Flow attack defense system based on SDN cloud security function service tree model
A technology of security functions and defense systems, applied in the network field, to solve problems such as insufficient security guarantees for interactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
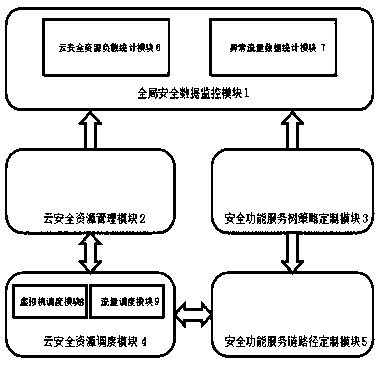
[0021] Such as figure 1 As shown, a traffic attack defense system based on the SDN cloud security function service tree model, including cloud security resource management module 2, cloud security resource scheduling module 4, security function service tree policy customization module 3, security function service chain path customization module 5 and the global security data monitoring module 1;
[0022] According to the user's own security requirements for the current network situation, by calling the security function service chain path customization module 5 and the security function service tree policy customization module 3, the user completes the customization of the cloud security service tree model that meets his own security requirements, and then the system calls the update The underlying cloud security resource management module 2 and cloud security resource scheduling module 4 complete the deployment and scheduling of the underlying virtual machines of the system, ...
Embodiment 2
[0024] In this embodiment, the cloud security resource management module 2 uses KVM technology in the cloud environment to realize the virtualization of general server computing resources to generate a virtual machine resource pool, and uses NFV technology to integrate firewalls, load balancers, deep packet analysis, Various types of network security functions such as intrusion detection / defense and coarse-grained attack detection run on a general-purpose VM, and various security functions implemented on a general-purpose VM can be freely combined and matched according to user needs, thereby achieving flexible Security function service chain orchestration policy.
[0025] As a preferred embodiment, the cloud security resource scheduling module 4 includes a virtual machine scheduling module 8 and a traffic scheduling module 9, and the virtual machine scheduling module 8 implements deployment and scheduling of VMs across data centers, and solves Hot migration problem; the traffi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com