WMN (Wireless Mesh Network)-based node accessing control method and device
An access control and node technology, applied in access restriction, connection management, electrical components, etc., can solve problems such as clock asynchrony, improve resource utilization, and facilitate resource scheduling.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
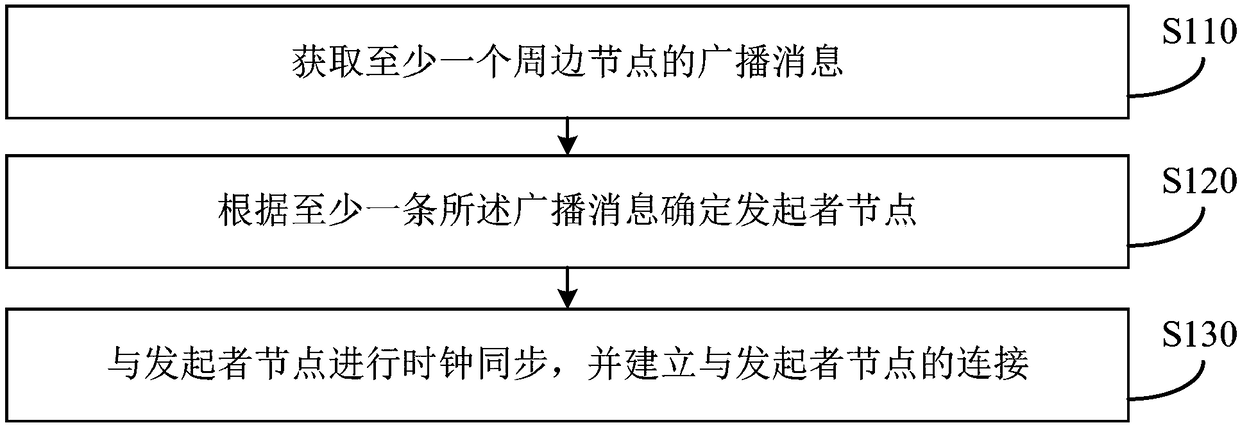
[0031] Figure 1a It is a flow chart of a WMN-based node access control method provided by Embodiment 1 of the present invention. The node access control method provided in this embodiment is applicable to a scenario in which a new node accesses an adjacent node in a WMN. The node access control method provided in this embodiment can be executed by a WMN-based node access control device, which can be implemented in software and / or hardware, and integrated into the equipment of the node to be accessed. Wherein, the node to be accessed refers to a new node in the WMN that is ready to be accessed with other peripheral nodes.
[0032] refer to Figure 1a A WMN-based node access control method provided in this embodiment specifically includes:
[0033] S110. Obtain a broadcast message of at least one peripheral node.
[0034] All the node access control methods provided in this embodiment may be executed by a media access control layer (Media Access Control, MAC) of the node to b...
Embodiment 2
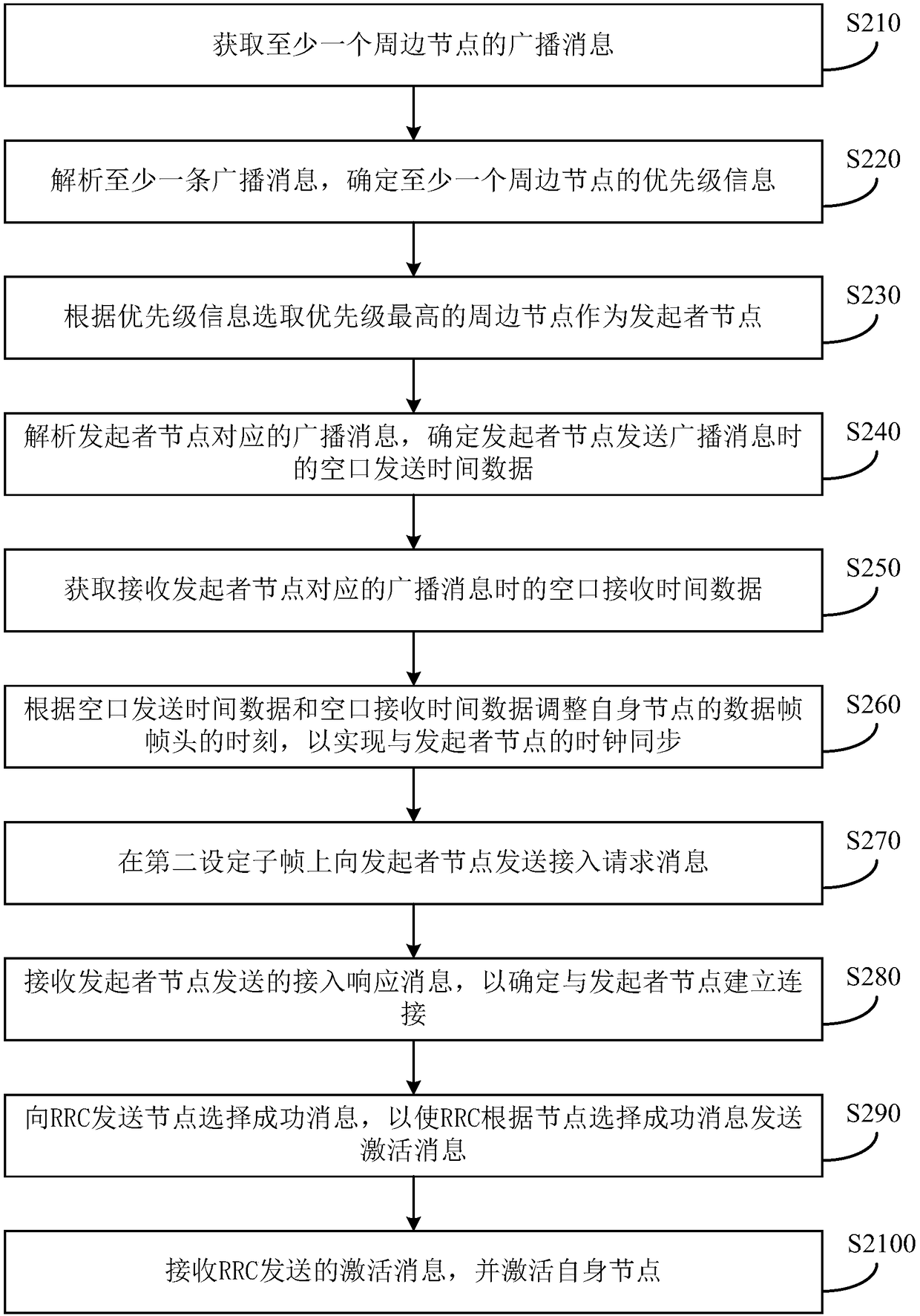
[0052] Figure 2a It is a flow chart of a WMN-based node access control method provided by Embodiment 2 of the present invention. This embodiment is embodied on the basis of the above-mentioned embodiments. Specifically, refer to Figure 2a A WMN-based node access control method provided in this embodiment specifically includes:
[0053] S210. Obtain a broadcast message of at least one peripheral node.
[0054] S220. Parse at least one broadcast message, and determine priority information of at least one peripheral node.
[0055] Exemplarily, the specific parsing manner of the broadcast message is not limited in this embodiment. After parsing at least one broadcast message, the priority information of at least one peripheral node is obtained from the broadcast message.
[0056] Wherein, the priority information includes synchronization priority and / or CQI. In this embodiment, priority information including synchronization priority and CQI is used as a preferred example f...
Embodiment 3
[0110] Figure 3a It is a flow chart of a WMN-based node access control method provided by Embodiment 3 of the present invention. This embodiment is embodied on the basis of the above-mentioned embodiments. Specifically, refer to Figure 3a A WMN-based node access control method provided in this embodiment specifically includes:
[0111] S310. Receive a node configuration message sent by the RRC.
[0112] Specifically, when the node to be accessed detects that it is powered on, the RRC of the node to be accessed configures its own node through an Ethernet message, and generates a node configuration message. Among them, the node configuration message can optionally include: configuration parameters such as the maximum number of nodes allowed by the network, bandwidth, and frequency point, and can also optionally include: configuration parameters for enabling switches with special functions such as frequency selection, authentication, and service priority . Further, the RRC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com