Sensitive information protection method and device and a readable storage medium
A sensitive information, hash algorithm technology, applied in the field of information security, can solve problems such as side channel attacks, key tampering, information leakage, etc., and achieve the effect of improving the success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
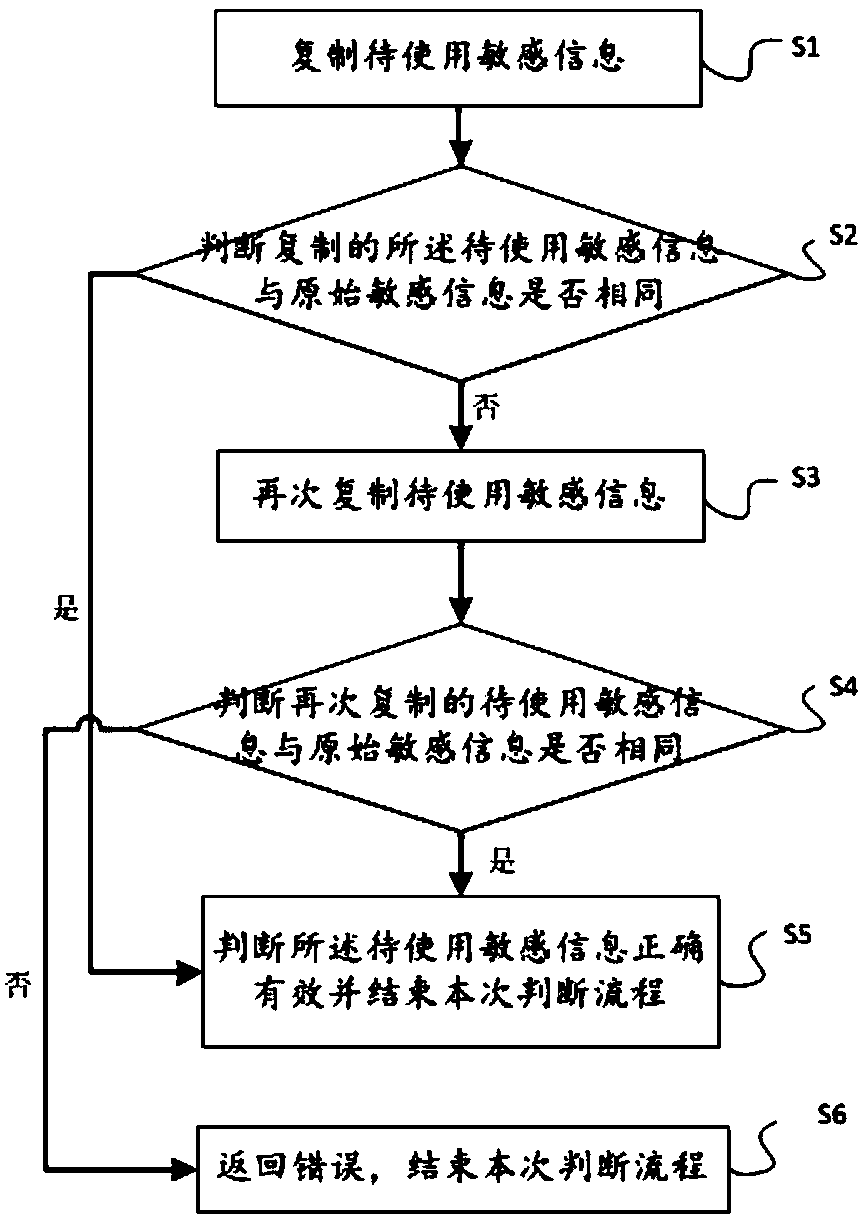
[0040] Please refer to figure 1 , a sensitive information protection method. Before the sensitive information is used, the original sensitive information has been stored in the security chip. When the sensitive information is used, it is checked whether the sensitive information to be used is correct and valid according to the following judgment process:
[0041] S1: copy the sensitive information to be used, and copy the sensitive information to be used from the data source address to the target address;
[0042] S2: Determine whether the copied sensitive information to be used is the same as the original sensitive information: if they are the same, that is, the sensitive information to be used has been securely copied, then jump to step S5;
[0043] S3: Copy the sensitive information to be used again; if the copied sensitive information to be used is different from the original sensitive information, it is considered that the sensitive information copying process may be subj...
Embodiment 2
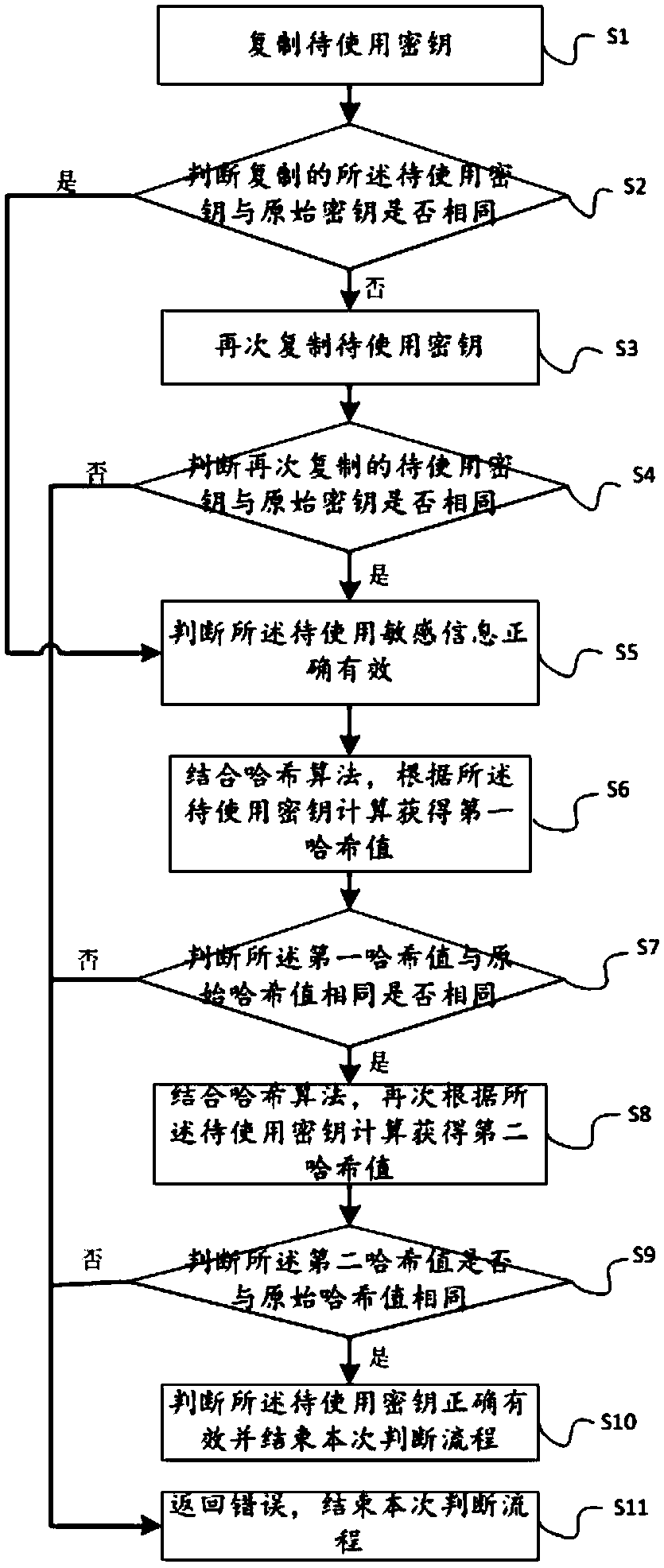
[0053] Please refer to figure 2 , which is a protection method for sensitive information as a key. Before the key is used, the original key and the original hash value have been stored in the security chip. When using the key, check whether the key to be used is correct and valid according to the following judgment process:
[0054] S1: Copy the key to be used, and copy the key to be used from the data source address to the target address;
[0055]S2: Determine whether the copied key to be used is the same as the original key: if they are the same, that is, the key to be used has been securely copied, then jump to step S5;
[0056] S3: Copy the key to be used again; if the copied key to be used is different from the original key, it is considered that the key copying process may be subjected to a side-channel attack, and the key to be used at the target address is untrusted Data, therefore, by providing the opportunity to copy the key to be used again to reconfirm the corre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com