A data forwarding control method and system based on hardware control logic
A technology of hardware control and control method, applied in the direction of transmission system, digital data authentication, electronic digital data processing, etc., can solve problems such as lack of data flow control and security protection, system misoperation, host compatibility issues, etc., to achieve Solve the effect of virus Trojan implantation and malicious code injection, reduce network security risks, and achieve physical isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
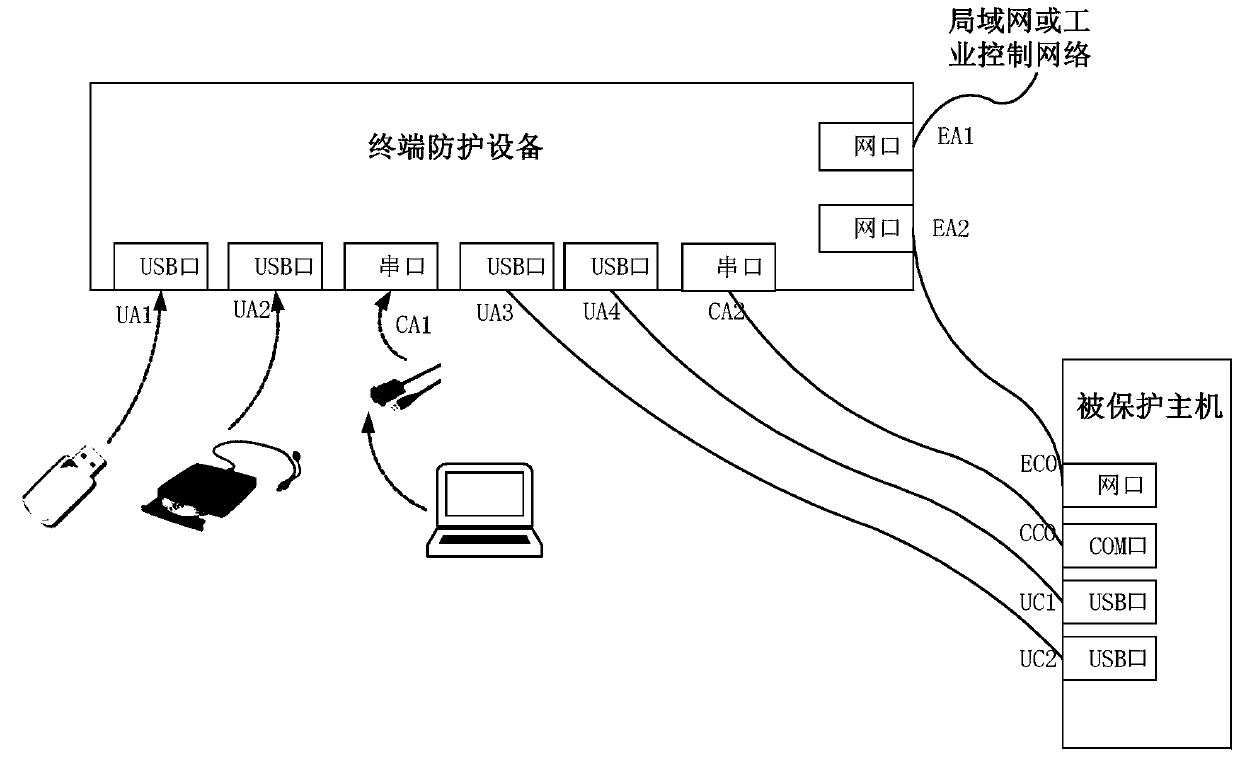
[0035] figure 1 Shown is an application scenario of an application scenario for a data forwarding control system related to the present invention.
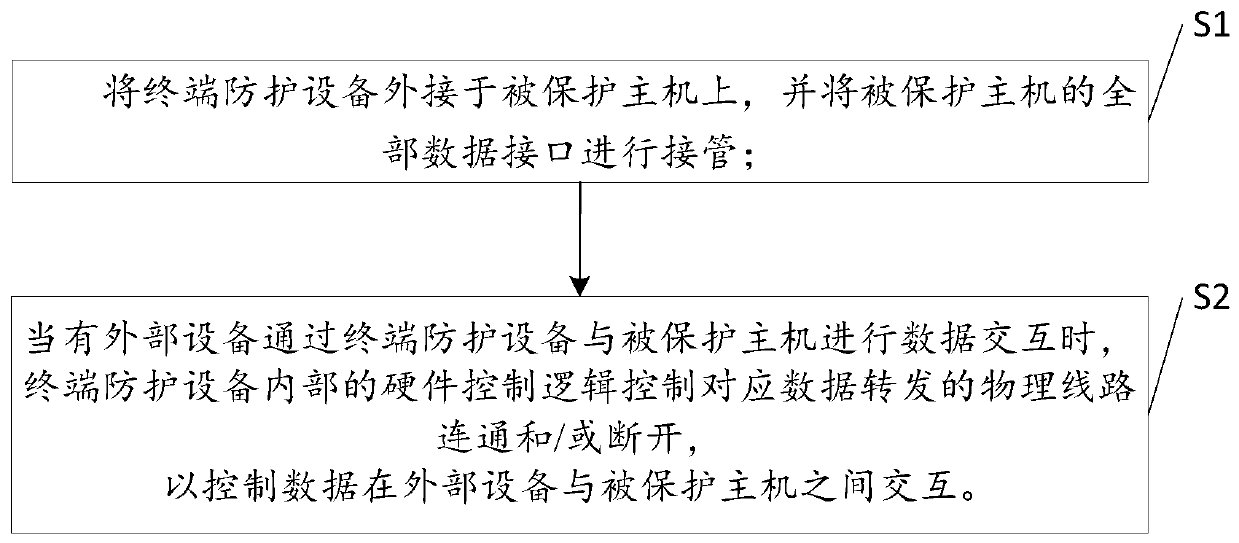
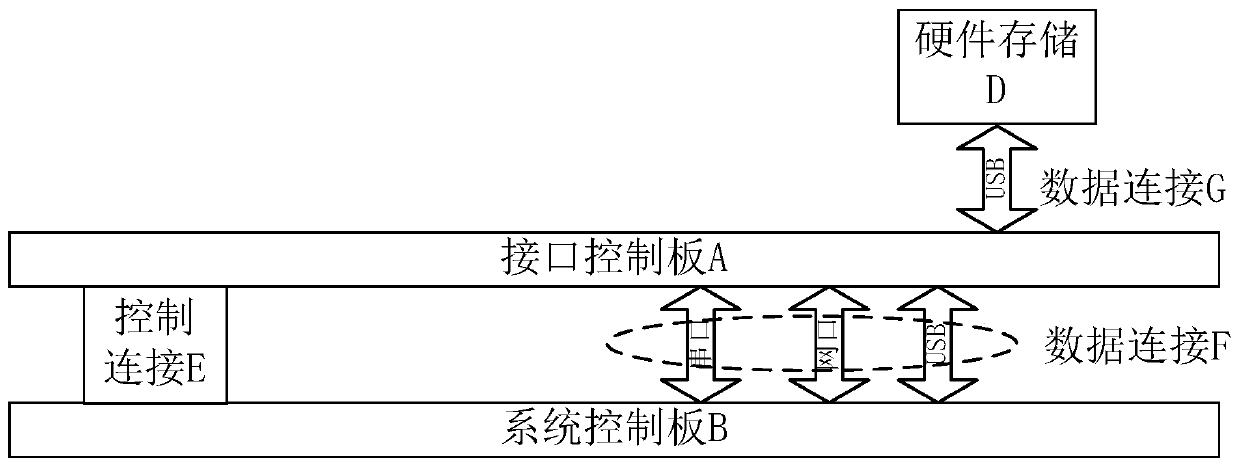
[0036] Such as figure 1 As shown, in order to control each data forwarding of the protected host, it is necessary to take over each interface of the protected host. Therefore, the method proposed by the present invention sets internal At the same time, it also provides corresponding external interfaces. Each internal interface is used to connect to the protected host, and the external interface is used to connect external devices that need to exchange data with the protected host. The terminal protection device is externally connected to the protected host, and each interface (such as UC1 and UC2 of the USB port, CC0 of the COM port, and EC0 of the network port) on the protected host that needs to be protected is connected to itself through various types of connecting wires. Corresponding types of internal interfaces, for exampl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com