A two-dimensional code authentication method, device and computer-readable storage medium
An authentication method and two-dimensional code technology, applied in the field of computer-readable storage media, two-dimensional code authentication methods, and devices, can solve the problem of relying on the security model of the two-dimensional code virus database, unable to prove the source of the two-dimensional code, and unable to guarantee security, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
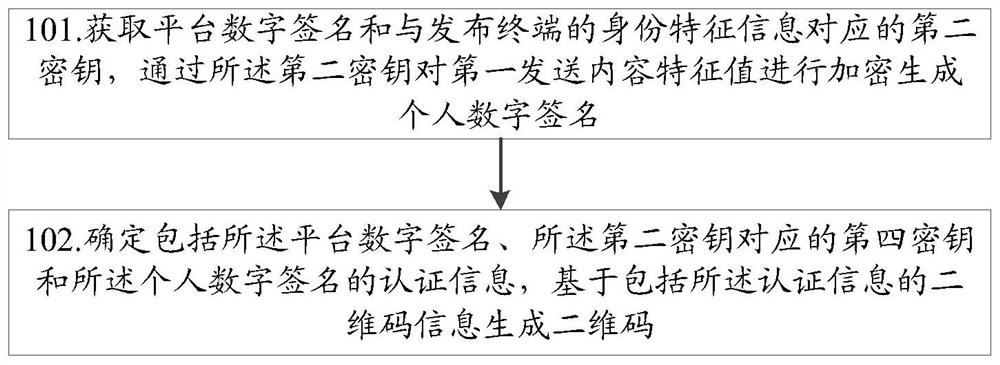
[0103] An embodiment of the present invention provides a two-dimensional code authentication method, such as figure 1 As shown, the method includes:
[0104] S101. Obtain a platform digital signature and a second key corresponding to the identity feature information of the issuing terminal, and use the second key to encrypt the first sent content feature value to generate a personal digital signature;
[0105] The platform digital signature is obtained by encrypting the platform identification information with the first key;
[0106] Obtaining the platform digital signature and the second key corresponding to the identity feature information of the issuing terminal includes: sending the first communication identification representing the identity feature of the issuing terminal to the authentication platform; receiving the corresponding first communication key sent by the authentication platform; An identified digital certificate and a second key, the digital certificate carr...
Embodiment 2
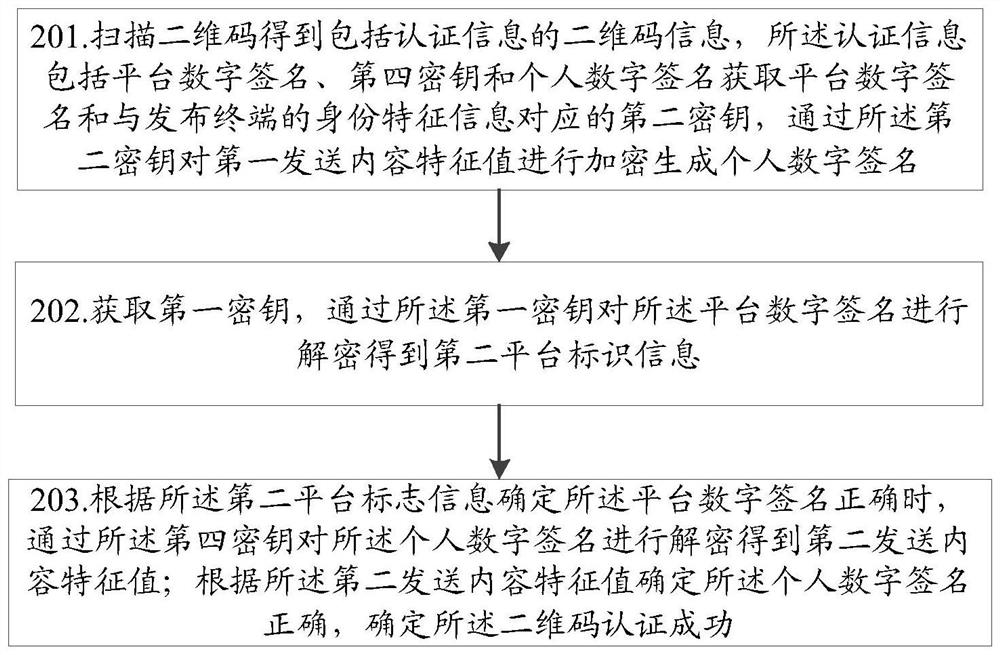
[0126] An embodiment of the present invention provides a two-dimensional code authentication method, such as figure 2 shown, including:
[0127] S201. Scan the QR code to obtain QR code information including authentication information, where the authentication information includes a platform digital signature, a fourth key, and a personal digital signature;
[0128] Here, the fourth key corresponds to the identity feature information of the issuing terminal.
[0129] After the scanning terminal scans the two-dimensional code issued by the issuing terminal, information about the two-dimensional code is obtained, wherein the information may be unencrypted two-dimensional code information or encrypted two-dimensional code information.
[0130] When the information is encrypted two-dimensional code information, the key for encrypting the two-dimensional code information is the third key corresponding to the identity feature information of the scanning terminal, and the key for d...
Embodiment 3
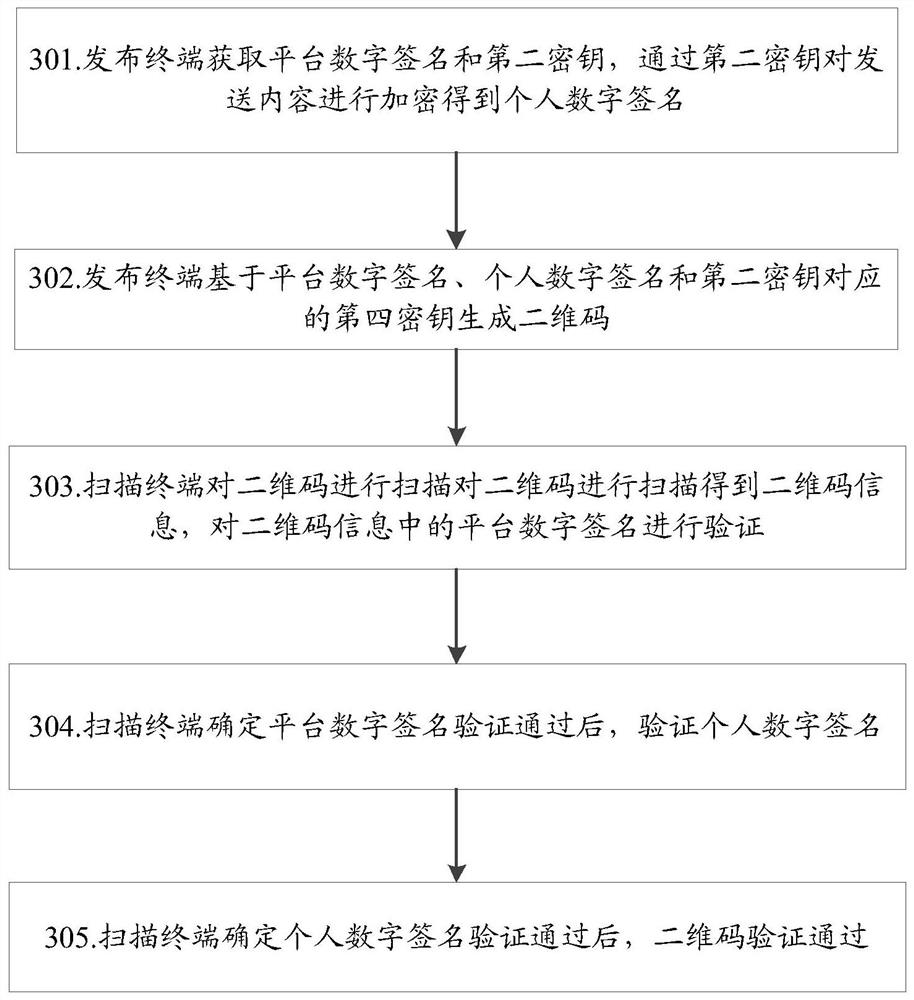
[0154] The embodiment of the present invention provides a two-dimensional code authentication method, wherein, in the embodiment of the present invention, the complete process of generating and identifying a two-dimensional code is used as a specific application scenario for the two-dimensional code authentication method in the embodiment of the present invention Be explained. Here, the issuing terminal that generates the two-dimensional code and the scanning terminal that recognizes the two-dimensional code are pre-installed with a client that interacts with the authentication platform, so as to obtain the communication identification based on the issuing terminal or scanning terminal through interaction with the authentication platform The key is used to generate or identify the two-dimensional code, and the root certificate of the authentication platform is installed, that is, the first key to decrypt the digital signature of the platform, so as to authenticate the digital s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com