Method, system, computer device and storage medium for acquiring shell execution authority
A technology of permissions and execution results, which is applied in the field of computer device permission control, can solve problems that affect user experience, be easily attacked by rogue software, and cannot be used in time, and achieve the effect of reducing the trouble of running permissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
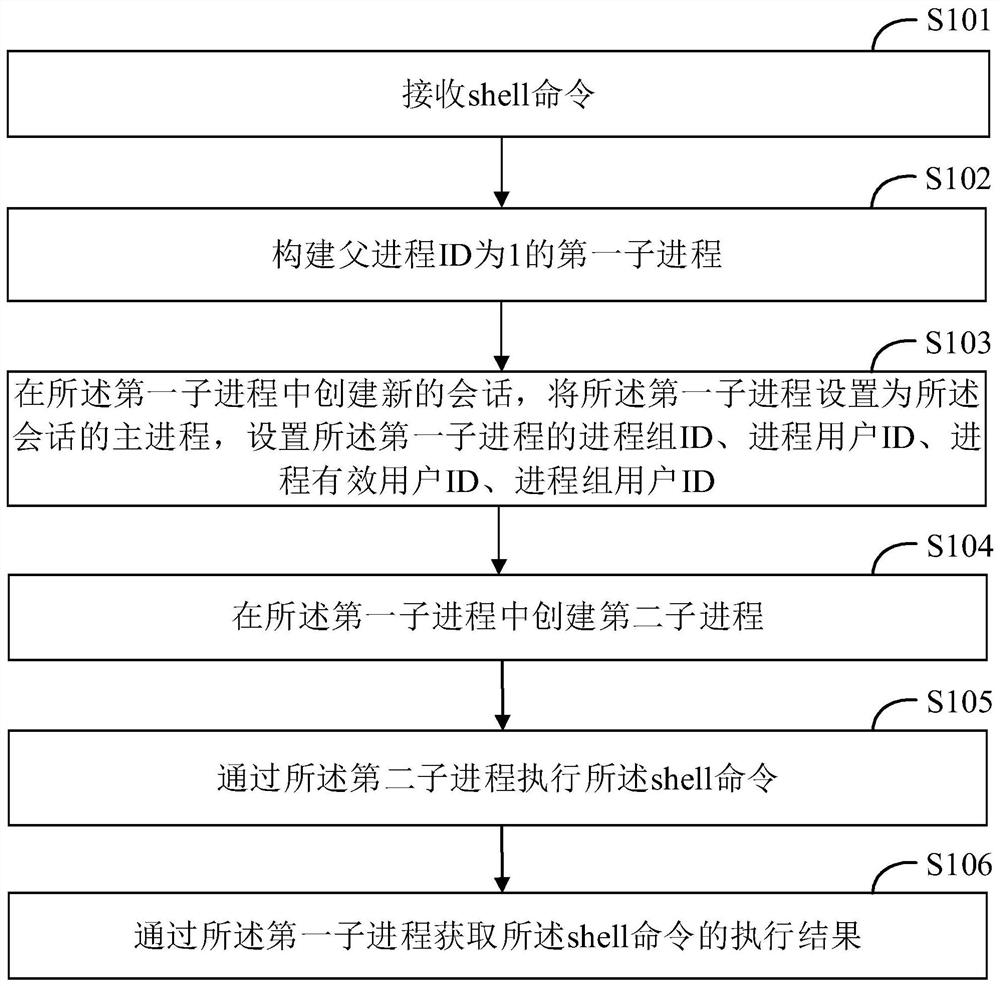
[0049] figure 1 is a flowchart of a method for obtaining shell execution authority provided by an embodiment of the present invention. The method for obtaining shell execution authority is applied to a computer device, and is used to obtain the shell execution authority of the computer device.
[0050] Referring to 1, the method for obtaining shell execution permission specifically includes the following steps:
[0051] S101. Receive a shell command.
[0052] The shell command is used to access the services of the operating system kernel.
[0053] Shell commands are in the form of strings. For example, the shell command is "am start –ncom.example.hello / .MainActivity".
[0054] Shell commands can include file and directory operation commands, such as the ls command, which is used to display information about files and directories; another example is the cd command, which is used to rename a directory; and another example is the diff command, which is used to compare file co...
Embodiment 2
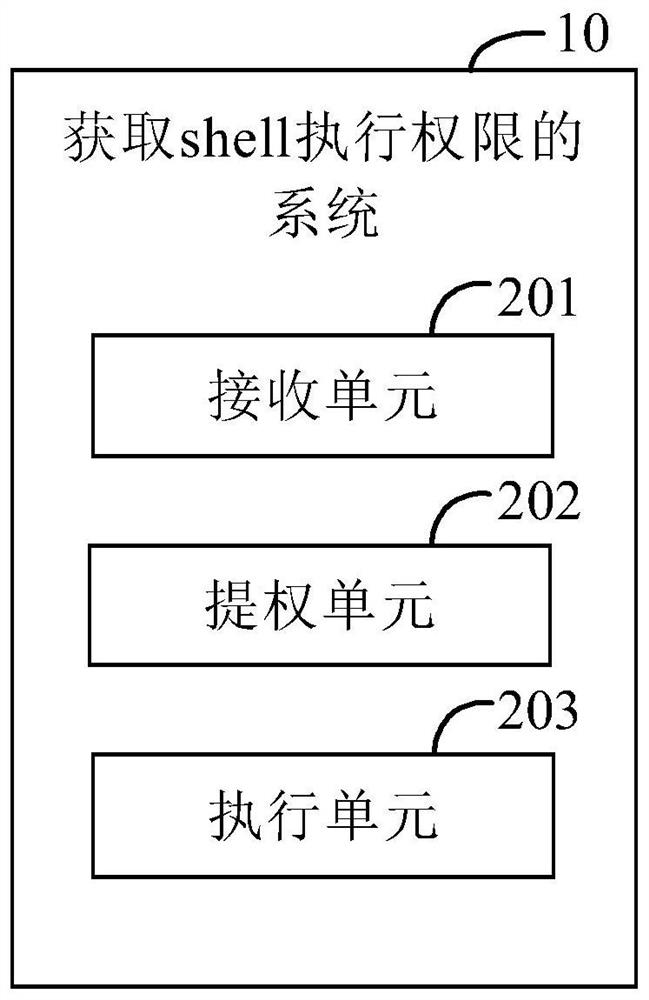
[0096] figure 2The structural diagram of a preferred embodiment of the system for obtaining shell execution authority provided by the embodiment of the present invention. The system for obtaining shell execution authority is applied to a computer device, and is used to obtain the shell execution authority of the computer device.
[0097] like figure 2 As shown, the system 10 for obtaining shell execution authority may include: a receiving unit 201 , a privilege escalation unit 202 , and an execution unit 203 .
[0098] The receiving unit 201 is configured to receive a shell command.
[0099] The shell command is used to access the services of the operating system kernel.
[0100] Shell commands are in the form of strings. For example, the shell command is "am start –ncom.example.hello / .MainActivity".
[0101] Shell commands can include file and directory operation commands, such as the ls command, which is used to display information about files and directories; another...
Embodiment 3
[0143] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium. When the computer program is executed by a processor, the steps in the above-mentioned method embodiment for acquiring shell execution authority are implemented, for examplefigure 1 S101-S106 shown:
[0144] S101, receiving a shell command;
[0145] S102, constructing the first child process whose parent process ID is 1;
[0146] S103. Create a new session in the first sub-process, set the first sub-process as the main process of the session, and set the process group ID, process user ID, and process effective user of the first sub-process ID, process group user ID;
[0147] S104. Create a second subprocess in the first subprocess;
[0148] S105. Execute the shell command through the second subprocess;
[0149] S106. Obtain an execution result of the shell command through the first subprocess.
[0150] Alternatively, when the compute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com