Two-dimensional-code security protection method and system
A security protection and two-dimensional code technology, applied in the field of two-dimensional code security protection methods and systems, can solve the problems of no unified security authentication method and certification center, two-dimensional code detection cannot be treated differently, unfavorable promotion and use, etc. To achieve the effect of convenient promotion and use, protection and security, and convenient access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] First of all, it needs to be explained that the present invention is an application of computer technology. During the implementation of the present invention, the application of multiple software function modules will be involved. The applicant believes that, after carefully reading the application documents and accurately understanding the realization principle and purpose of the present invention, combined with existing known technologies, those skilled in the art can fully implement the present invention by using their software programming skills. Everything mentioned in the application documents of the present invention belongs to this category, and the applicant will not list them one by one.
[0058] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
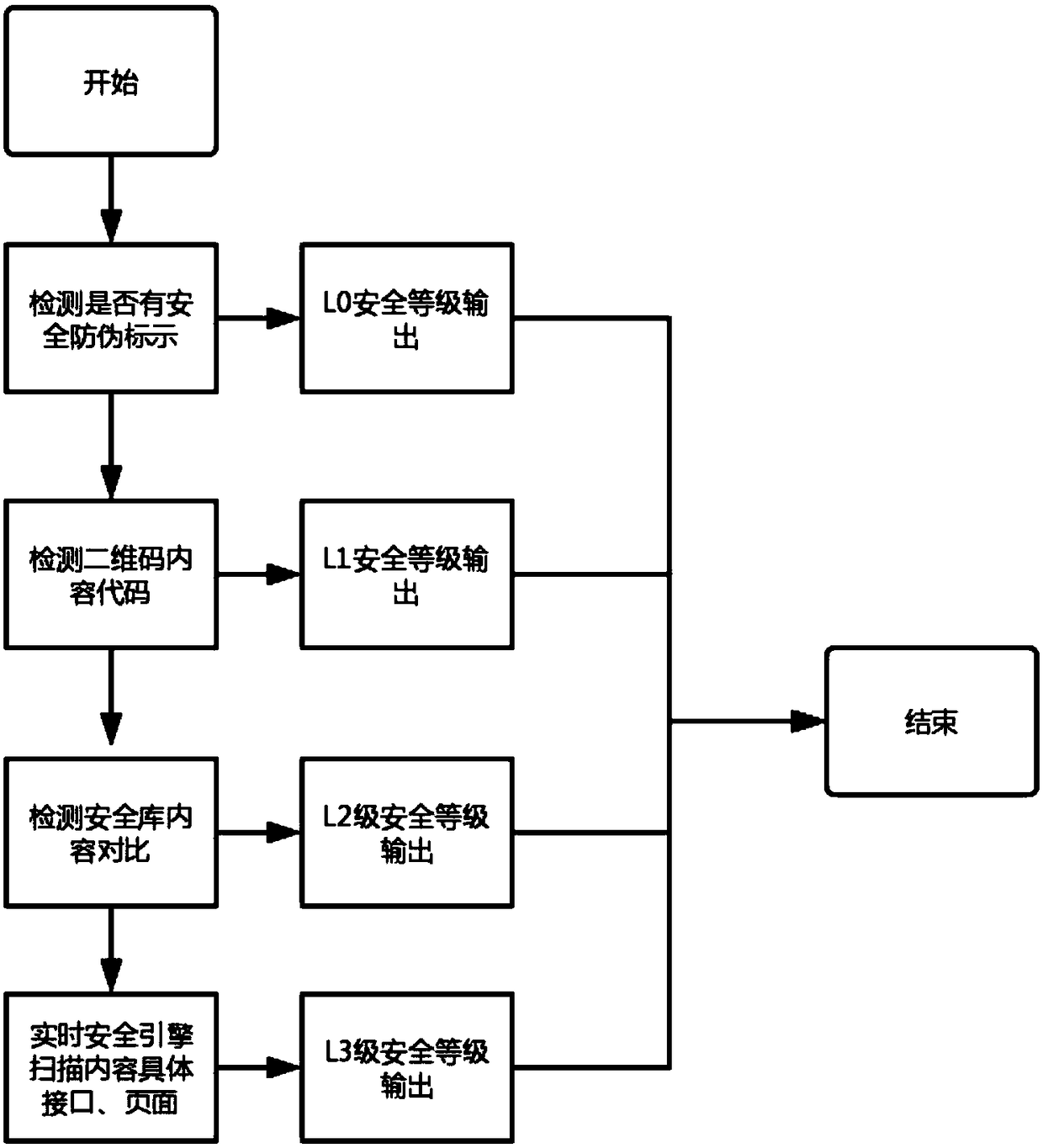
[0059] For QR code security, it is divided into two types of rectification schemes on a large scale: the first is to do corresponding secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com