An image encryption method and a terminal
An image and terminal technology, applied in the computer field, can solve the problems of poor randomness, removal of image correlation, correlation, redundancy and large amount of data, etc., and achieve the effect of high randomness and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
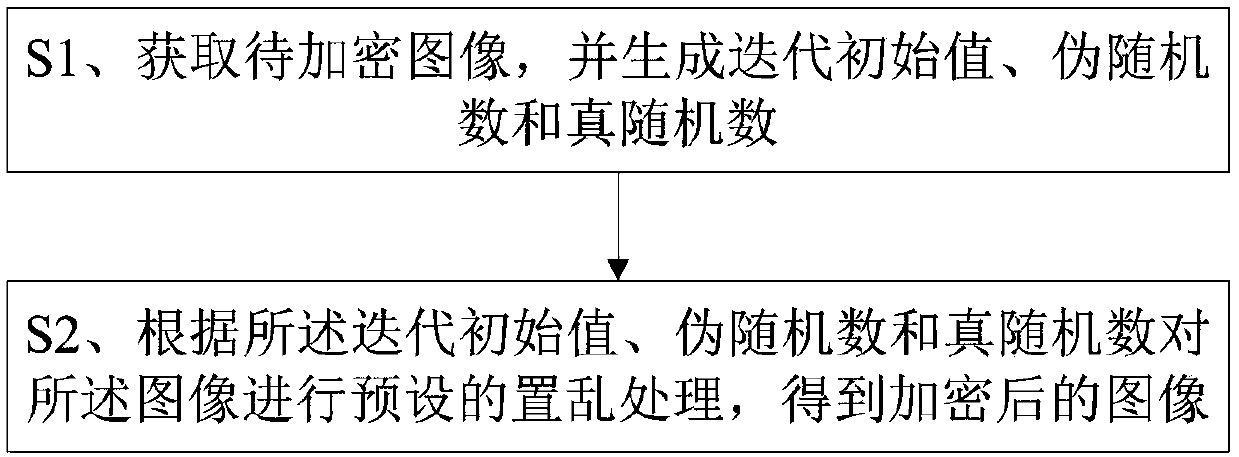
[0071] Please refer to figure 1 , a method for image encryption, comprising steps:
[0072] S1. Obtain the image to be encrypted, and generate an iterative initial value, a pseudo-random number and a true random number;
[0073] The generation iteration initial value described in step S1 is specifically:
[0074] S11. Obtain the image to be encrypted and the preset initial secret key;
[0075] S12. Generate an iterative initial value according to the image to be encrypted and the initial key;
[0076] The generation of pseudo-random numbers and true random numbers described in step S1 is specifically:
[0077] Generate pseudo-random numbers through two-dimensional Logistic mapping, and generate true random numbers according to the pseudo-random numbers and preset rules;
[0078] The generating of true random numbers according to the pseudo-random numbers and preset rules is specifically:
[0079] converting the pseudo-random number into a binary form, and dividing the pse...
Embodiment 2
[0086] This embodiment will further illustrate how the above image encryption method is implemented in combination with specific application scenarios:
[0087] 1. Obtain the image to be encrypted, and generate the iteration initial value, pseudo-random number and true random number
[0088] 1.1. Obtain the image to be encrypted and the preset initial key (x 0 ,y 0 ), the size of the grayscale image of the image to be encrypted is M×N as an example;
[0089] 1.2. Calculate the initial value of iteration according to the initial secret key as follows:
[0090]
[0091]
[0092]
[0093]
[0094] Where P(i,j) represents the gray value of row i and column j, (x 0 ,y 0 ) represents the given initial key, (x 0 1 ,y 0 1 ) is the initial value of the iterative row scrambling, (x 0 2 ,y 0 2 ) is the iterative initial value of column scrambling, and mod represents the remainder operation;
[0095] 1.3. Two-dimensional Logistic mapping
[0096] The formula of t...
Embodiment 3
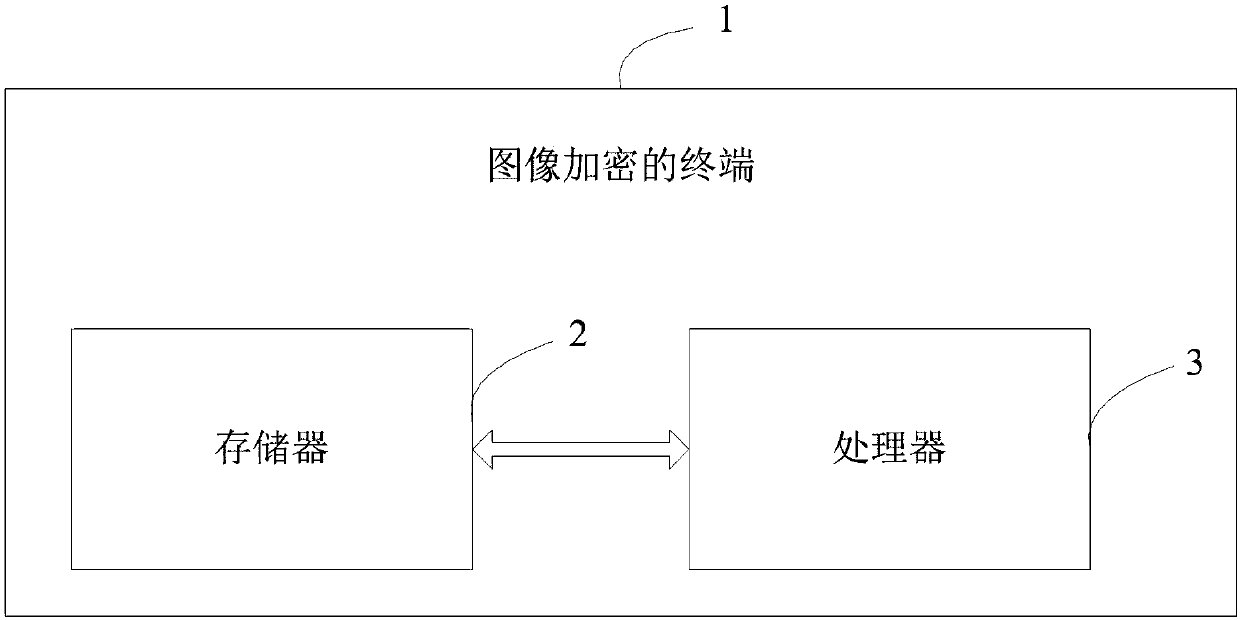
[0161] Please refer to figure 2 , an image encryption terminal 1, including a memory 2, a processor 3, and a computer program stored in the memory 2 and operable on the processor 3, when the processor 3 executes the program, implements the first embodiment various steps.
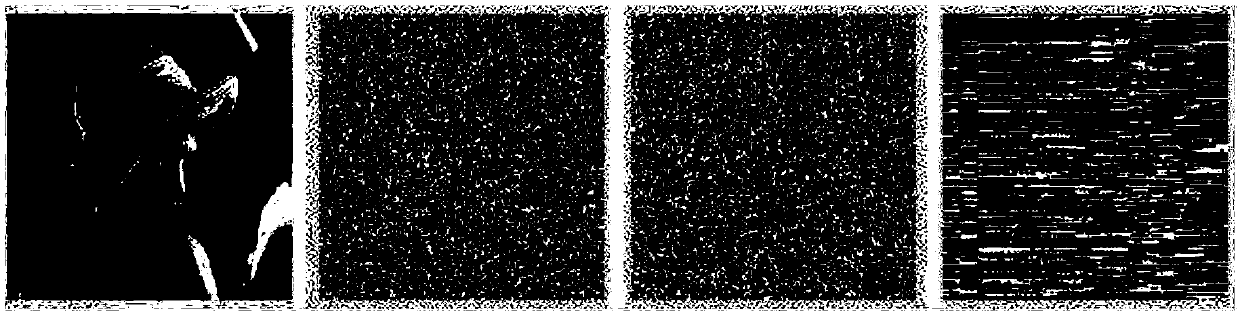
[0162] To sum up, the method and terminal for image encryption provided by the present invention acquire an image to be encrypted and generate an iterative initial value, a pseudo-random number, and a true random number. The random number performs preset scrambling processing on the image to obtain the encrypted image, and uses the combination of true random number and pseudo-random number to effectively remove the correlation between images and make the encrypted image more random , through the preset scrambling process, the encrypted image can resist plaintext attacks, and the security is higher. The first bit stream is obtained by converting the pseudo-random number into binary form and dividing the pse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com