Code obfuscation method and system, computer device and computer readable storage medium
A code obfuscation, computer program technology, applied in the field of software development, can solve problems such as reducing development efficiency and quality, misconfiguration, etc., to achieve the effect of reducing the probability of manual configuration omission or configuration error
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
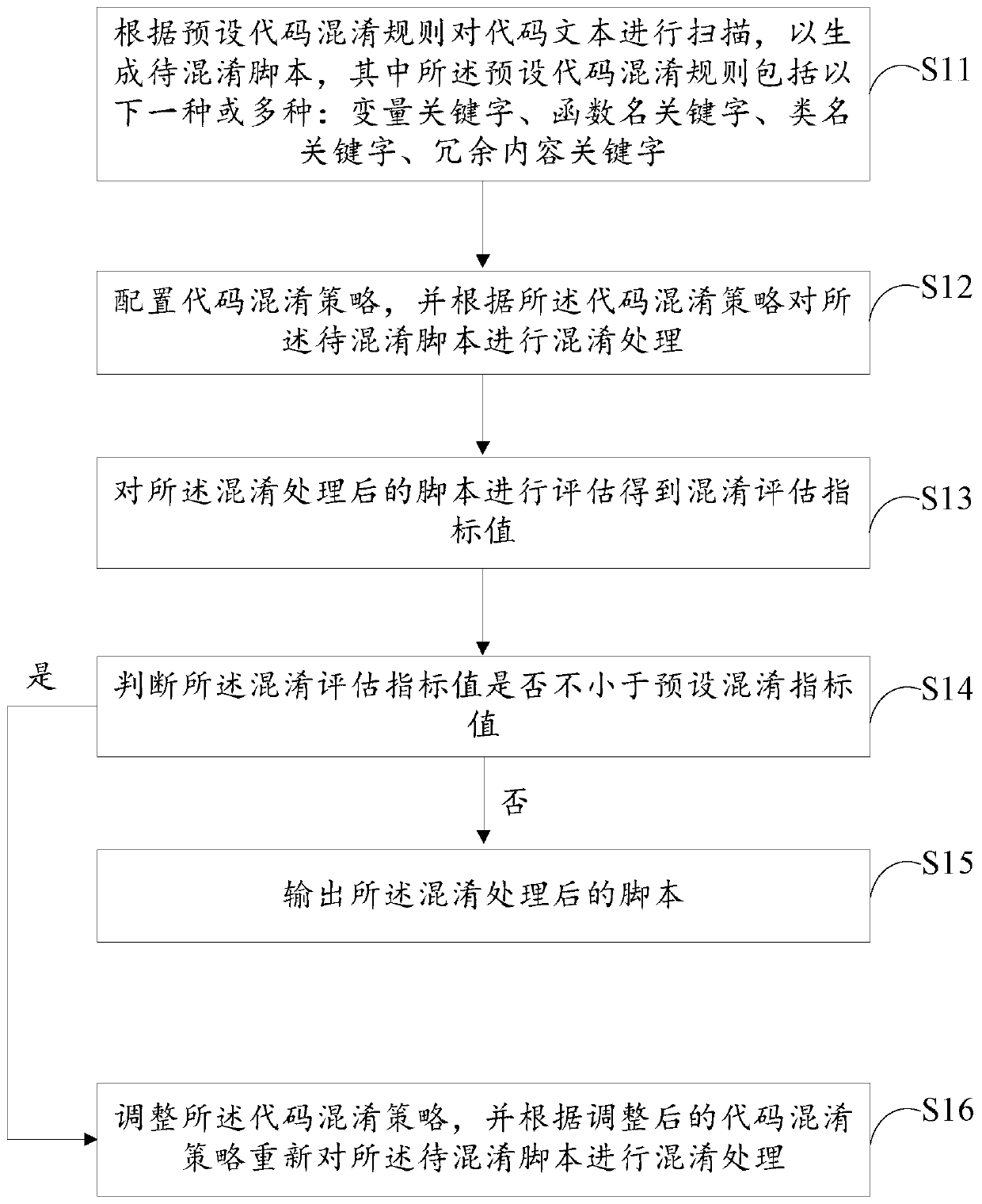
[0044] figure 1 It is a flow chart of the steps of a preferred embodiment of the code obfuscation method of the present invention. According to different requirements, the order of the steps in the flowchart can be changed, and some steps can be omitted.
[0045] refer to figure 1 As shown, the code obfuscation method specifically includes the following steps.
[0046] Step S11, scan the code text according to the preset code obfuscation rules to generate the script to be obfuscated, wherein the preset code obfuscation rules include one or more of the following: variable keywords, function name keywords, class name keywords , redundant content keywords.
[0047] In one embodiment, before the obfuscation operation, a code obfuscation rule can be pre-defined and established, and the code obfuscation rule can include multiple variable keywords, multiple function name keywords, multiple class name keywords, multiple redundant content keywords, etc. After the code obfuscation ...
Embodiment 2
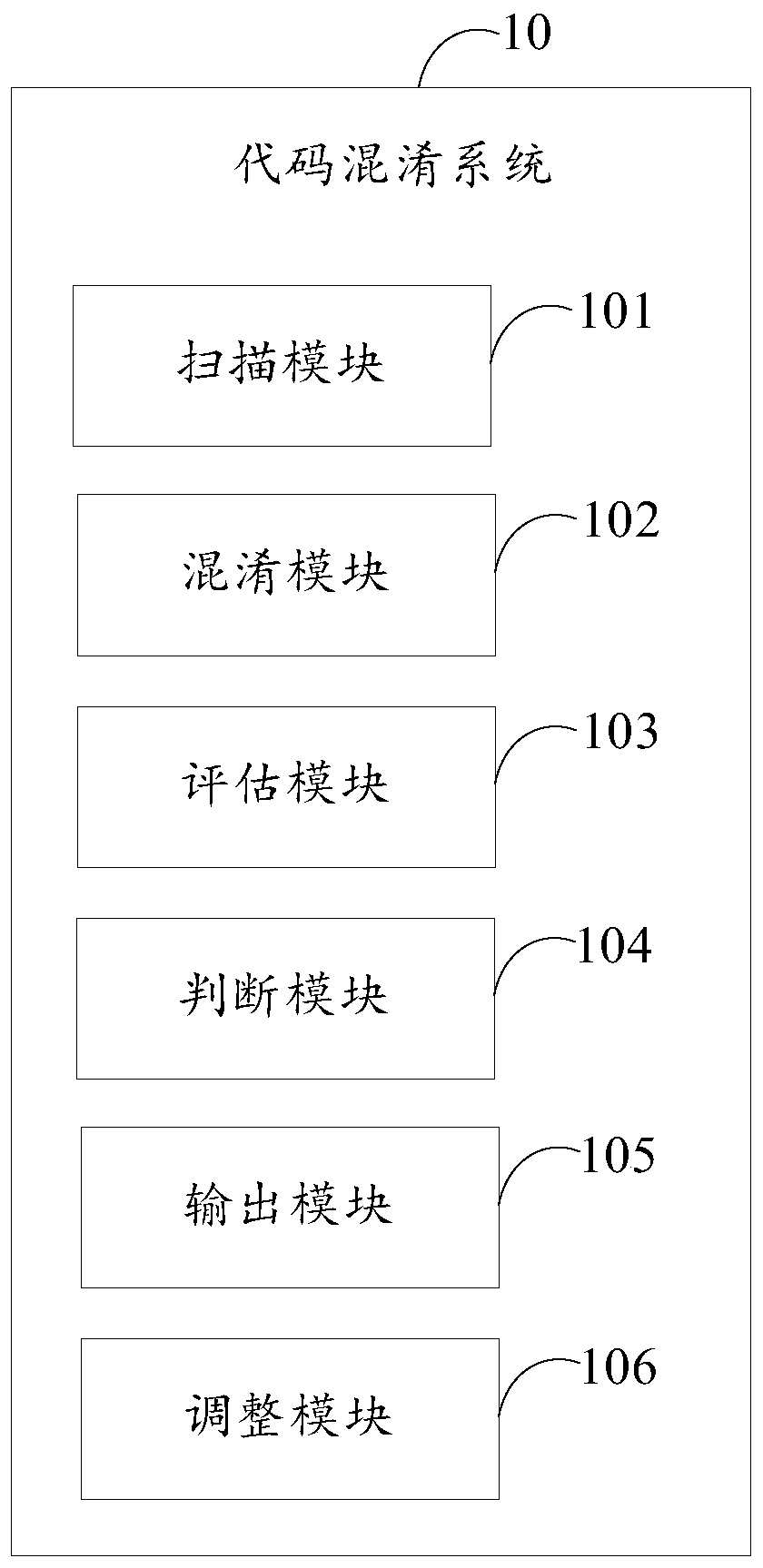
[0072] figure 2 It is a functional block diagram of a preferred embodiment of the code obfuscation system of the present invention.
[0073] refer to figure 2 As shown, the code obfuscation system 10 may include a scanning module 101 , an obfuscation module 102 , an evaluation module 103 , a judgment module 104 , an output module 105 and an adjustment module 106 .
[0074] The scanning module 101 is used to scan the code text according to the preset code obfuscation rules to generate the script to be obfuscated, wherein the preset code obfuscation rules include one or more of the following: variable keywords, function name keywords, Class name keywords, redundant content keywords.
[0075] In one embodiment, before the obfuscation operation, a code obfuscation rule can be predefined and established, and the code obfuscation rule can include multiple variable keywords, multiple function name keywords, multiple class name keywords, multiple redundant content keywords, etc. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com