Anonymous network access method, client, system, server, and medium
An anonymous network and access method technology, applied in the system, anonymous network access method, client, server and media fields, can solve the problems of easy capture and tampering of data, insecure communication methods, etc., to reduce the possibility of stealing or tampering performance, enhanced overall security and reliability, fast and secure communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
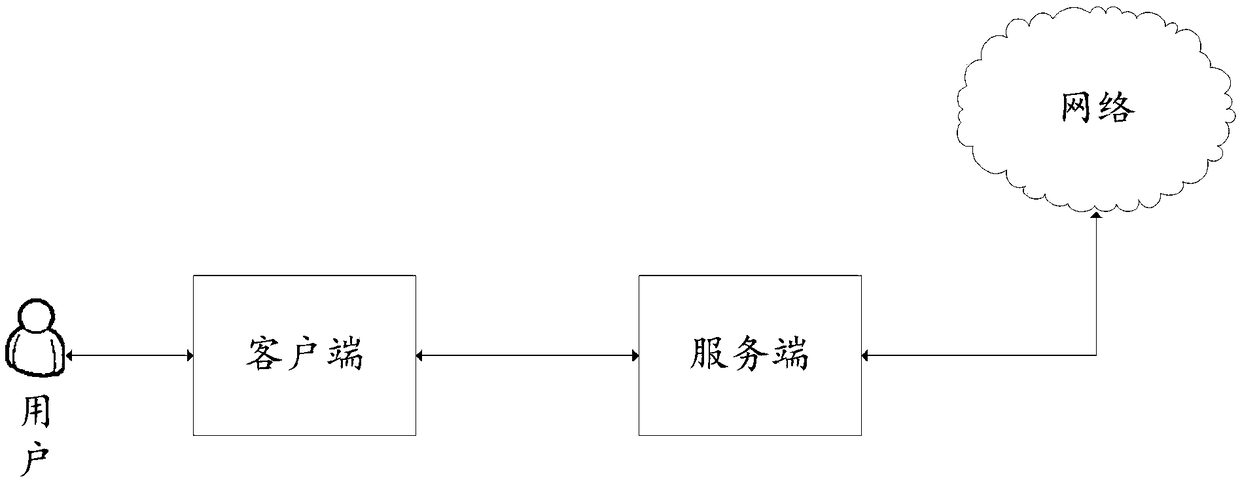
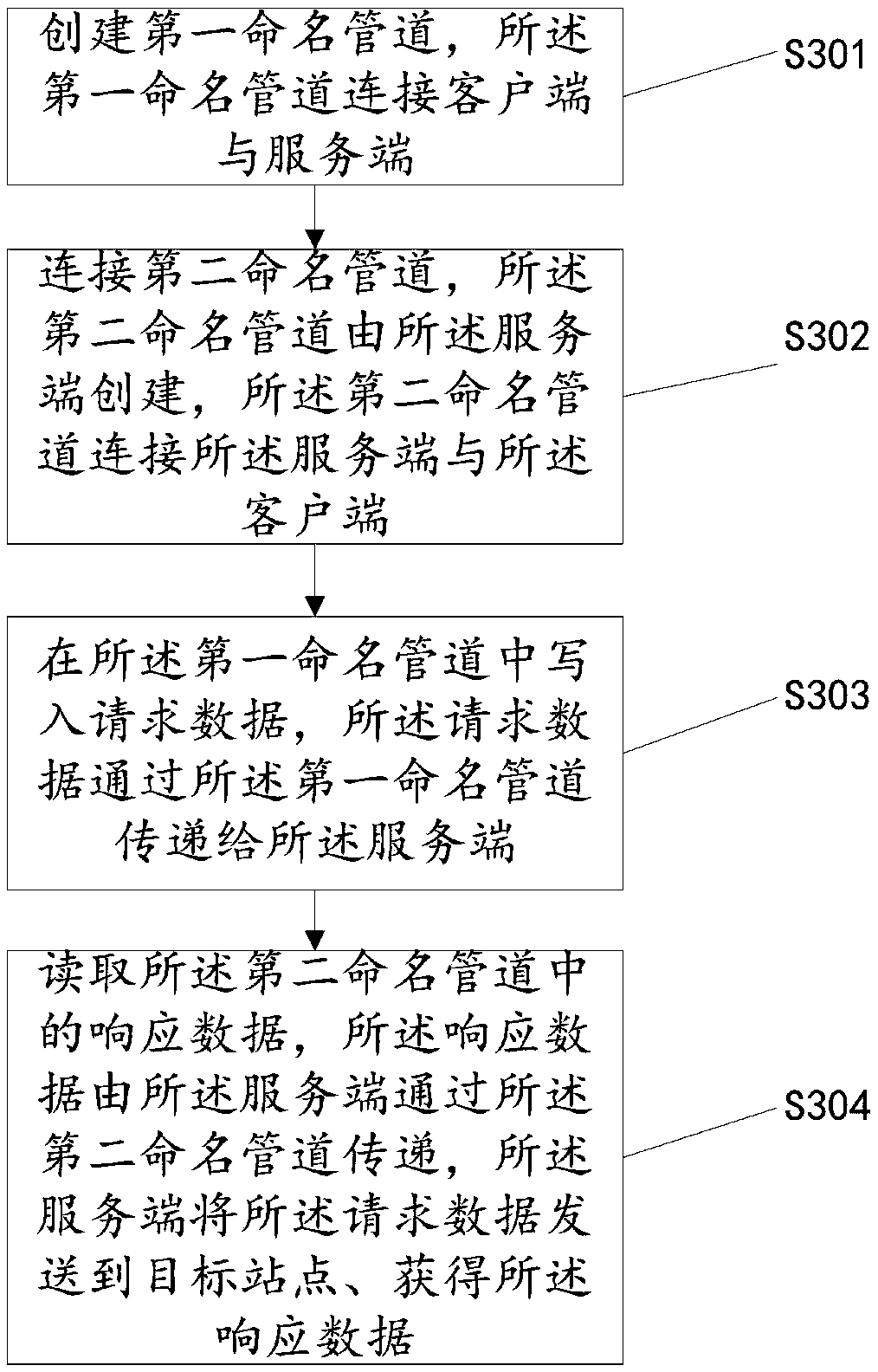
[0042] Example 1: Please refer to figure 2 , figure 2 It is a schematic diagram of a communication method between the client and the server provided by the embodiment of the present invention. The specific anonymous network access method is as follows: image 3 As shown, the method may include:
[0043] S301: Create a first named pipe, where the first named pipe connects the client and the server;
[0044] Such as figure 2 As shown, the user opens the Tor client, and the Tor client will create the first named pipe. Create a Pipe_C pipeline, the Pipe_C pipeline is used to transmit data to the Tor server. When the client establishes the first named pipe, it specifies a name, and the server can open the other end of the pipe through the name, and communicate with the client according to the given authority.
[0045] S302: Connect a second named pipe, the second named pipe is created by the server, and the second named pipe connects the server and the client;
[0046] Such ...
Embodiment 2
[0072] Example 2: Please refer to Figure 6 , Figure 6 It is a schematic diagram of a communication method between the client and the server provided by the embodiment of the present invention. The specific anonymous network access method is as follows: Figure 7 As shown, the method may include:
[0073] S701: Create a first memory file mapping object, where the first memory file mapping object and the second memory file mapping object created by the server point to the same memory;
[0074] After the Tor client starts, it will create a memory file mapping object named FileMappingObject, which is the first memory file mapping object, and the Tor client will then notify the Tor server to save the memory file mapping object, which is equivalent to creating a first memory file mapping object on the Tor server. Two memory file mapping objects. The two memory file mapping objects have the same name FileMappingObject and point to the same memory.
[0075] S702: Map the first m...
Embodiment 3
[0089] Example 3: Please refer to Figure 8 , Figure 8 It is a schematic diagram of a communication method between the client and the server provided by the embodiment of the present invention. The specific anonymous network access method is as follows: Figure 9 As shown, the method may include:
[0090] S901: Create a client stub code, where the client stub code communicates with the server stub code created by the server through the first network;
[0091] Using RPC (Remote Procedure Call, remote procedure call), the Tor client Stub (pile code) and the Tor server Stub are respectively used for the Tor client and the Tor server to realize the process of obtaining or sending data from the network to the network . In the process of RPC call, the client calls the service locally. After receiving the call, the client stub is responsible for assembling the method, parameters, etc. into a message body that can be transmitted over the network. The client stub finds the service ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com