Anti-replay authentication method and system
An authentication method and authentication system technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the problems of high technical requirements and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
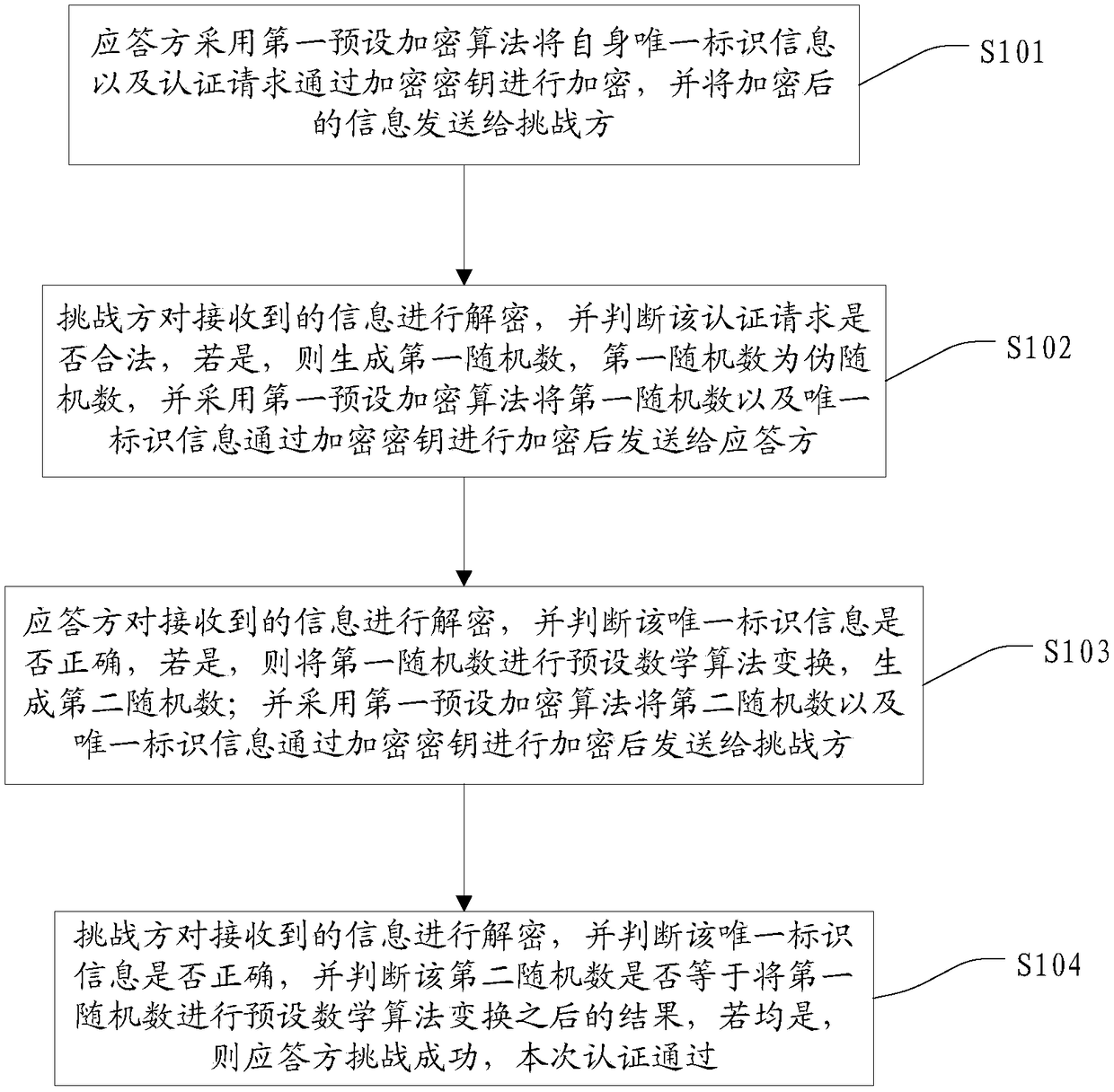
[0040] This embodiment provides an anti-replay authentication method, see figure 1 , figure 1 A flow chart of an anti-replay authentication method provided in this embodiment, the anti-replay authentication method includes the following steps:
[0041] S101: The responding party encrypts its own unique identification information and authentication request with an encryption key using a first preset encryption algorithm, and sends the encrypted information to the challenger;
[0042] The responding party is also the authenticated party, including IoT devices, smart terminals, etc., and the first preset encryption algorithm includes AES algorithm, DES algorithm, SM4 algorithm, etc.; the challenger is also the authenticating party, including IoT devices, etc.;
[0043] The encryption key is written into the chip by the outside world when the challenger's chip is produced, and the encryption key is a true random number.
[0044] The encryption key is generally written in the ins...
no. 2 example
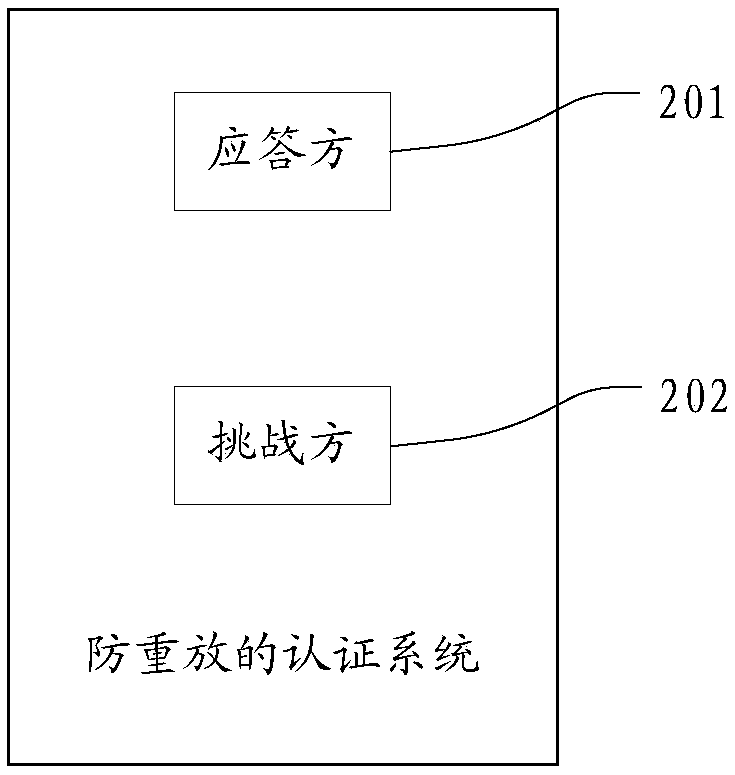
[0072] This embodiment provides an anti-replay authentication system, see figure 2 , figure 2 A schematic diagram of an anti-replay authentication system provided in this embodiment, the anti-replay authentication system includes: a responder 201 and a challenger 202;
[0073] The responder 201 is used to encrypt its own unique identification information and authentication request with an encryption key using a first preset encryption algorithm, and send the encrypted information to the challenger 202;
[0074] The responder 201 is also the authenticated party, including IoT devices, smart terminals, etc., and the first preset encryption algorithm includes AES algorithm, DES algorithm, SM4 algorithm, etc.; the challenger 202 is also the authenticating party, including IoT devices, etc.;
[0075] The encryption key is written into the chip by the outside when the chip of the challenger 202 is produced, and the encryption key is a true random number.
[0076] The encryption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com