Digital key protection method based on Android system and system thereof
A digital key and protection system technology, which is applied to the public key and key distribution of secure communication, can solve the problem that the dex file is easily reversed into java code, the key is not safe to store statically, and the key is easy to be captured and intercepted, etc. problems, to achieve the effect of not being easy to intercept randomly, realizing protection and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
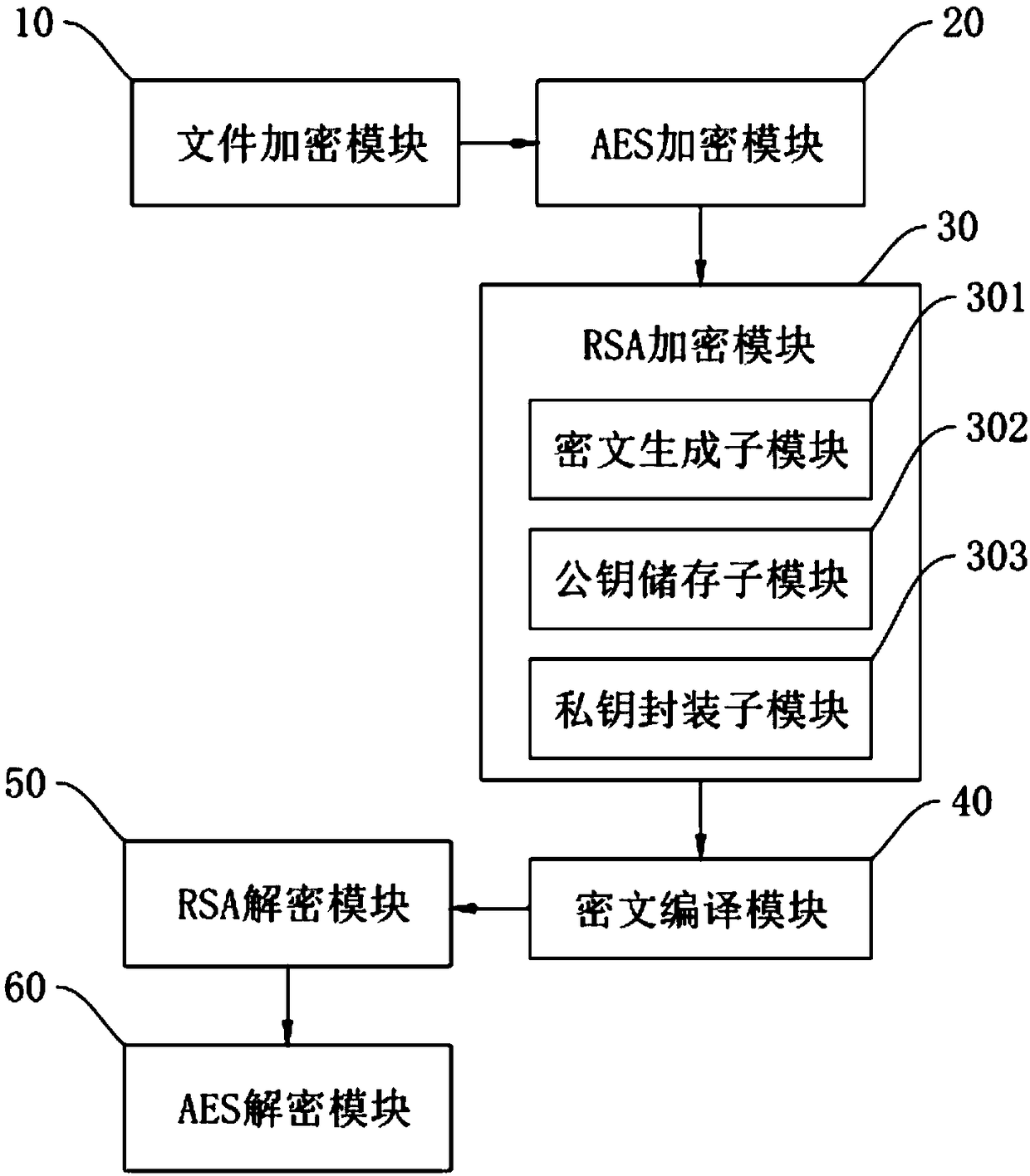
Image
Examples
Embodiment 1
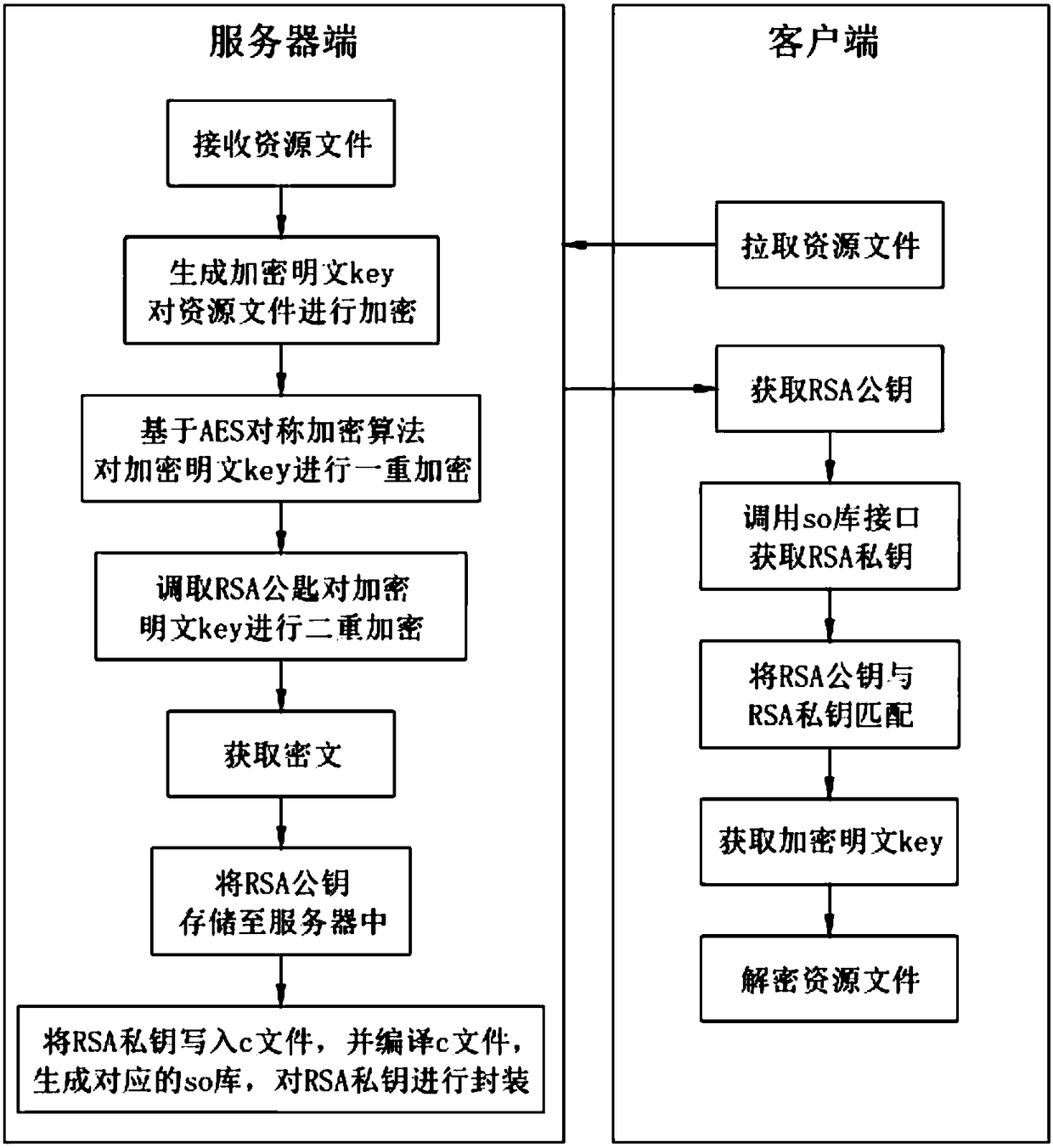
[0048] Such as figure 1 Shown, a kind of digital key protection method based on Android system comprises the following steps:
[0049] a. Receive the resource file, generate an encrypted plaintext key to encrypt the resource file;
[0050] b. Based on the AES symmetric encryption algorithm, the encrypted plaintext key is encrypted once;
[0051] c. According to the RSA asymmetric encryption algorithm, double-encrypt the encrypted plaintext key to obtain the ciphertext.
[0052] In this embodiment, AES symmetric encryption is used to encrypt and decrypt resource files; then RSA asymmetric encryption is used to encrypt and decrypt the encrypted plaintext key, which solves the problem of insecure key static storage in the android system, and solves the problem of In the android system, the key is easy to be captured and intercepted. At the same time, it also solves the problem that the dex file in the android system is easily reversed into java code, and the key is directly obt...
Embodiment 2
[0056] In this embodiment, on the basis of Embodiment 1, the step b includes the following steps:
[0057] b101. After obtaining the encrypted plaintext key, call the RSA public key, perform double encryption on the encrypted plaintext key, and obtain the ciphertext;
[0058] b102, storing the RSA public key used for decryption in the server;
[0059] b103. Write the RSA private key into the c file, compile the c file, generate the corresponding so library, and encapsulate the RSA private key.
[0060] In this embodiment, RSA asymmetric encryption is used to encrypt and decrypt the encrypted plaintext key, and the public key is stored in the server; while ensuring the integrity of the file, the security of the key is guaranteed to realize the protection of the digital key.
Embodiment 3
[0062] On the basis of embodiment 2, this embodiment also includes the following steps:
[0063] After the encryption is completed, if the decryption command is received, the so library interface is called to obtain the RSA private key;
[0064] If the RSA private key matches the RSA public key stored in the server, the decryption is successful and the encrypted plaintext key is obtained.
[0065] In this embodiment, the client uses RSA to decrypt locally, uses the ndk development tool to encapsulate the key in the so file, the matching is successful, and the link to the resource file is obtained; ensuring that the file is secure enough to prevent it from being randomly intercepted.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap