Real-time secure network system based on dual-engine forwarding
A secure network and security technology, applied in the field of network security, can solve problems such as complementary interference without interaction and inability to isolate a physical network, and achieve the effect of ultra-high security and superior performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
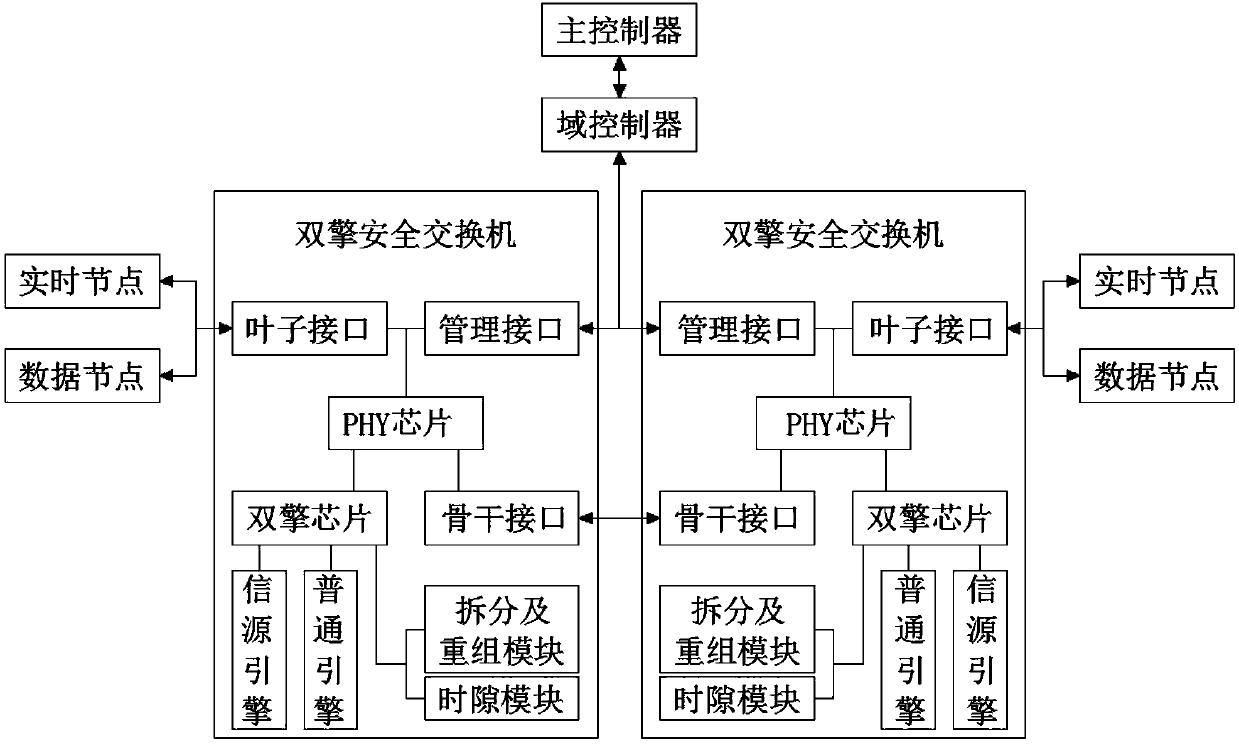
[0036] This embodiment provides a real-time security network system based on dual-engine forwarding, such as figure 1 shown.
[0037] A real-time security network system based on dual-engine forwarding, including a dual-engine security switch, the dual-engine security switch is connected to a real-time node and a data node respectively, the dual-engine security switch includes a PHY chip, and the PHY chip is respectively connected to a leaf interface, a dual engine chip and backbone interface; the dual-engine chip includes a source engine and a common engine, the real-time node is provided with a real-time node control chip, and the dual-engine security switch adopts a cell transmission mode, and the real-time node is embedded in the operating machine Or directly connected with the machine, in order to achieve higher real-time performance; the data node is a kind of data communication equipment or device, connected to the common data network and IT network, and the common node...
Embodiment 2
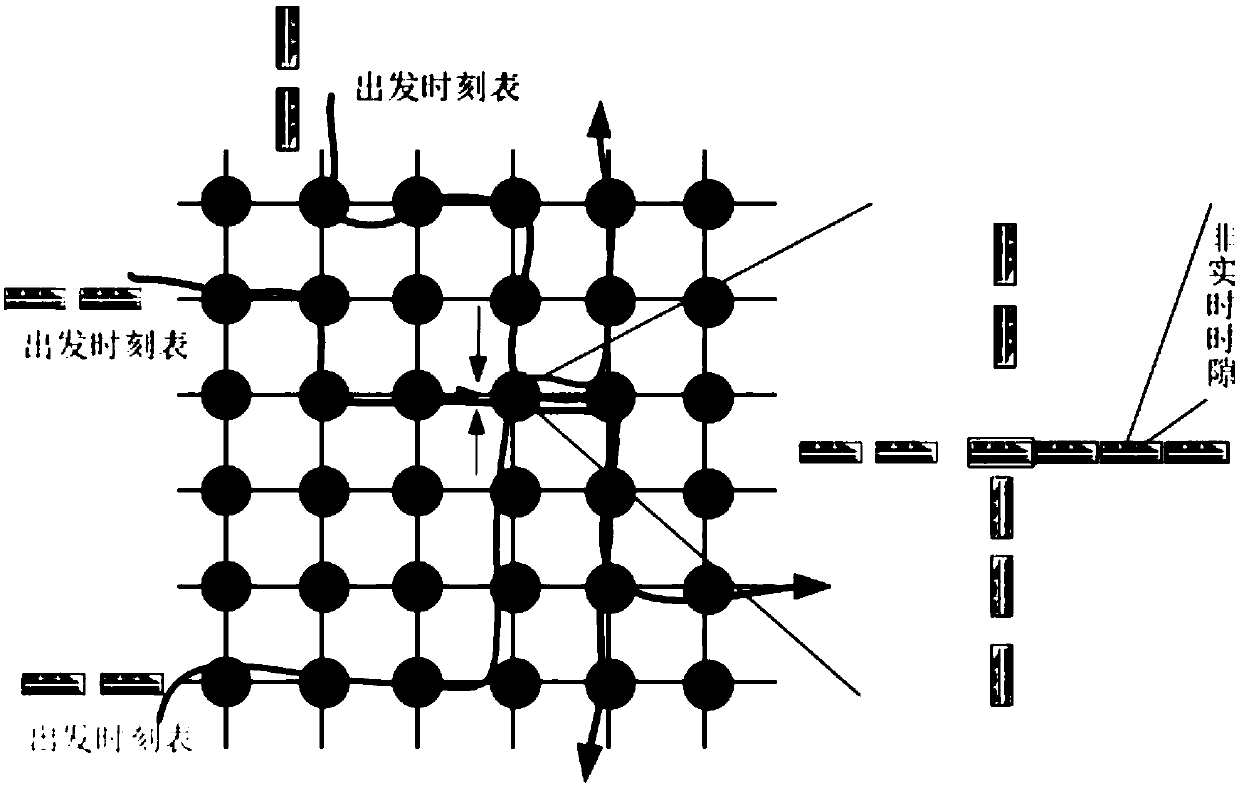
[0062]This embodiment discloses a non-blocking transmission based on a train timetable applying the present invention, such as figure 2 shown.
[0063] figure 2 It is a schematic diagram of non-blocking transmission based on a train timetable. The present invention has a time trigger at a real-time node, which is analogous to a train departure timetable. The domain controller passes the backbone interface to the backbone interface; the real-time node to the leaf interface performs time measurement, and the forwarding delay is fixed, so the domain controller forwards all real-time streams to the time slots of the incoming and outgoing time slots into cloud computing based on the SDX idea , and then through each interface issued by the domain controller and the real-time node. Cloud computing based on the SDX idea will realize zero-delay non-blocking forwarding in the exit direction of each node, which is very similar to the case where a series of high-speed trains pass thro...
Embodiment 3
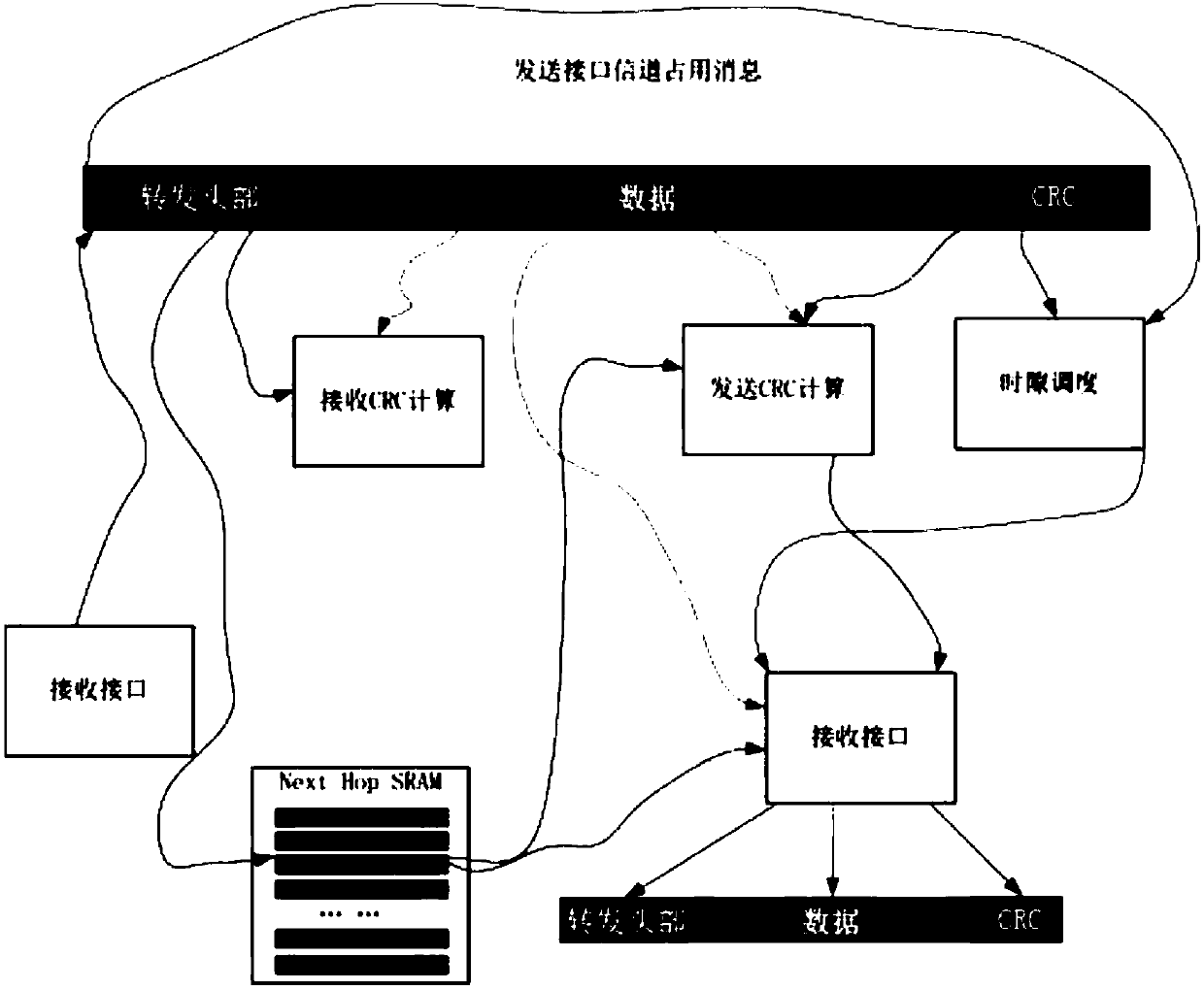
[0065] This embodiment discloses a PHY design based on the shoot-through low-latency design of the present invention. The core PHY design is based on the low-latency design of the shoot-through. After the data received by the PHY is directly encrypted and decrypted through the FIFO memory, it is directly sent to the serial deserializer. The ultra-low-latency circuit design makes the delay possible. Reach <50ns, and the serial deserializer also adopts ultra-low delay circuit design, so that the delay is also <50ns
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com