Method, intermediate device, server and system for transmission protection of URL request
An intermediate device and server technology, applied in the field of network security, to achieve the effect of increasing attack difficulty and complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
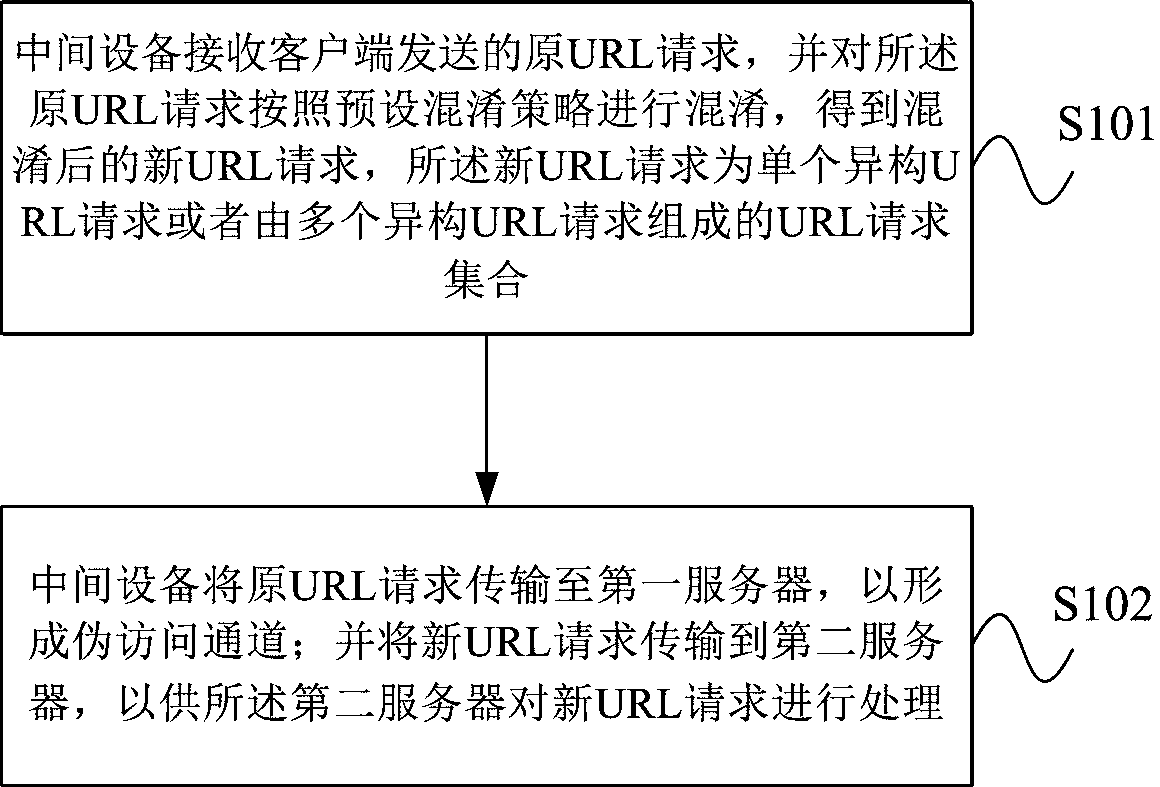
[0047] figure 1 It is a schematic flowchart of a URL request transmission protection method provided by an embodiment of the present invention. Such as figure 1 As shown, the method includes the following steps:
[0048] S101. The intermediate device receives the original URL request sent by the client, and obfuscates the original URL request according to a preset obfuscation strategy to obtain an obfuscated new URL request, and the new URL request is a single heterogeneous URL request or multiple A set of URL requests composed of heterogeneous URL requests;
[0049] S102. The intermediate device transmits the original URL request to the first server to form a fake access channel; and transmits the new URL request to the second server for the second server to process the new URL request.
[0050] Specifically, the first server and the second server are isomorphic, and the difference between the two is that the first server does not have the functions of identification, reco...
Embodiment 2
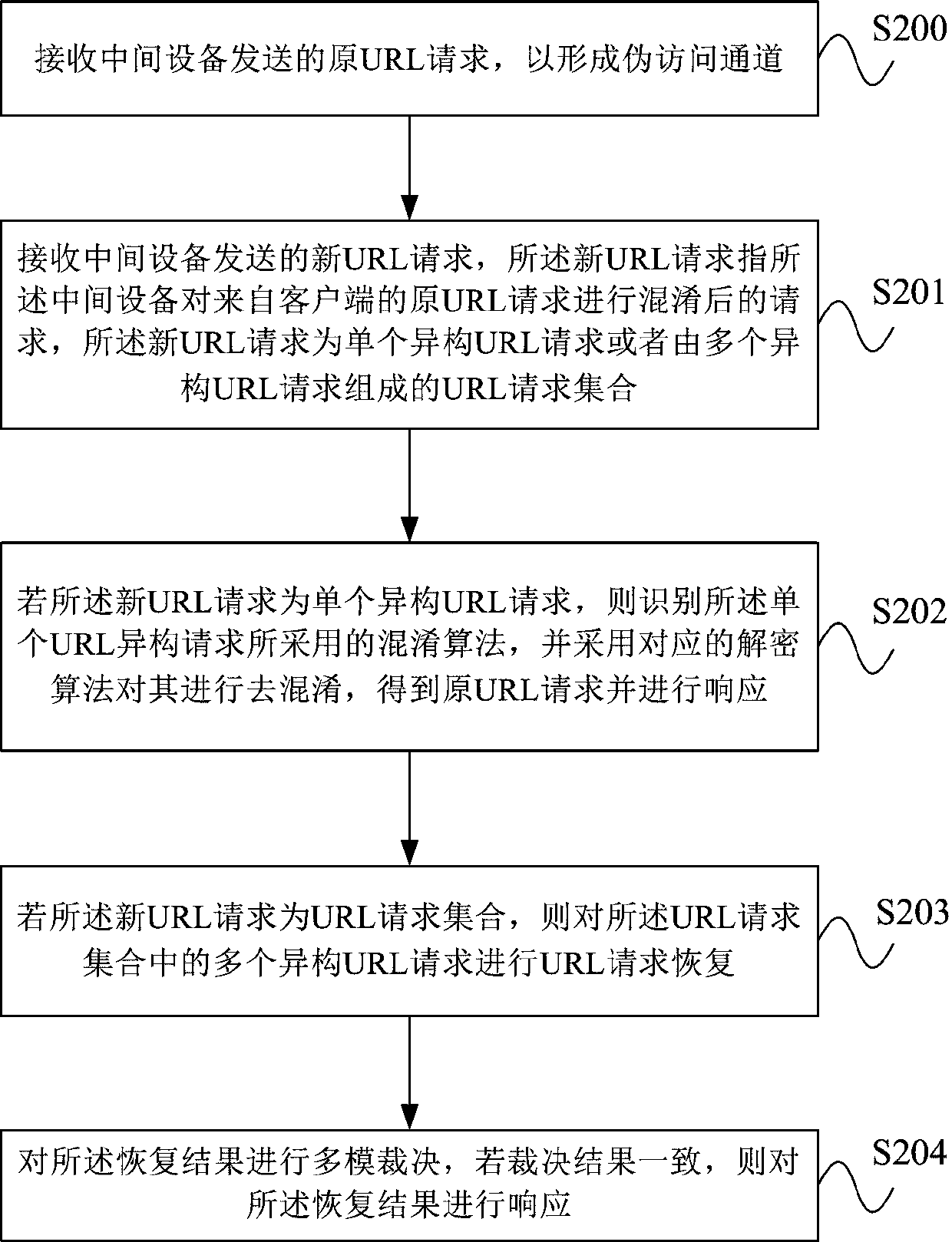
[0053] On the basis of the first embodiment above, the preset obfuscation strategy includes: determining the obfuscation control component to be used; selecting at least one obfuscation algorithm to be used through the obfuscation control component; using the at least one obfuscation algorithm to The new URL request is obfuscated.
[0054] Specifically, the user edits the URL request on the client, and the client sends the user's original URL request to the intermediate device. After receiving the original URL request, the intermediate device dynamically selects one or more obfuscation control components, and each obfuscation control Each component contains a variety of different obfuscation algorithms, and the obfuscation functions implemented by different obfuscation control components are also different. The intermediate device selects at least one internal obfuscation algorithm to obfuscate the user URL request through the obfuscation control component, so as to obtain het...
Embodiment 3
[0058] On the basis of Embodiment 1 or Embodiment 2 above, the method further includes: the intermediate device receives the response of resending the new URL request fed back by the second server, and resends the new URL request to the second server according to the response.
[0059] It can be seen from the first to third embodiments above that the URL request transmission protection method provided by the embodiment of the present invention has the following advantages: (1) Combined with dynamic thinking, one or more obfuscation control components are dynamically selected to realize corresponding URL heterogeneity Effect. The dynamics of control component selection increases the uncertainty of URL request transmission factors and increases the attack difficulty for attackers. (2) Using heterogeneous ideas to confuse user URLs, increasing the difficulty for attackers to identify user URL requests. (3) The intermediate device increases the complexity of the user URL request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com