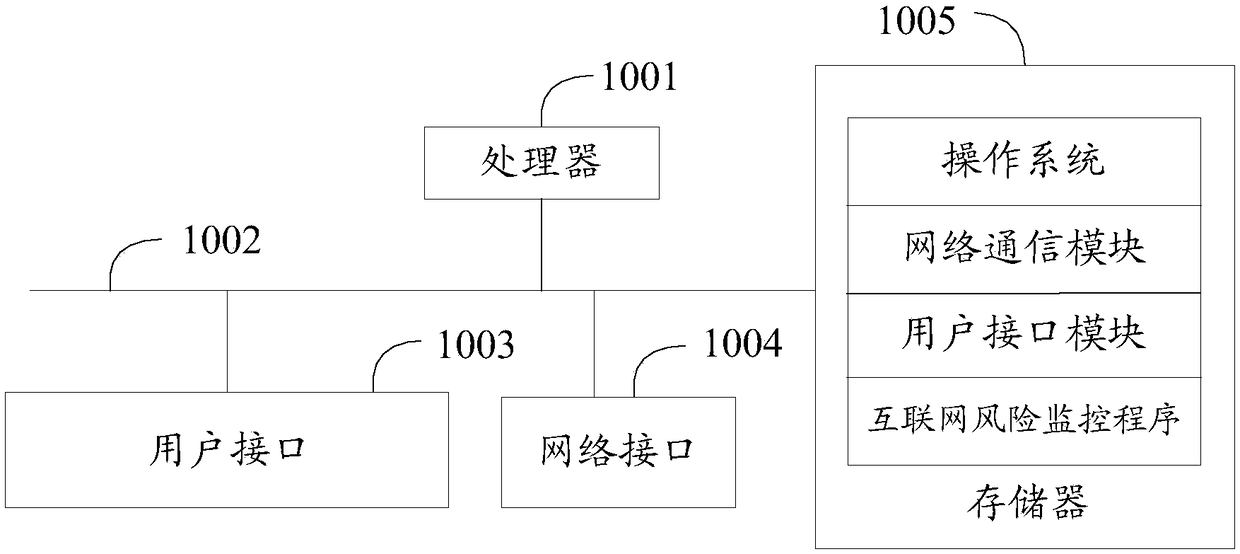
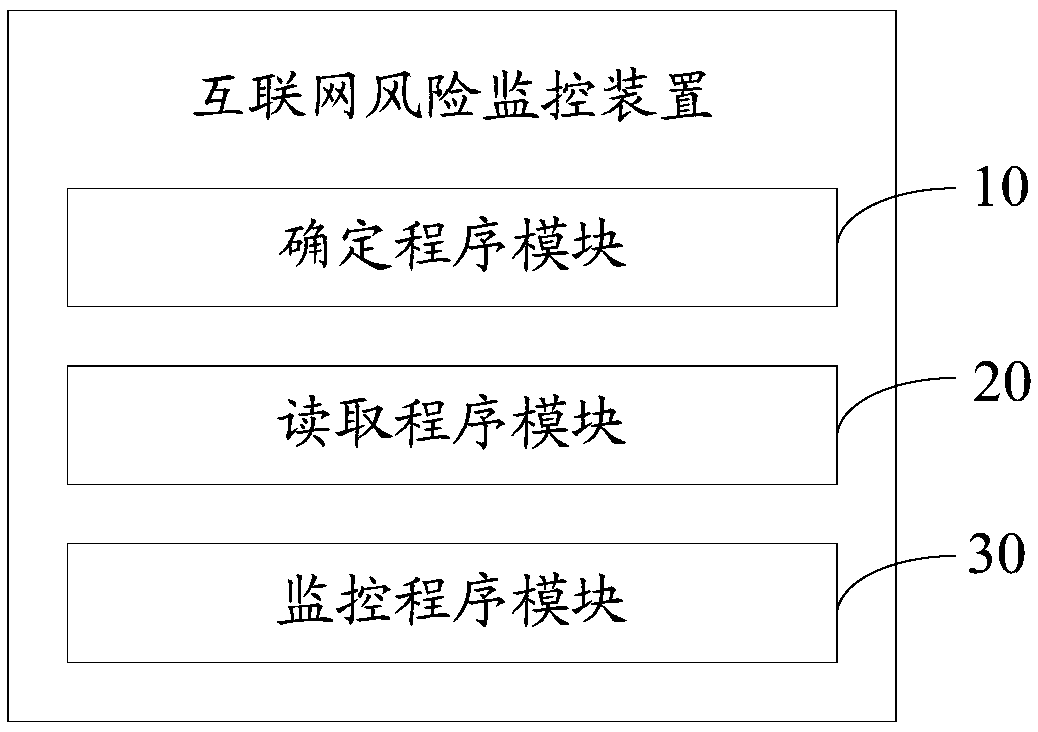
Internet risk monitoring method, device and equipment as well as storage medium
An Internet and Internet code technology, applied in the Internet field, can solve problems such as insufficient flexibility and scalability, narrow monitoring points and other issues, and achieve the effects of strong flexibility and scalability, comprehensive monitoring, and improved efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
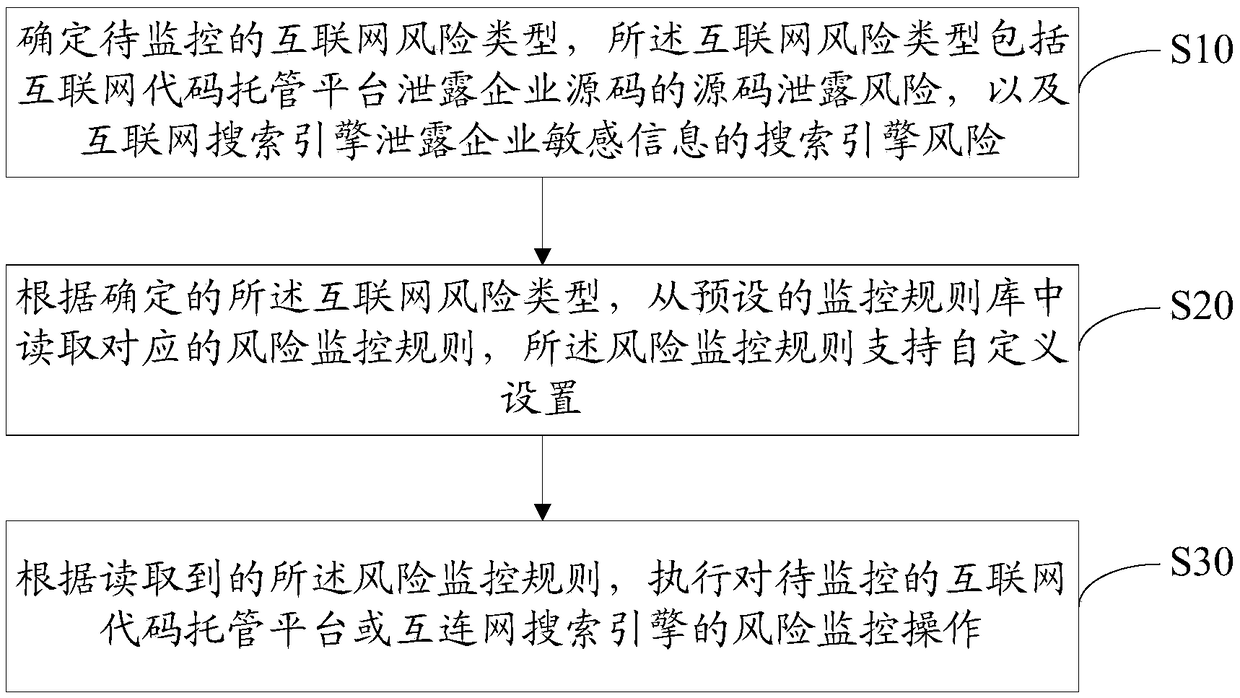
[0043] The main solution of the embodiment of the present invention is to determine the Internet risk type to be monitored, and the Internet risk type includes the source code leakage risk of the Internet code hosting platform leaking the source code of the enterprise, and the search engine risk of the Internet search engine leaking the sensitive information of the enterprise; according to The determined Internet risk type reads the corresponding risk monitoring rules from the preset monitoring rule library, and the risk monitoring rules support custom settings; according to the read risk monitoring rules, the Internet to be monitored is executed. Risk monitoring operations of code hosting platforms or Internet search engines.
[0044] In the prior art, monitoring for Internet information leakage mainly includes the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com