A mobile terminal screenshot authentication method and system
A mobile terminal and authentication system technology, which is applied in the field of mobile terminal screenshot authentication methods and systems, can solve the problems that it is difficult for users to effectively supervise screen capture actions, without supervision, etc., and achieve the effect of improving real effectiveness, effective monitoring and management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
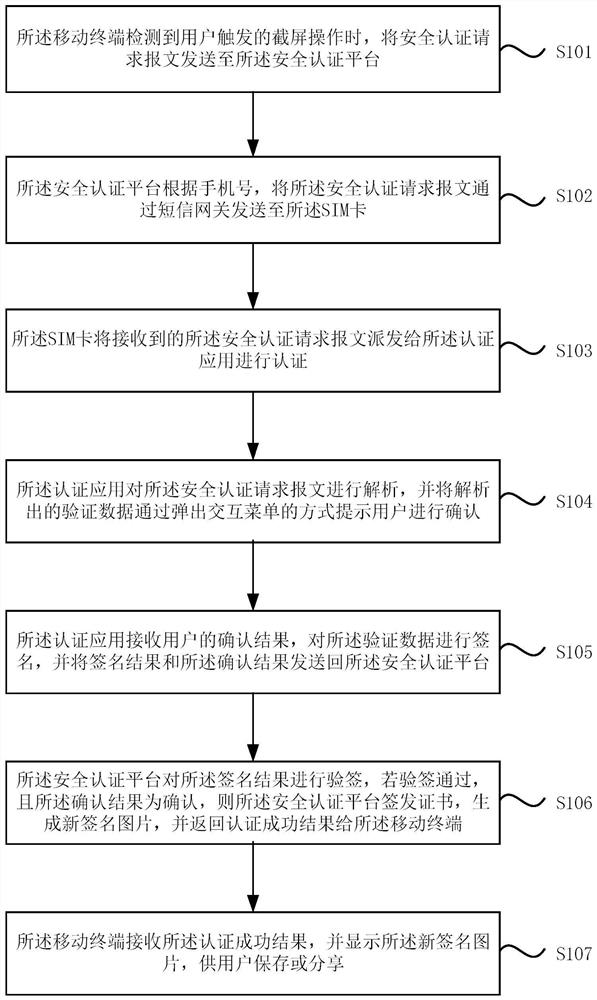
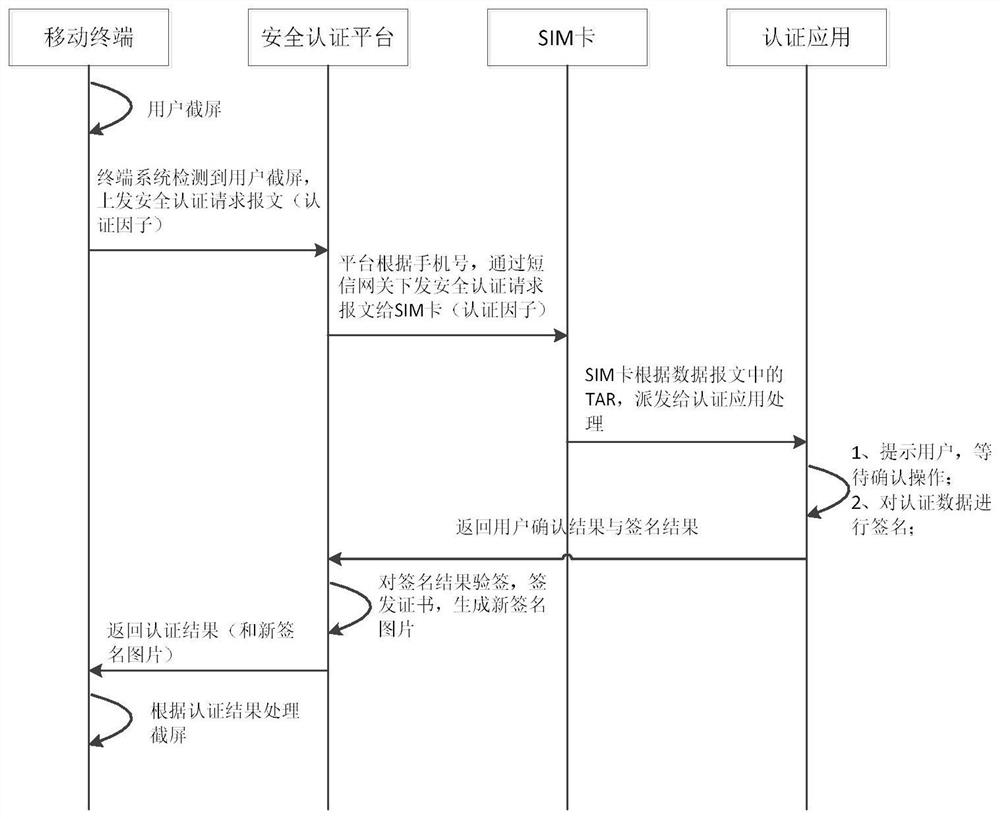
[0053] Please refer to the attached figure 1, is a schematic flowchart of a mobile terminal screenshot authentication method provided in Embodiment 1 of the present invention. This method is applicable to the scene where a customer takes a screenshot of the screen content on a mobile terminal, and the method is executed by a mobile terminal screenshot authentication system. The mobile terminal screenshot authentication system includes a mobile terminal, a SIM card set in the mobile terminal, a security authentication platform and a trusted service platform, and the SIM card stores authentication applications downloaded through the trusted service platform. The method specifically includes the following steps:
[0054] S101. When the mobile terminal detects a screen capture operation triggered by a user, it sends a security authentication request message to the security authentication platform.
[0055] S102. The security authentication platform sends the security authenticati...
Embodiment 2
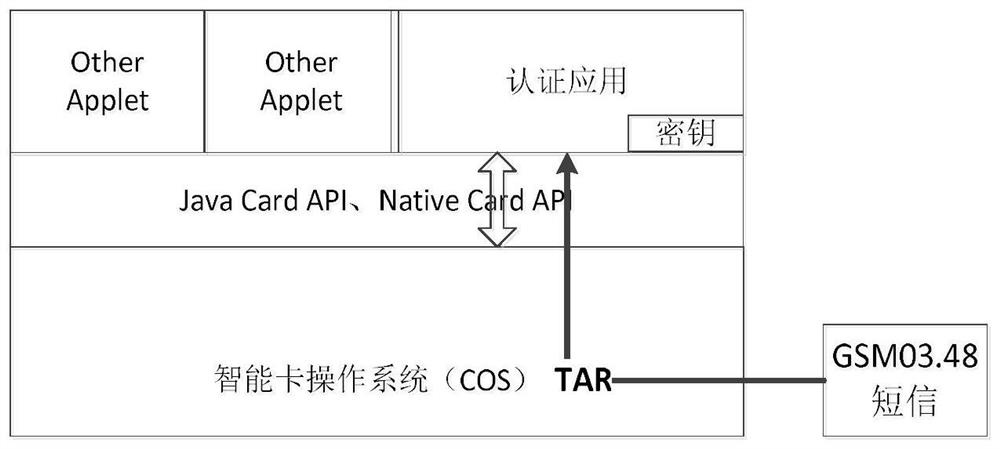
[0113] Please refer to the attached Figure 5 , is a schematic structural diagram of a mobile terminal screenshot authentication system provided in Embodiment 2 of the present invention, and the device is suitable for executing the mobile terminal screenshot authentication method provided in the embodiment of the present invention.
[0114] Described system comprises mobile terminal 51, the SIM card 52 that is arranged in described mobile terminal 51, security authentication platform 53 and trusted service platform 54, and described SIM card 52 stores the authentication that is downloaded by described trusted service platform 54. apply 55;
[0115] The mobile terminal 51 is configured to send a security authentication request message to the security authentication platform 53 when detecting a screenshot operation triggered by a user;
[0116] The security authentication platform 53 is used to send the security authentication request message to the SIM card 52 through the SMS ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com