A data leakage prevention system based on computer behavior
An anti-leakage, computer technology, applied in the field of information security, can solve problems such as loss, lack of security protection measures, enterprise loss, etc., and achieve the effect of safe and reasonable design, avoiding access and publishing information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
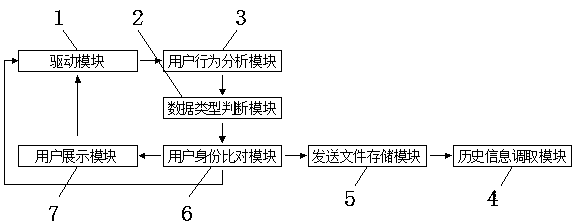
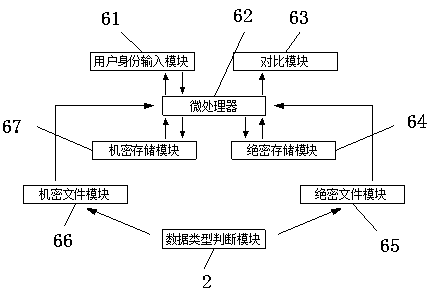
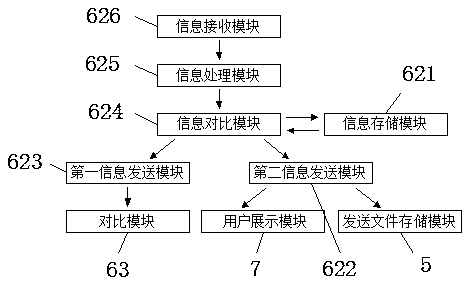
[0023] see Figure 1-3, the present invention provides the following technical solutions: a data leakage prevention system based on computer behavior, including a drive module 1, a user behavior analysis module 3 is arranged on one side of the driver module 1, and a data type judgment is arranged below the user behavior analysis module 3 Module 2, the data type judgment module 2 is provided with a user identity comparison module 6 away from the side of the user behavior analysis module 3, a side of the user identity comparison module 6 is provided with a sending file storage module 5, and the other side of the user identity comparison module 6 The side is provided with a user display module 7, and the side of the sending file storage module 5 away from the user identity comparison module 6 is provided with a historical information retrieval module 4, a driving module 1 and a user behavior analysis module 3, and a data type judgment module 2 and a user behavior analysis module. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com