Secure Interaction Method for Wireless Cooperative Communication
A technology of cooperative communication and interaction method, applied in the field of wireless cooperative communication security interaction, can solve the problem of not forming a security mechanism, restricting communication nodes, etc., and achieve the effects of good security guarantee, efficient and secure interaction, and reduced complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, but it should be understood that the protection scope of the present invention is not limited by the specific embodiments.
[0015] Unless expressly stated otherwise, throughout the specification and claims, the term "comprise" or variations thereof such as "includes" or "includes" and the like will be understood to include the stated elements or constituents, and not Other elements or other components are not excluded.
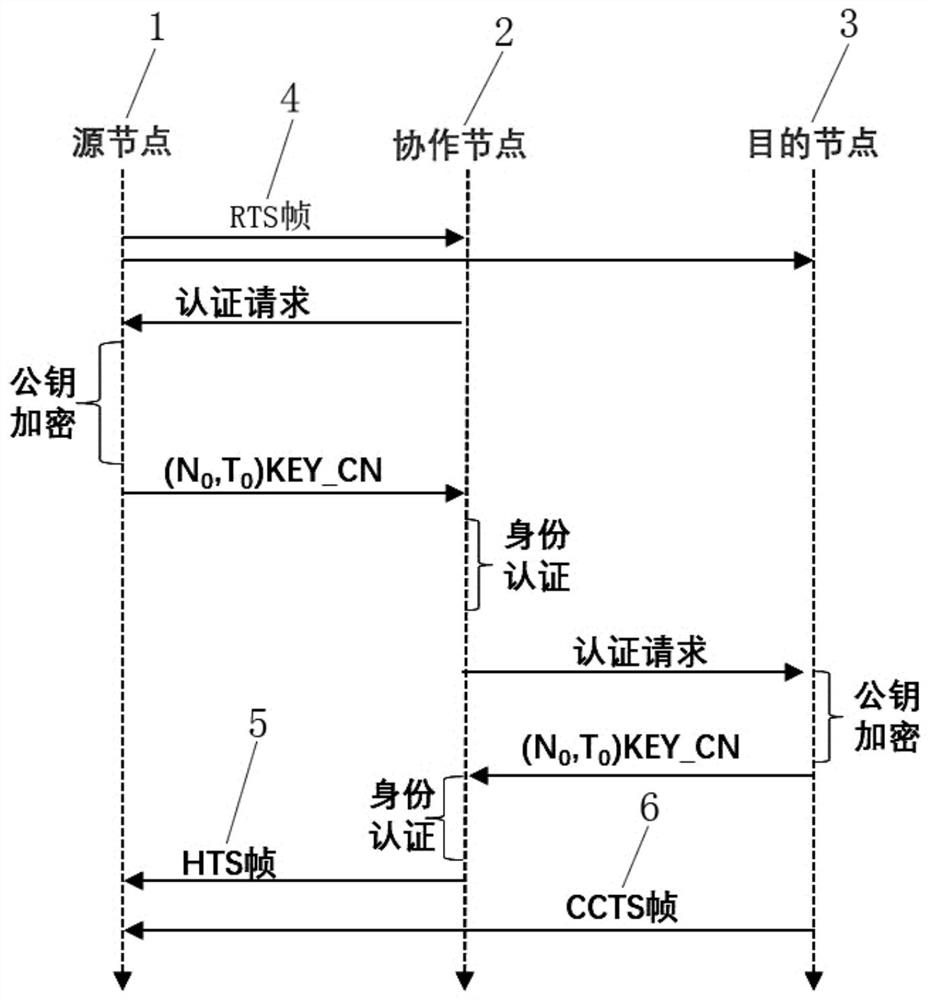
[0016] Such as figure 1 as shown, figure 1 It is a schematic diagram of an interaction process of a secure interaction method for wireless cooperative communication according to an embodiment of the present invention.
[0017] A secure interaction method for wireless cooperative communication according to a preferred embodiment of the present invention, comprising the following steps: the source node 1 sends the RTS frame...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com