A scalable secure shadow storage and tag management method based on hardware isolation
A technology of hardware isolation and label management, applied in the field of information security, to achieve the effect of good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
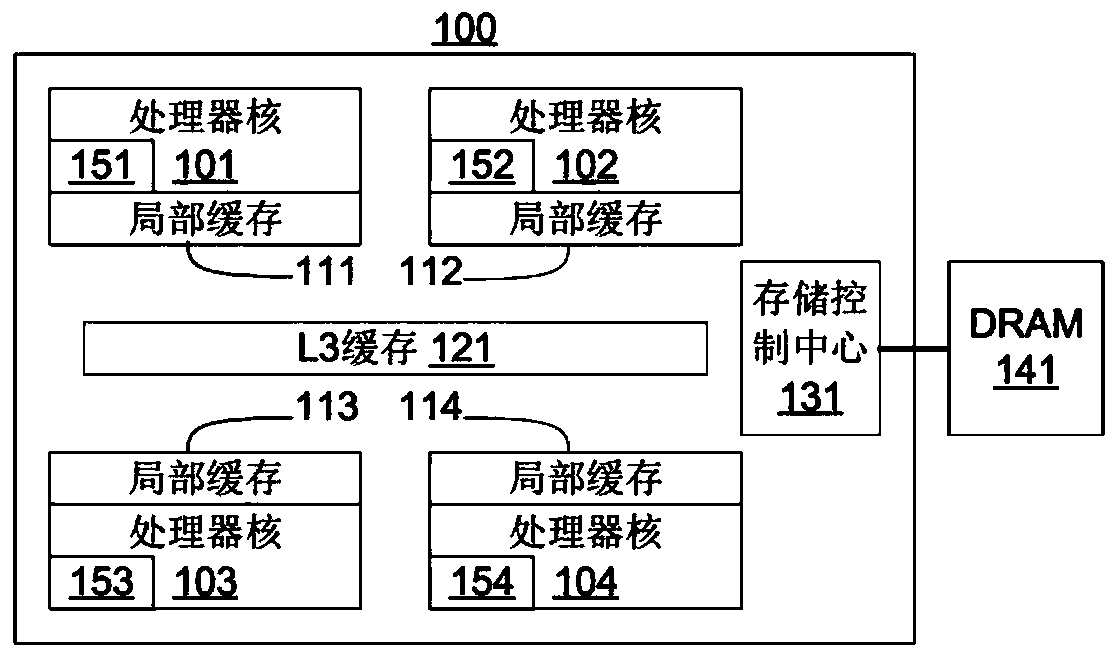
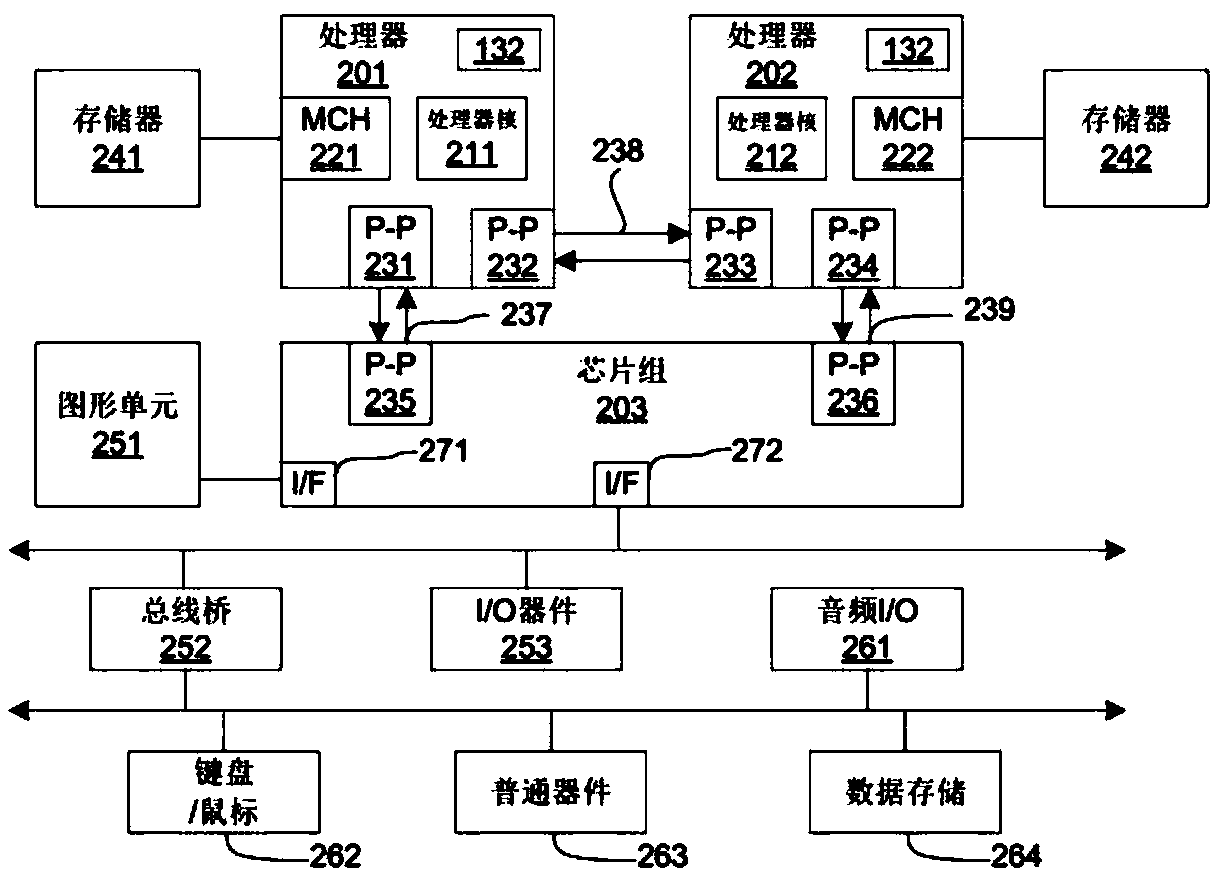
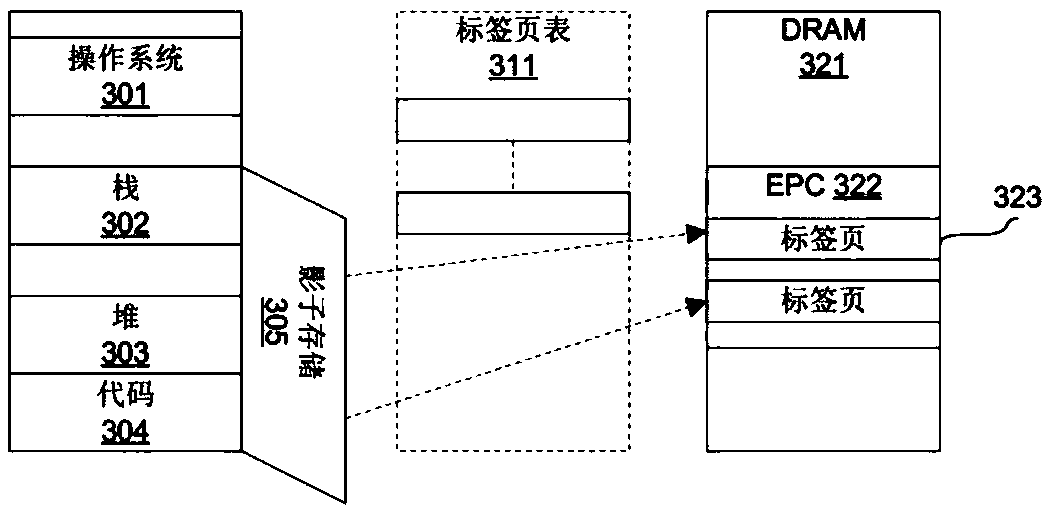
[0039] SGX guarantees that the software in the enclave is isolated from all software outside the enclave. SGX hardware-based isolation is at the heart of the SGX security model. SGX ensures that the code in the enclave can only access the EPC pages and non-EPC pages belonging to its own enclave through a series of storage operation checks, and the code in the non-enclave cannot access the storage within the PRM range. In addition, MEE enables SGX to prevent physical attacks, and the data of EPC pages can be safely swapped to disk. The present invention draw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com