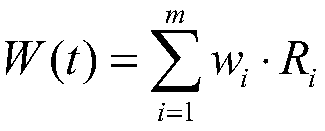Network security situation assessment method
A situation assessment and network security technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of complex effects, single influencing factors, and single data sources of link threat assessment methods, and achieve a good link situation , the method is simple and effective, and the effect of comprehensive situation assessment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in detail below in conjunction with the accompanying drawings.
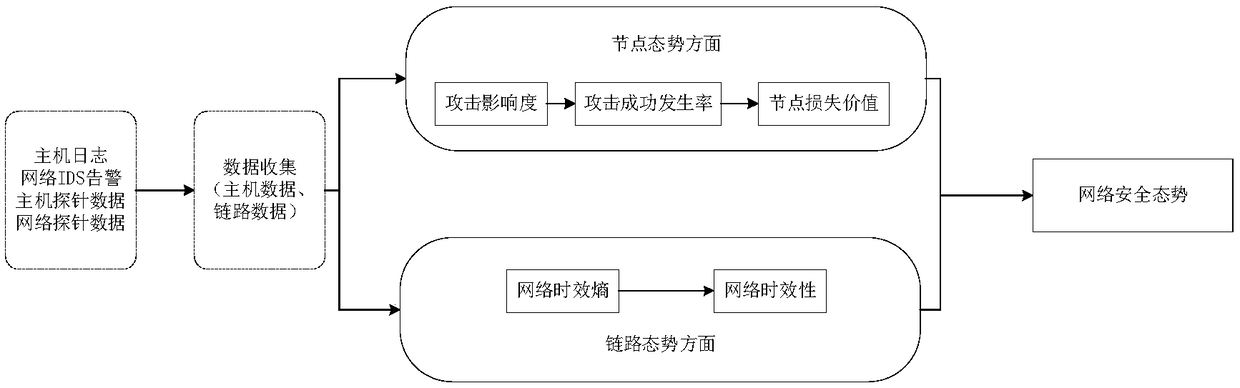
[0040] The present invention uses various indexes in the network as a basis, utilizes the index information collected by nodes and the index information collected by links, and according to the degree of attack threat received in the node, the occurrence rate of attack threat and the value of node loss, as well as the delay on the link, Congestion degree, packet loss rate, respectively calculate the node situation and link situation in the network, and then integrate the two to obtain the final security situation of the whole network. The present invention can effectively measure the state of the network according to the real-time information of the network, and the method is simple efficient.
[0041] see figure 1 , the present invention specifically comprises the following steps:
[0042] 1) First, monitor each host node and each network link in the network, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com