Malicious domain name detection method based on SMOTE and BI-LSTM network
A domain name detection and domain name technology, applied in the field of network security, can solve the problems of passive defense, domain name detection difficulty, low efficiency, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0065] The present invention provides a kind of malicious domain name detection method based on SMOTE and BI-LSTM, comprises the following steps:
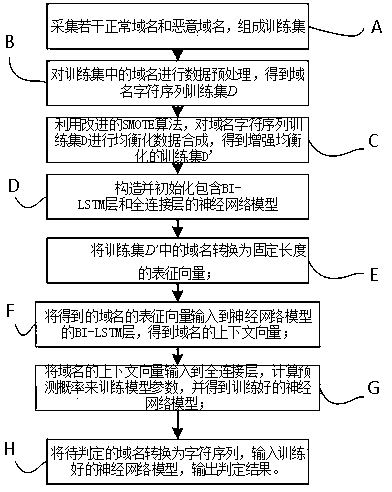
[0066] Step A: Collect several normal domain names and malicious domain names to form a training set;
[0067] Step B: Carry out data preprocessing to the domain name in training set, obtain domain name character sequence training set D;
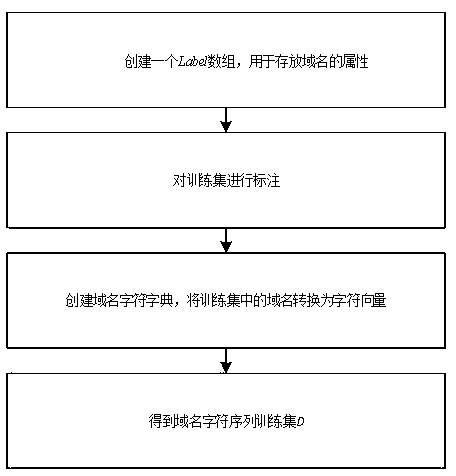
[0068] Step B1: Create a Label array to store the attributes of the domain name, and label the training set;
[0069] Step B2: Create a domain name character dictionary, convert the domain names in the training set into character vectors, and obtain the domain name character sequence training set D.
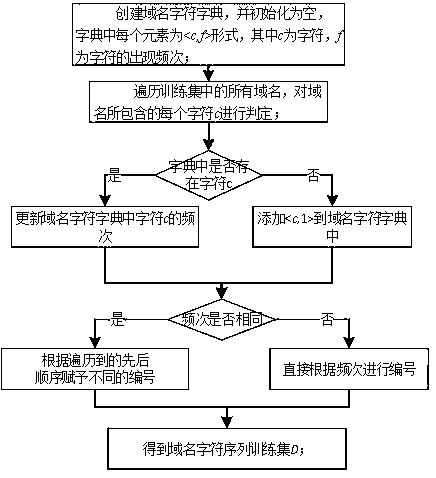
[0070] Step B21: Create a domain name character dictionary and initialize it to be empty. Each element in the dictionary is in the form of , where c is a character and f is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com