Event-aware Android malicious software detection method
A technology of malware and detection method, applied in the field of event-aware Android malware detection and malware detection, can solve the problems of indistinguishable, difficult to detect, unable to extract effective semantic information, etc., and achieve the effect of robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Below in conjunction with accompanying drawing and specific embodiment the present invention will be described in further detail:
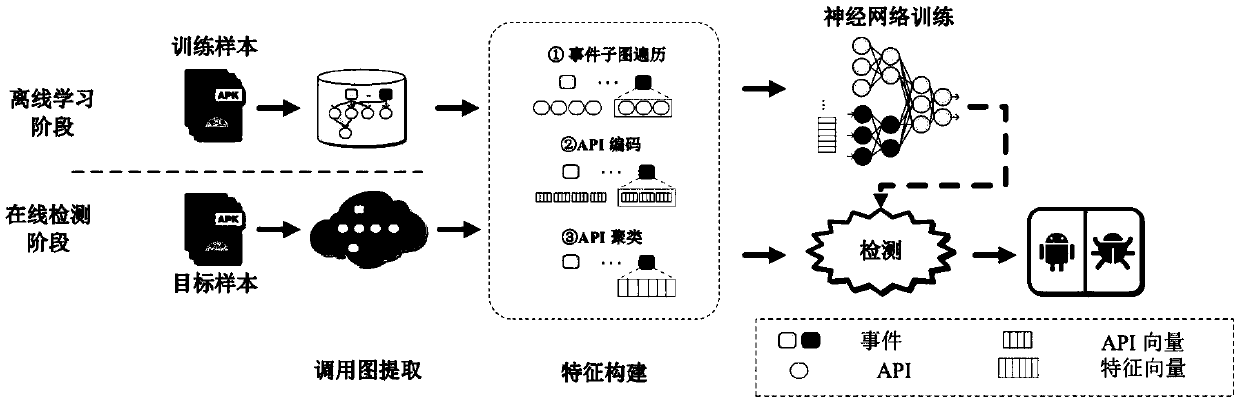
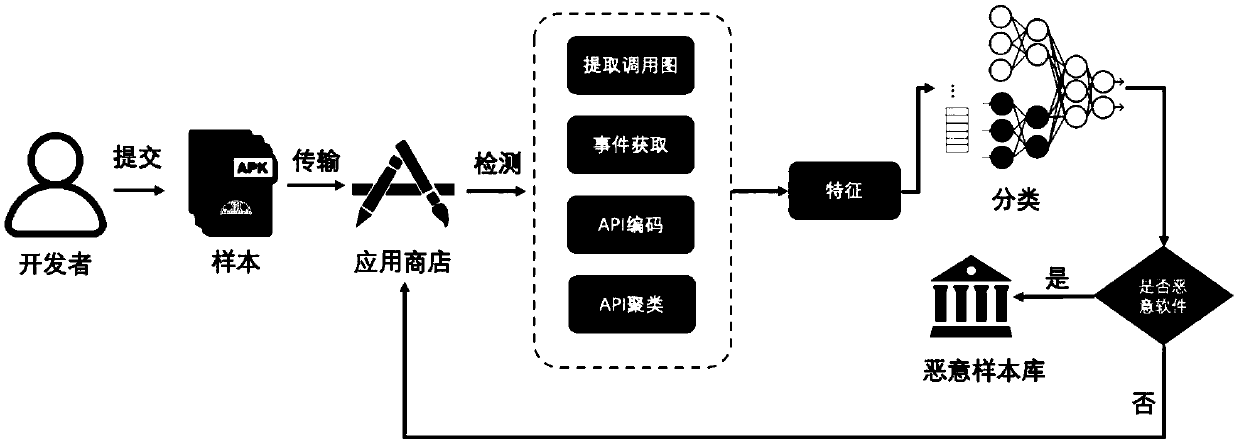
[0052] The invention belongs to the field of software security. Considering that when the Android system is updated, there will be API updates and the characteristics of malicious software hiding malicious behavior in various events, an event-aware Android malware detection method is proposed, which is automatically analyzed from the event level. Android software behaviors are used to detect hidden behaviors, and at the same time, converting behaviors in events into API function groups can resist the evolution of malware. The invention can enhance the capability of resisting the degradation of the performance of the detection model caused by the update of the Android system and the evolution of malicious software.
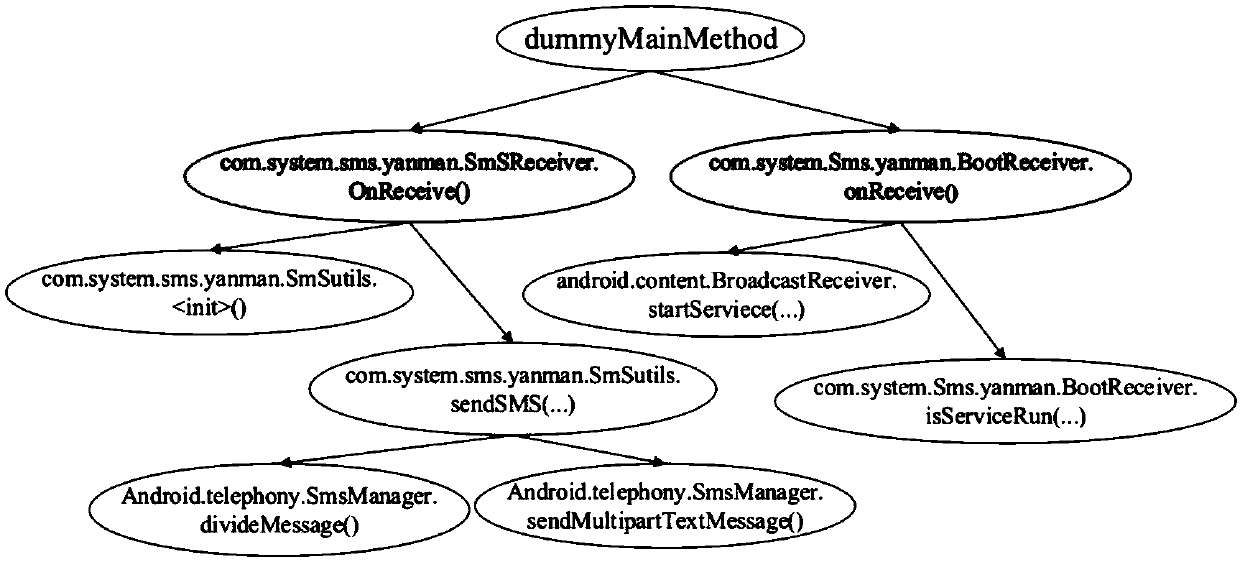
[0053] The method provided by the invention can use computer software technology to realize the process. see figure 2 , an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com