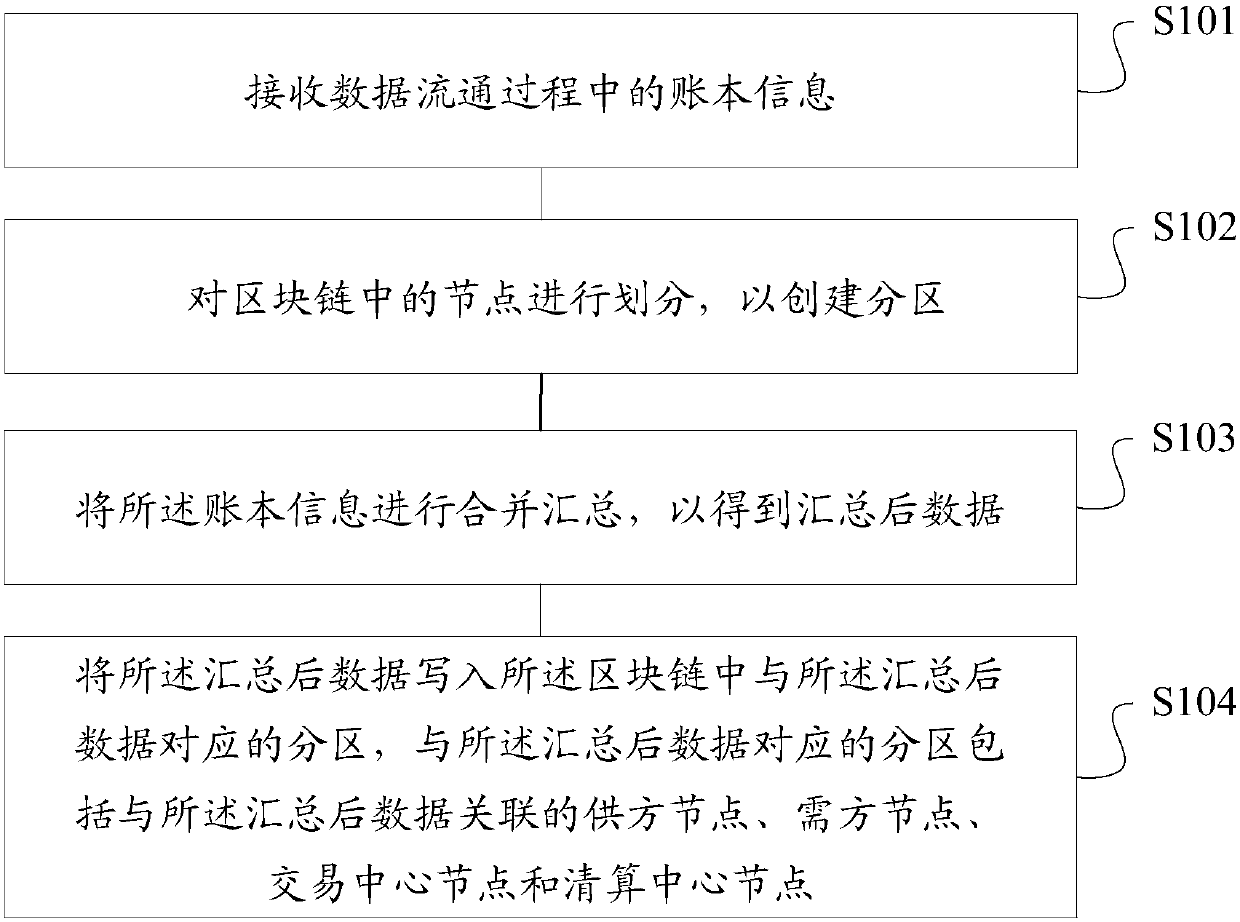
Block chain construction method and device for data communication, storage medium and server
ActiveCN107786642AImprove the efficiency of reaching consensusAccelerate the speed of entering the chainFinanceUser identity/authority verificationTime distributionNetwork overhead
The invention provides a block chain construction method and device for data communication, a storage medium and a server. The block chain construction method comprises the steps that account book information generated in the data communication process is received; nodes in a block chain are partitioned to create partitions; the account book information is combined and summarized to obtain summarized data; and the summarized data is written into the partitions, corresponding to the summarized data, in the block chain, wherein the partitions corresponding to the summarized data comprise supplier nodes, demander nodes, transaction center nodes and clearing center nodes which are associated with the summarized data. According to the technical scheme, the block chain which is applied to the data communication field, achieves quick chaining, reduces the network overhead and saves the storage space can be provided to meet the application requirement of real-time distribution of high-concurrency and massive data.
Owner:上海数据发展科技有限责任公司
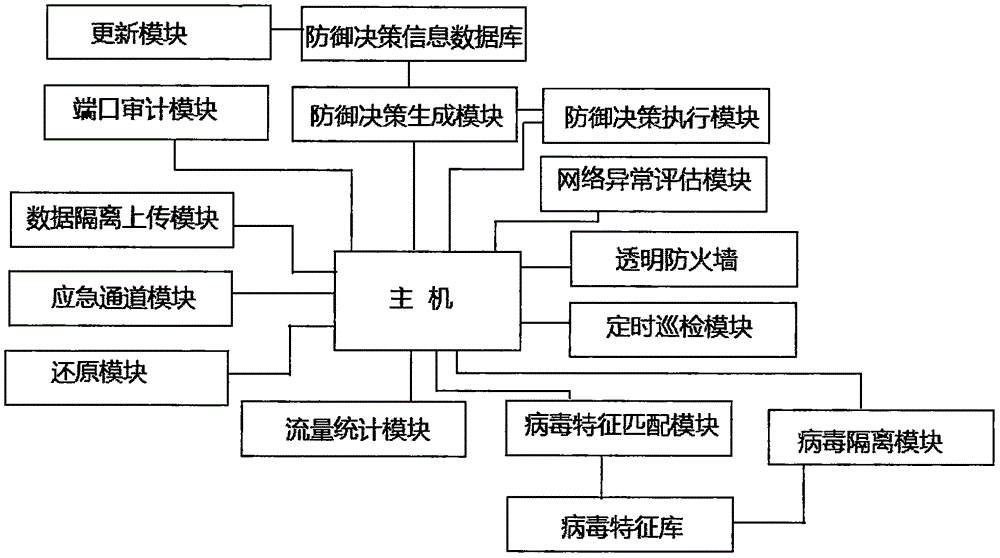
Computer network defense decision system
InactiveCN105847291AWell maintainedImprove immunityMessaging/mailboxes/announcementsPlatform integrity maintainanceDecision schemeDecision system
The invention discloses a computer network defense decision-making system, which includes a transparent firewall, a regular inspection module, a virus isolation module, a virus feature matching module, a port audit module, a traffic statistics module, a network abnormality evaluation module, a defense decision generation module, and a defense decision-making module. Execution module, emergency channel module, restore module, data isolation upload module. The present invention realizes the real-time monitoring and auditing of the network flow, maintains the good state of the network; improves the immunity of the network through the analysis and memory of the unknown intrusion behavior; and can effectively control the harm range after the intrusion, ensuring the smooth flow of the network and the service It is provided normally, and at the same time, it can automatically generate and execute different defense decision-making schemes according to different network attacks, which improves the self-repair and restoration capabilities of the system, maintains the stable operation of the network, and has data protection capabilities. The occurrence of the previous situation leading to the loss of information.
Owner:INNER MONGOLIA UNIV OF TECH
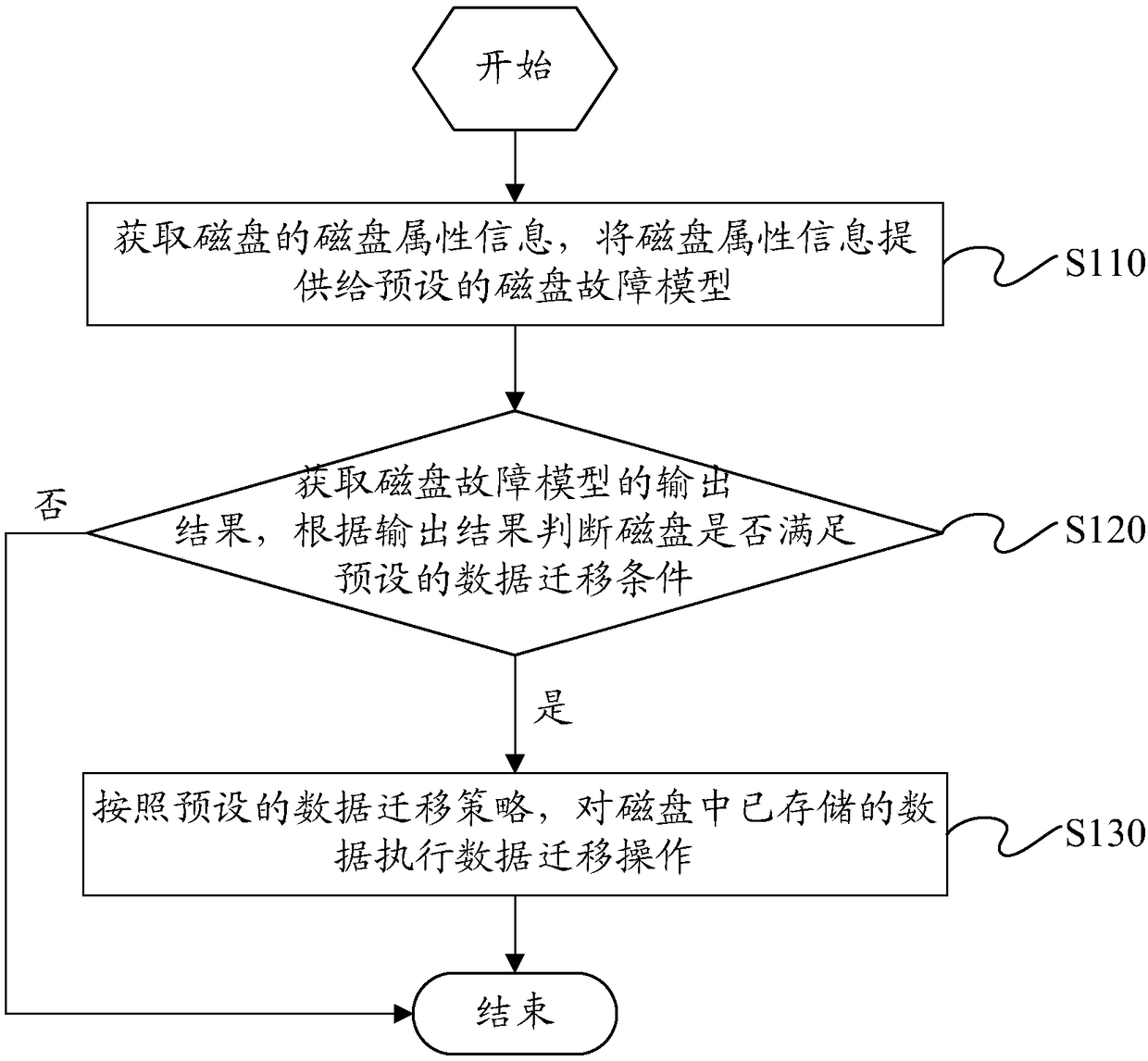
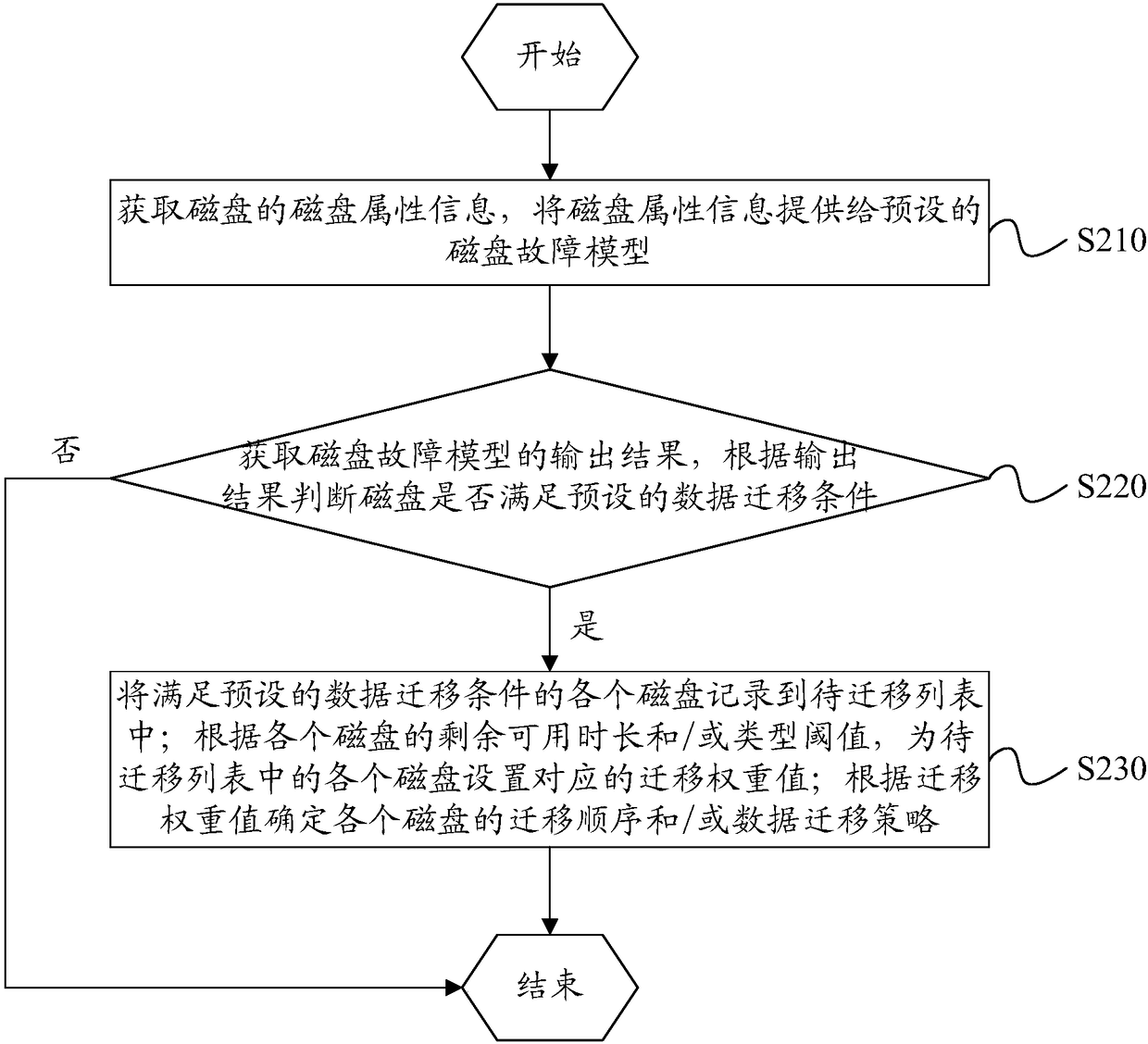
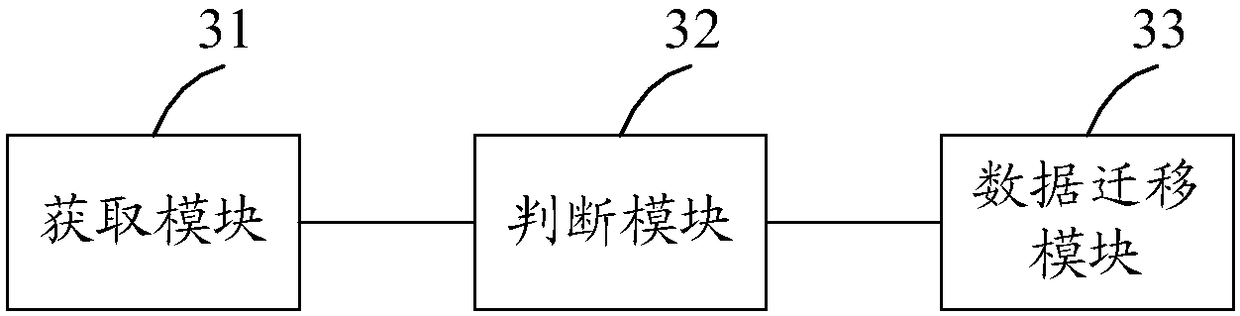
Disk-based data migration method and apparatus, and electronic device
The invention discloses a disk-based data migration method and apparatus, and an electronic device. The method comprises the steps of obtaining disk attribute information of a disk, and providing thedisk attribute information for a preset disk fault model; obtaining an output result of the disk fault model, and according to the output result, judging whether the disk meets a preset data migrationcondition or not; and if yes, according to a preset data migration policy, executing data migration operation on stored data. In the way, the fault information of the disk can be predicted in advance, and the stored data in the disk can be actively migrated before the disk has a fault, so that the situation of data loss caused by the fault of the disk is effectively avoided; and in addition, thepreset disk fault model can predict the fault information of various types of disks, so that the applicability is wide.
Owner:BEIJING QIHOO TECH CO LTD
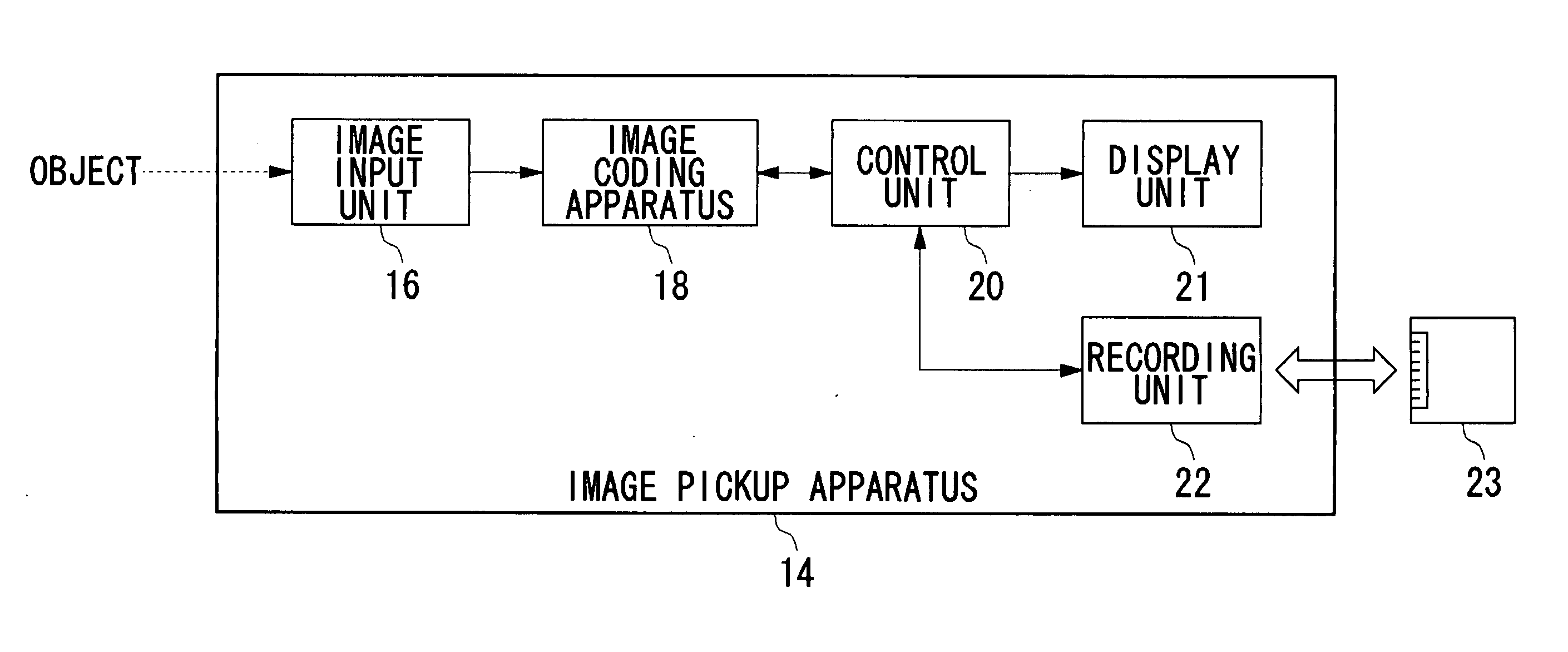
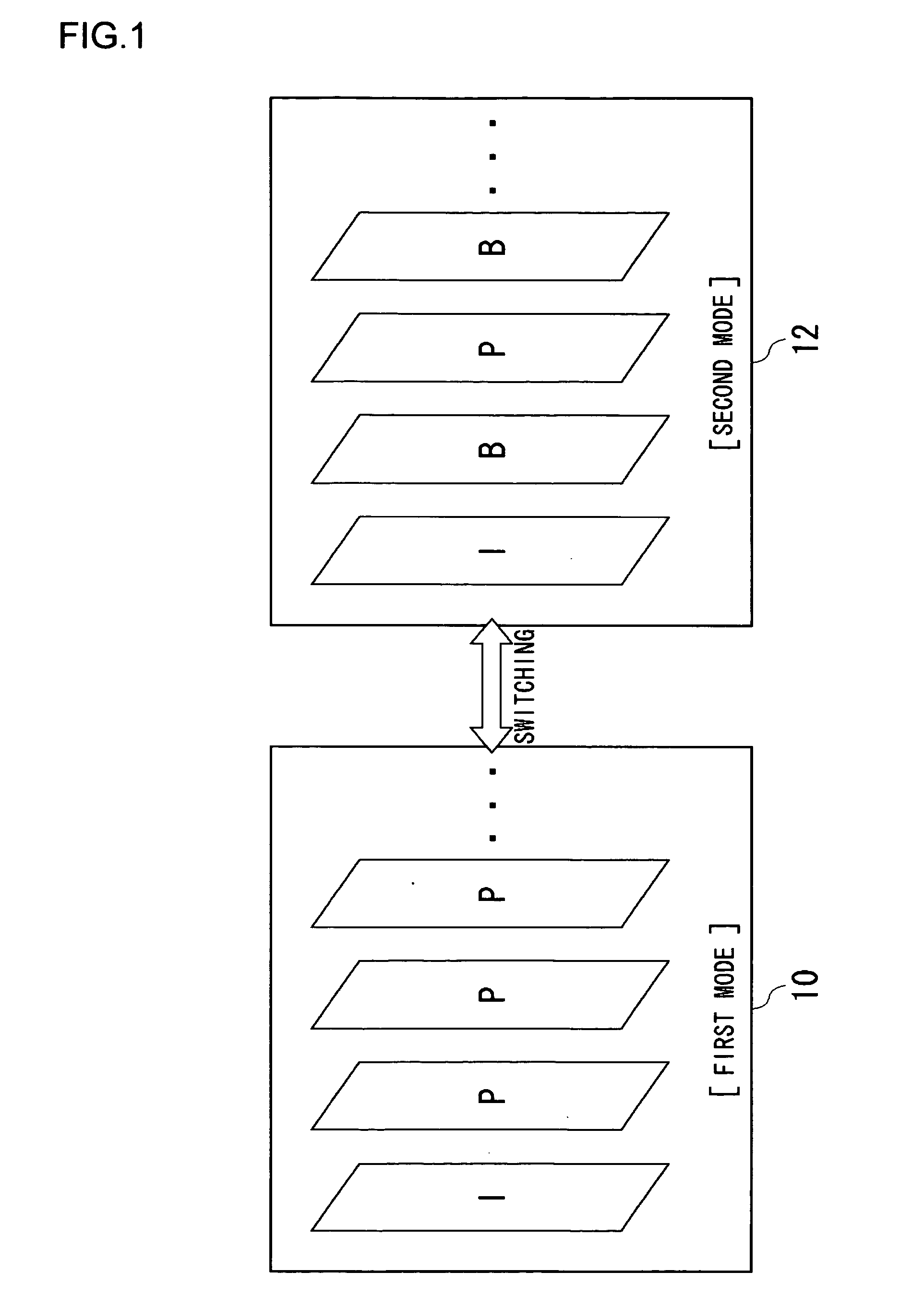
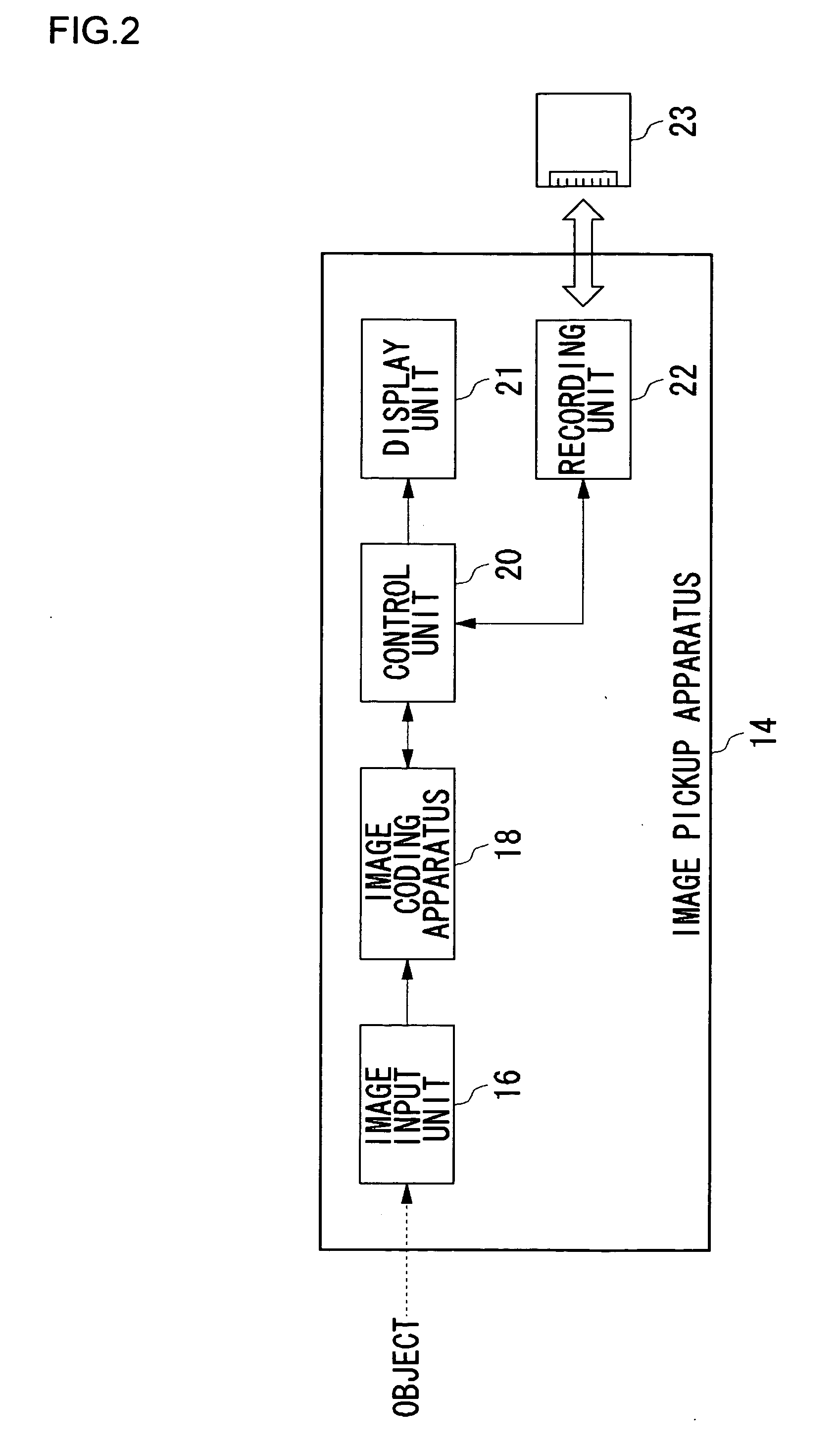
Apparatus and Method for Controlling Image Coding Mode
InactiveUS20070291131A1Prevent lossEnhance image qualityTelevision system detailsColor television with pulse code modulationImage codeData format
As result of the diversified structure of a terminal device, the demand for data format is also diversified and there is a need to adjust a terminal to such a demand. An image coding apparatus according to the present invention uses a method complied with MPEG, as a method by which to code images, and particularly uses intra-frame coding and inter-frame coding. As an inter-frame coding method, a first mode which is a reference mode using bidirectional coding and a second mode which is a reference mode not using the bidirectional coding can be selectively set. In the case of the first mode, the bidirectional coding is not used, so that B pictures are not generated and the images are coded with I pictures and P pictures only.
Owner:SANYO ELECTRIC CO LTD
Safety protecting method for application software of portable intelligent equipment
InactiveCN103634482APrevent unsafe behaviorPrevent misuse or privacy theftSubstation equipmentSecurity arrangementPrivacy protectionApplication software
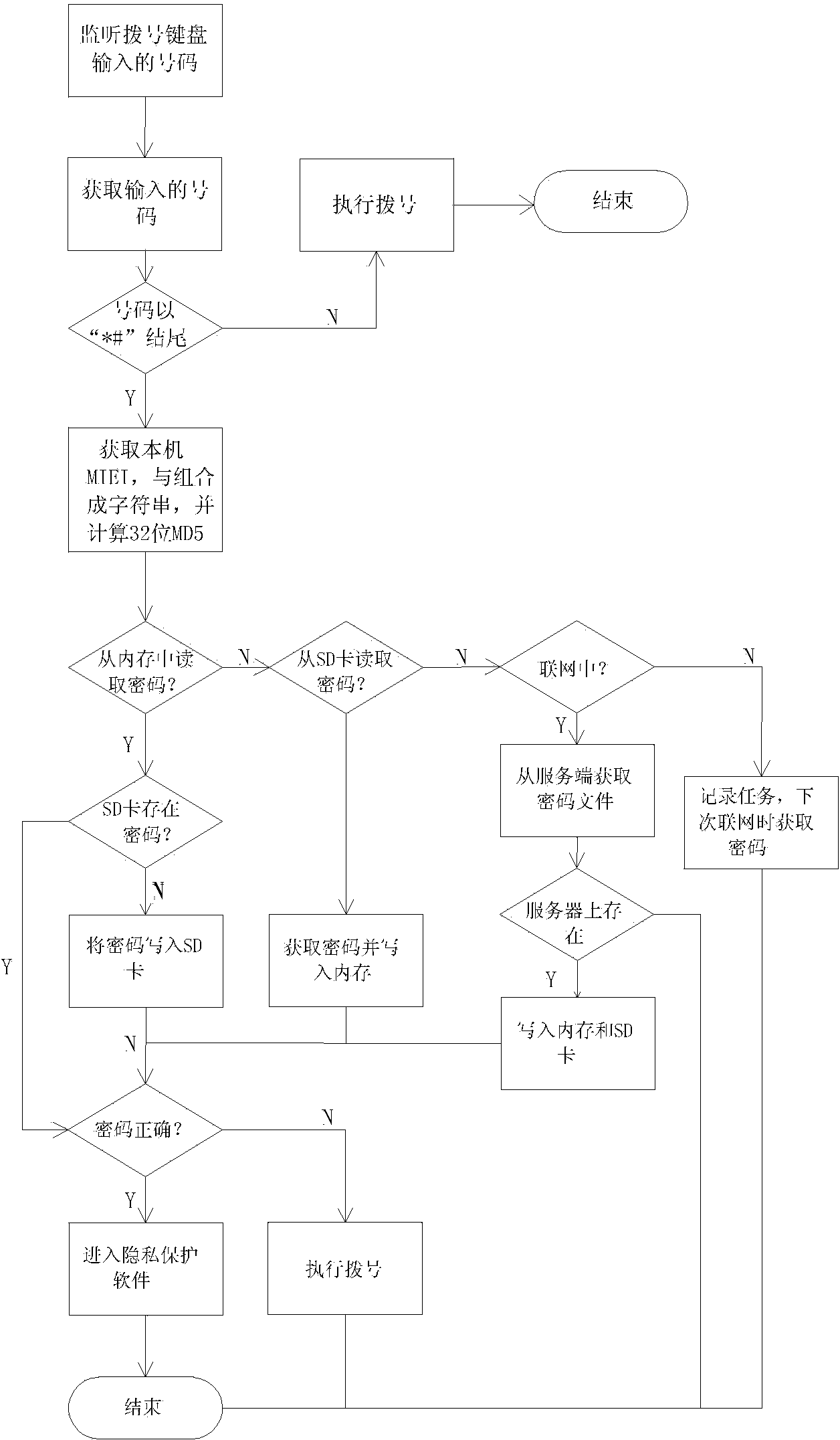
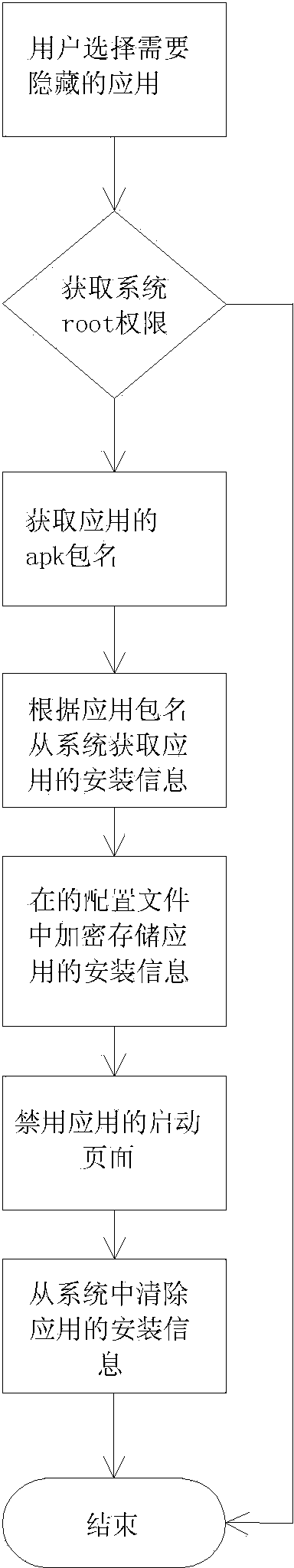
The invention discloses a safety protecting method for application software of portable intelligent equipment. The method comprises the following steps: S1, setting application software to be protected in a hidden mode; under the hidden mode, a user neither can find the application software in application programs nor can find an icon of the application software from desktop icons or icons of all application programs; S2, monitoring number input of a dialing keyboard to obtain the number input by the user to judge whether the number is ended according to a preset rule; if not, executing the dialing operation and ending the flow; if so, verifying the number input by the user according to the preset rule; after successfully verifying, entering the application software corresponding to the number; if not, executing the dialing operation. According to the method disclosed by the invention, the private application software is protected by hiding the application software, and the application software is accessed through the dialing keyboard, so that the method is convenient and efficient, and has the good practicality.
Owner:XIAMEN FULONG WORLD NETWORK TECH CO LTD
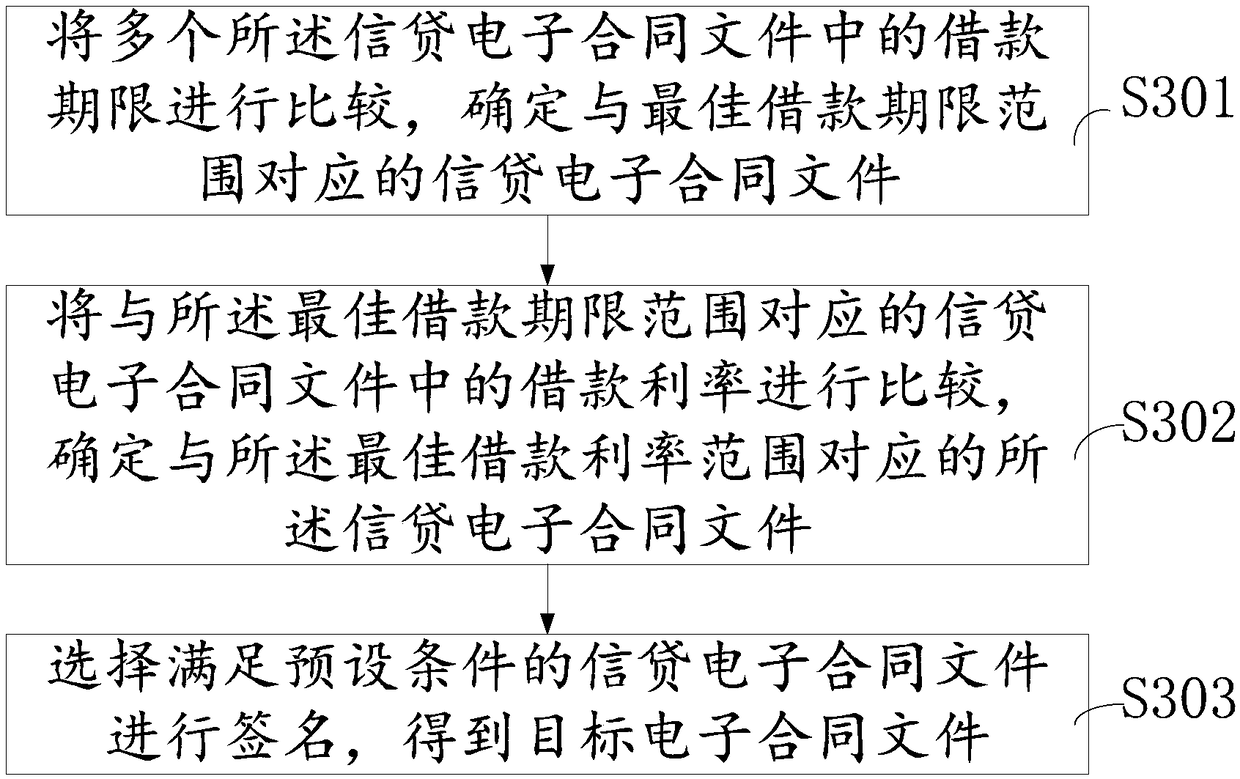
Block chain borrowing method and system
InactiveCN108399567AAvoid the possibility and loss of accounts for lending and lending transactionsEnsure safetyFinancePayment protocolsChain systemBlockchain
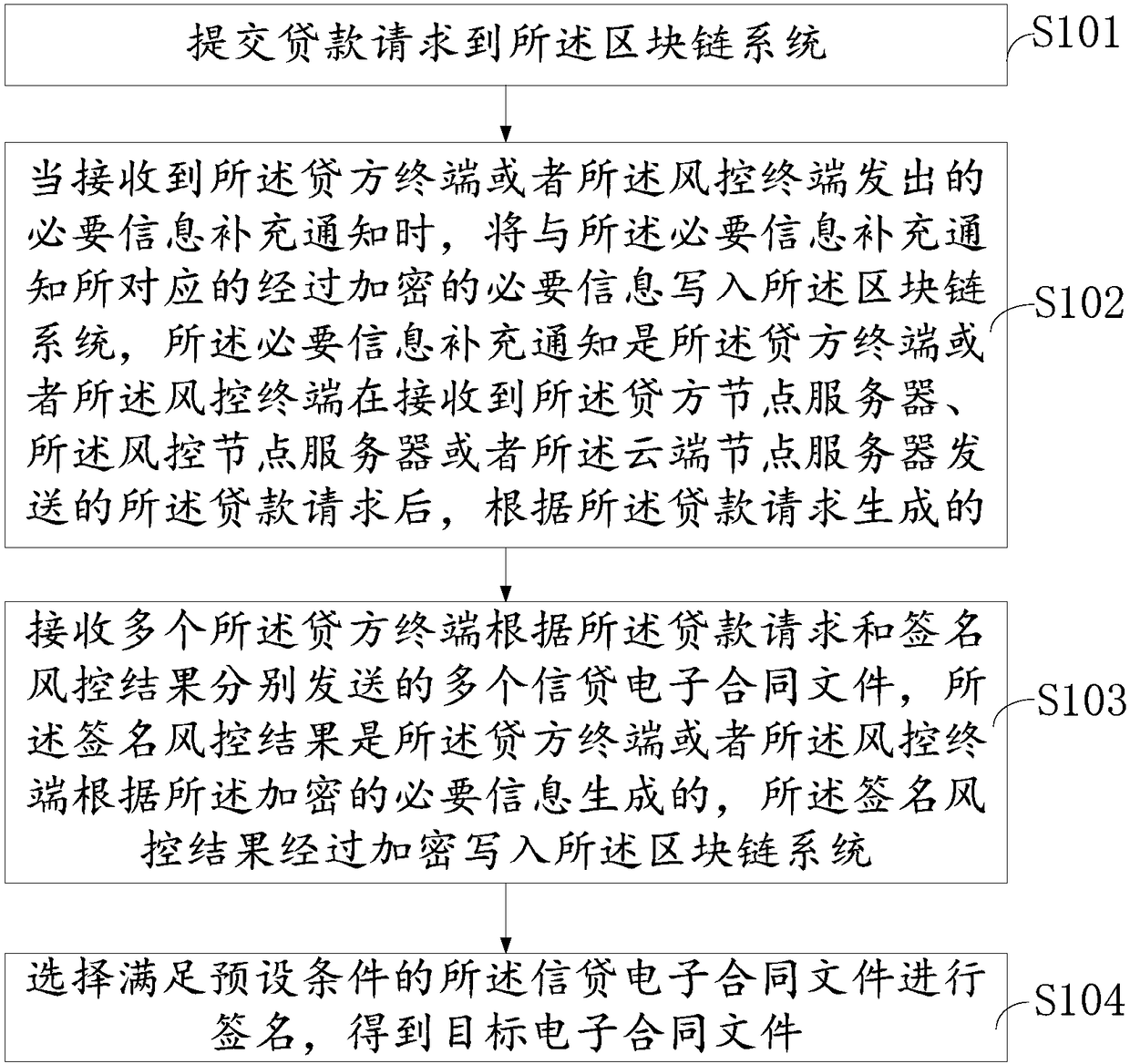
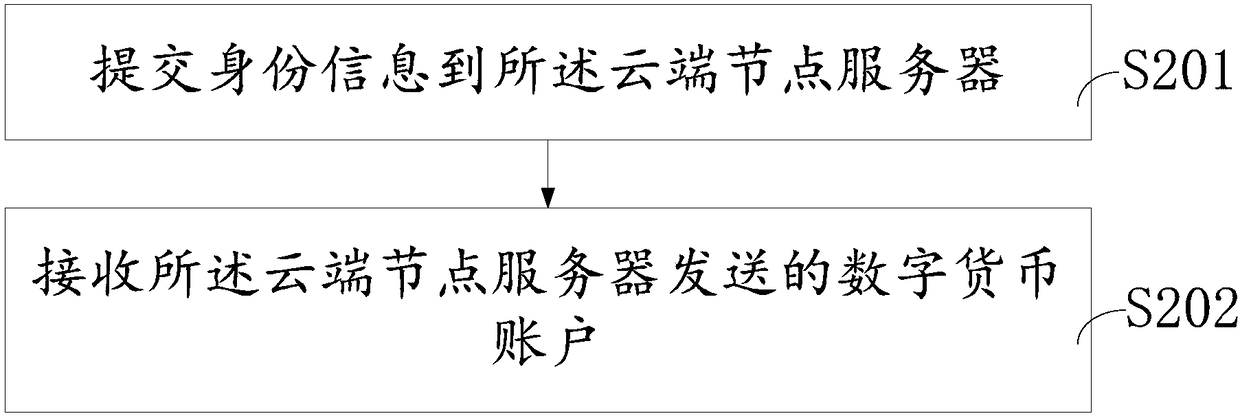
The invention provides a block chain borrowing method and system. The method is applied to multiple borrower terminals in the block chain borrowing system. The method comprises the steps that a loan request is submitted to a block chain system; when a necessary information supplement notification sent by lender terminals or a risk management terminal is received, encrypted necessary information corresponding to the necessary information supplement notification is written into the block chain system, wherein the necessary information supplement notification is generated according to the loan request; multiple credit and loan electronic contract files sent by multiple lender terminals according to the loan request and a signature risk management result respectively are received, wherein thesignature risk management result is generated by the lender terminals or the risk management terminal according to the encrypted necessary information and written into the block chain system after being encrypted; the credit and loan electronic contract files which meet a preset condition are selected for signature, and target credit and loan electronic contract files are obtained. The problem oflow safety of a transaction process and data in the prior art is solved, and the method has the advantage of improving the safety.
Owner:数字乾元科技有限公司
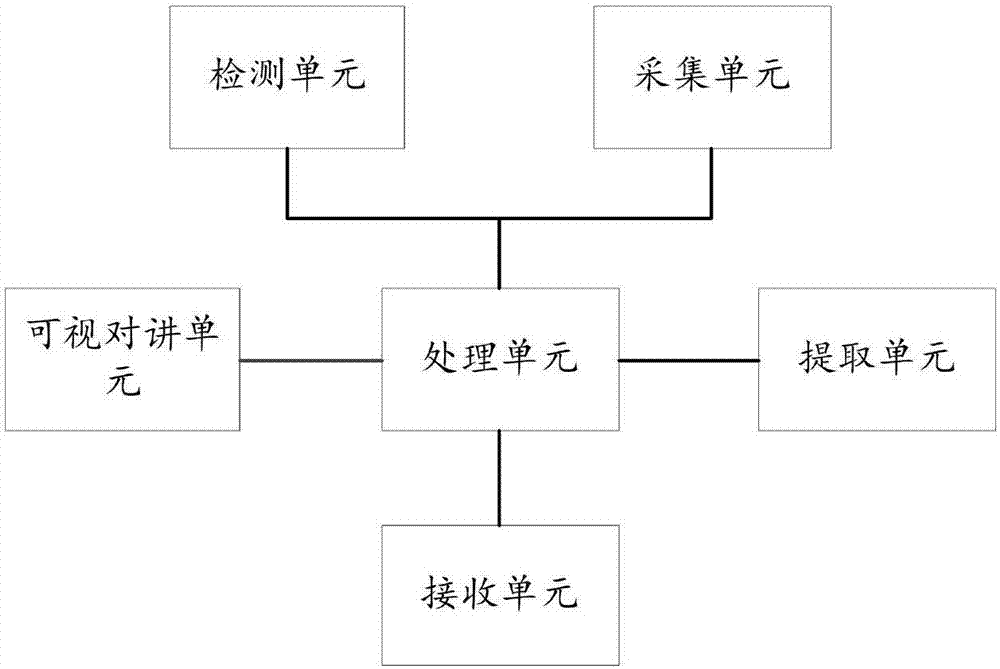
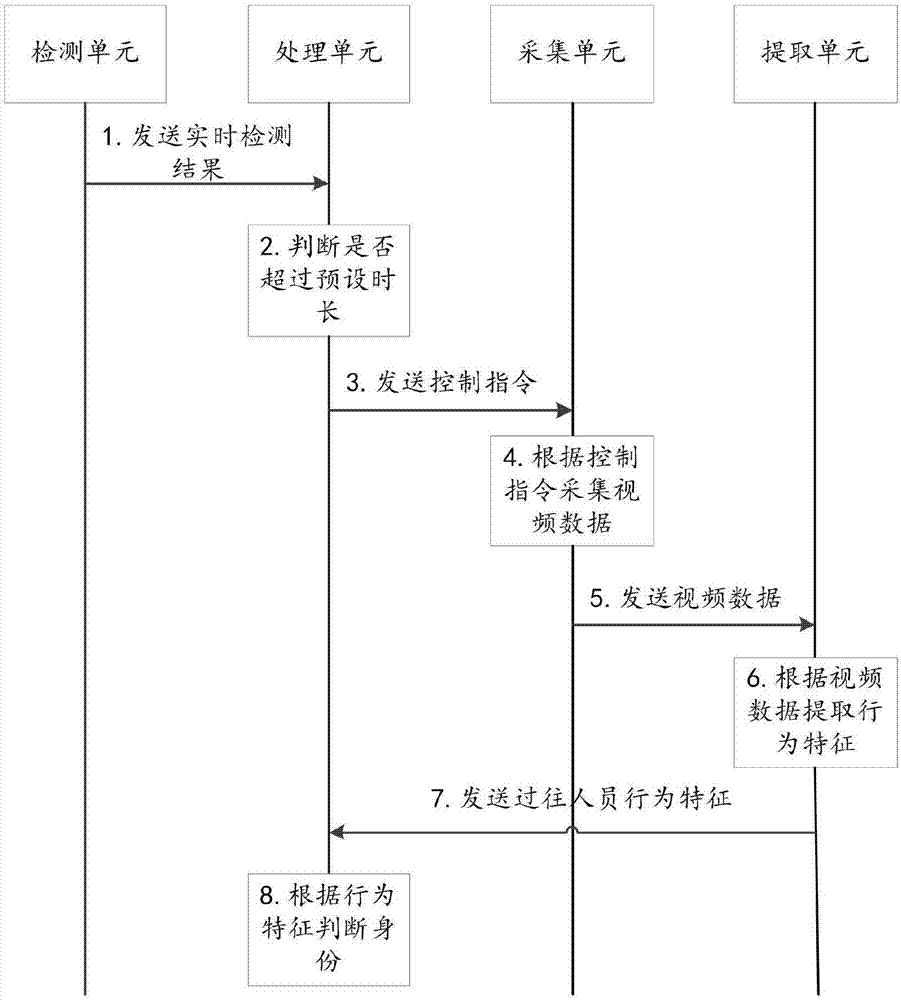
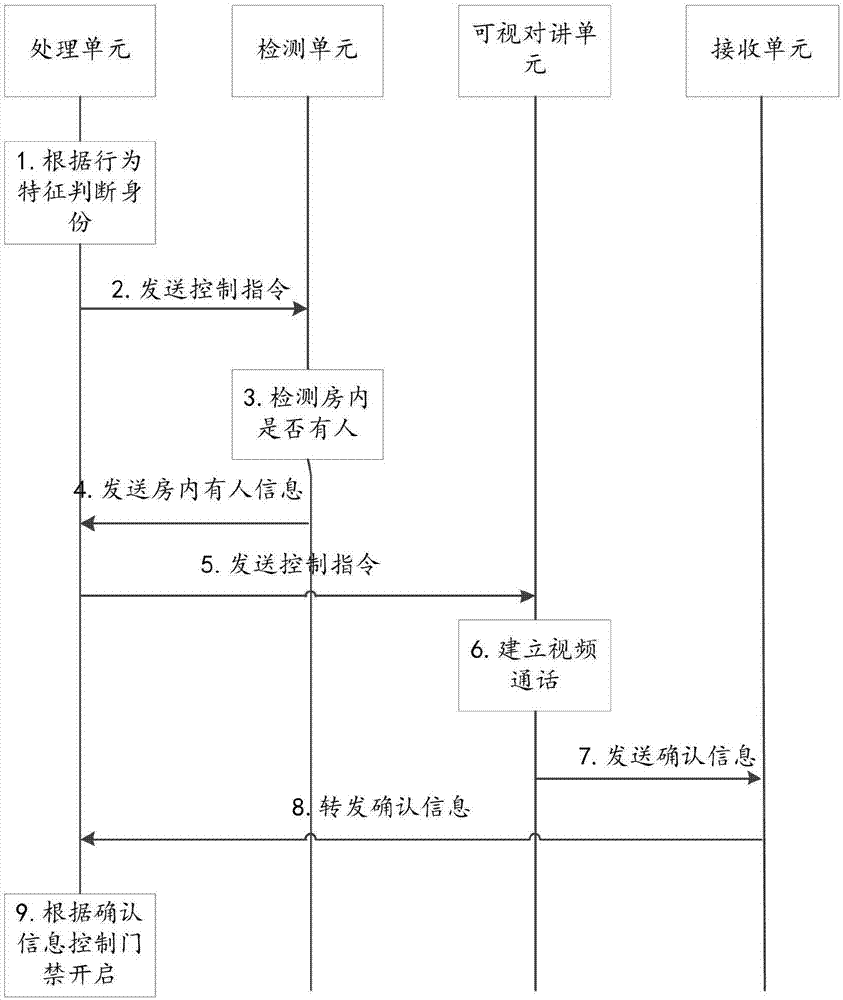
Home security method and system
InactiveCN107341880AEnsure safetyResolve missing situationsCharacter and pattern recognitionTwo-way working systemsHome securityData collecting
The invention relates to a home security method and system. The system comprises a detection unit, a processing unit, a collecting unit, an extracting unit, a video data collecting unit, a visual intercom unit and a receiving unit. Standing time of passing persons is detected in real time through the detection unit, whether the passing persons are visitors or not is judged through the processing unit, communication between a home owner and the visitors is achieved through different processing modes according to the condition in a house, whether an access control is started or not is selected according to the communication result, and after the access control is started, the visitors are monitored till the visitors leave, and then the access control is closed. The condition that when a user is not in the home, the visitors need to enter the house, but there is not a person to open a door is avoided; for example, when no person receives arriving expresses, and after the visitors are determined, the access control is remotely controlled to be opened.
Owner:SHENZHEN SHENGLU IOT COMM TECH CO LTD
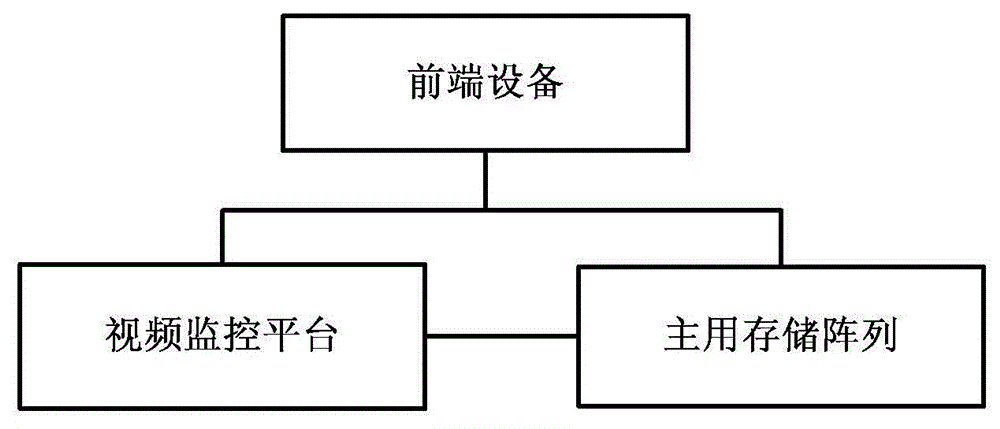
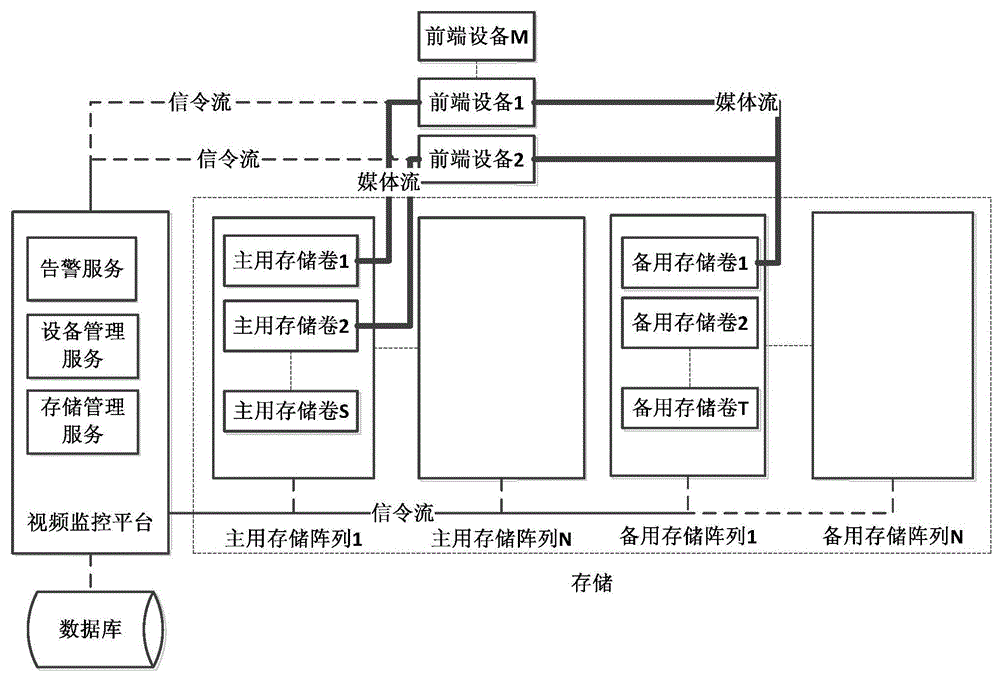
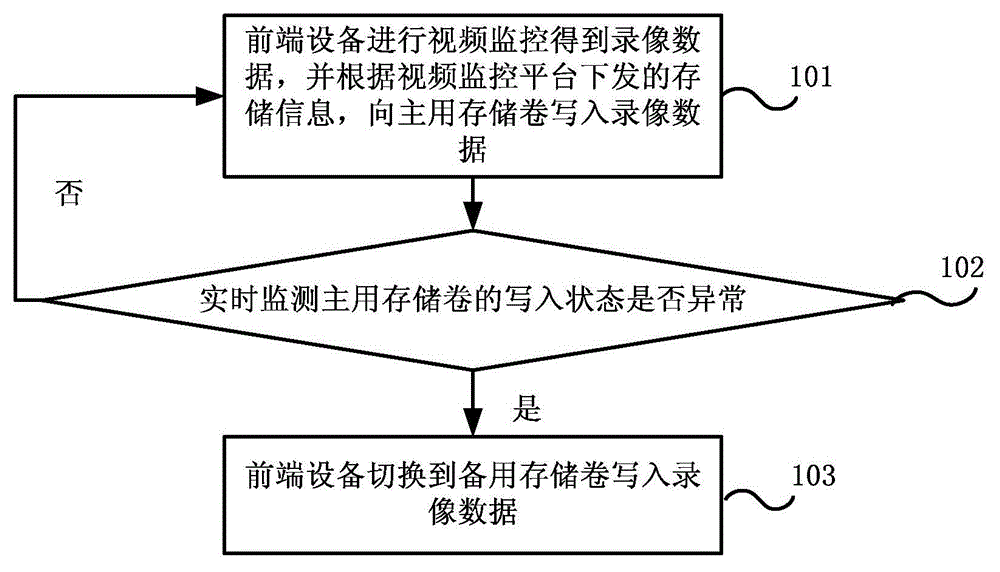
Record data network storage method and system and video monitoring platform
InactiveCN104469310APrevent lossImprove stabilityTelevision system detailsColor television detailsComputer hardwareVideo monitoring
The embodiment of the invention discloses a record data network storage system and method and a video monitoring platform. The method comprises the steps that front-end equipment carries out video monitoring to obtain a video record, writes record data of the video record into a main storage volume according to the storage volume information issued by the video monitoring platform, and monitors whether the writing-in state of the main storage volume is normal or not in real time; the storage volume information comprises path information which is divided to the main storage volume and a standby storage volume of the front-end equipment from a first main storage array and a first standby storage array located on different physical equipment by the video monitoring platform; when it is monitored that the writing-in state of the main storage volume is abnormal, the front-end equipment is switched to write the record data into the standby storage volume. The problem of video data loss caused by storage volume faults can be avoided.
Owner:ZHENGJIANG PUBLIC INFORMATION
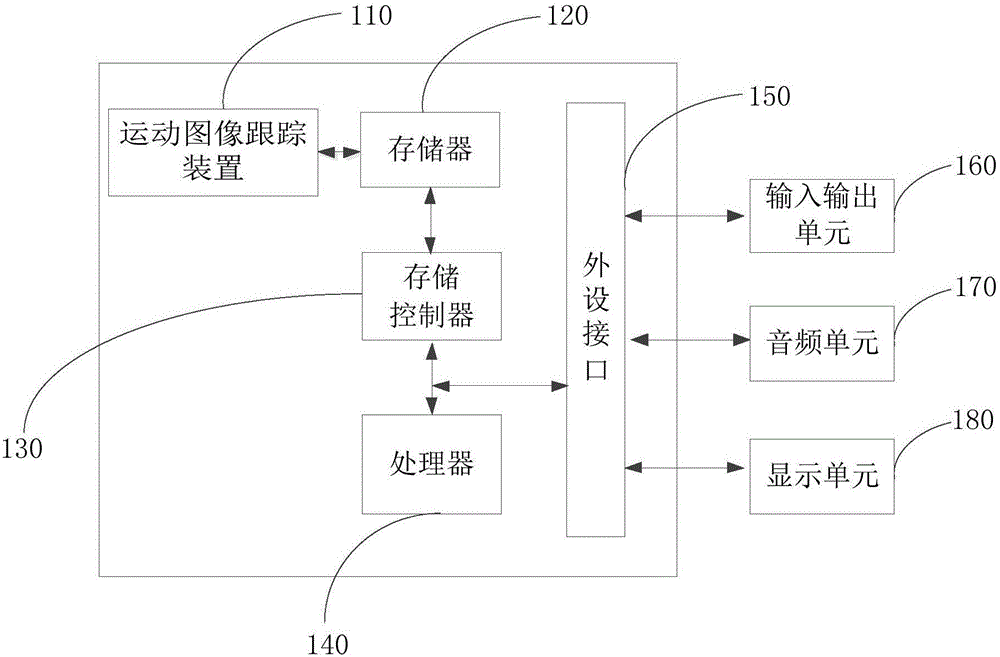
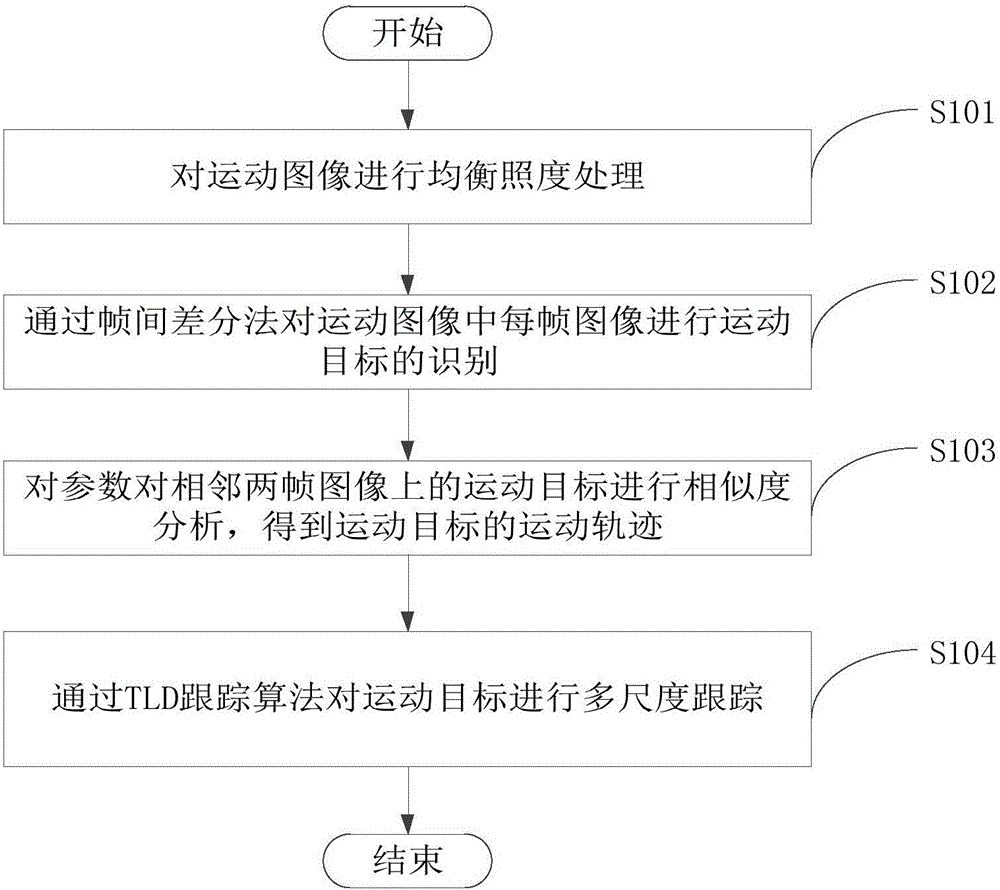
Motion image tracking method and device
InactiveCN106204658AAccurate identification and trackingAvoid lossImage enhancementImage analysisImage trackingBackground information
The invention provides a motion image tracking method and device, and relates to the technical field of image processing. The method comprises the steps: carrying out the illumination equilibrium processing of a motion image; carrying out the recognition of a moving target in each frame of the motion image through employing an inter-frame difference method; carrying out the similarity analysis of the moving targets in two adjacent frames through a Bhattacharyya parameter, and obtaining a moving track of the moving object. The method and device provided by the invention can achieve the processing of images of different scenes at different motion scales, eliminate the interference from background information and motion noise, and improve the accuracy and instantaneity of a moving target recognition and tracking result.
Owner:BEIJING UNIV OF POSTS & TELECOMM
A charging income guarantee method realized by auditing
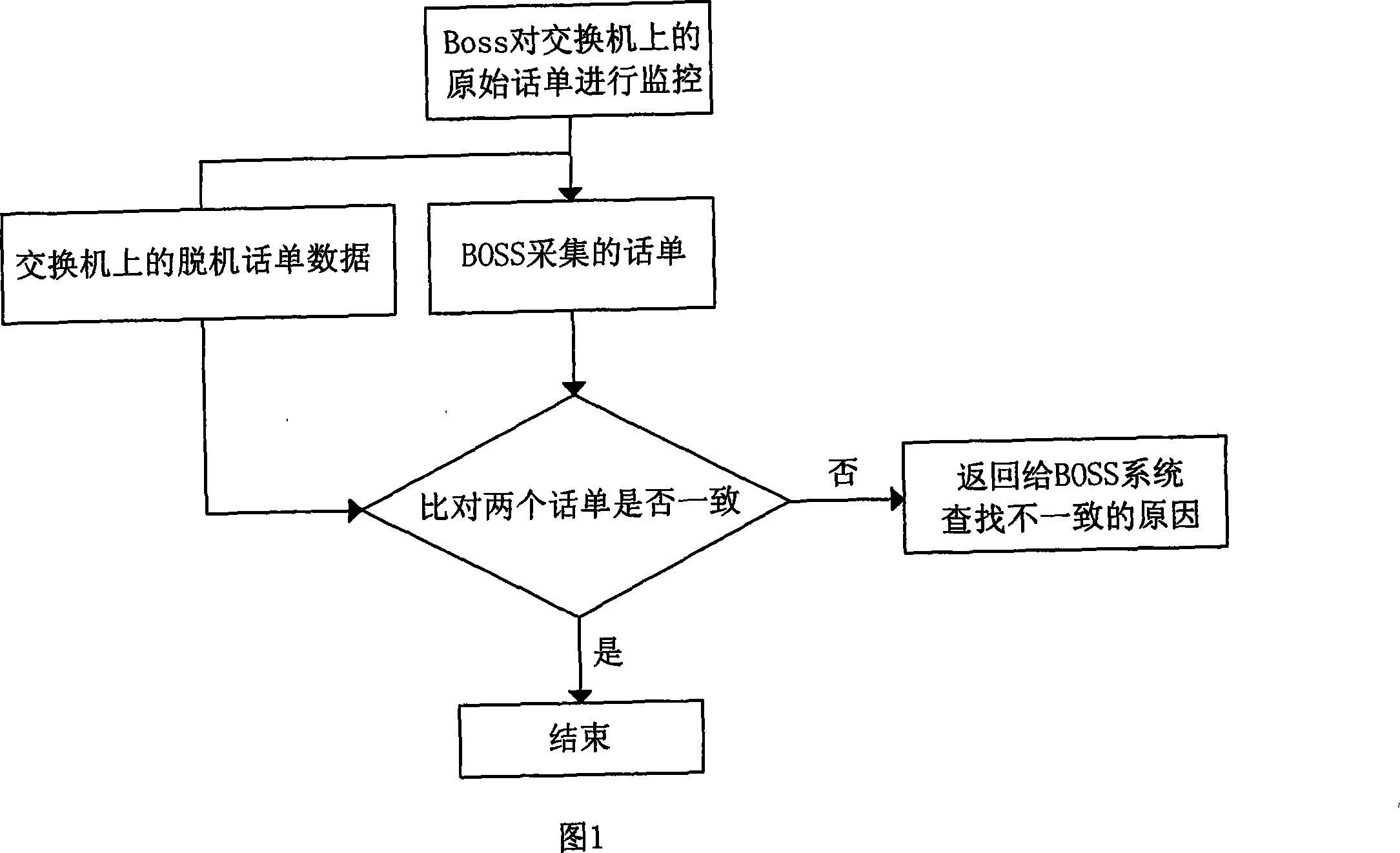
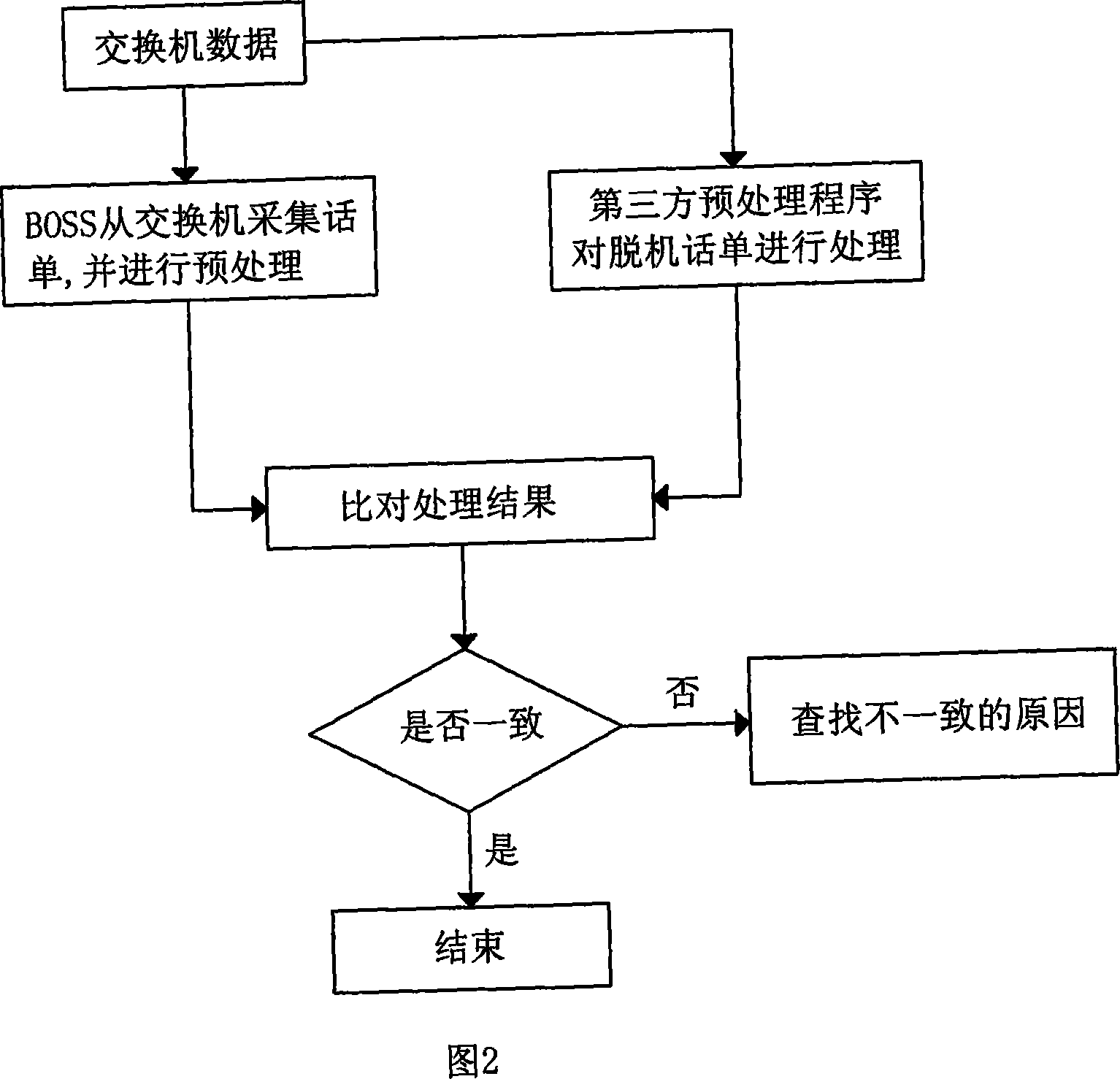
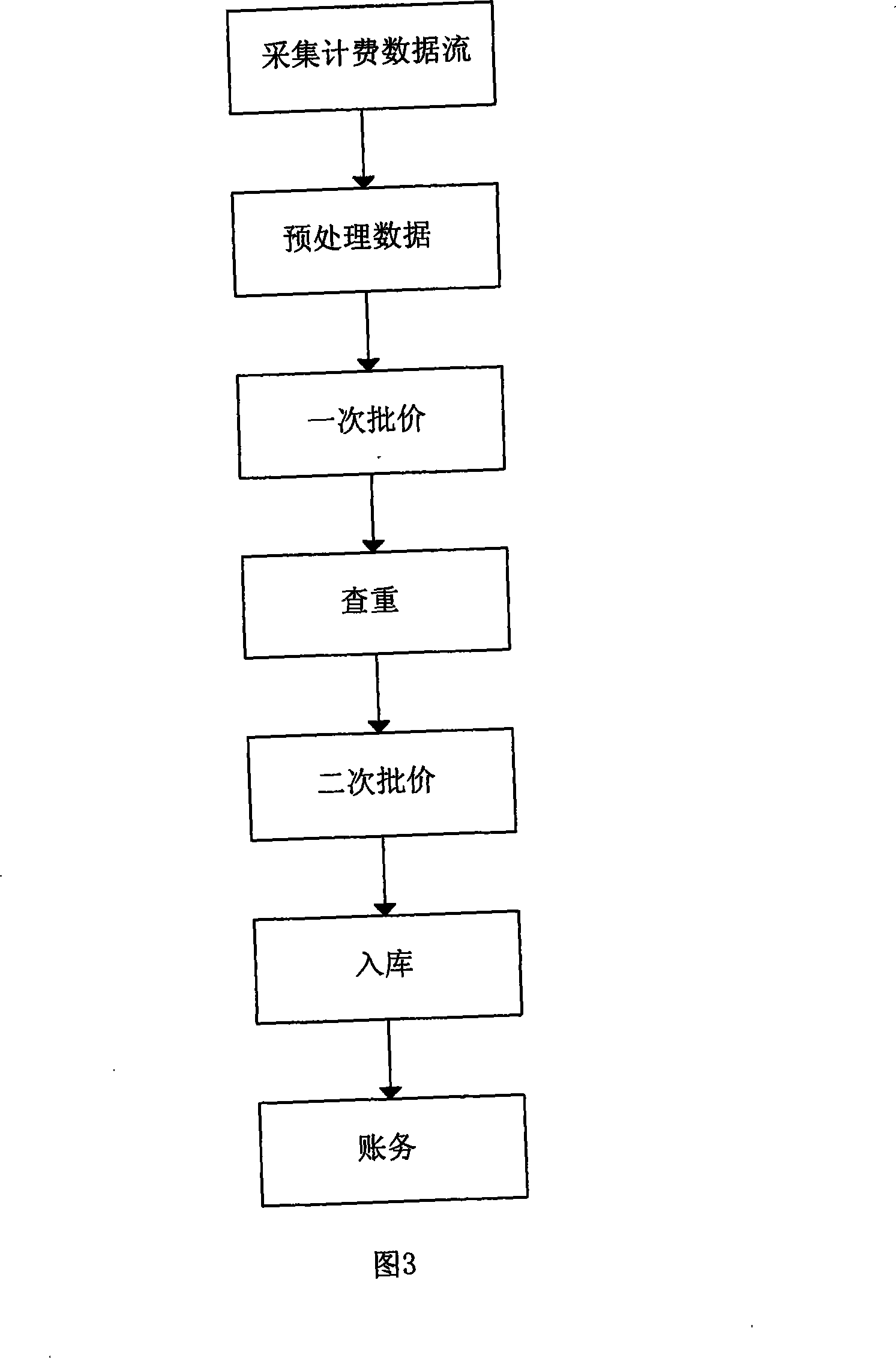
InactiveCN101217393APrevent lossSimplified means of discoveryMetering/charging/biilling arrangementsRadio/inductive link selection arrangementsOriginal dataData mining
The invention discloses a method for ensuring the accounting revenue through audition and extracting the auditing information from each link of the accounting treatment process from collecting to accounting through the monitoring and analysis of the BOSS system. The invention is characterized in that the invention comprises the audition of the integrity of network / accounting original data, the audition of end-to-end balance of the accounting process and the subject audition of the numerical integrity of multi network element accounting data; the audition of the integrity of network / accounting original data comprises the checking and monitoring of the continuity of original bill record sequence numbers and audits original bill record files; the audition of end-to-end balance of the accounting process is the balancing audition from step to step in the whole accounting process; the subject audition of the numerical integrity multi network element accounting data verifies the consistency of accounting bill records of different network elements in switching networks. The invention realizes the function of continuously checking and monitoring the original bill record sequence numbers, the function of auditing pretreated modules, the function of auditing the balance of whole accounting businesses and simplification of the searching means for the loss of bill records.
Owner:CHINA MOBILE GROUP SICHUAN
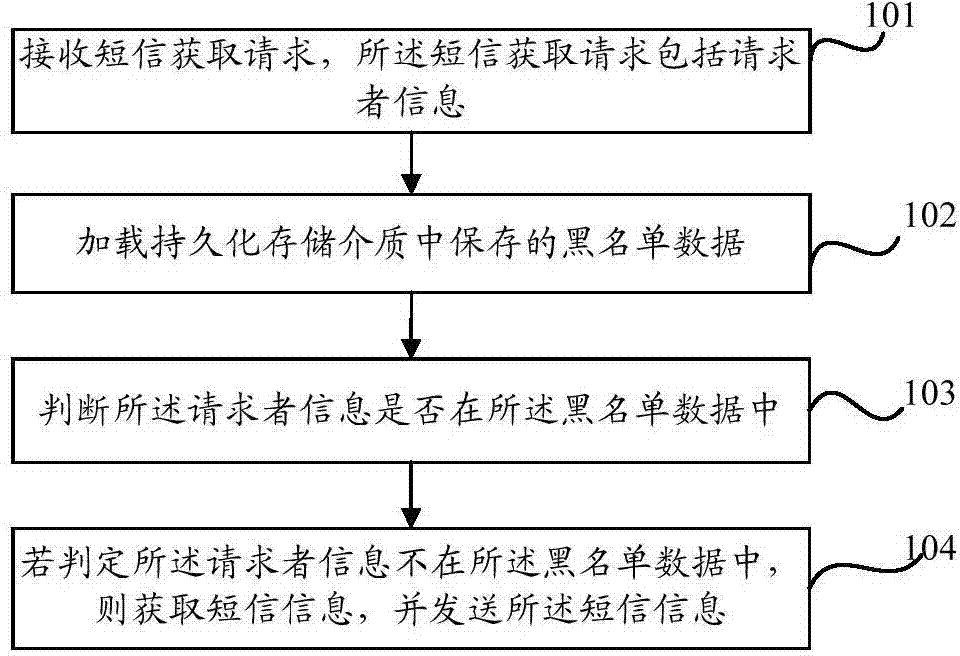
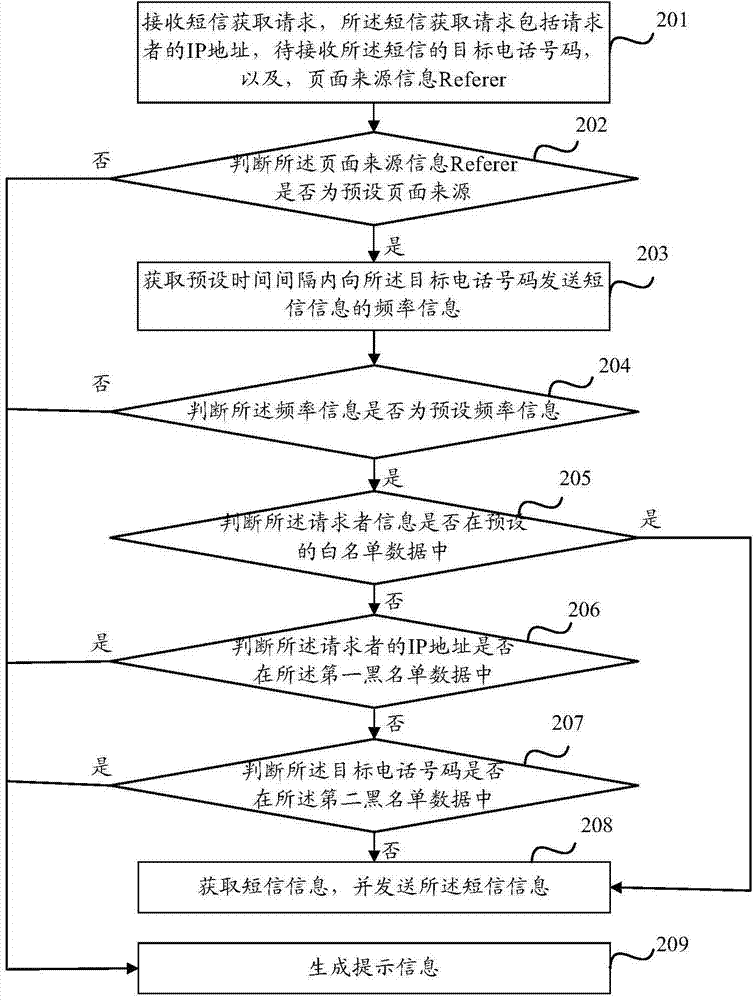
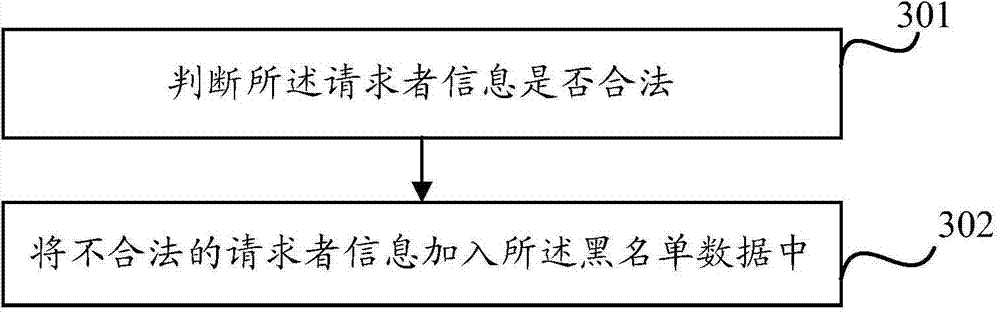
Method and device for sending short messages
ActiveCN104768139APrevent lossImprove defenseMessaging/mailboxes/announcementsSecurity arrangementText messagingBlack list
The invention discloses a method and device for sending short messages. The method includes the steps that a short message acquiring request is received, and the short message acquiring request comprises information of a requester; blacklist data stored in a persistent storage medium are loaded; whether the information of the requester is included in the blacklist data is judged; if the information of the requester is included in the blacklist data, short message information is received, and the short message information is sent. By means of the method and device for sending the short messages, the short messages can be defended to be attacked, and a short message platform can be prevented from suffering hostile attacks.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
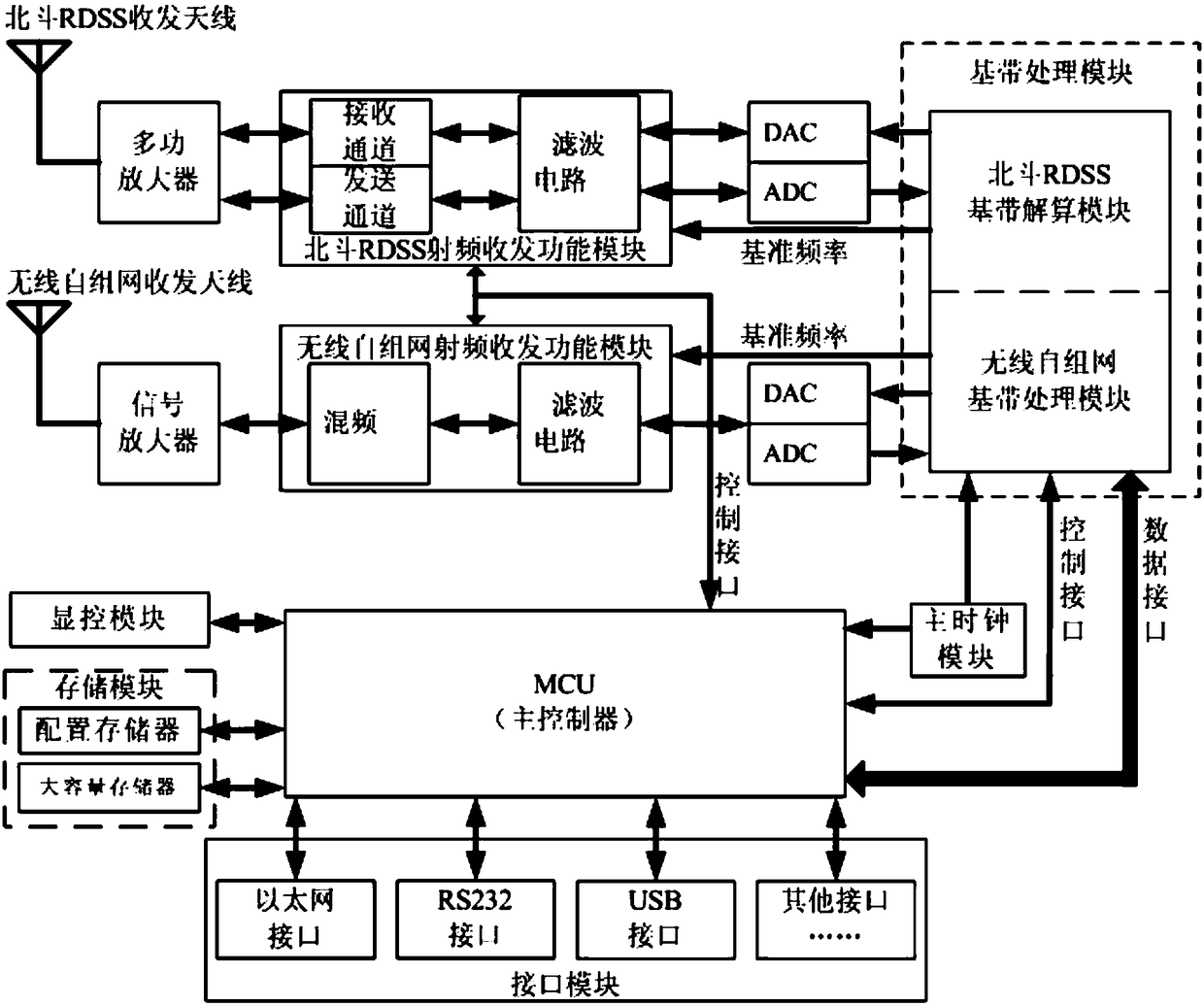
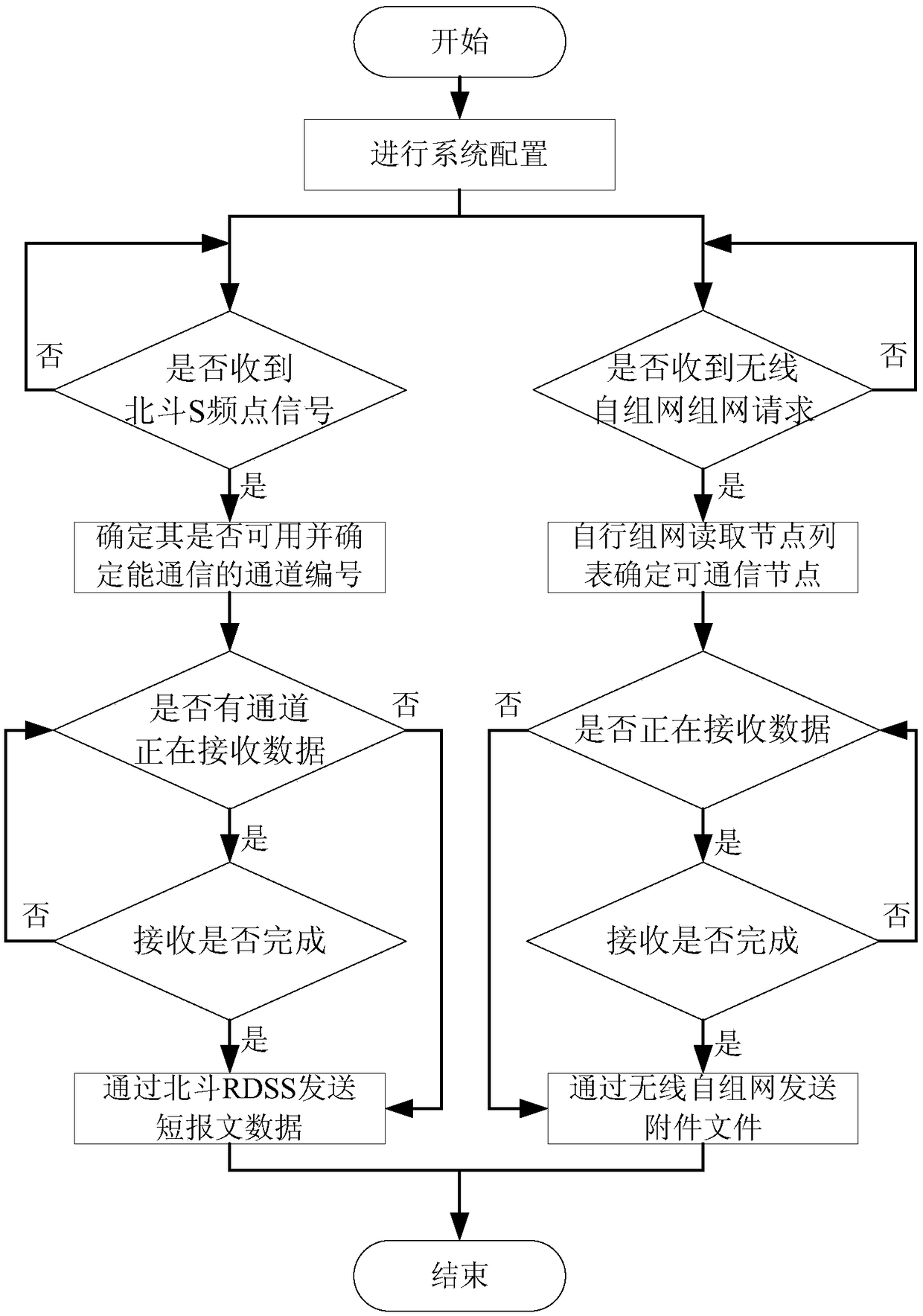
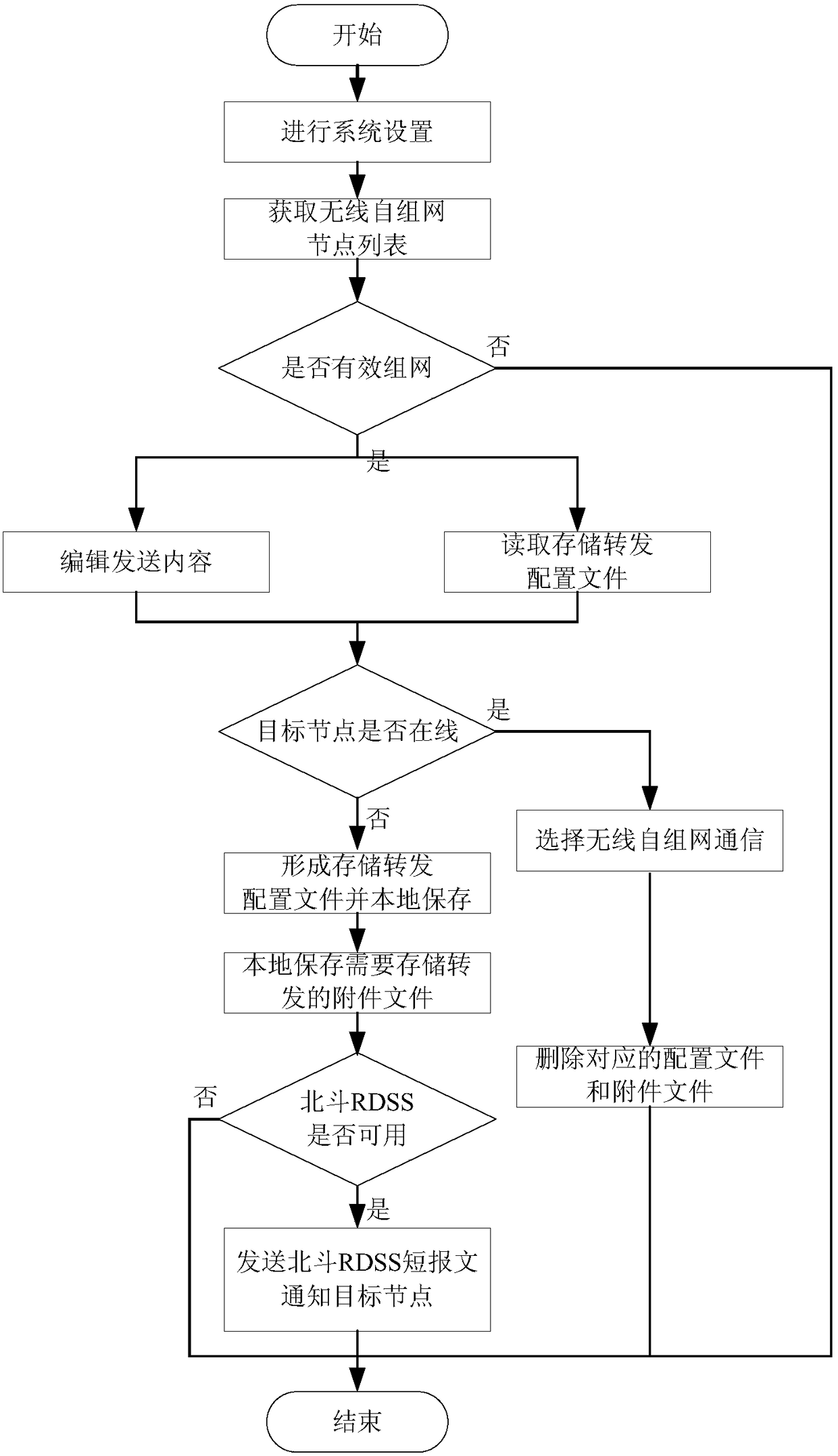
Dual-mode communication system based on wireless ad hoc network and BeiDou RDSS technology and communication method
ActiveCN108111217AThe communication process is controllableControllable communication contentParticular environment based servicesNetwork topologiesCommunications systemTrunking
The invention discloses a dual-mode communication system based on a wireless ad hoc network and BeiDou RDSS technology and a communication method. A BeiDou transmitting-receiving link comprises a BeiDou RDSS baseband solution module connected to the control interface and the data interface of a master controller, and an analog-to-digital and digital-to-analog converter and a Beidou RDSS RF transmitting-receiving functional module which are successively connected with the BeiDou RDSS baseband solution module. A wireless ad hoc transmitting-receiving link includes a wireless ad hoc baseband processing module connected to the control interface and the data interface of the master controller, and an analog-to-digital and digital-to-analog converter and a wireless ad hoc RF transmitting-receiving functional module which are successively connected with the wireless ad hoc baseband processing module. The master controller is configured to perform communication channel signal monitoring and communication channel transmitting-receiving monitoring on the BeiDou RDSS baseband solution module and the wireless ad hoc transmitting-receiving link, and to switch the communication modes according to a monitoring situation, wherein the communication modes includes at least one of a fusion mode, a store-and-forward mode, and a BeiDou RDSS short message relay mode.
Owner:中国兵器装备集团自动化研究所有限公司
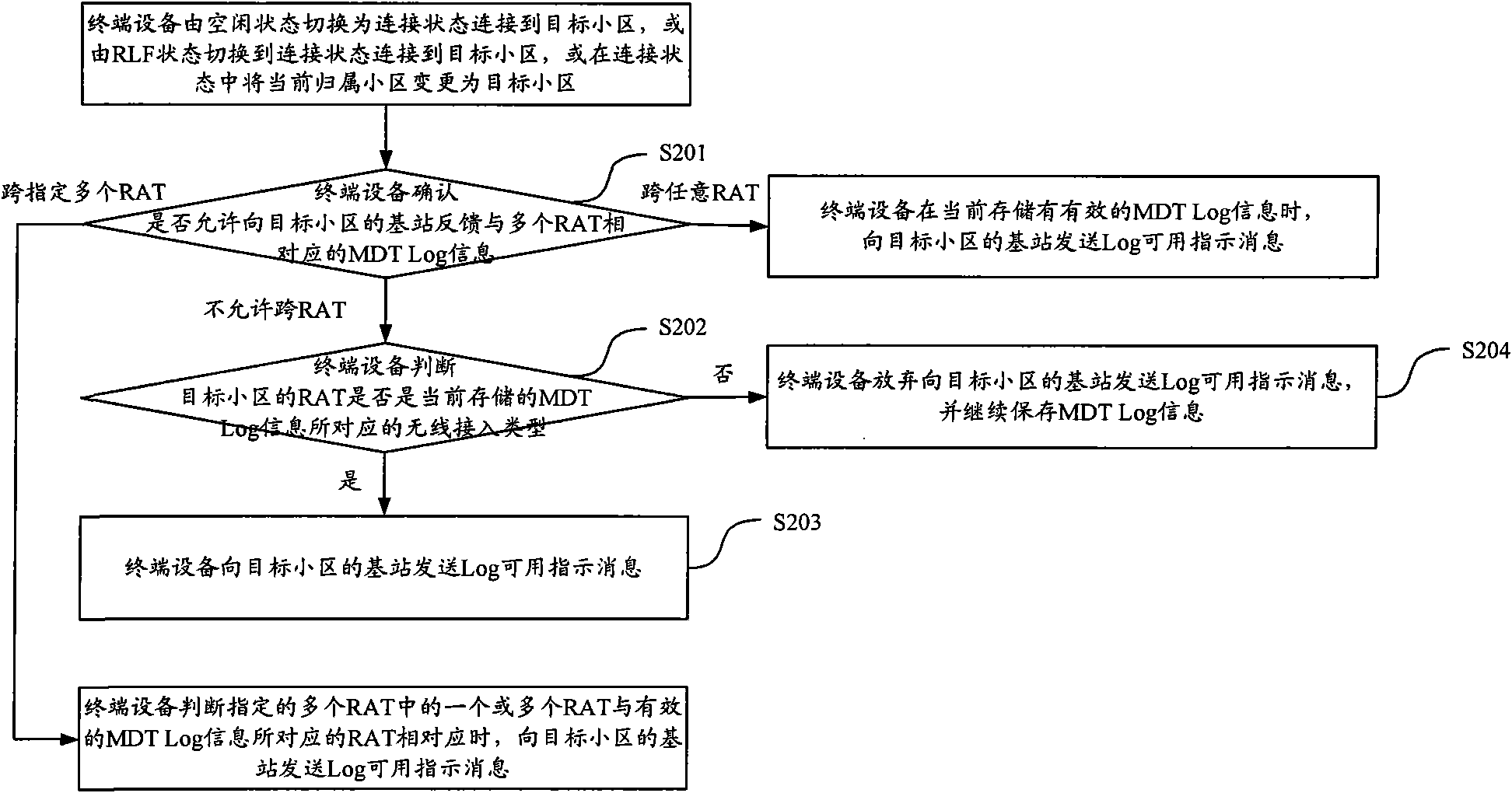
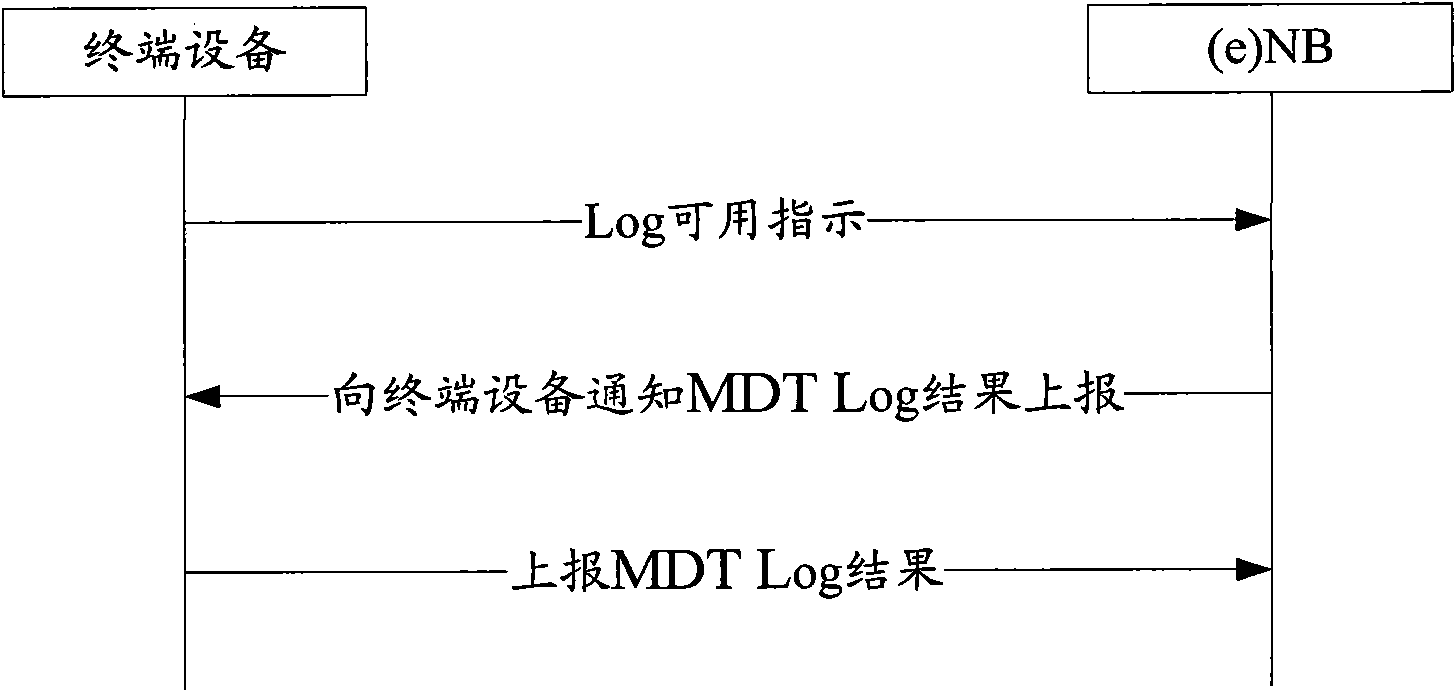
Feedback method and device of minimization drive test (MDT) Log information
ActiveCN102098721AAvoid reportingSave air interface resourcesError prevention/detection by using return channelNetwork traffic/resource managementAir interfaceRadio access
The embodiment of the invention discloses a feedback method and device of minimization drive test (MDT) Log information. By using the technical scheme proposed by the embodiment of the invention, terminal equipment can reasonably select whether available Log indication information is sent to a network in accordance with a radio access type (RAT) corresponding to MDT Log information stored in the terminal equipment, thus avoiding a phenomenon that effective MDT Log information is lost resulting from feedback of the MDT Log information when an existing RAT does not correspond; and in addition, the terminal equipment determines whether the available Log indication information is reported to a network side in accordance with an actual RAT condition, so that report of unnecessary MDT Log information can be avoided, and air interface resources of a system can be effectively saved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Detection kit and detection method of circulating tumor cells
The invention discloses a detection kit and a detection method of circulating tumor cells. The kit comprises a PBS buffer solution, a density gradient separation medium, a red blood cell lysate, a CD45 immunomagnetic bead, an incubation solution, a fixing solution, a permeabilizing solution, a confining liquid, an antifade mounting medium, an antibody dilution solution and a fluorescent antibody concentrate, and the fluorescent antibody concentrate contains a fluorescent dye pan-CK-AF488, a fluorescent dye CD45-PE and a cell nucleus dye Hoechst33342. The detection method comprises the following steps: S10, centrifuging a blood sample, and separating and enriching the CTCs; and S20, carrying out dyeing identification on the enriched CTCs through the cell nucleus dye pan-CK-AF488, the fluorescent dye CD45-PE and Hoechst33342 fluorescence antibodies, wherein the detection is carried out for the purpose of non-treatment. When the detection kit and the detection method are adopted to perform detection, the detection result is accurate and reliable.
Owner:亚能生物技术(深圳)有限公司
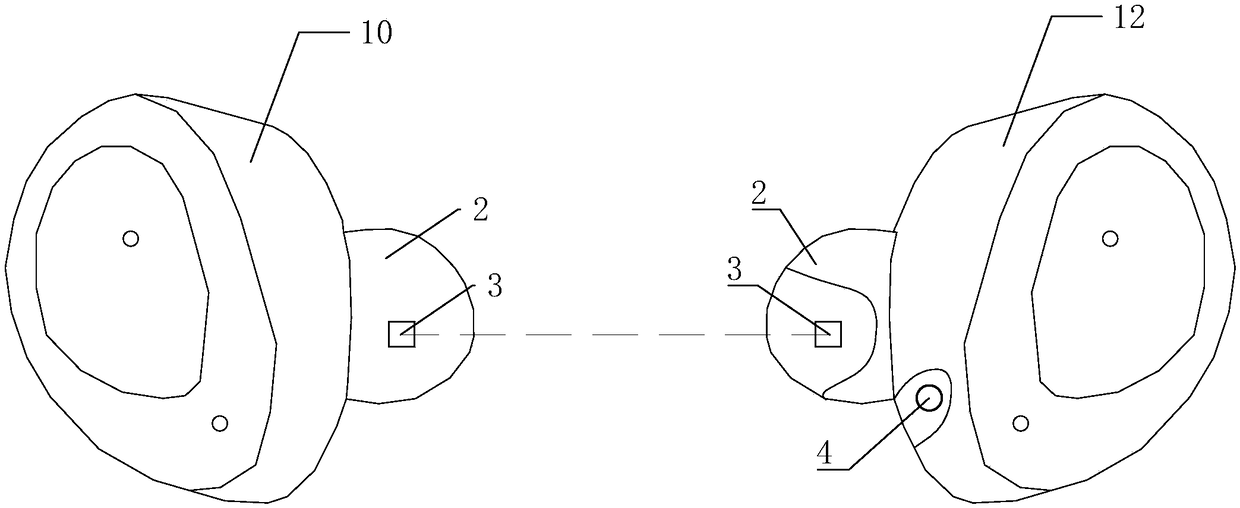
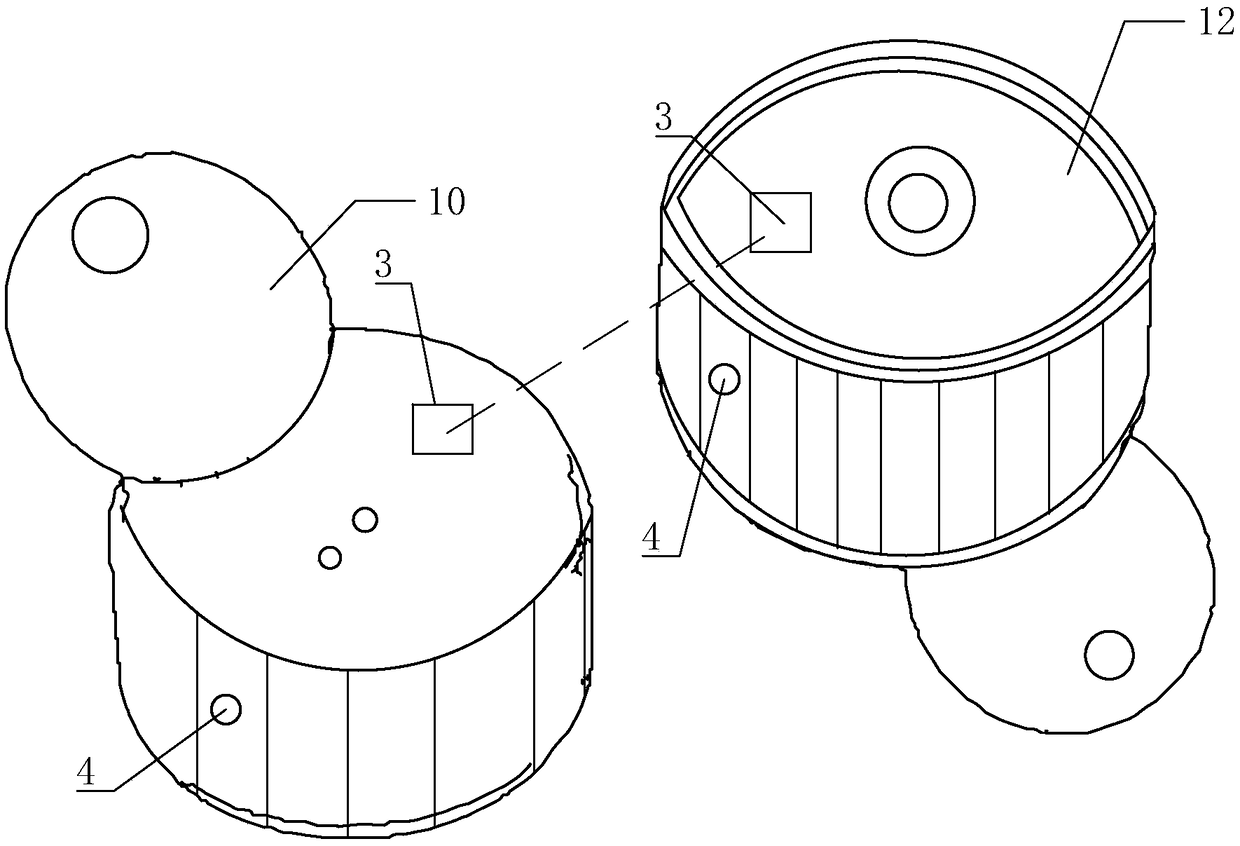
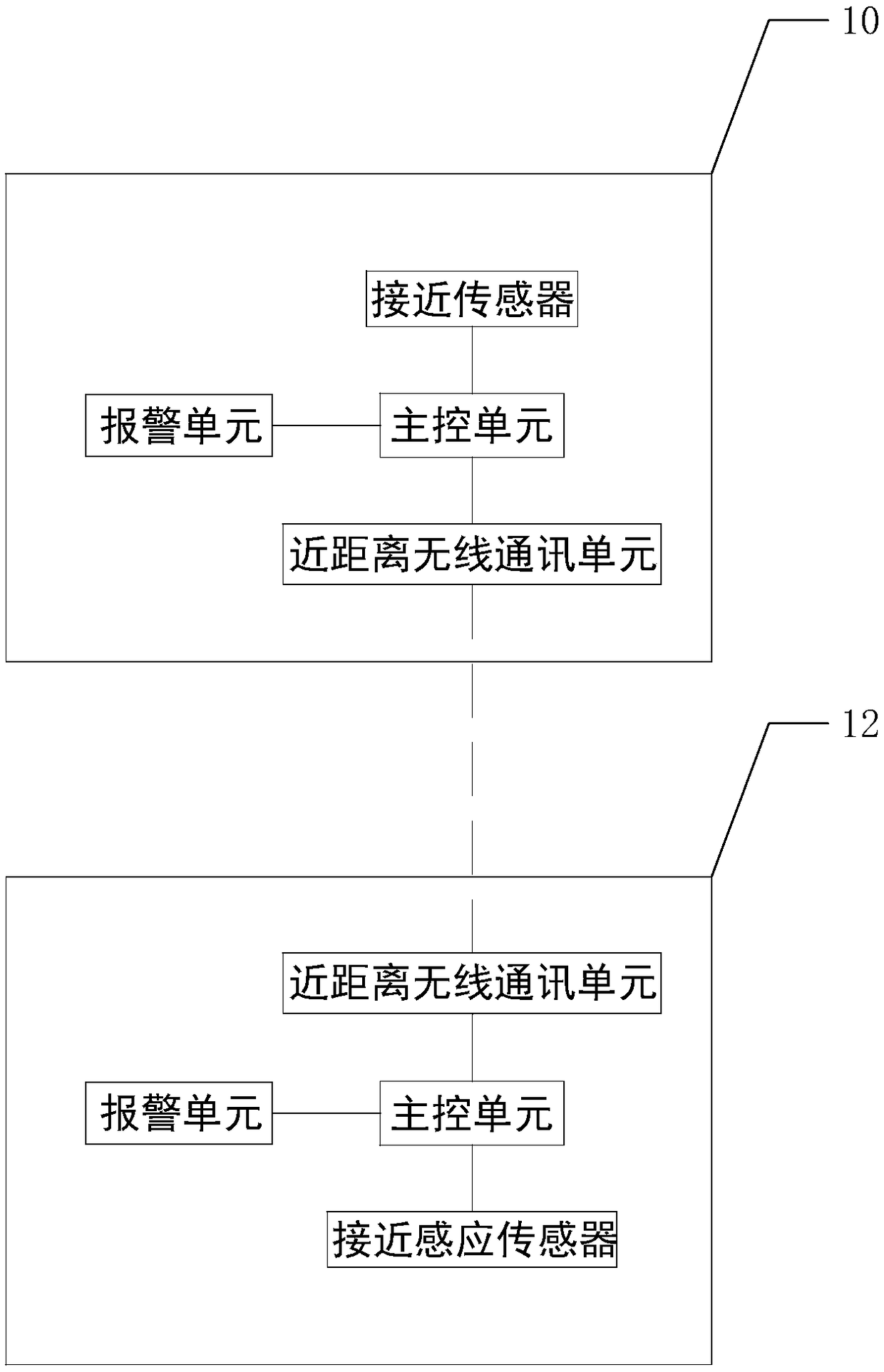
Wireless earphone and alarm method thereof
ActiveCN108718431AAvoid lossTroubleshoot missing technical issuesMicrophonesLoudspeakersCommunication unitShortest distance
The invention discloses a wireless earphone and an alarm method thereof. The wireless earphone comprises a left earphone body and a right earphone body, and the left earphone body and the right earphone body are both internally provided with a main control unit, a short-distance wireless communication unit and an alarm unit; the short-distance wireless communication unit in the left earphone bodyand the short-distance wireless communication unit in the right earphone body are in short-distance wireless communication connection. During normal wearing, the distance between the left earphone body and the right earphone body is within a short-distance wireless communication distance, and once the left earphone body or the right earphone body falls off from the ear, communication of the short-distance wireless communication units cannot be achieved. Meanwhile, the main control units judge whether or not the short-distance wireless communication units electrically connected with the main control units achieve short-distance wireless communication, and if not, an alarm signal is generated, the alarm units are controlled to give an alarm according to the alarm signal, and a user is notified that the earphone falls off. Therefore, according to the wireless earphone and the alarm method thereof, the earphone is effectively prevented from being lost.
Owner:GOERTEK INC
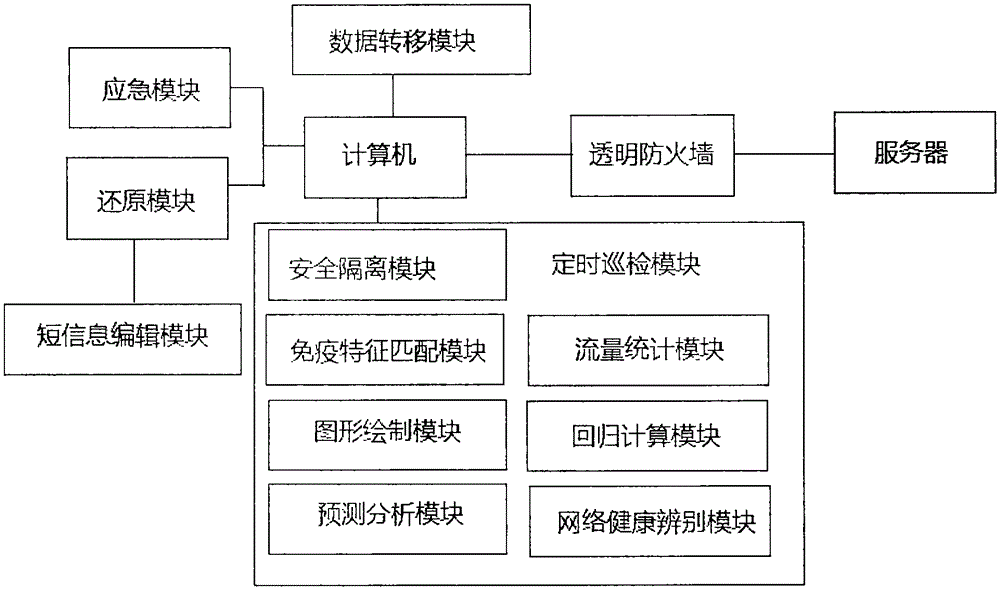
Computer network monitoring system
The invention discloses a computer network monitoring system, and the system comprises a transparent firewall disposed between a computer and a server, a timing inspection tour module, an emergency module, a restoration module, and a data transfer module. The system achieves the monitoring and audit of network flow, maintains the good network state, improves the network immune capability through the analysis and memorizing of unknown behaviors, can effectively control the danger range after invasion, and guarantees the smooth network and normal providing of services. The system has the capability of autonomous restoration, maintains the stable operation of the network, has a capability of data protection, and also prevents information from being lost because a user is not in front of a computer.
Owner:XIAN UNIV OF SCI & TECH
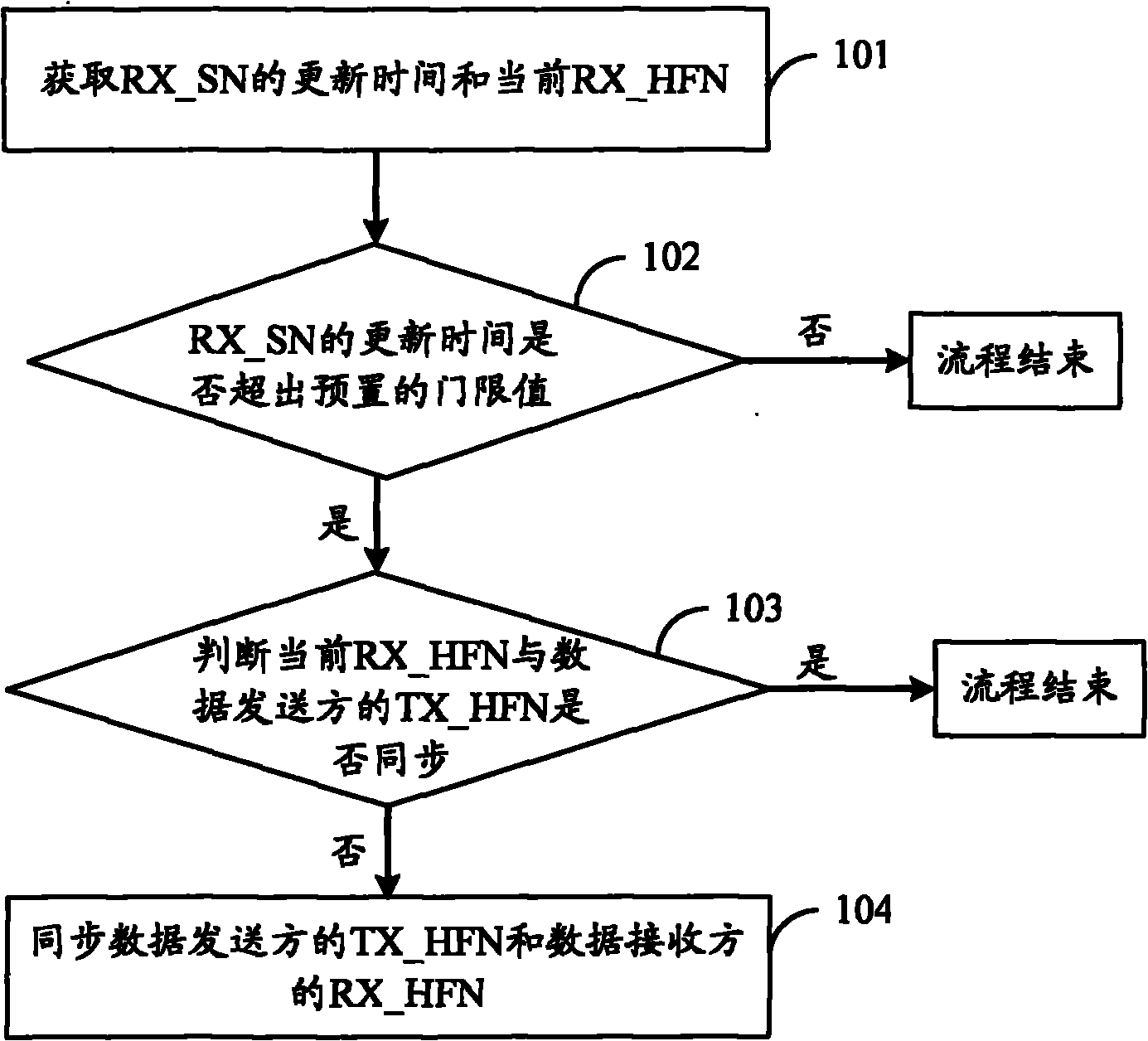
Method, device and system for processing data
ActiveCN102137435AAvoid data lossImprove data transmission reliability and user experienceSynchronisation arrangementNetwork traffic/resource managementData transmissionData processing
The embodiment of the invention discloses a method, device and system for processing data. The method comprises the following steps: acquiring update time of RX_SN and current RX_HFN; when the update time of the RX_SN exceeds a preset threshold, judging whether the current RX_HFN is synchronized with TX_HFN of a data sender; and if not, synchronizing the TX_HFN with the RX_HFN. By utilizing the method, the device and the system, an abnormal link can be discovered and recovered timely so that the TX_HFN of the data sender is resynchronized with the RX_HFN of a data receiver within a short time, thus avoiding data loss caused by failure in timely discovery of asynchronization between the TX_HFN and the RX_HFN, and being beneficial to enhancing data transmission reliability and user experience.
Owner:SHANGHAI HUAWEI TECH CO LTD
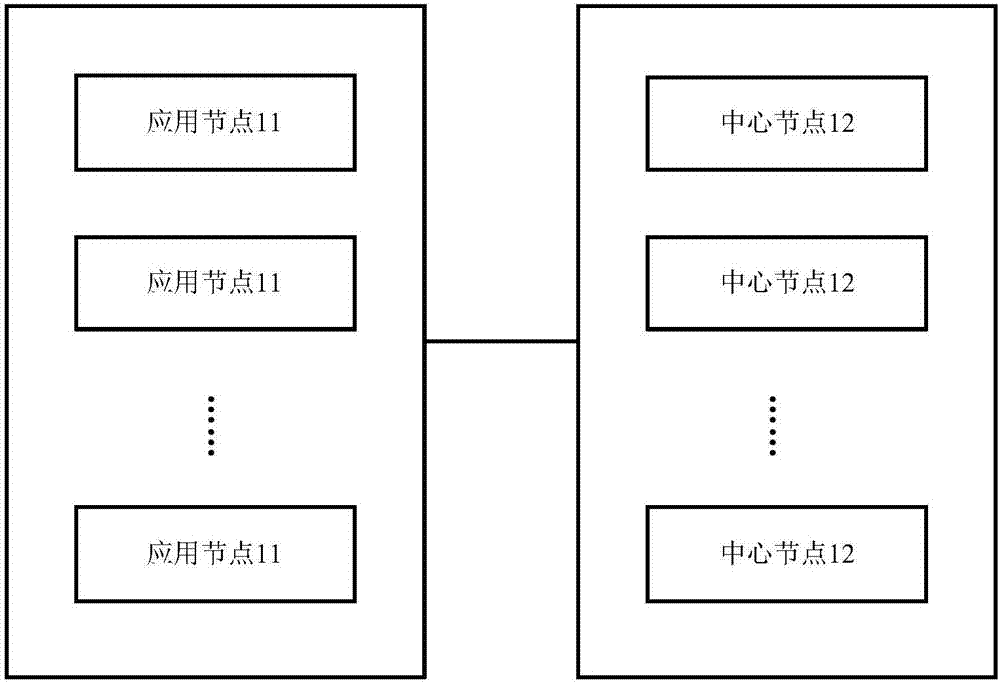
Log storage system and method
ActiveCN107291928APrevent lossSpecial data processing applicationsMultiple applicationsReal-time computing
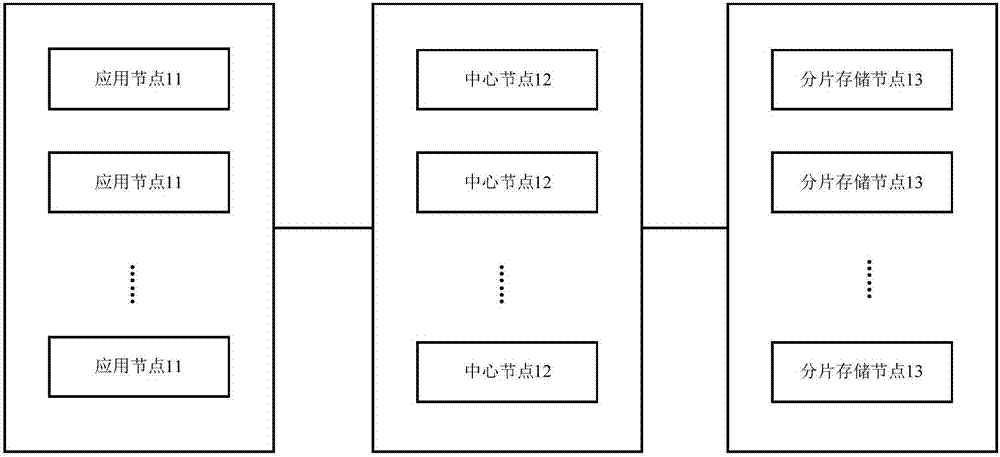
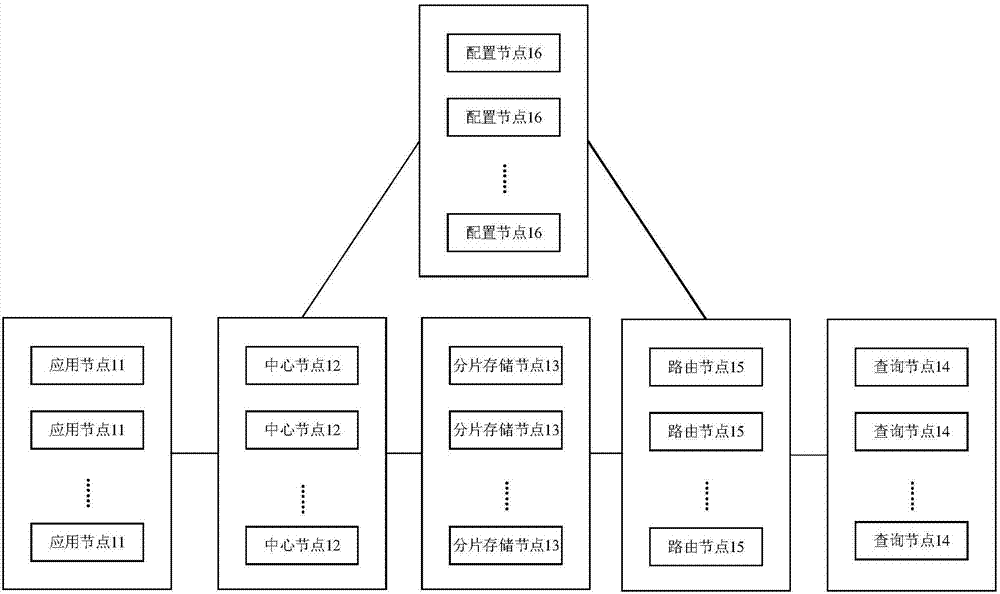
The invention provides a log storage system and method. The log storage system comprises multiple application nodes and at least one center node; a log collection process and at least one application are deployed in each application node, and each center node is in communication connected with at least one application node; the application nodes are used for collecting log data generated during operation of the applications through the log collection processes in real time, and sending the collected log data to the center nodes in communication connection with the application nodes through the log collection processes; the center nodes are used for integrating the received log data from the application nodes, and storing the integrated log data. Loss of logs in a cloud platform can be prevented.
Owner:GUOXIN YOUE DATA CO LTD
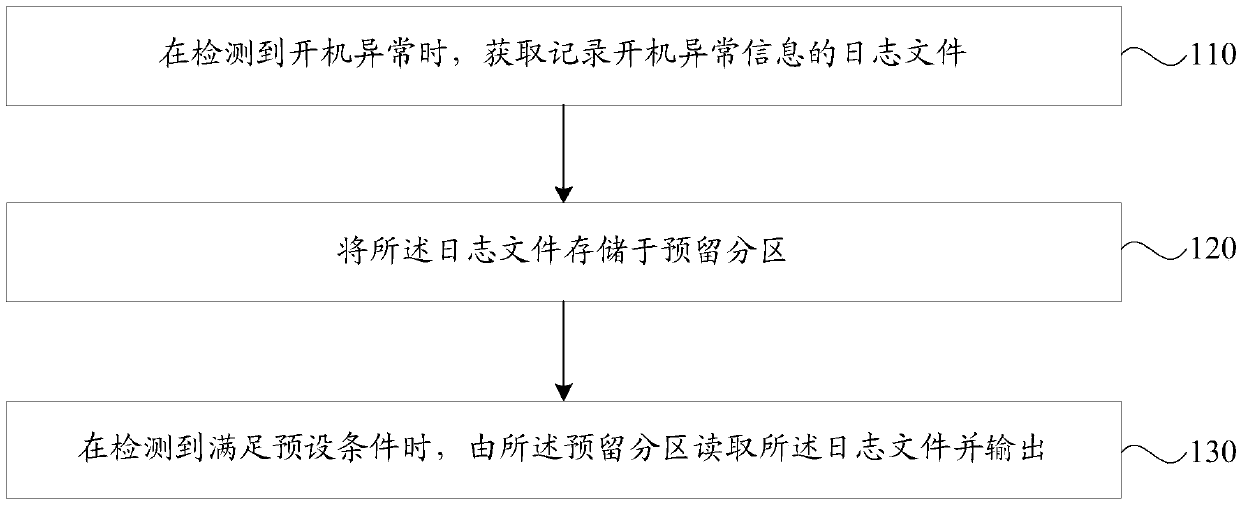
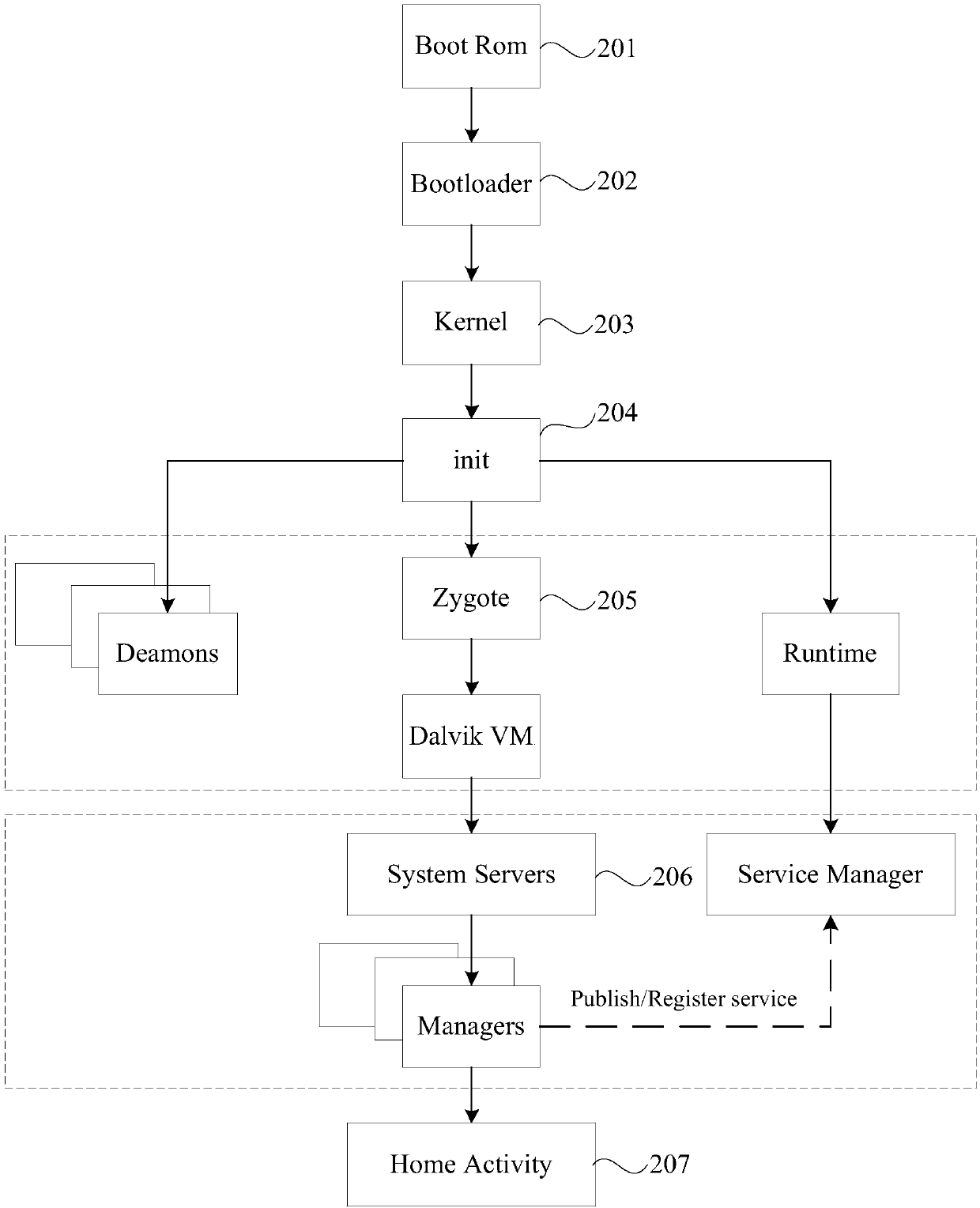
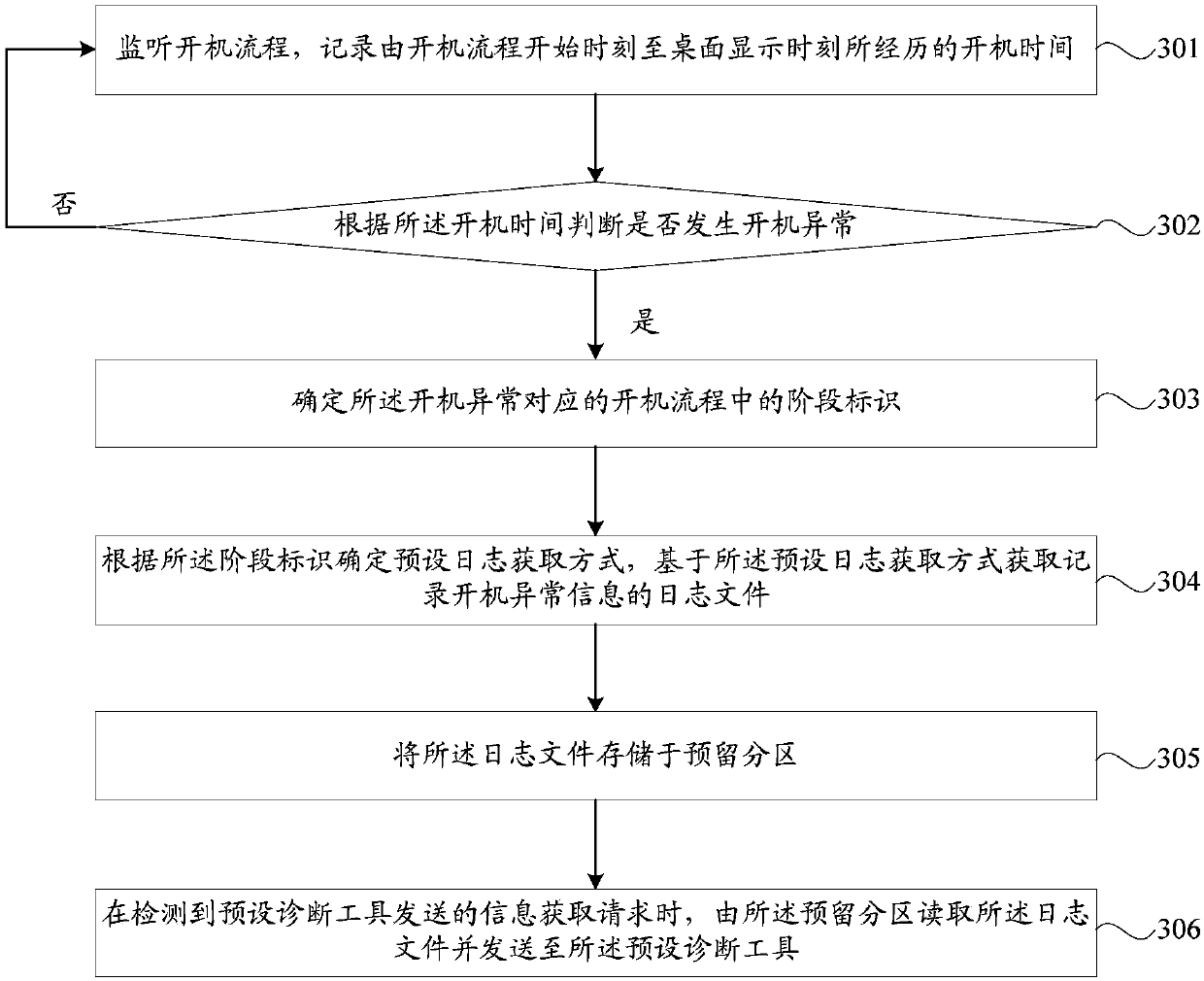
Method and device for recording startup abnormity information, storage medium and terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Node switching method and system
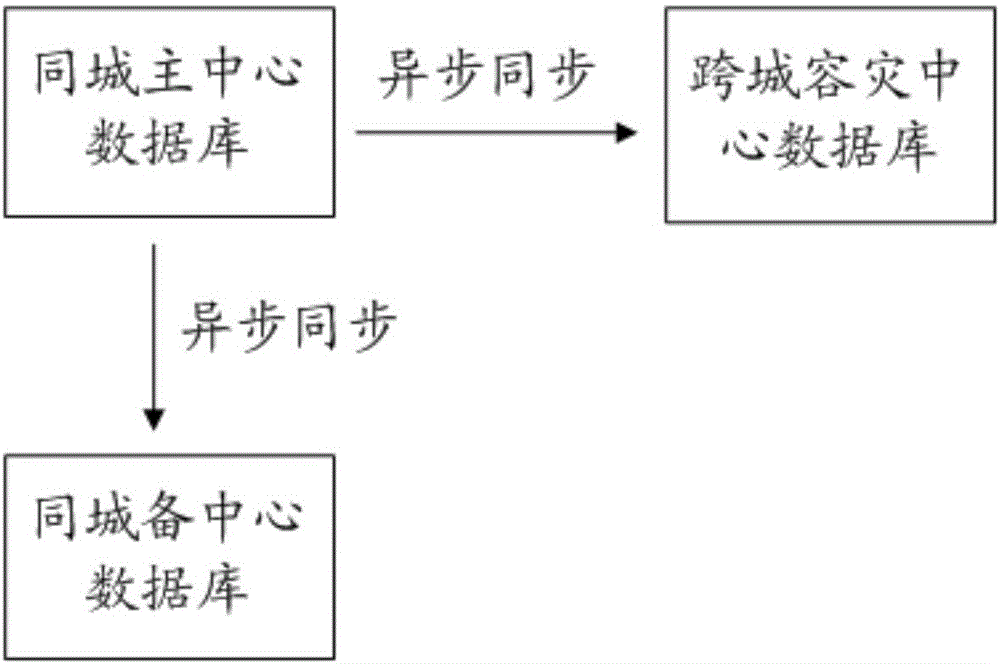
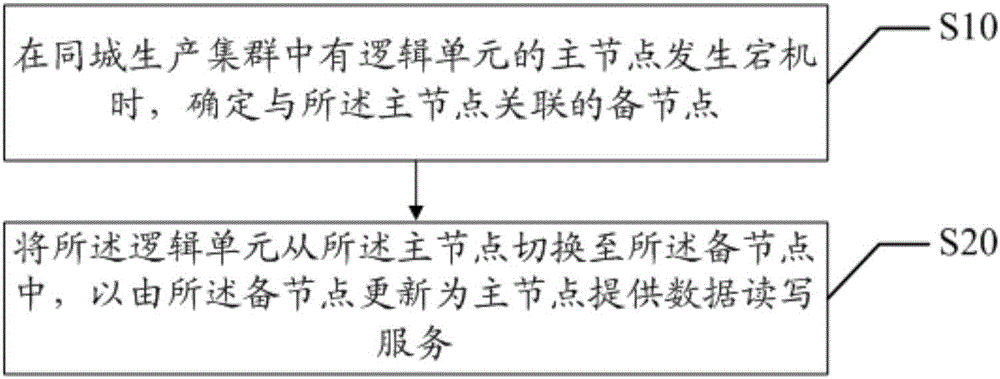
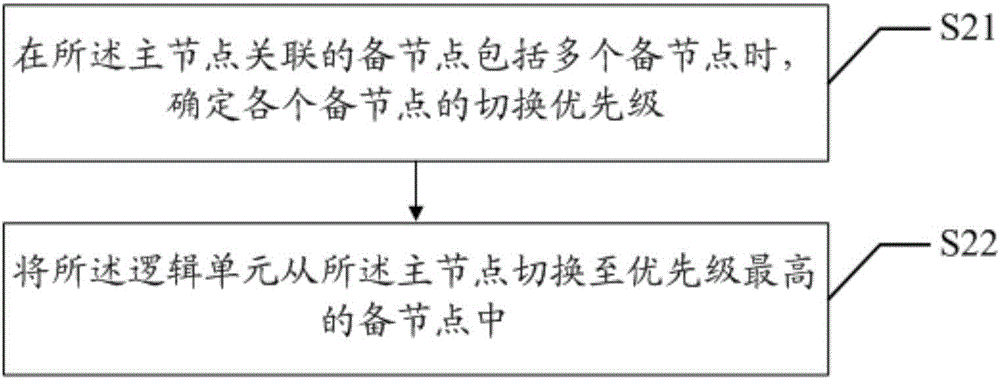
InactiveCN106557543APrevent lossRedundant operation error correctionSpecial data processing applicationsData synchronizationData loss
The invention discloses a node switching method applied to a city-wide production colony. The city-wide production colony comprises a main node and an auxiliary node, and a data synchronism mode is set between the main node and the auxiliary node. The node switching method includes the steps that when the main node of a logical unit in the city-wide production colony is down, the auxiliary node correlated with the main node is determined; the logical unit is switched to the auxiliary node from the main node, so that the auxiliary node is updated into the main node to provide data read-write service. The invention further discloses a node switching system. Data synchronism is adopted between the main node and the auxiliary node in the city-wide production colony, even if the main node is down, the logical unit can be fast switched into the auxiliary node and continues to provide data read-write service, and data loss is avoided.
Owner:WEBANK (CHINA)
Data processing method and device based on block chain and block chain system
The invention discloses a data processing method and device based on a block chain, and a block chain system. Two types of nodes are identified from all the computer nodes corresponding to the block chain: retrieval nodes and nodes to be stored; wherein the retrieval node is a node that satisfies preset conditions confirmed from all the computer nodes corresponding to the block chain; and the nodeto be stored is a node whose residual storage is larger than a preset residual storage threshold confirmed from all the computer nodes corresponding to the block chain. The data processing method based on the block chain comprises the following steps: using the retrieval node to obtain the data to be transmitted and the corresponding storage rules from a user node; processing the data to be transmitted according to the storage rules; and confirming a target storage node from a plurality of nodes to be stored, and storing the processed data to be transmitted in the target storage node.
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com