Hawkeye anti-fraud big data risk control evaluation system
An evaluation system and big data technology, applied in data processing applications, instruments, finance, etc., can solve problems such as limited evaluation data, inability to meet, and risk control technology difficult to meet risk evaluation, etc., to expand the scope of customer sources and data, avoid The effect of gang fraud and increasing the review rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
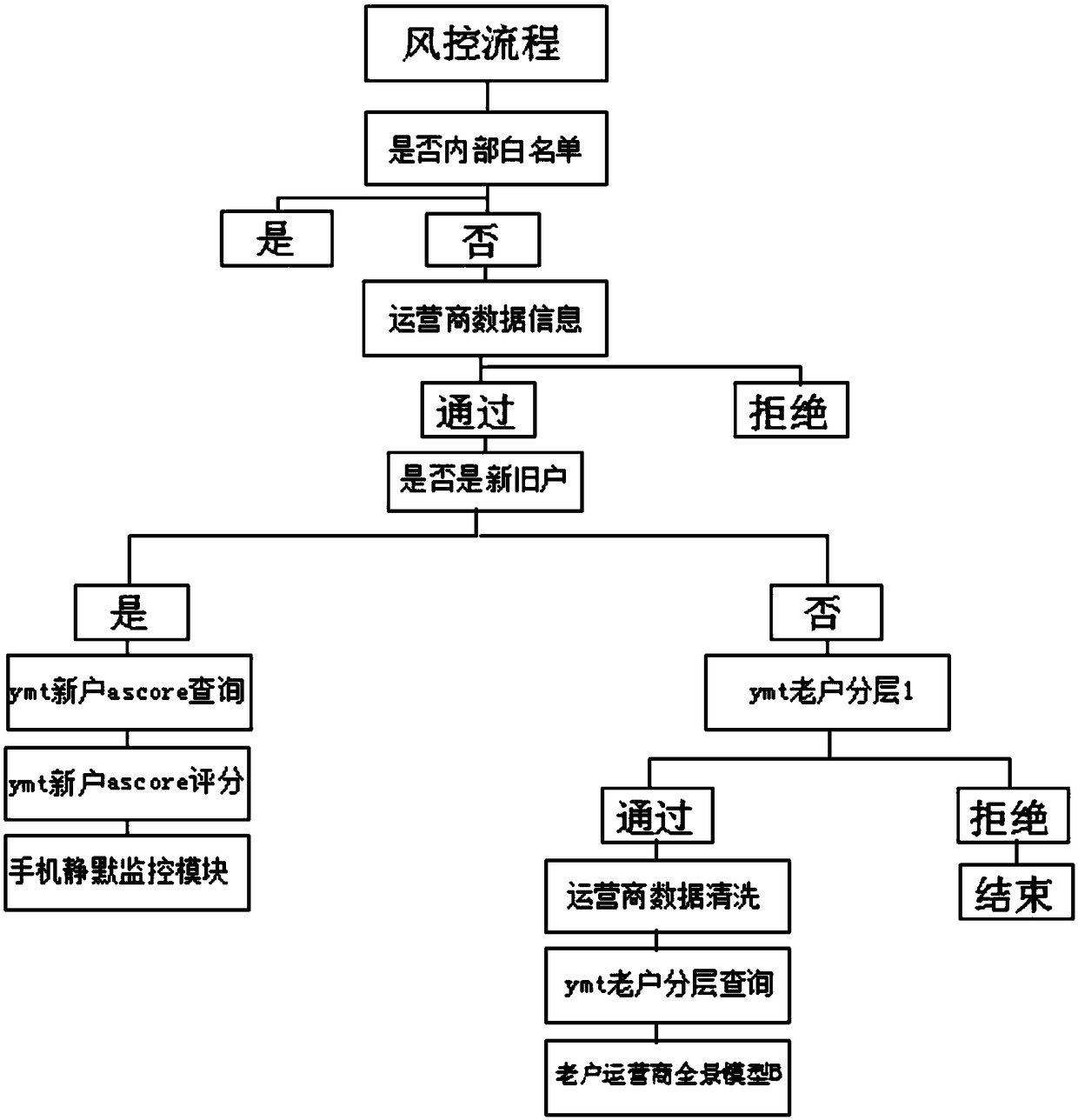
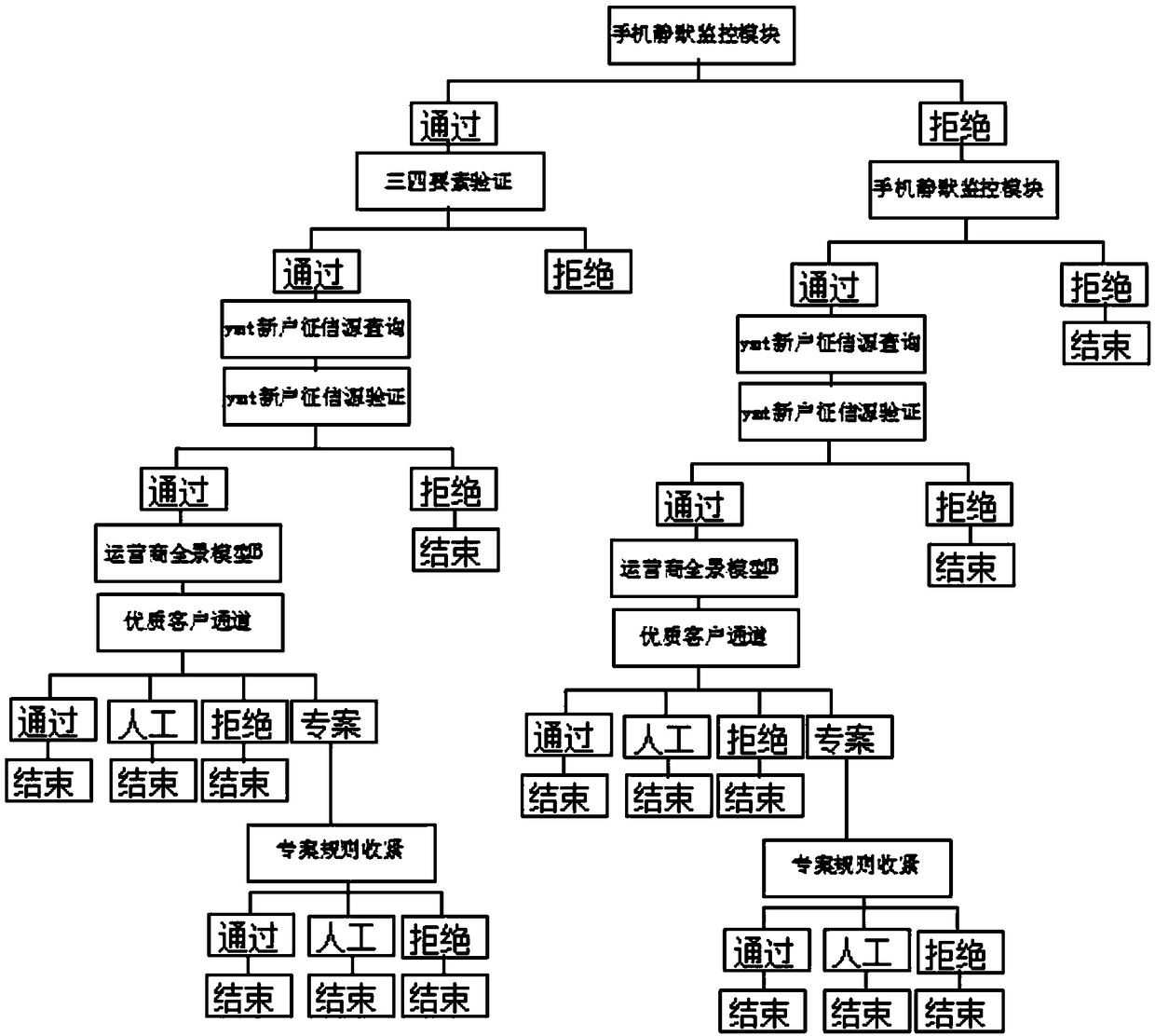
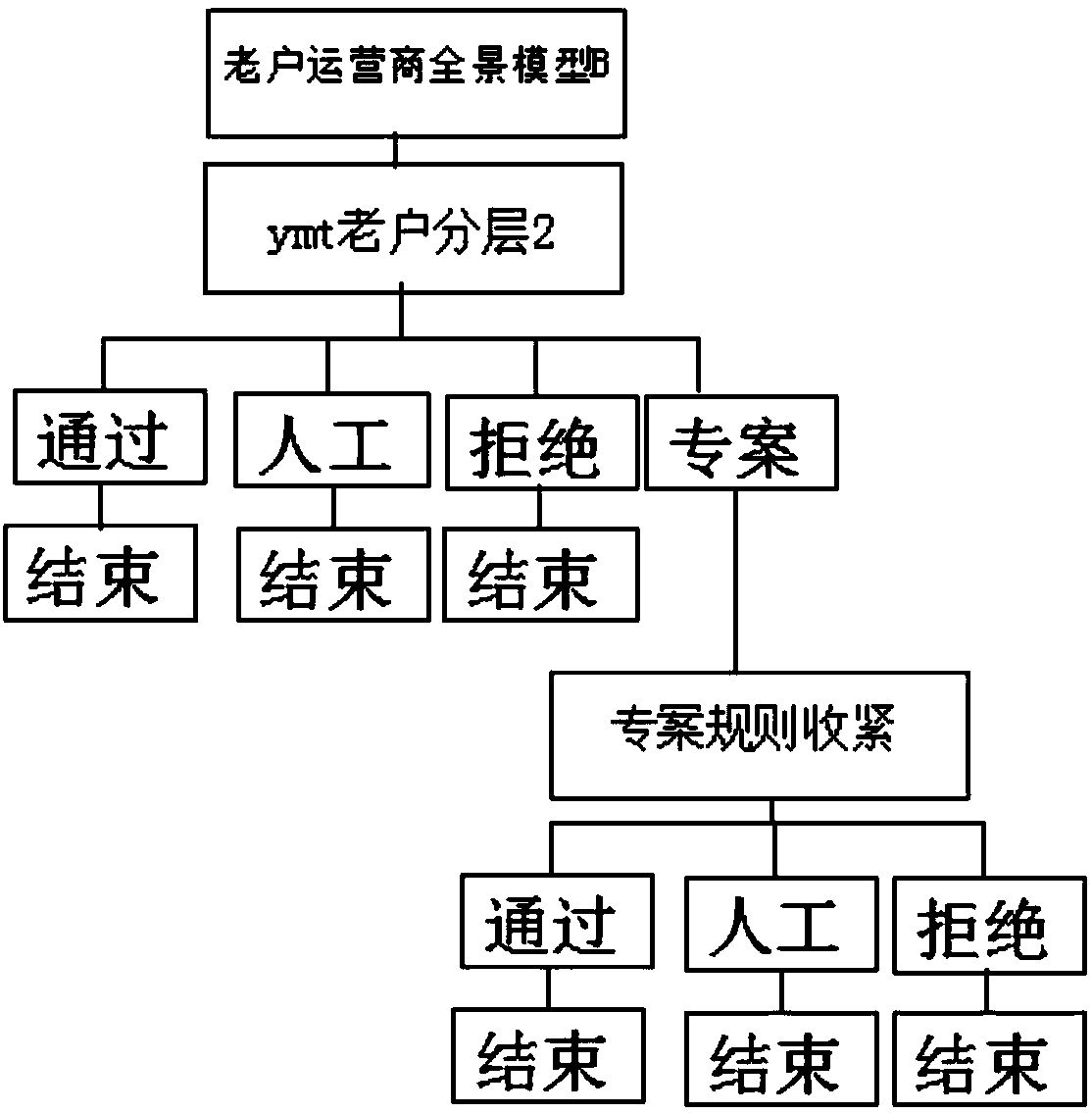
[0037] The Hawkeye anti-fraud big data risk control evaluation system includes original data, knowledge graph, user portrait, risk control model and risk control products, characterized in that: the original data is a basic data warehouse; the knowledge graph is a data governance platform; The user portrait includes a feature platform; the risk control model includes a model platform, and the model platform includes policy rules, score cards, and data mining; the risk control product includes a risk control platform.
[0038] In this embodiment, aiming at the shortcomings of traditional financial institutions' risk control, the "Hawkeye Anti-fraud Big Data Risk Control Evaluation System" is launched to form a new risk control plan for comprehensive analysis and evaluation of big data. We use data collection and cleaning technology, big data storage technology and big data intelligent data mining technology to complete the online collection risk assessment and decision-making of...
Embodiment 2
[0040] The basic data warehouse is to store all the data of any user that can be captured, including the address book, call records, text messages, mobile phone app installation and usage, buried point information data, device information data, etc. , It also includes that we pay for customers to obtain credit information source data, including social security, provident fund, UnionPay data, Zhima Credit, JD.com, Tencent and other credit data.
[0041] In this embodiment, here we will store the full amount of all user data that can be captured. Under normal circumstances, it includes the mobile phone address book, call records, text messages, mobile app installation and usage, buried point information data, device information data, etc. that the user authorizes to capture, and also includes the credit information source data that we pay for the customer to call. Credit data such as social security, provident fund, UnionPay data, Sesame Credit, JD.com, Tencent, etc. After captu...
Embodiment 3
[0043] The data governance platform is conducting in-depth analysis, mining, and cleaning on various dimensions of users. User data is split into six dimensions: user basic attribute data, user behavior data, user historical lending data, user authentication data, and user social relations. For data and user repayment ability data, the data governance platform includes the cleaning and transformation of raw data, storage definition according to business division, etc.
[0044] In this embodiment, the data governance platform is like a high-quality data processing factory. The data on this platform mainly conducts in-depth analysis, mining, and cleaning of various dimensions of users. For example, we split user data into six dimensions. The basic attribute data, user behavior data, user historical lending data, user authentication data, user social relationship data, user repayment ability data, etc., under each large data dimension, we have hundreds of important core indicators...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com