Key person monitoring method based on a face recognition technology
A face recognition and key technology, applied in the field of computer vision, to achieve the effect of flexible deployment and control mechanism, rich real-time alarms, and wide application fields
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
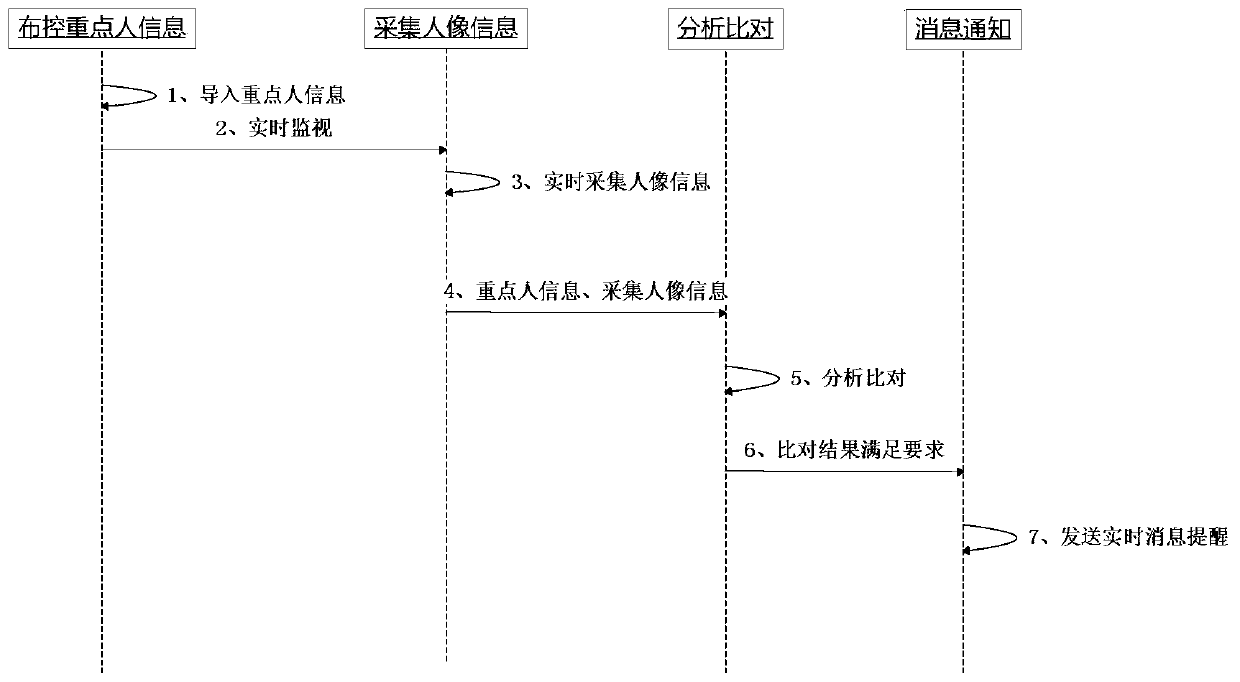
[0048] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. Such as figure 1 Shown, method of the present invention comprises the following steps:
[0049] Step 1. Based on computer vision technology, the face images in the video are automatically collected and compared, and long-distance, non-contact monitoring and early warning of key people are carried out:
[0050] Step 1.1. Maintain key person information, enter the key person import interface, and import key person information in batches;
[0051] Step 1.2. Add, modify, and delete key person information in the system;
[0052] Step 2. Select the file to be imported, fill in the import description information and display the import success information and import failure information and explain the original image of the failure;
[0053] Step 3. Conduct key person query:
[0054] Step 3.1. Enter the name of the person on the key person query interface to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com