SATA bridging real-time transmission encryption system and method based on a domestic cryptographic algorithm
A technology of domestic cipher and encryption system, applied in the field of SATA bridge real-time transmission encryption system based on domestic cipher algorithm, can solve the problems of poor data security, inability to realize data ciphertext transmission, etc., and achieve the effect of ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
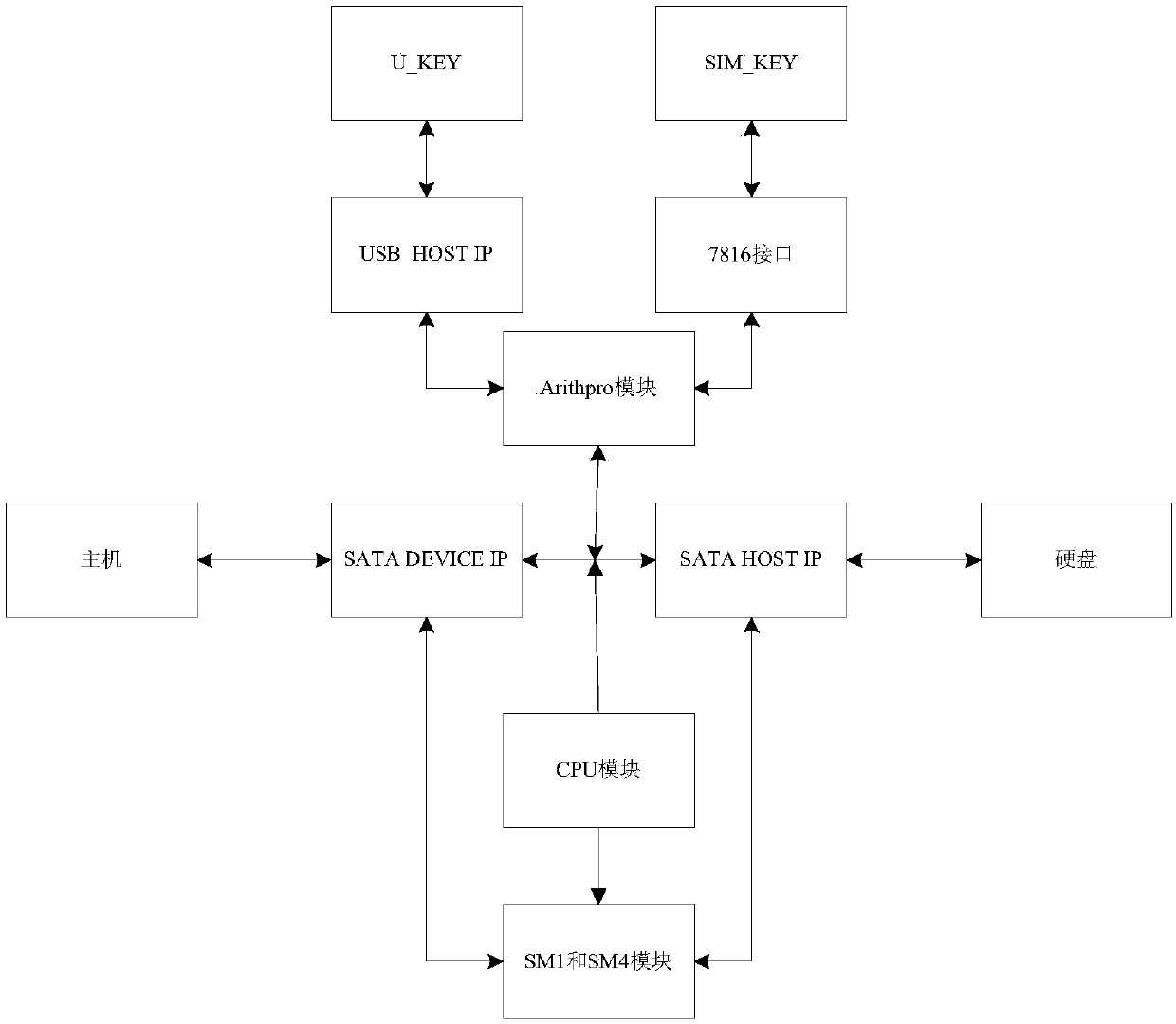
[0060] Such as figure 1 as shown, figure 1 It is an overall architecture diagram of the SATA bridging real-time transmission encryption system based on the domestic cryptographic algorithm, including the security storage control chip, SATA DEVICE IP core, SATA HOSTIP core and hard disk of the desktop system of the computer connected in sequence, and also includes the USB HOST IP core. To authenticate the storage device U_KEY on the external USB port of the secure storage control chip inserted into the desktop system, the simple data management protocol SM1 module and SM4 module for data encryption and decryption are connected to the SATA DEVICE IP core and SATA HOST IP core respectively.
[0061] Among them, the USB HOST IP or 7816 interface is mainly used to complete the verification work and realize the identity authentication function; the communication between the desktop system and the SATA DEVICE IP, and the communication between the SATA HOST IP and the hard disk are co...
Embodiment 2
[0066] The present invention also provides an encryption method of a SATA bridging real-time transmission encryption system based on a domestic cryptographic algorithm. According to the working process, the present invention is divided into two parts: one is an identity authentication process, and the other is a data encryption and decryption process.
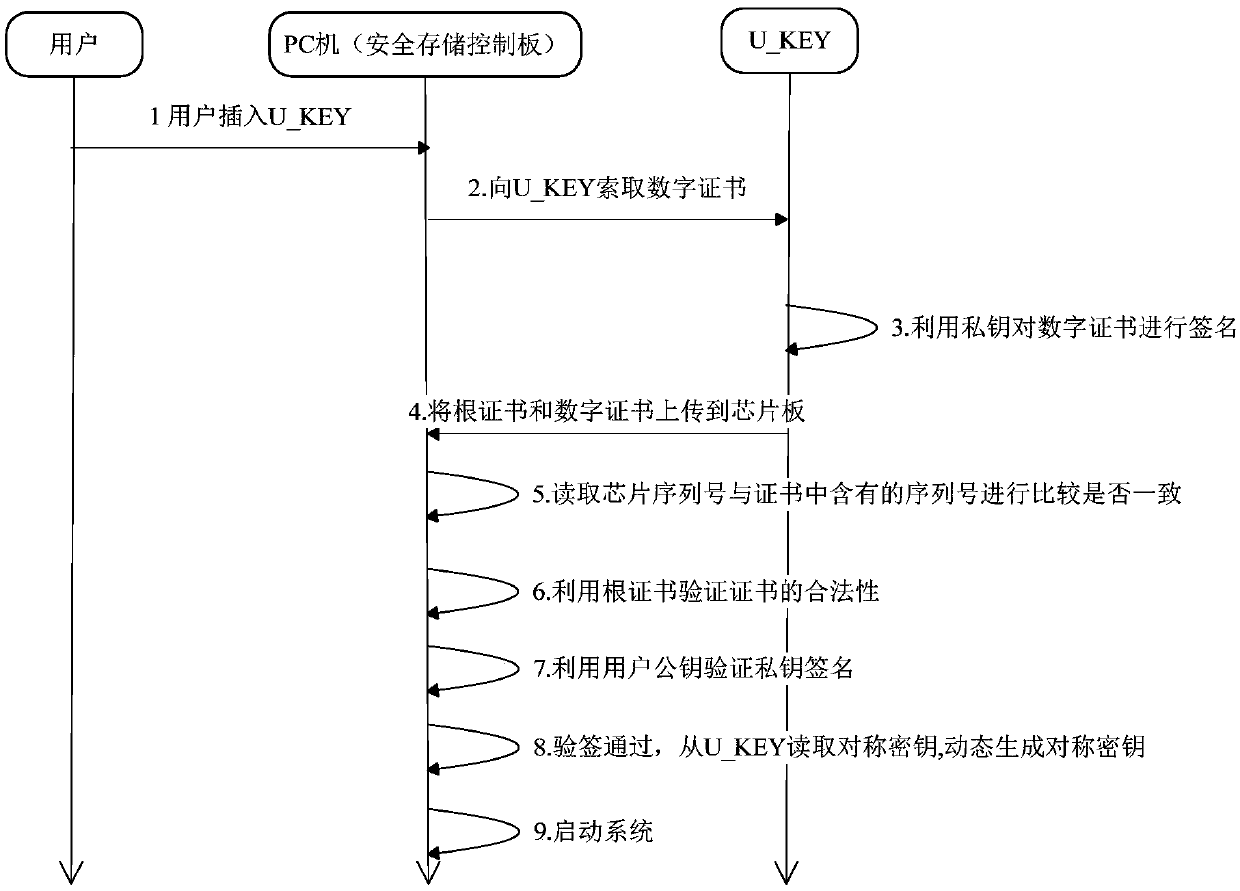
[0067] Identity authentication is a very important part of the design. When the user inserts the U_KEY into the external U port of the chip board, the identity authentication firmware will complete the identity authentication interaction with the U_KEY. The specific interaction process is as follows:
[0068] After the user's computer is started, the user inserts the U-KEY; reads the signature certificate information from the U_KEY through the USB HOST IP; before U_KEY sends the signature certificate, it first uses the SM3 module of U_KEY to hash the signature digital certificate, and then uses the user's private key to hash ag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com