Low-speed DDoS attack defense method and system
A low-speed, attacker technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to judge users, inability to achieve attack defense, etc., to achieve the effect of improving network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
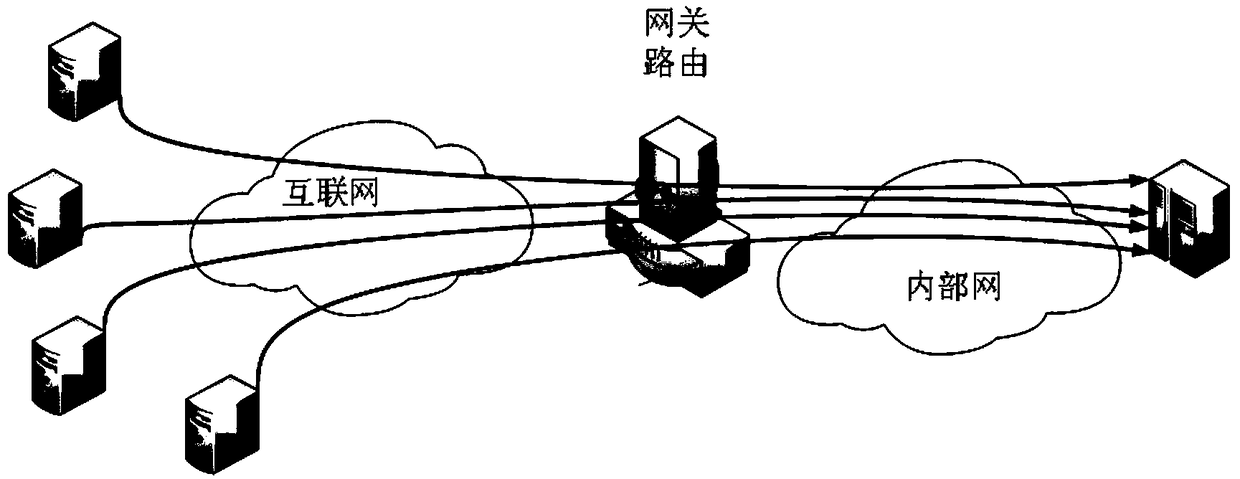
[0048] The network model based on the low-speed DDoS attack defense studied in the present invention is as follows: figure 1 As shown, users in the Internet access the internal network through a central gateway, and the internal network consists of server farms. The central gateway includes a central router and a central server. The central router is responsible for real-time data forwarding and online attack defense, while the central server can implement offline decoding.
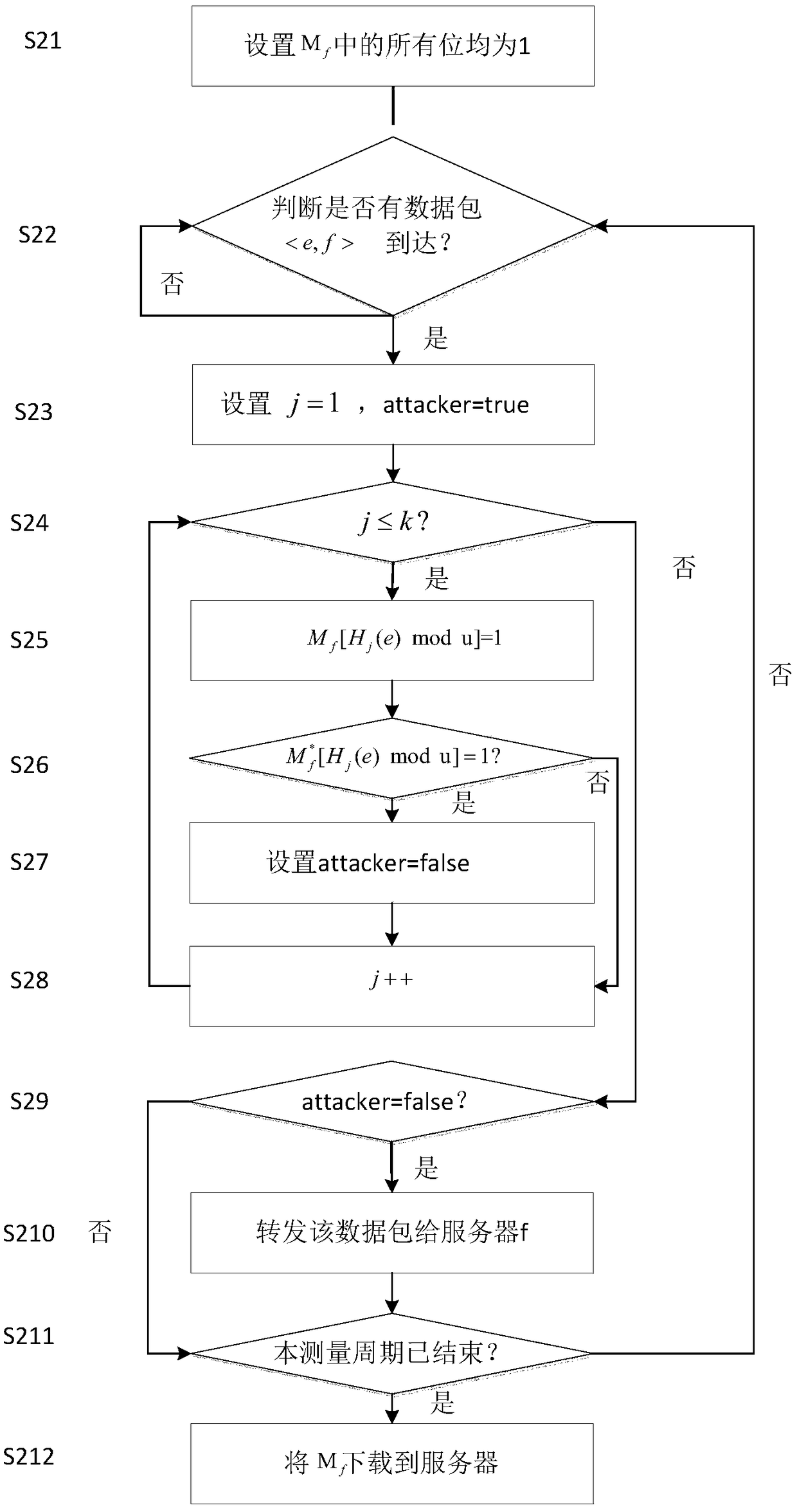
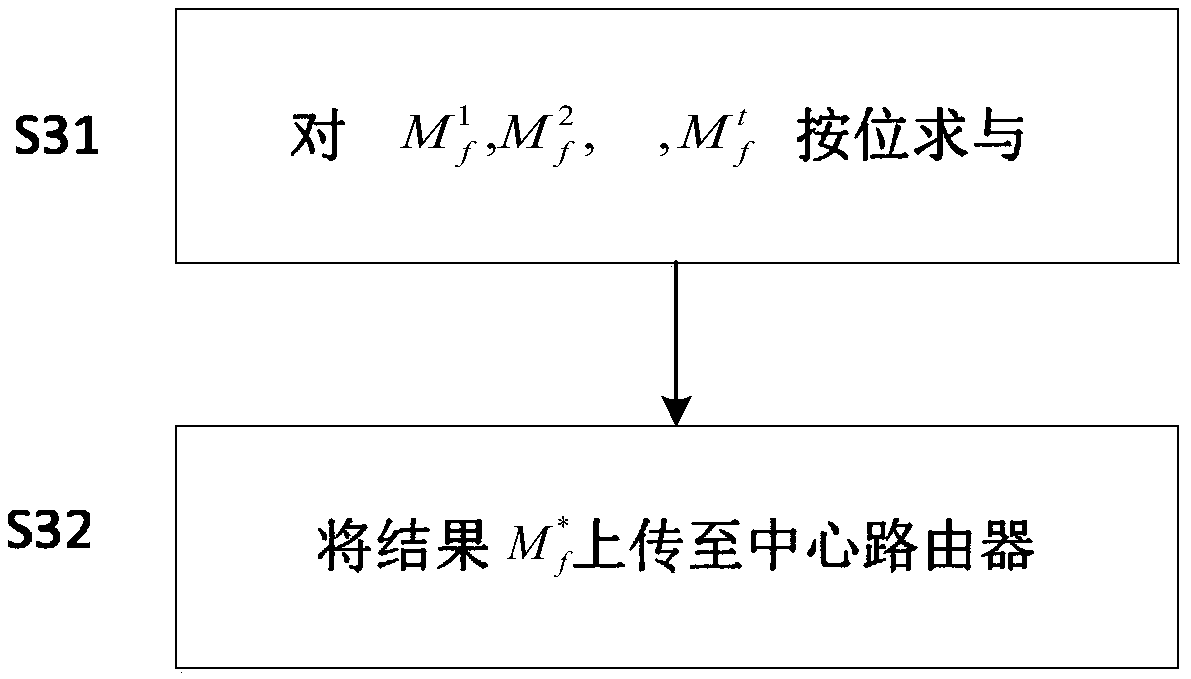
[0049] like figure 2 As shown, the specific implementation steps of the low-speed DDoS attack defense online coding flowchart based on the continuous attack model (the attacker has accessed the attacked server within a given t period) involved in the summary of the invention are as follows:
[0050] S21: At the beginning of each measurement cycle, initialize M f All bits are 0.
[0051] S22: Determine whether a data packet arrives? If a data packet arrives, continue to execute S23; otherwise, wait f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com