A data processing method, terminal and watermark server
A data processing and server technology, applied in the field of data security, can solve problems such as the inability to effectively protect the rights and interests of data owners, the difficulty of accountability, and the inability to identify leakers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
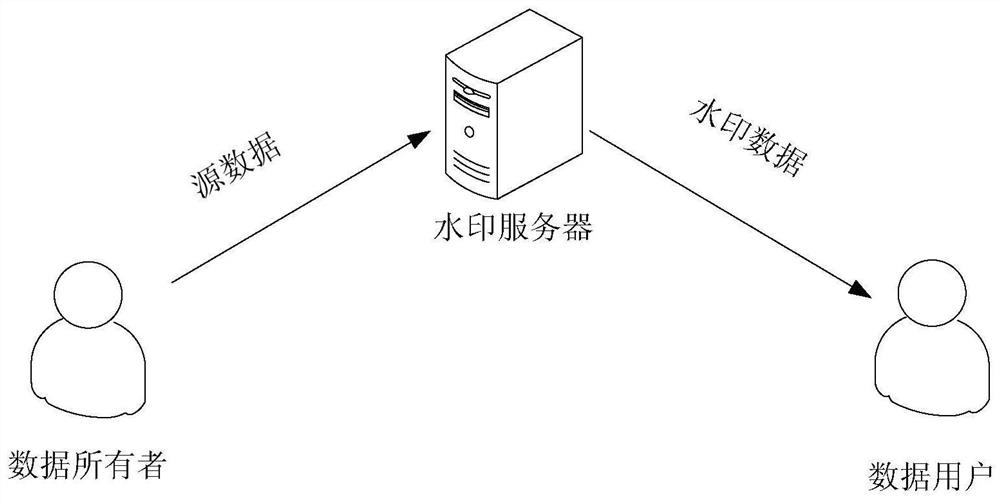
[0038] refer to figure 1 , the application scenarios of the data processing method of the present application include: data owners, watermark servers and data users.
[0039] The data owner sends the source file to the watermark server;
[0040] The watermark server embeds the digital watermark into the source file to obtain watermark data.
[0041] The data user receives the watermark data sent by the watermark server.
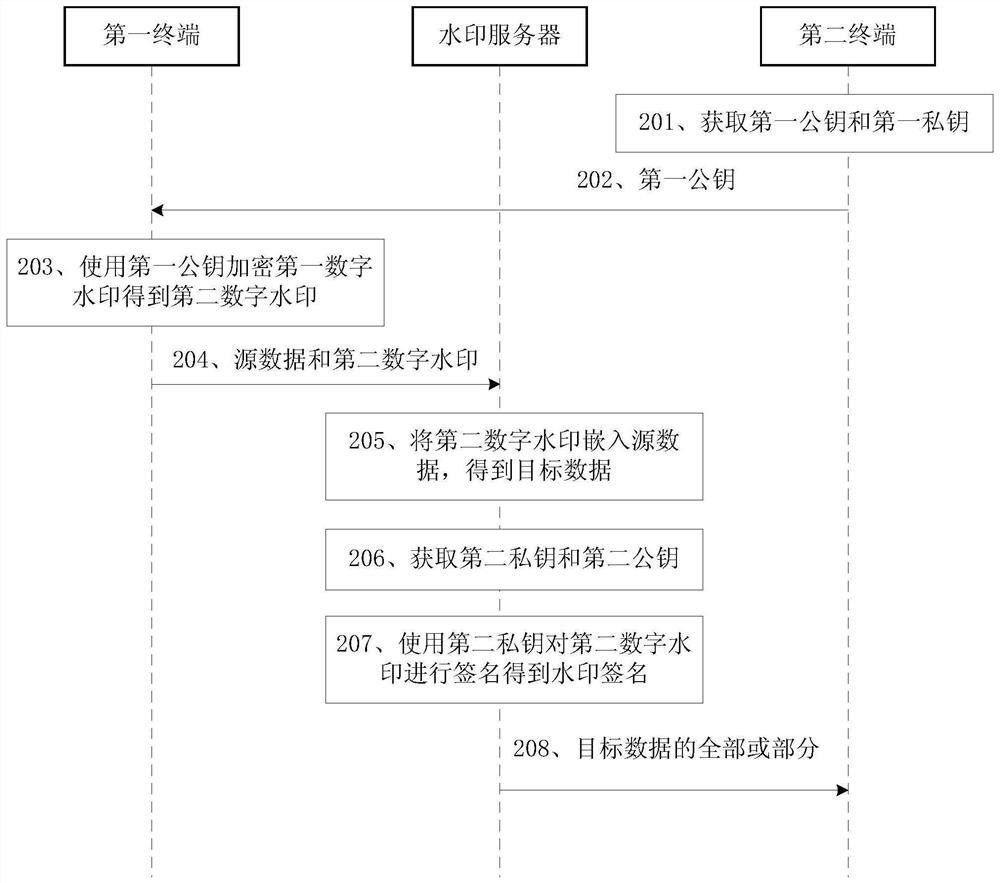
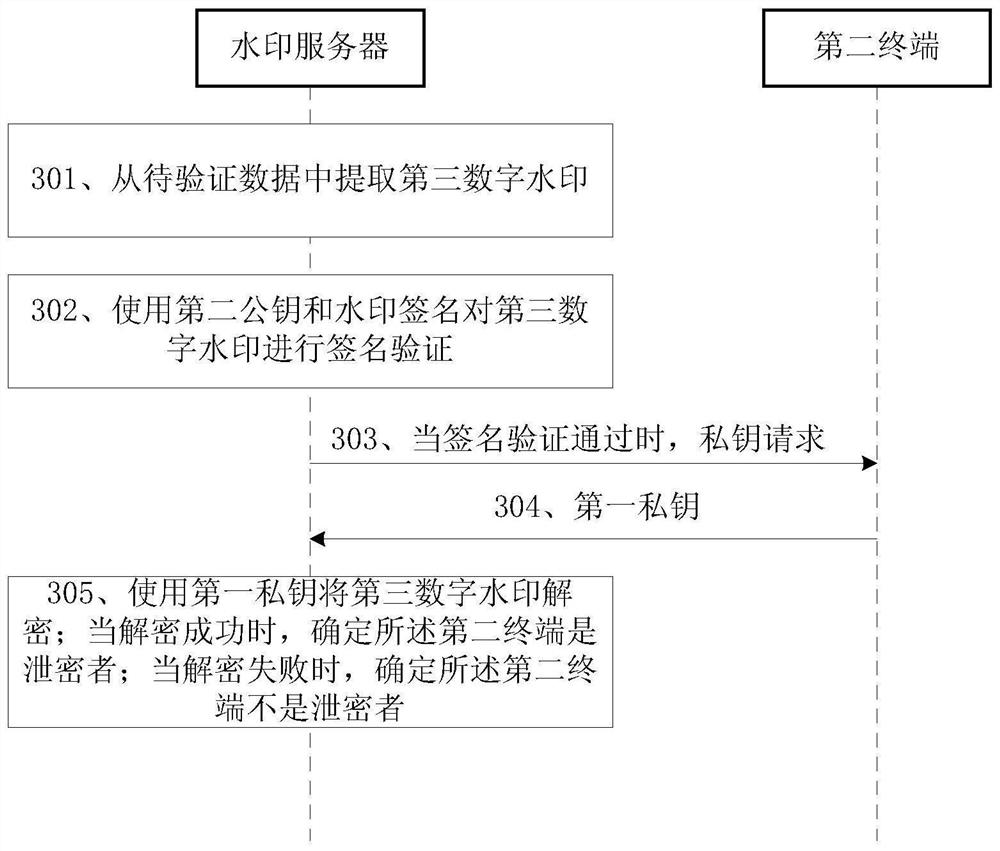
[0042] In the following content of this application, the terminal used by the data owner is marked as the first terminal, and the terminal used by the data user is marked as the second terminal.
[0043] A digital watermark may be an encoding of a sequence. When the watermark data is displayed on the display screen, the digital watermark is displayed on the background of the source data, which can be specifically displayed as text, graphics, symbols, etc. Source data can be database data, text data, etc. In the event of a copyright dispute, the data owne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com