Firewall configuration method based on service access data
A service access and configuration method technology, applied in the field of firewall configuration based on service access data, can solve problems such as difficult maintenance, large investment, and complicated firewall rules, and achieve the effects of accurate data, improved configuration time, and convenient operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
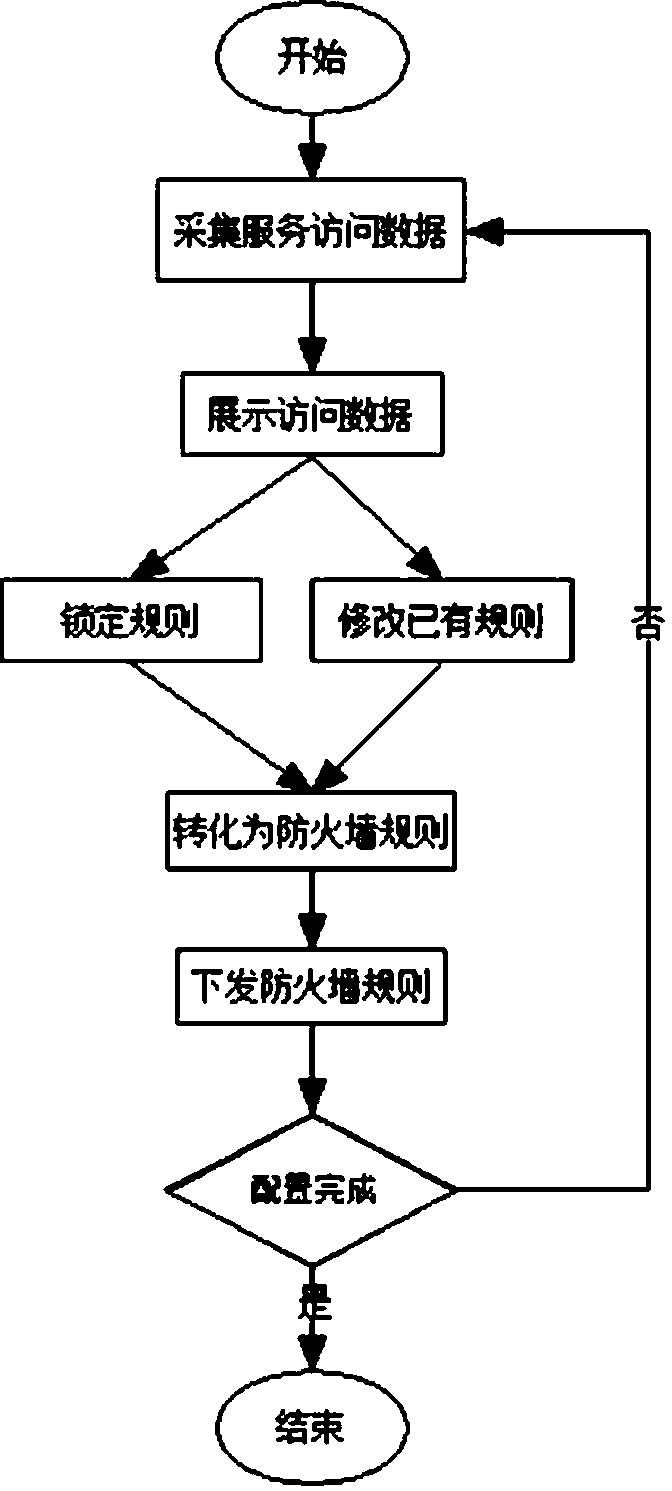
[0024] As a most basic embodiment of the present invention, such as figure 1 , this embodiment discloses a firewall configuration method based on service access data, including a data collection step, an access rule locking step, and a firewall rule generation step;
[0025] The data collection step collects and extracts service access data including source IP, source port, destination IP, destination port, application and protocol in a plurality of network paths through network monitoring bypass mode, and collects and extracts service access data according to source IP, source port, Classify the type of destination IP, destination port and protocol, and create a table or graph;
[0026] In the access rule locking step, the normal service access data in the service access data collected for the first time in the collection step is locked into access rule data, and the service access data collected each time in the collection step is compared with the previous service access da...
Embodiment 2
[0030] As a preferred embodiment of the present invention, such as figure 1 , this embodiment discloses a firewall configuration method based on service access data, including a data collection step, an access rule locking step, and a firewall rule generation step;
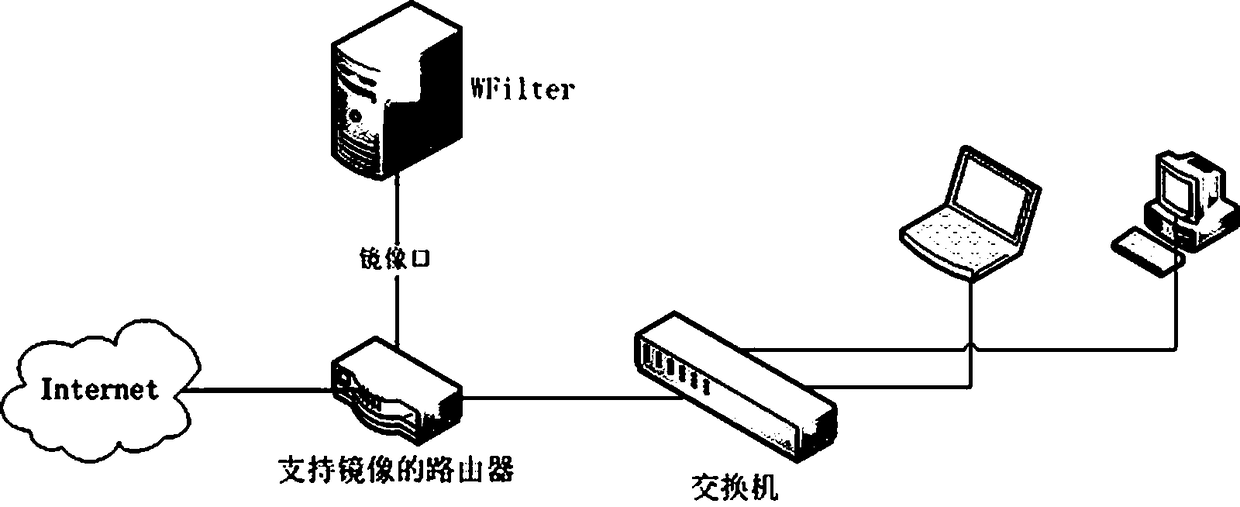
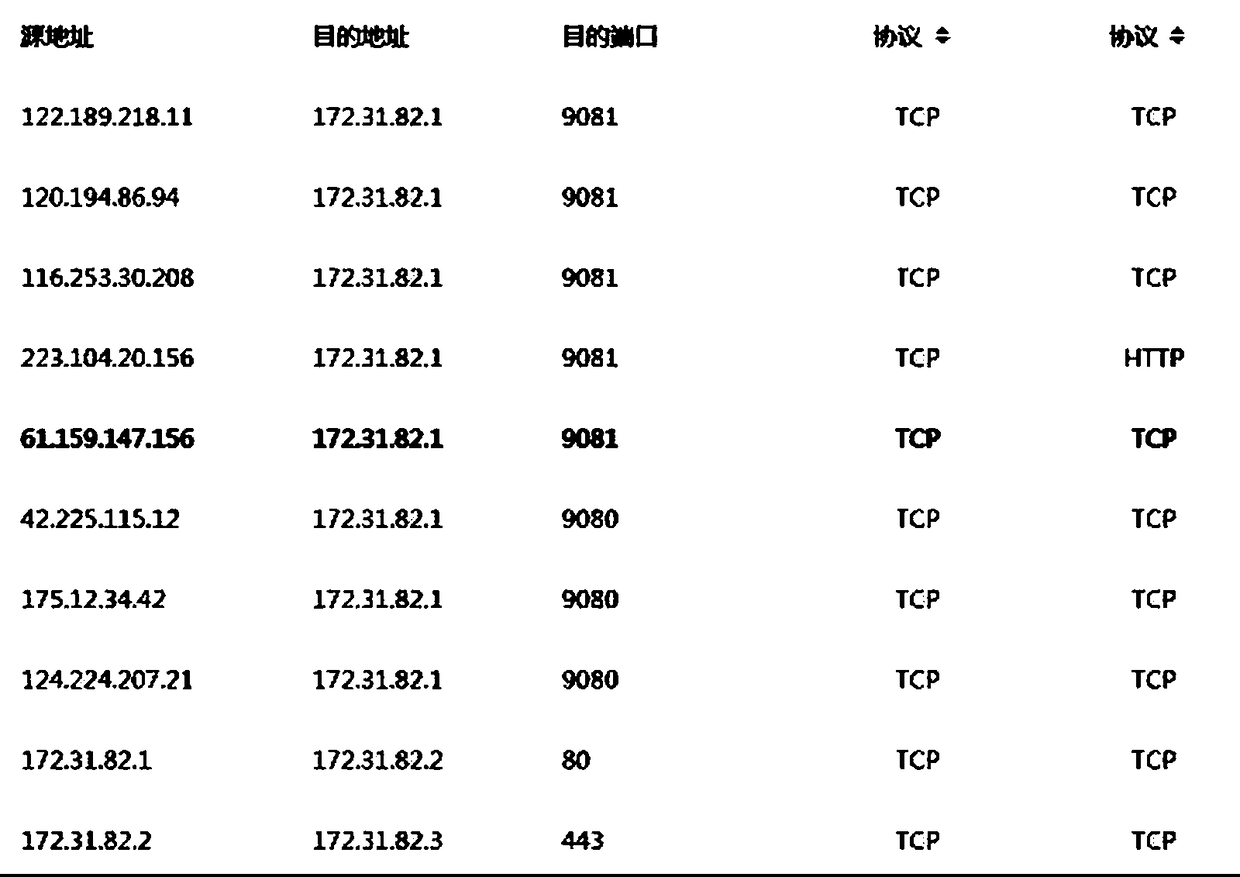
[0031] The data collection steps, such as figure 2 , the network traffic is mirrored through the switch mirroring function without affecting the normal business operation, the data of a single or multiple switches is mirrored and connected to the data collection port of the collection server, and through the analysis of the traffic data and identification of the application and protocol, all The above service access data, and extract the service access data including source IP, source port, destination IP, destination port, application and protocol in multiple network paths, such as image 3 , and classify according to the source IP, source port, destination IP, destination port and protocol type, and create a t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com