A security data authentication method, system and device
A data and authentication technology, applied in the field of navigation, can solve problems such as long waiting time, disappearance, and case delay, and achieve the effect of improving legitimacy and usability, improving real validity, and reducing time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
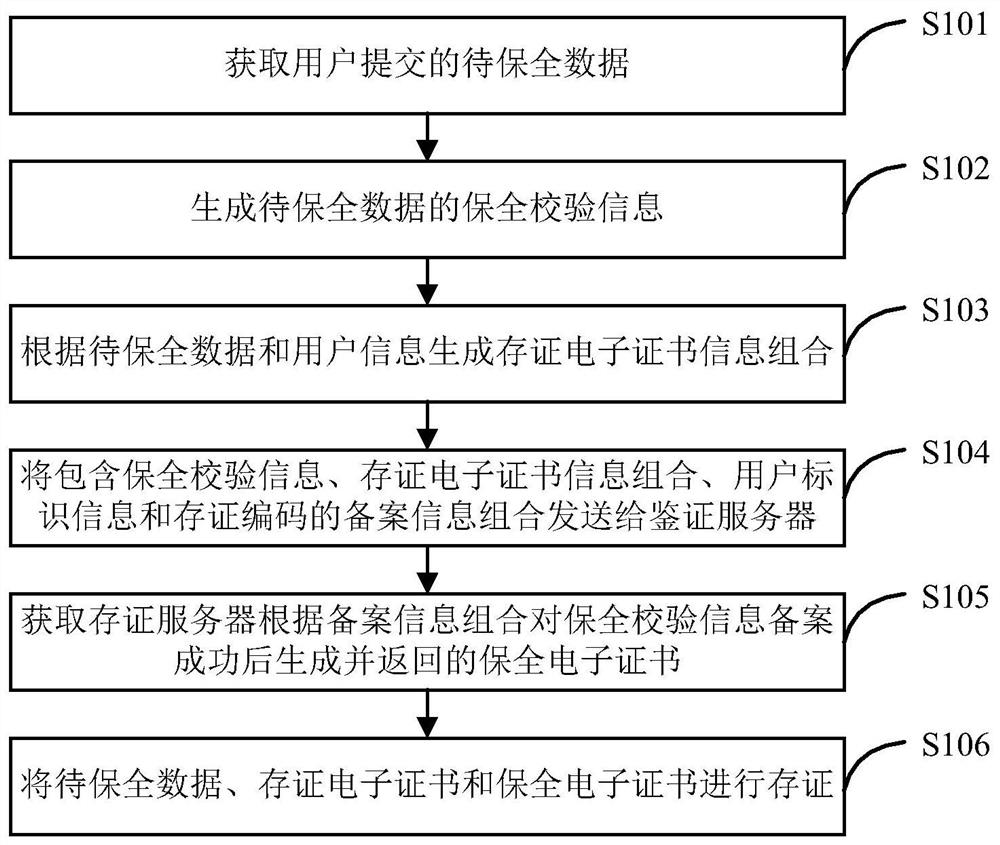
[0063] Embodiment 1 of the present invention provides an Internet data preservation method, the process of which is as follows figure 1 shown, including the following steps:
[0064] Step S101: Obtain the data to be preserved submitted by the user.
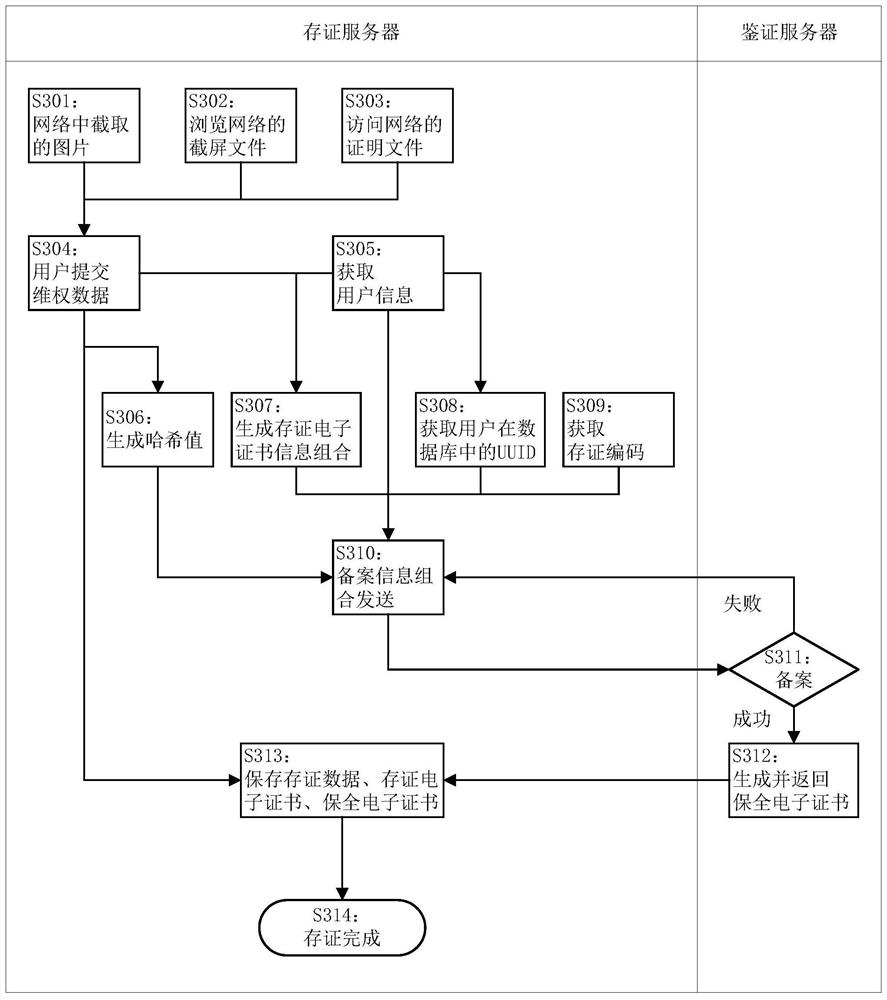
[0065] When users have data to be preserved, they can provide it to the certificate deposit server for certificate preservation. Users can upload their own electronic data with preservation needs to the certificate deposit server for certificate preservation, and they can also publish some data on the Internet, such as Infringement data that may infringe on one's own intellectual property rights is intercepted and uploaded to the certificate storage server for preservation and preservation for the purpose of rights protection.
[0066] Correspondingly, when the certificate storage server obtains the data to be preserved submitted by the user, it can obtain at least one file to be preserved submitted by the user or stored by itsel...
Embodiment 2
[0147] Embodiment 2 of the present invention provides a preserved data authentication method, which authenticates the electronic evidence preserved by the user, provides evidence legality proof for the user, and improves the usability and effectiveness of the electronic evidence. The process is as follows Figure 4 shown, including the following steps:
[0148] Step S401: Receive a user's authentication request for preserved data.
[0149] The certificate storage server receives the signed agreement file sent by the user; or the certificate deposit server receives the user's agreement signing request, provides the user with the agreement file for the user to sign, and obtains the signed agreement file uploaded by the user after signing online or offline.
[0150] In this step, when the user wants to authenticate the preserved data, he sends an authentication request to the certificate storage server. The user can directly sign the agreement file and send it to the certificate...
Embodiment 3
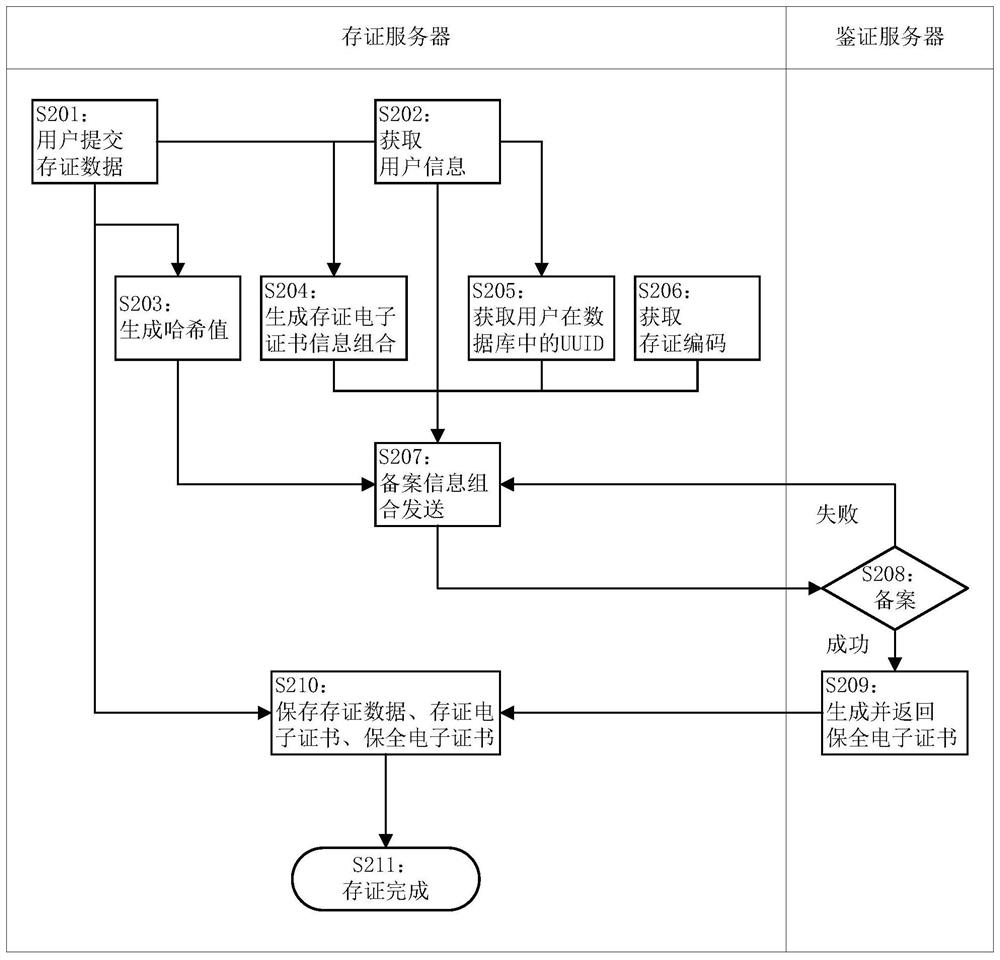
[0184] Based on the same inventive concept, Embodiment 3 of the present invention provides an Internet electronic data preservation system, the structure of which is as follows Figure 6 As shown, it includes: a client 601 , a certificate server 602 and an authentication server 603 .
[0185] The client 601 is used to submit the data to be preserved to the certificate server 602.
[0186] The deposit server 602 includes an Internet data preservation implementation device, which is used to obtain the data to be preserved submitted by the user, and generate the preservation verification information of the data to be preserved; generate a certificate electronic certificate information combination according to the data to be preserved and user information; The verification information, combination of stored electronic certificate information, user identification information and record information combination of stored certificate code are sent to the authentication server 603; Ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com