Patents
Literature
422 results about "Person Info" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
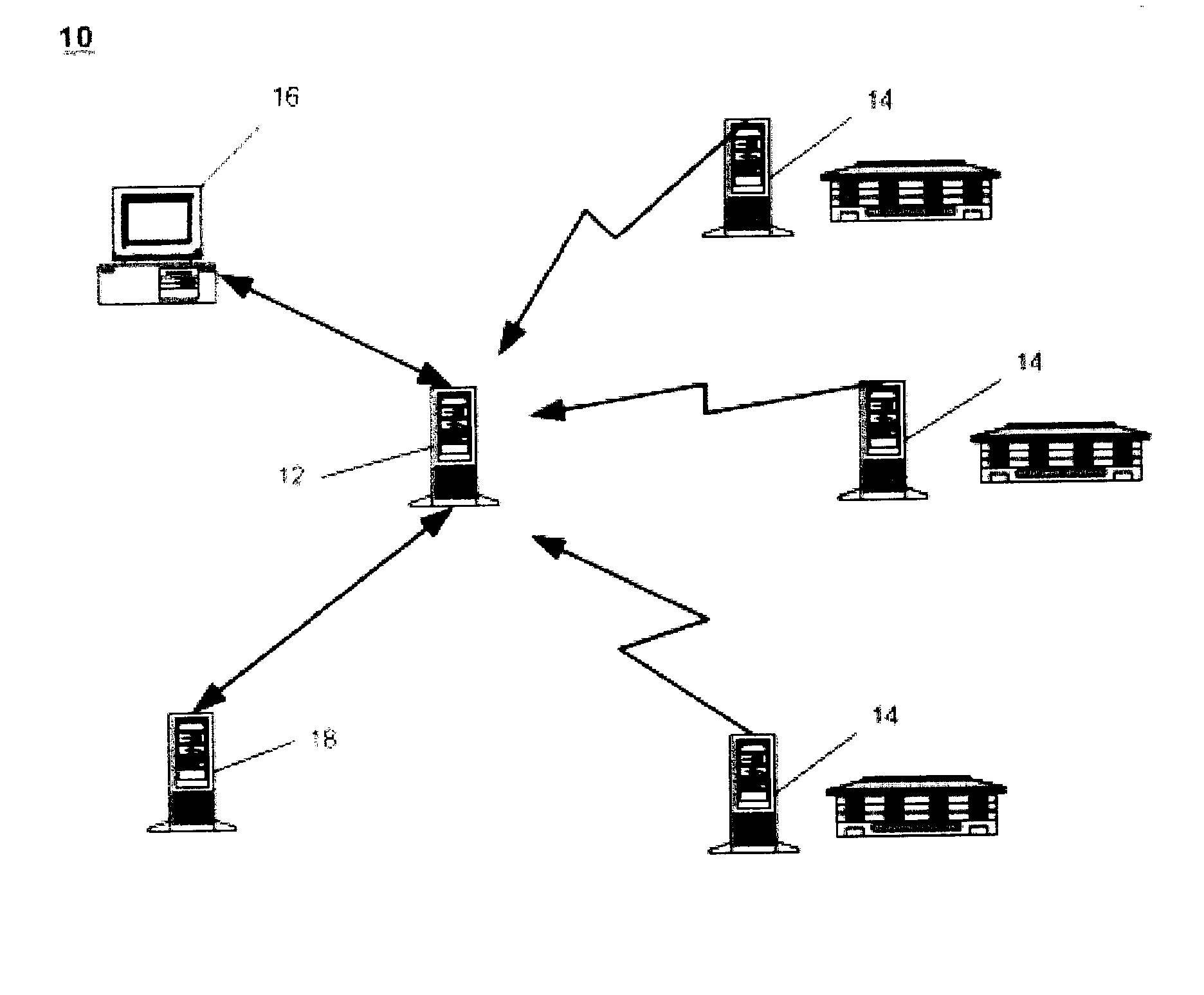
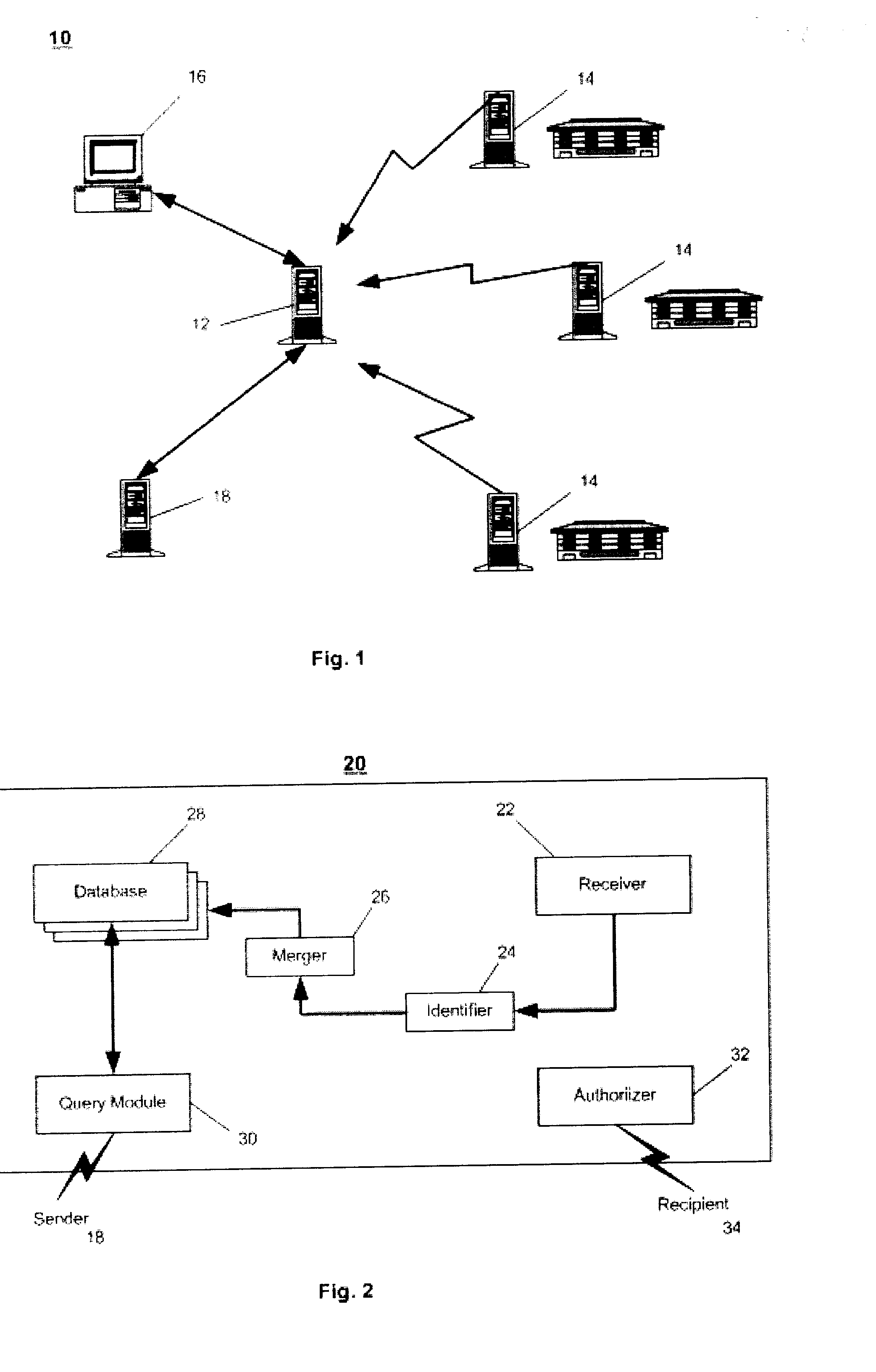
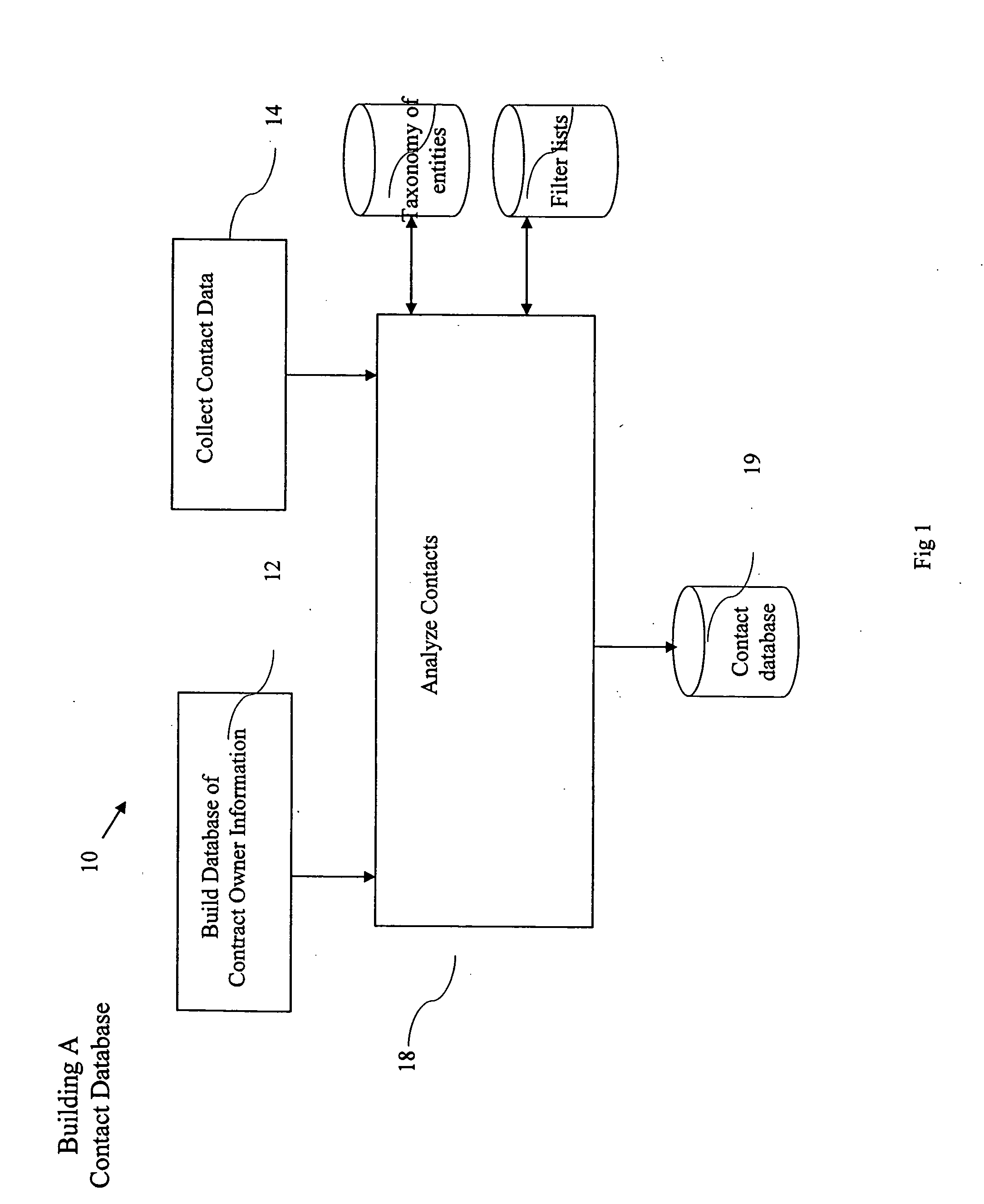
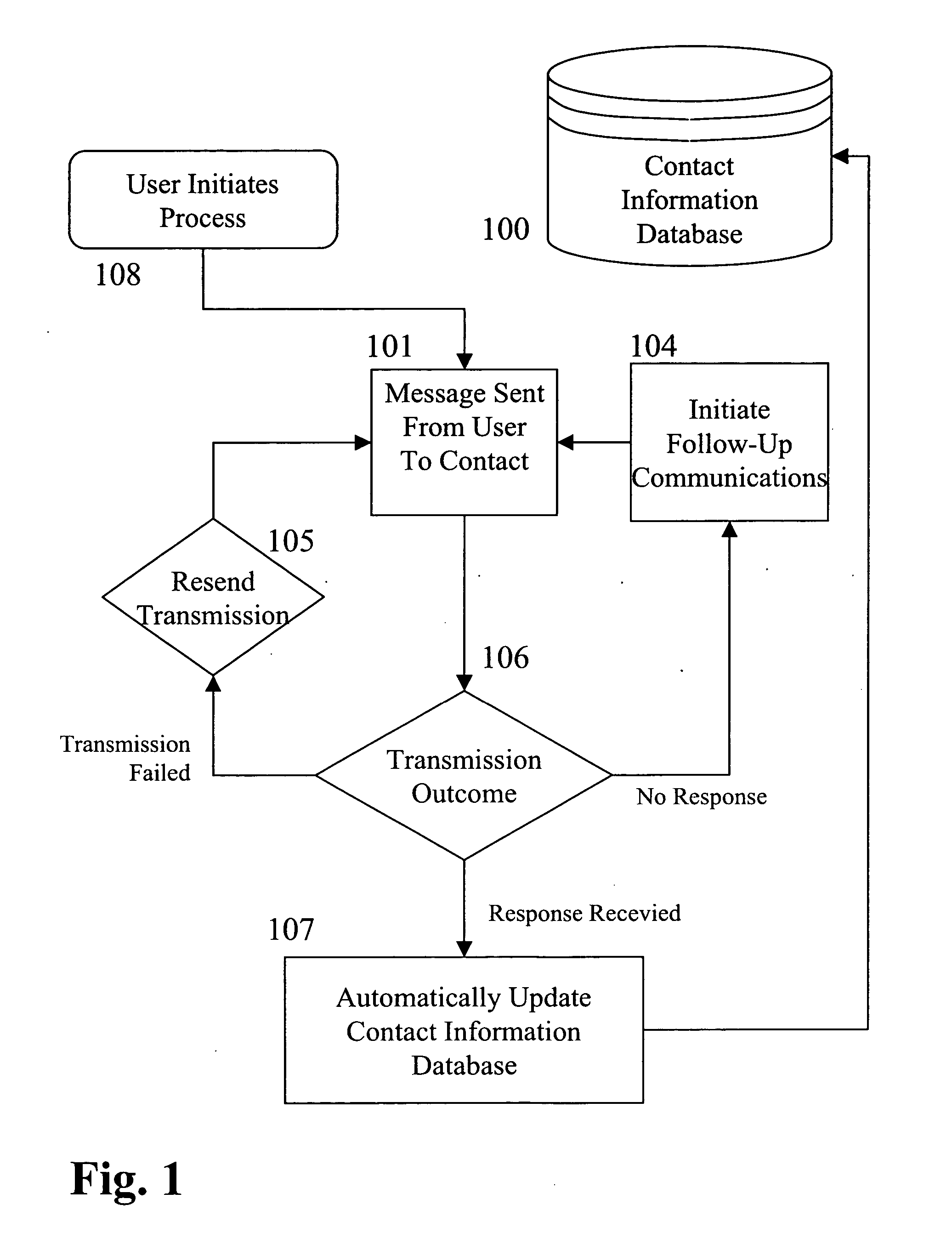
System and method for identifying alternate contact information
ActiveUS20040133561A1Reducing possible errorSimplify the search processDigital data processing detailsTelephonic communicationEmail addressAutomated database
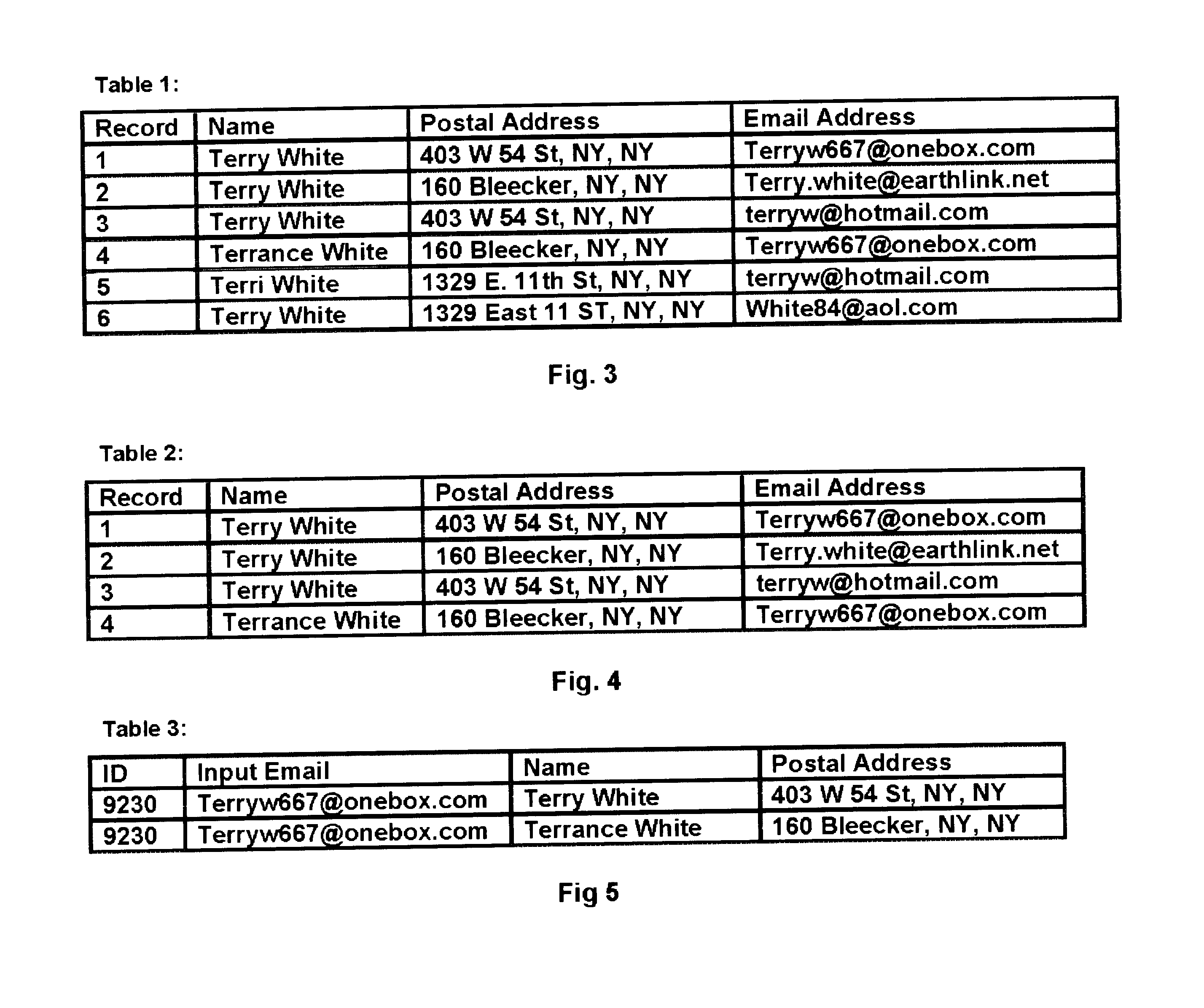
A method and system for identifying alternate contact information of a specific type; particularly, by providing an inputted Email address in a query, one or more alternate Email addresses can be returned to the query, using an automated database. The system is queried using an entity's known Email address, which, in turn, is associated with other contact information for the entity, such as name and postal address, and the other contact information is then used to identify alternative Email addresses for the targeted entity either at the time of the query or in preparation of the database, and the alternative Email address(es) are then outputted to the requestor from the system. The method uses knowledge of contact points of different types for the same entity to identify alternate contact points of a single type, within a database of contact information.
Owner:ATDATA LLC
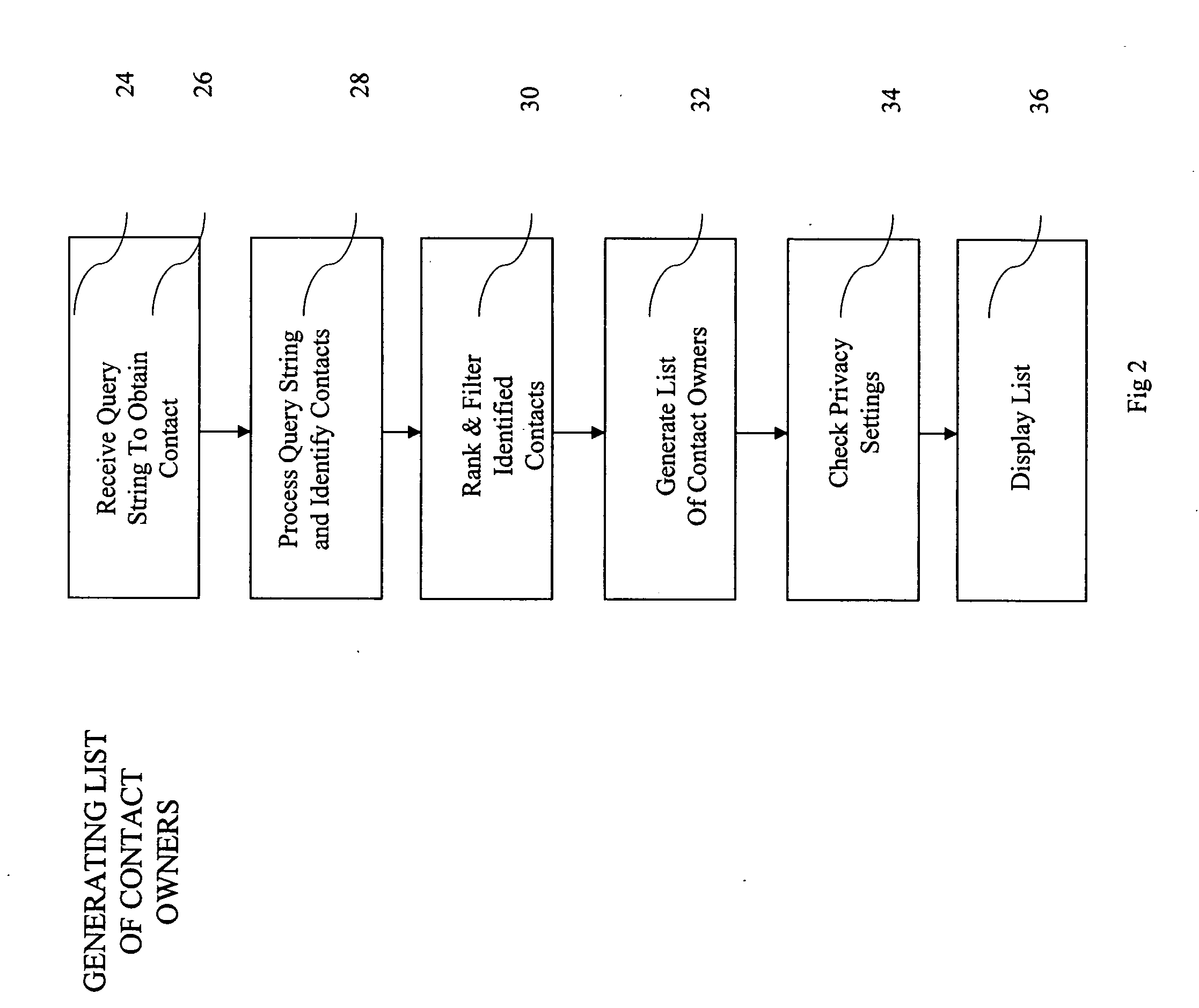
Relationship collaboration system
ActiveUS20050065980A1Improve identityData processing applicationsWeb data indexingDomain nameEmail address
A computer implemented method of processing data containing information about relationships between contacts and a community of contact owners, comprises: collecting data including contact information, contact owner information and one or more values related to strength of a relationship between the contact and the contact owner; evaluating the strength of the relationship based on the one or more values; and storing the collected data and evaluated strength in a computer database. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include a domain name field; and setting the domain name field as a key field; whereby a record for an entity is found by reference to a domain name. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include an email address field; and setting the email address field as a key field; whereby a record for an entity is found by reference to an email address. A method of keying a database, comprising: building a database of records, each containing information about an entity, and each of which includes a field holding an identifier uniquely associated with an entity by a convention of computer networking; and setting the field holding the identifier as a key field; whereby a record for an entity is found by reference to an identifier. A method of sharing relationship information, comprising: maintaining a database of relationship information records; selecting contact information according to a selection criterion; and returning selected relationship information also complying with restrictions set in a set of hierarchical privacy policies.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
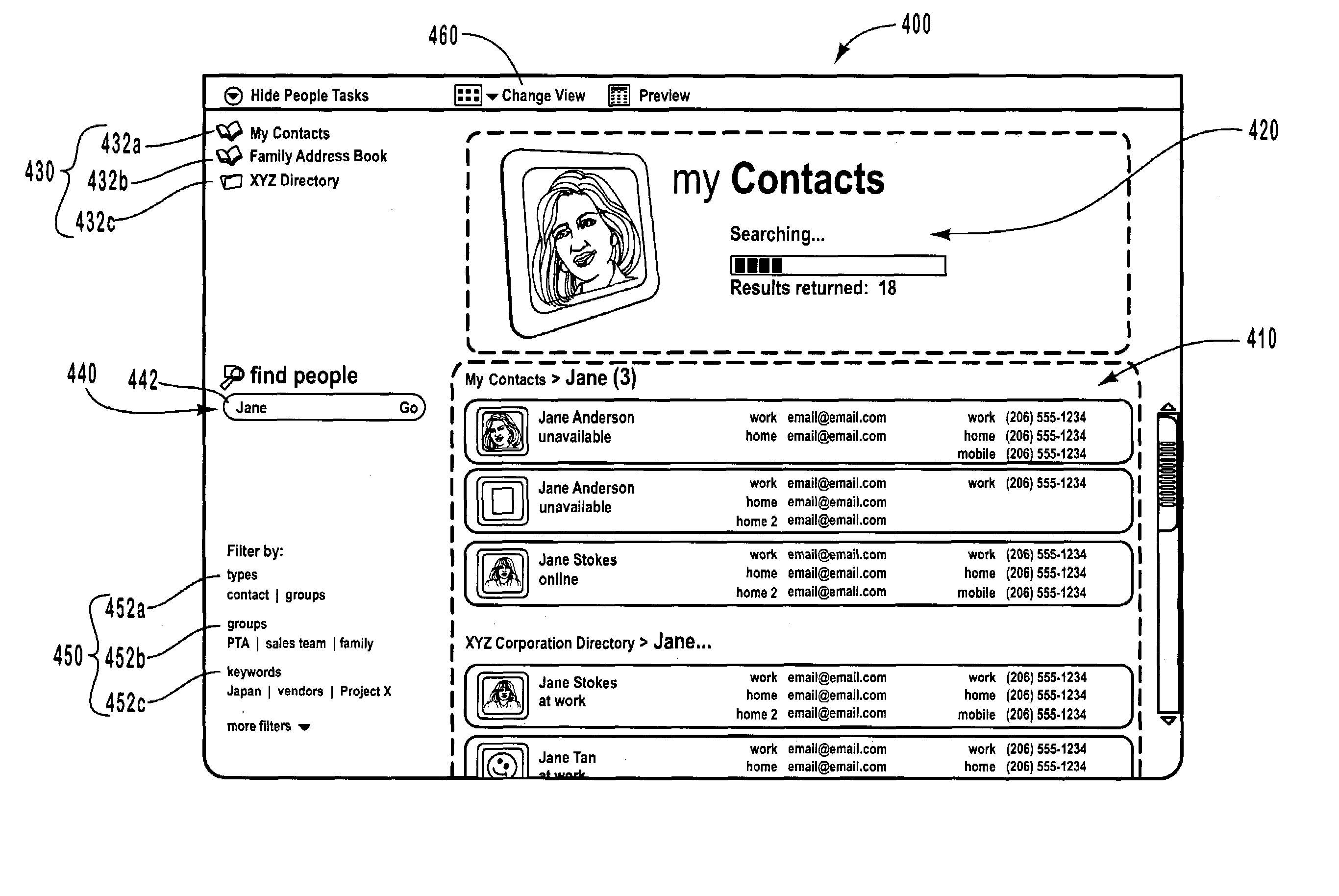
Contact user interface
An interface for enabling different contact information for a plurality of different contacts to be aggregated from numerous data stores into a single contact management system includes a window frame for displaying the contact information in a variety of rich views that graphically illustrate patterns existent within the contact information. Some of the available views include hierarchical, organizational, chronological, social, geographical and operational views of the contact information. The interface also enables a user to search through the aggregate contact information by search term and by filter. The interface also includes another window frame for displaying exploded, detailed, or additional information about selected directories and contacts.
Owner:MICROSOFT TECH LICENSING LLC
Methods of deterring, detecting, and mitigating fraud by monitoring behaviors and activities of an individual and/or individuals within an organization
InactiveUS20070294195A1Reduce fraudReduce detectionFinanceSpecial data processing applicationsRelevant informationKnowledge management
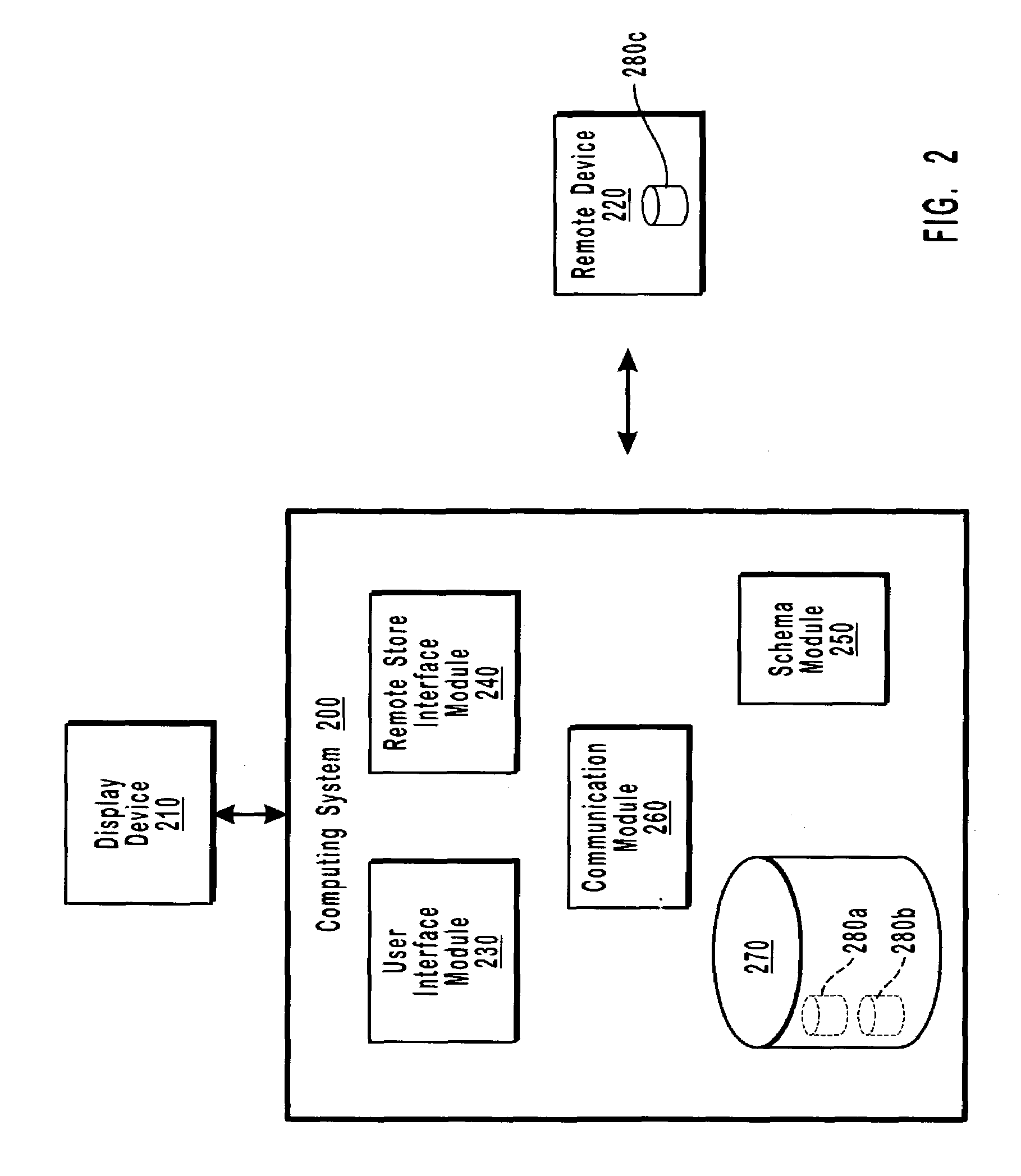
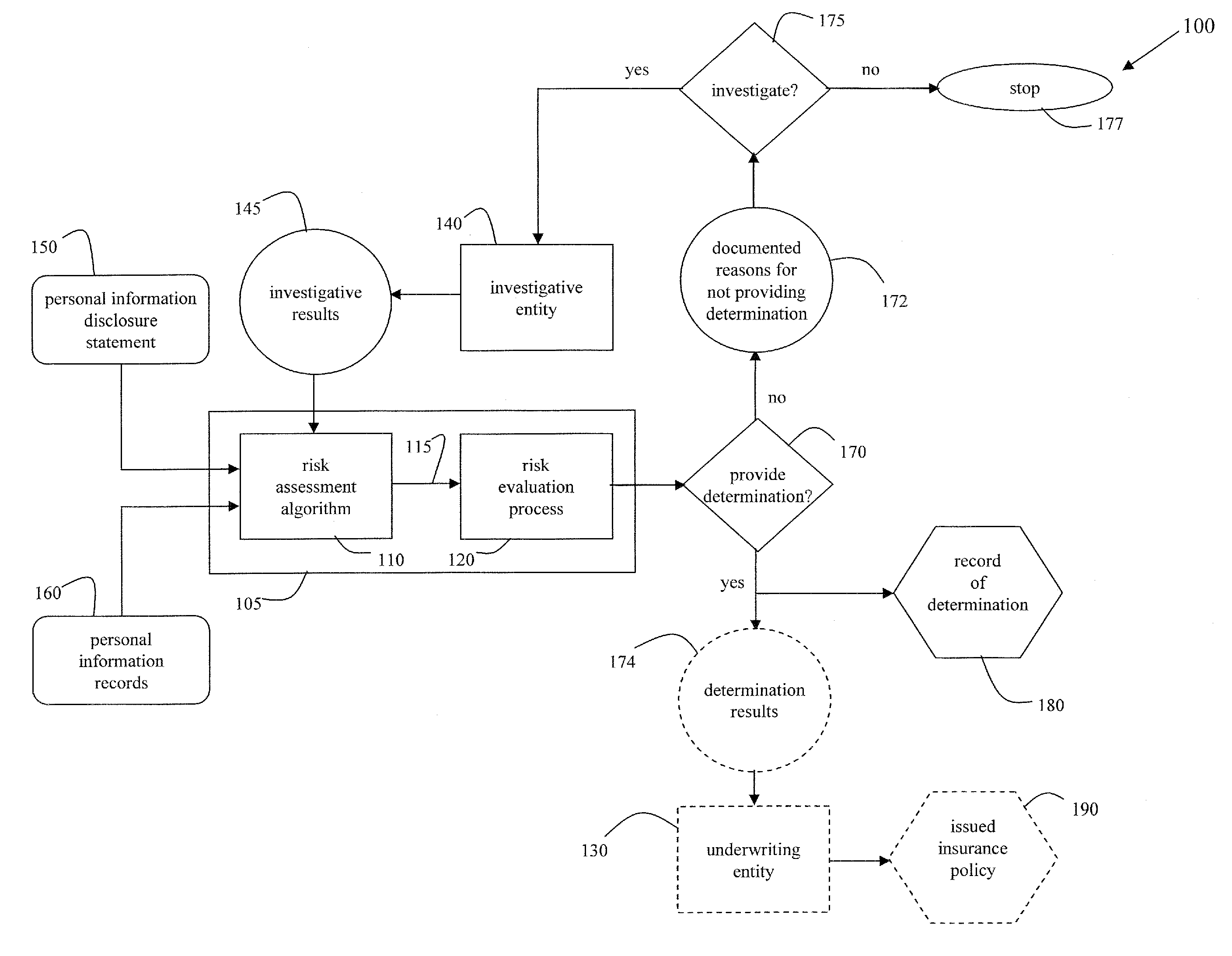
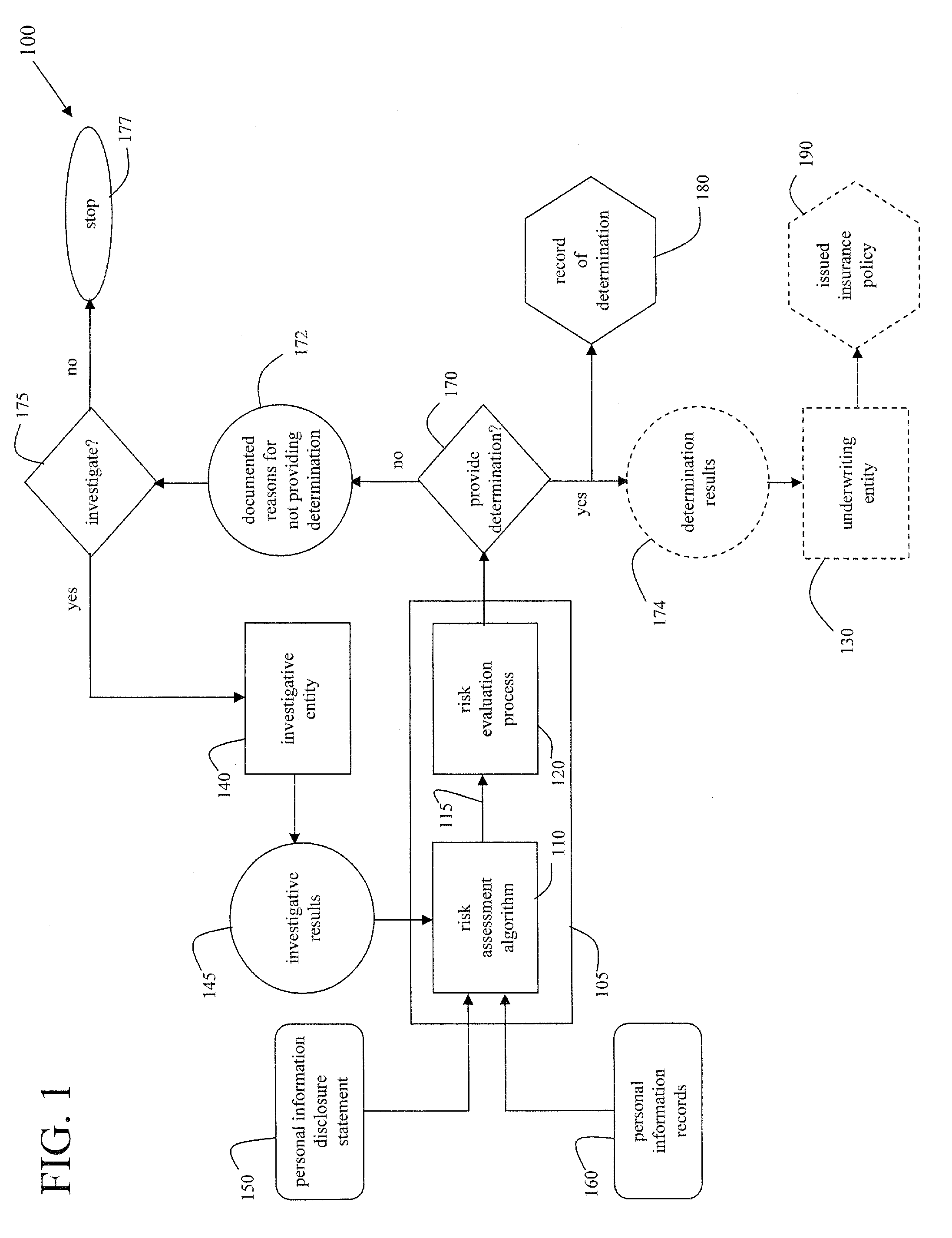
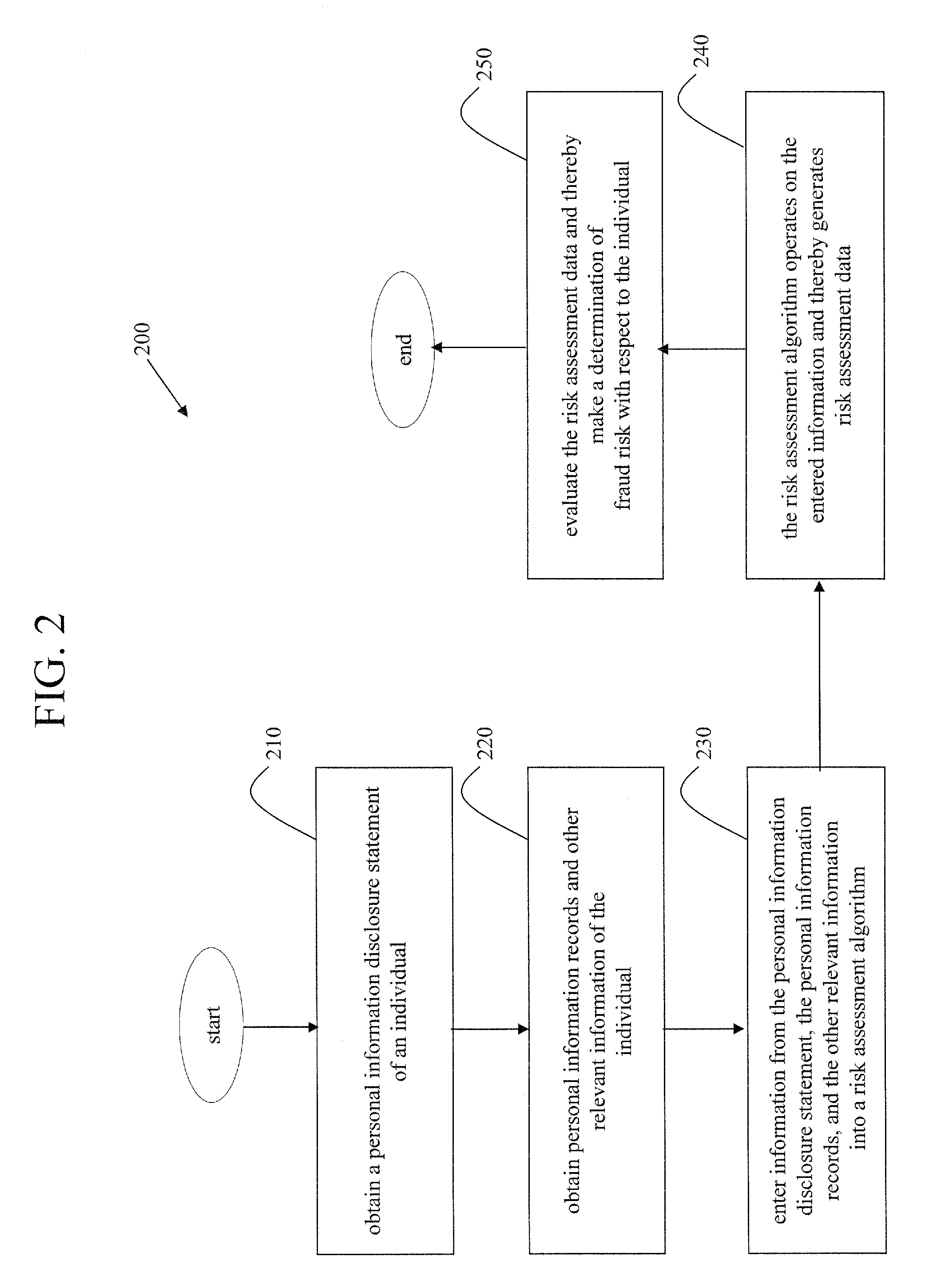
A cooperative arrangement and method to help deter and / or detect and / or mitigate fraud by evaluating and then monitoring the information of an individual or individuals for changes in fraud risk. A personal information disclosure statement, personal information records, and other relevant information associated with an individual, or a plurality of individuals, associated with an organization, an individual potentially to be associated with an organization, or an individual acting in his or her individual capacity are obtained. Information is extracted from the personal information disclosure statement, the personal information records, and the other relevant information and entered into a risk assessment algorithm. The risk assessment algorithm operates on the entered information and generates risk assessment data. The risk assessment data is evaluated to make a determination of fraud risk with respect to the individual(s). A decision to provide a fraud risk determination means that the risk associated with the individual, with respect to committing fraud, is acceptable. Risk assessment data on a plurality of key individuals within an organization may be generated and evaluated to make a determination of fraud risk with respect to the organization itself.
Owner:CURRY EDITH L +3
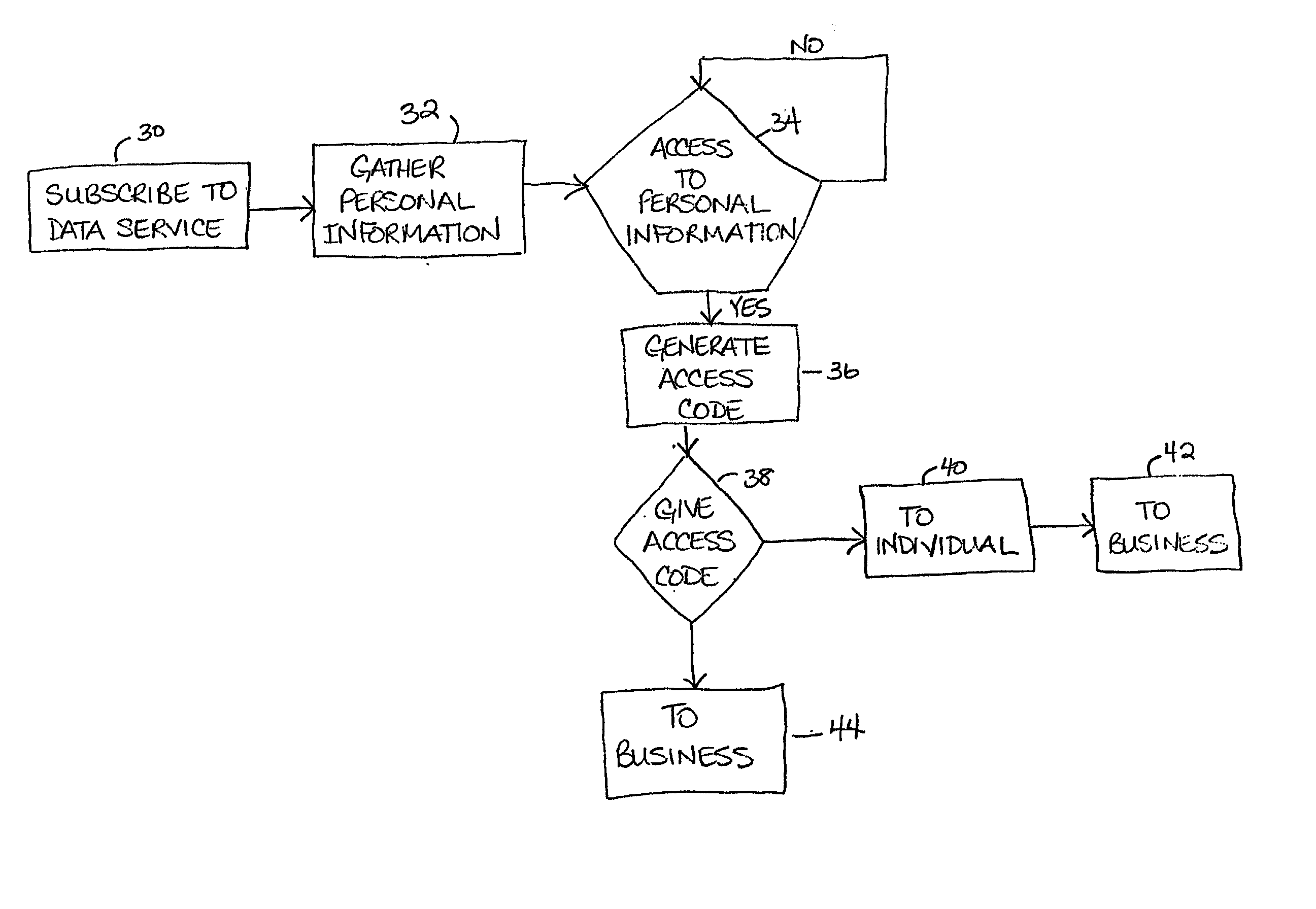
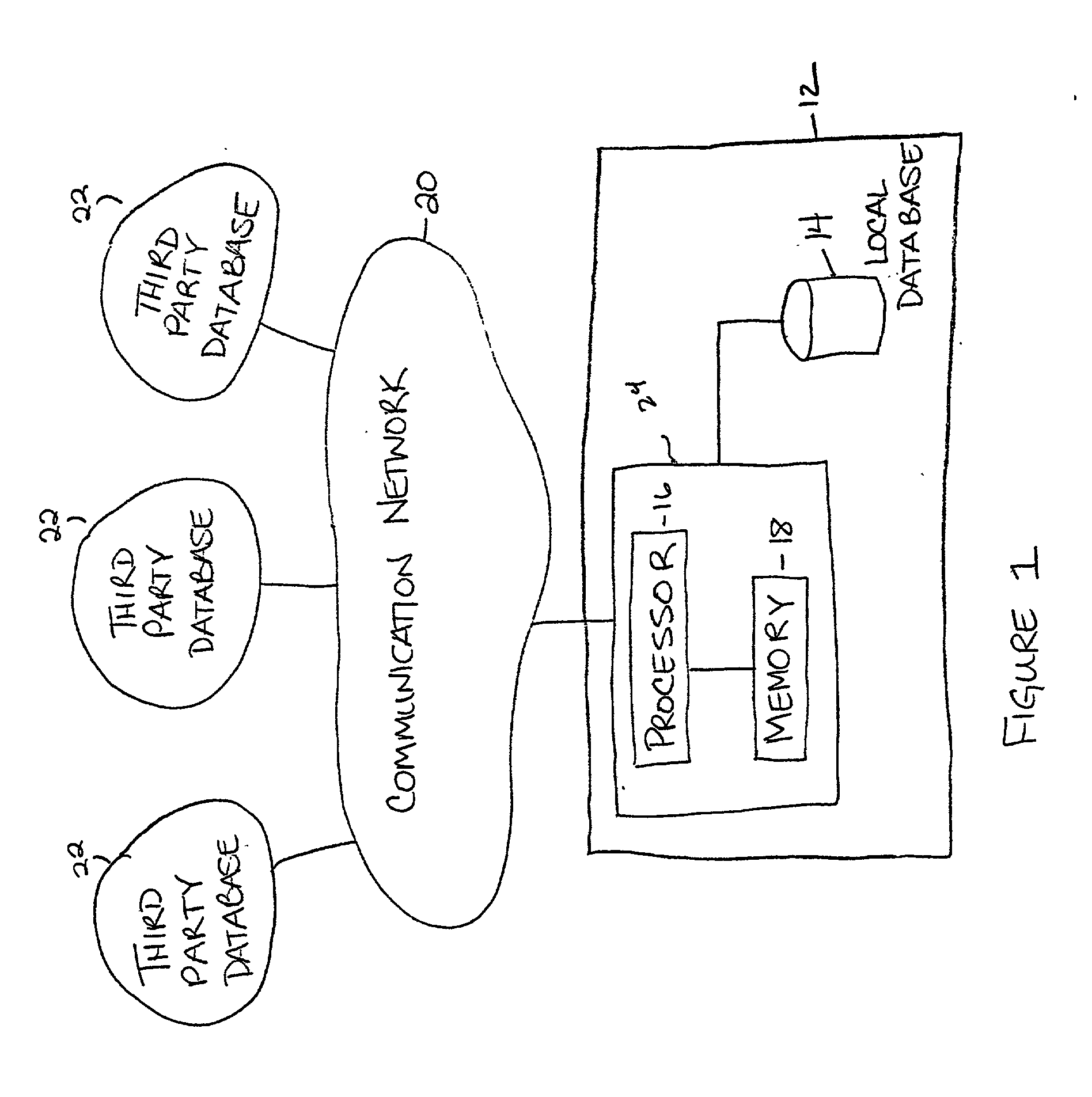
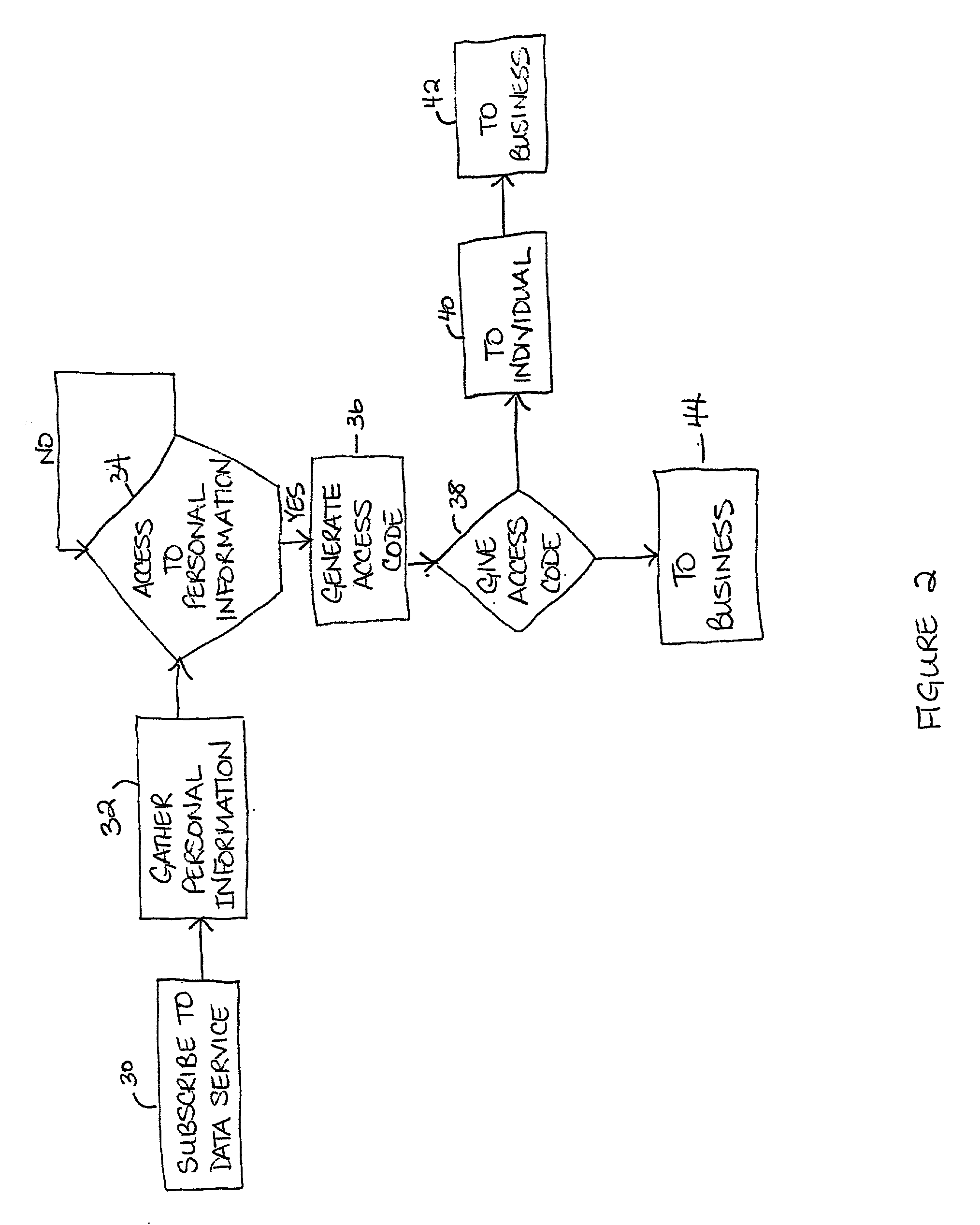
Method and system for a data service to control access to personal information
A method and system for a data service to gather, manage, and control access to personal information associated with an individual. The personal information may include an individual's financial records, medical records, motor vehicle records, and criminal records. The data service may collect the personal information from at least one third-party database, store the personal information in a local database, and actively verify whether the personal information is accurate. The data service may also allow the individual to remove all or selected personal information stored in the local database.
Owner:ZINGHER ABRAHAM +1
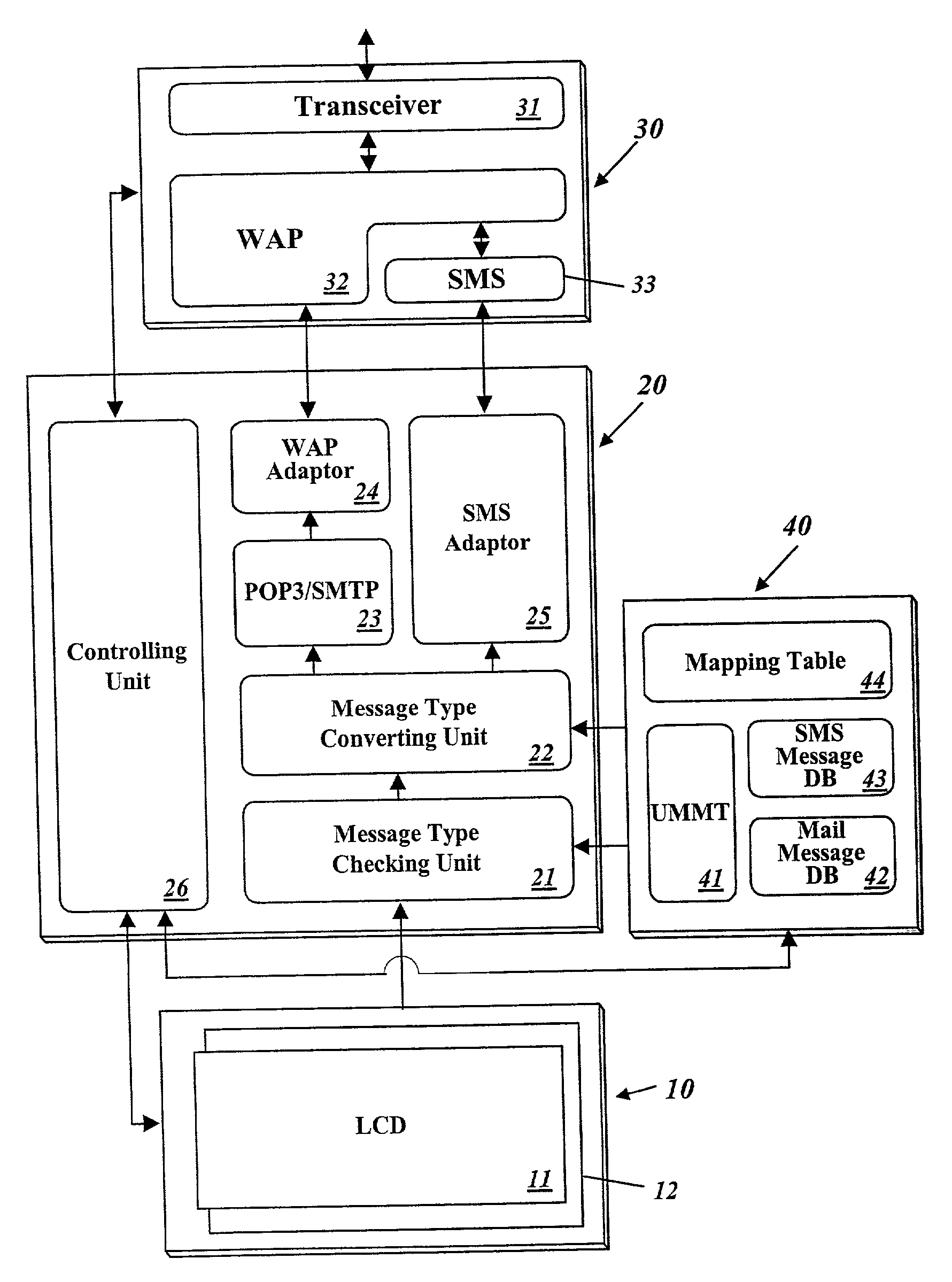
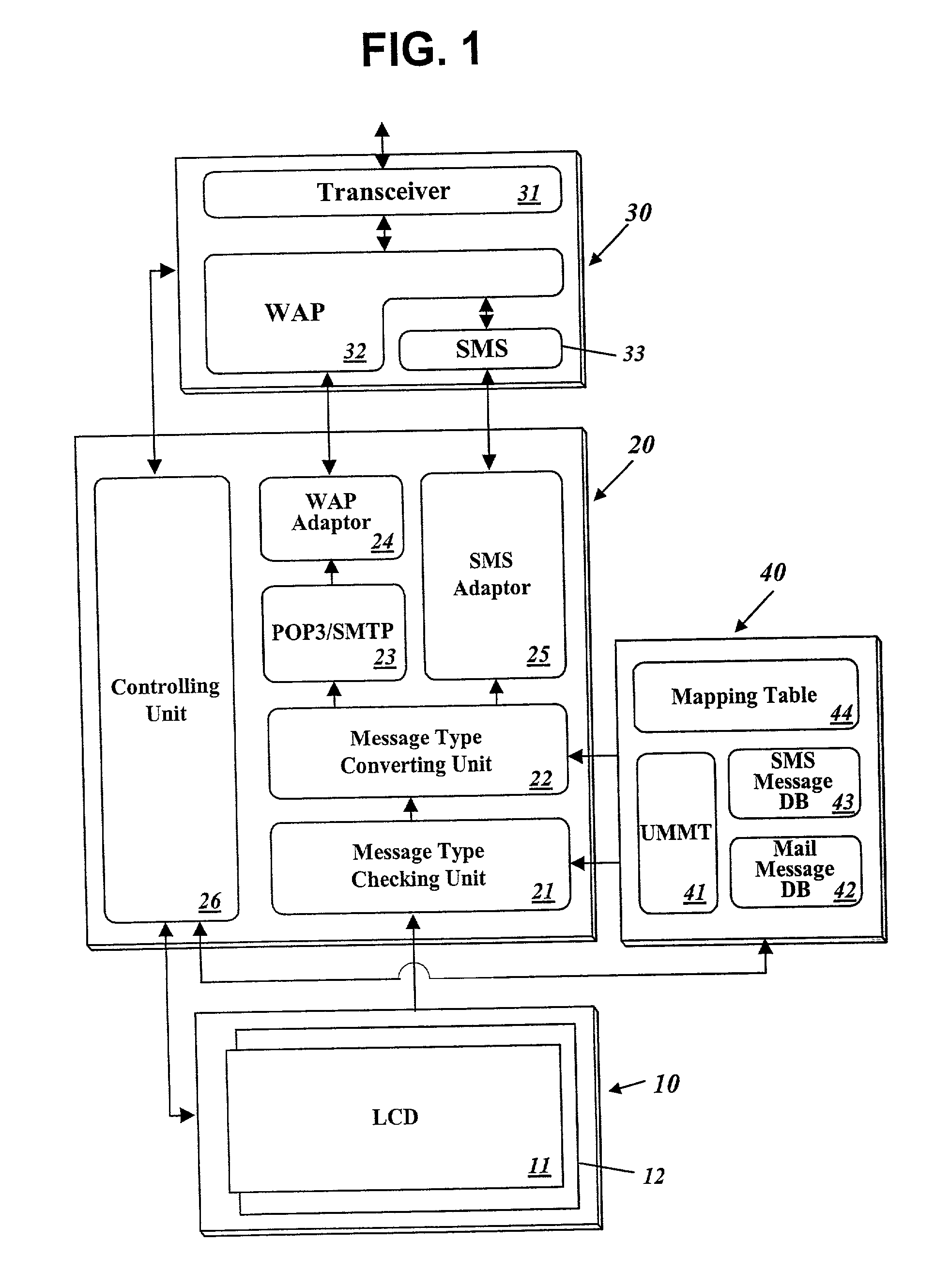
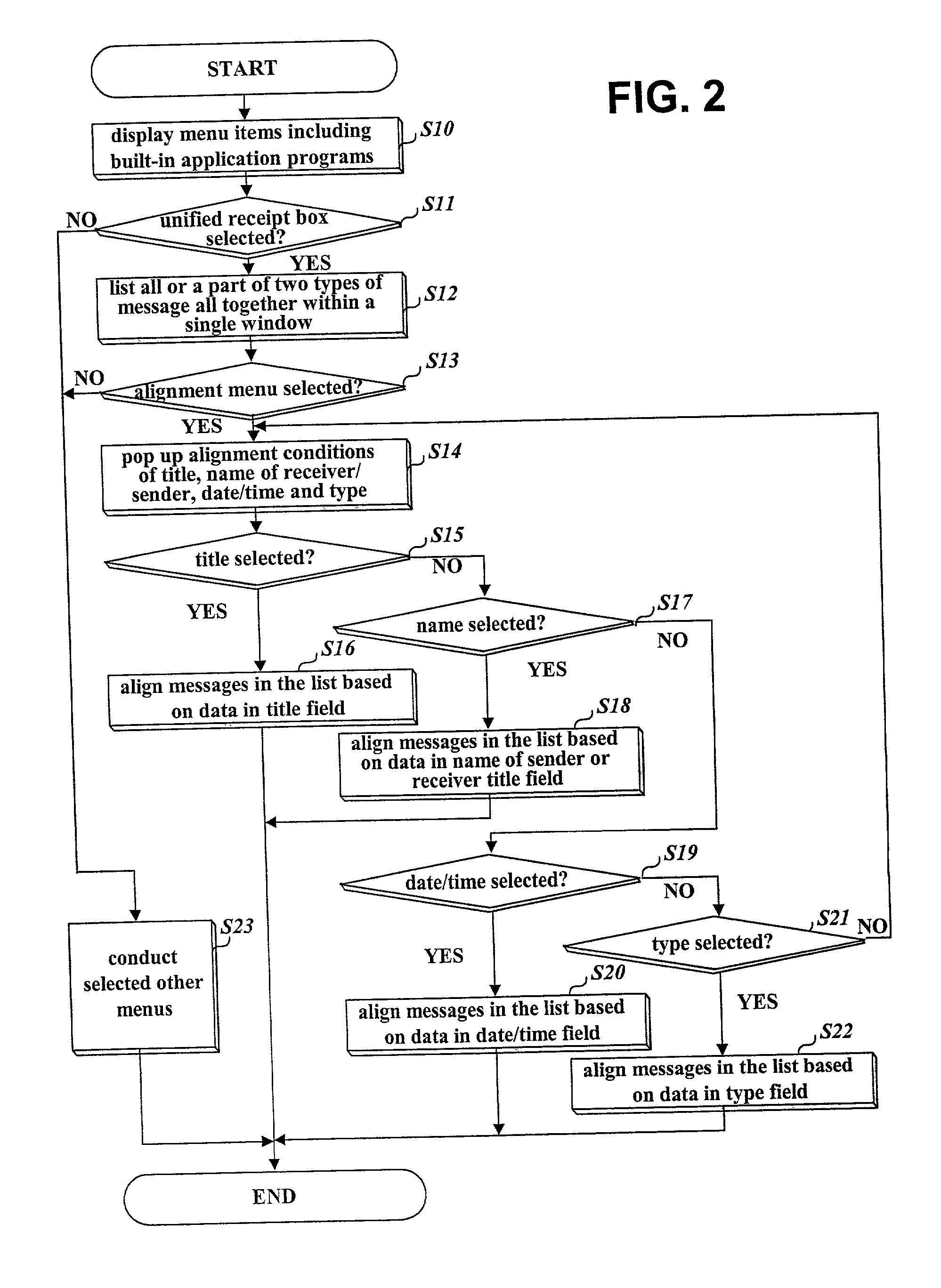
Unified management method of various types of messages of a personal information terminal
InactiveUS20020152220A1Data processing applicationsDigital data processing detailsComputer hardwareMessage type
The present invention relates to a method of displaying several types of messages all together through a single window and of enabling a user to write and transmit a message with no consideration of message type. This unified message management method displays various types of messages all together along with their respective message types through a single window, converts the type of a written message, if needed, to match it to a protocol determined based on information written in its field distinguishing a message type, and transmits the type-converted message, whereby a user can confirm all types of received messages at a time and user's inconvenience that a message type to write should be distinguished in advance prior to choosing a message input screen can be removed.
Owner:LG ELECTRONICS INC
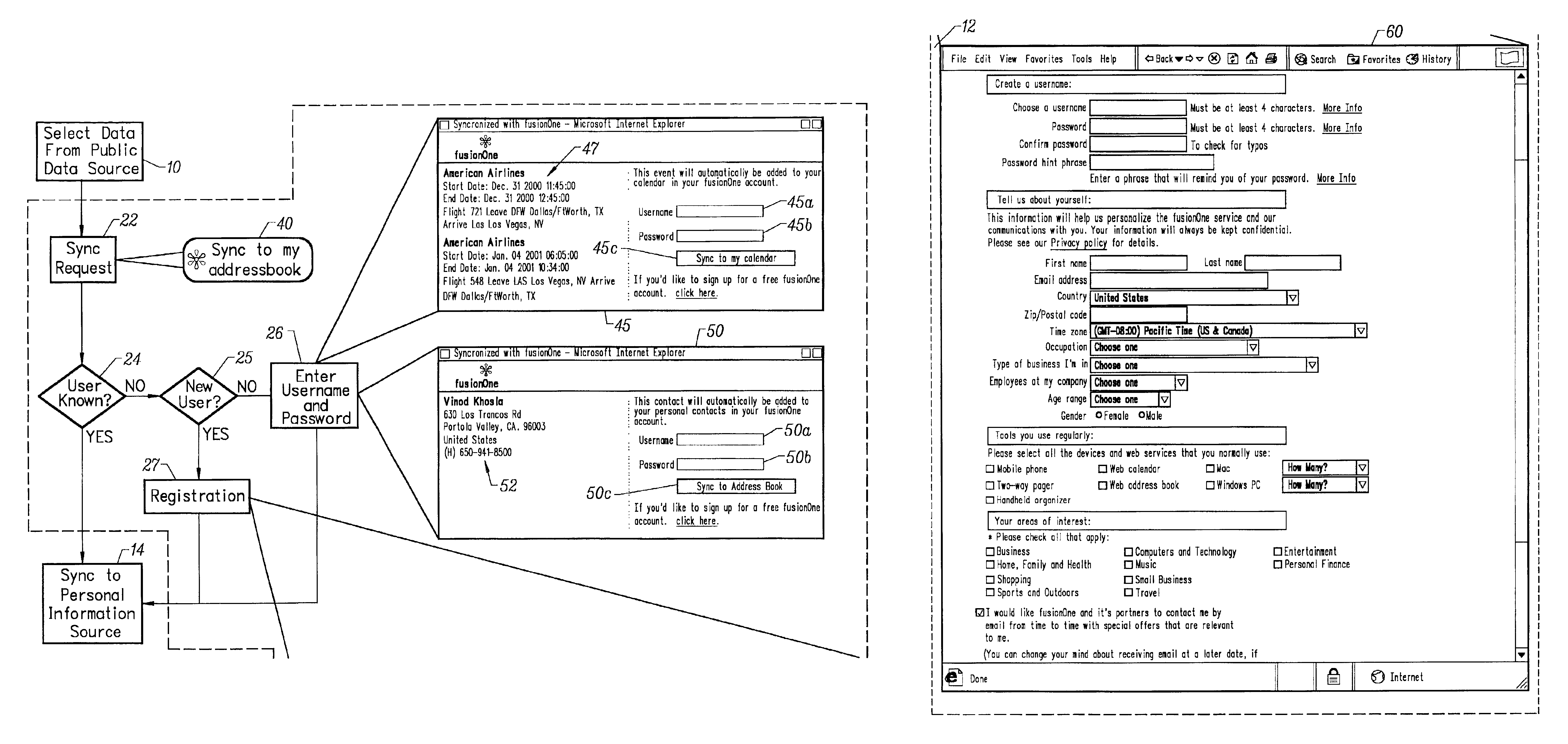
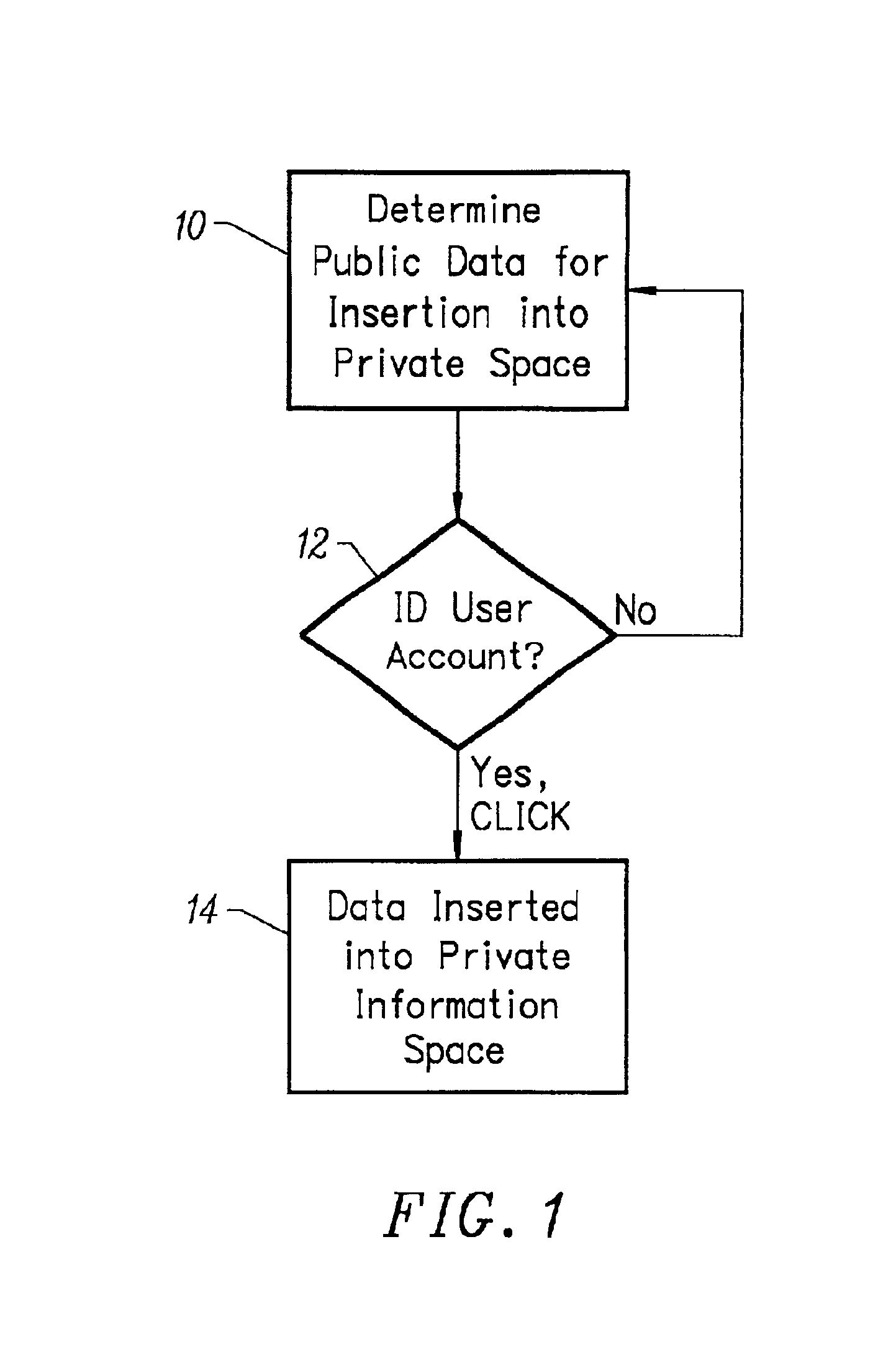
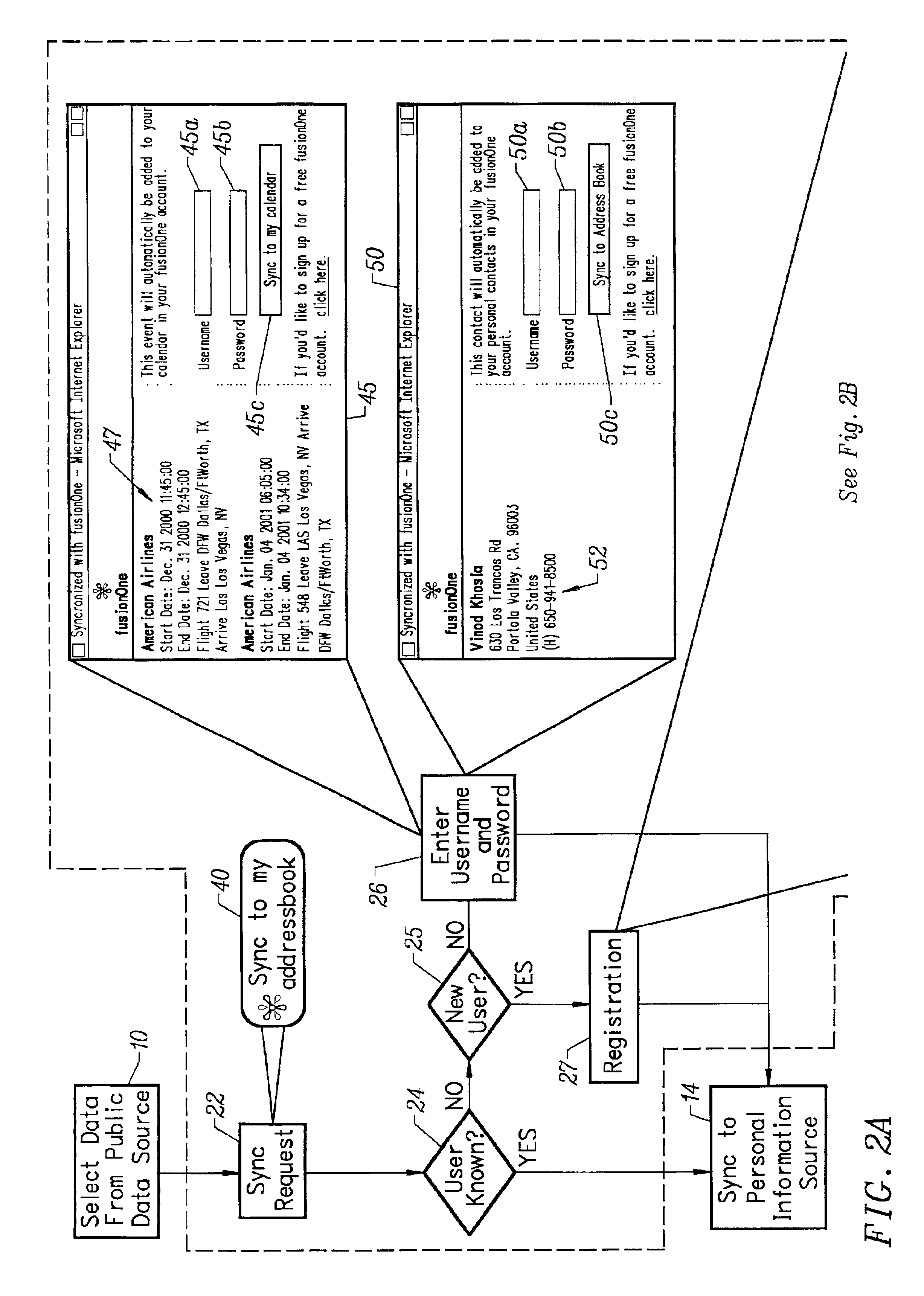
Single click synchronization of data from a public information store to a private information store
InactiveUS6944651B2Multiple digital computer combinationsWeb data navigationInformation spaceWeb site
A method for transferring public information to a private information store maintained by a private information space manager. The method may include the steps of selecting public information from a public information source; initiating a sync request by selecting a sync request button on the public information web site; and identifying the private information space were the public information is to be stored. In a further aspect, the invention comprises a system for synchronizing public content from a public information web site to a private information store. The system may include a sync enable button on the public information web site; a pop-up window provided by a private information store provided responsive to the sync enable button on the public information web site; and a sync interface transfer button on the pop-up window initiating transfer of the public information to the private information store. In a further aspect, the public information web site is provided by an affiliate server and said affiliate server includes code enabling said sync button by directing a client web browser to the private information store provider. The system may further include at least one synchronization routine synchronizing the public information data with the private information space.
Owner:SYNCHRONOSS TECH
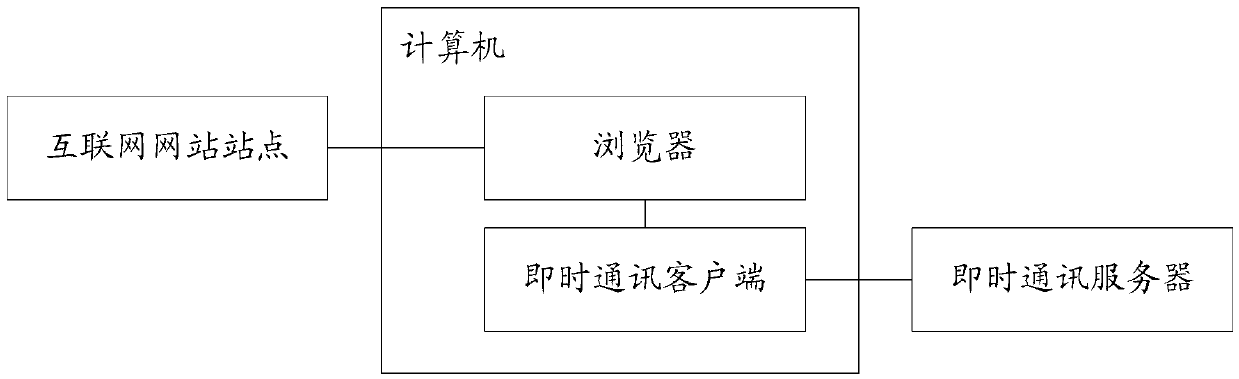
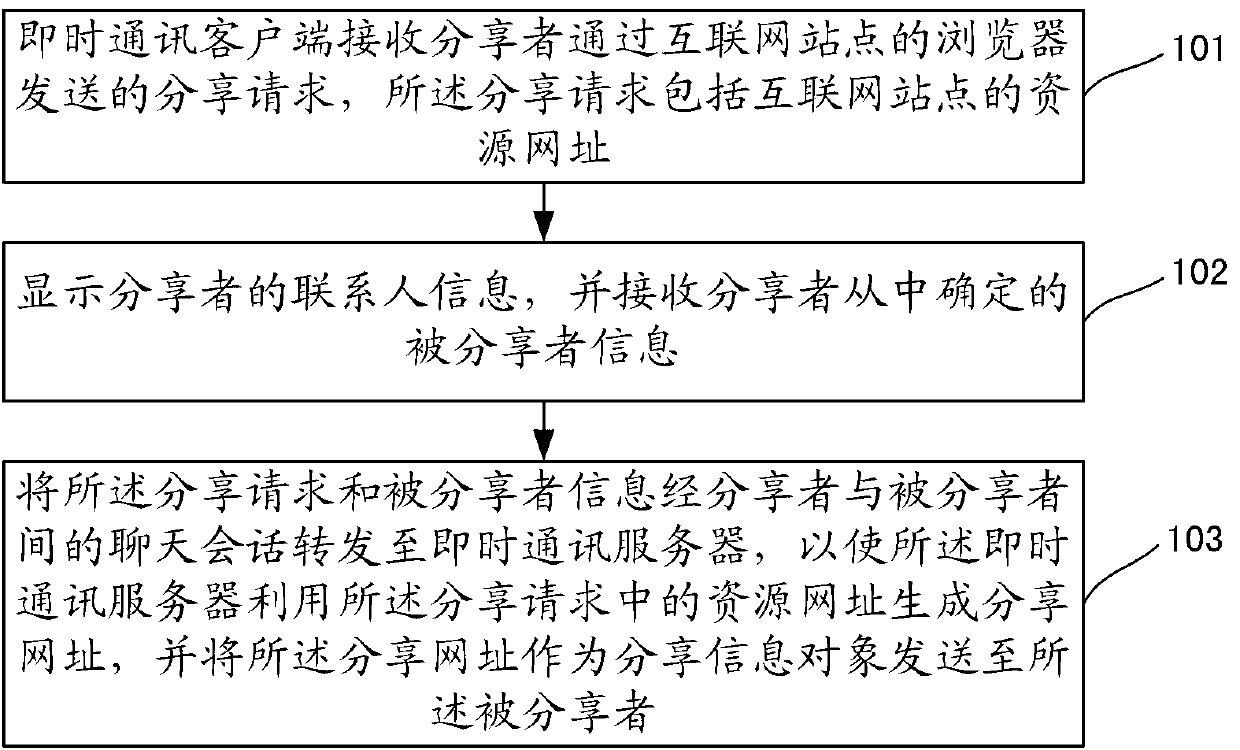
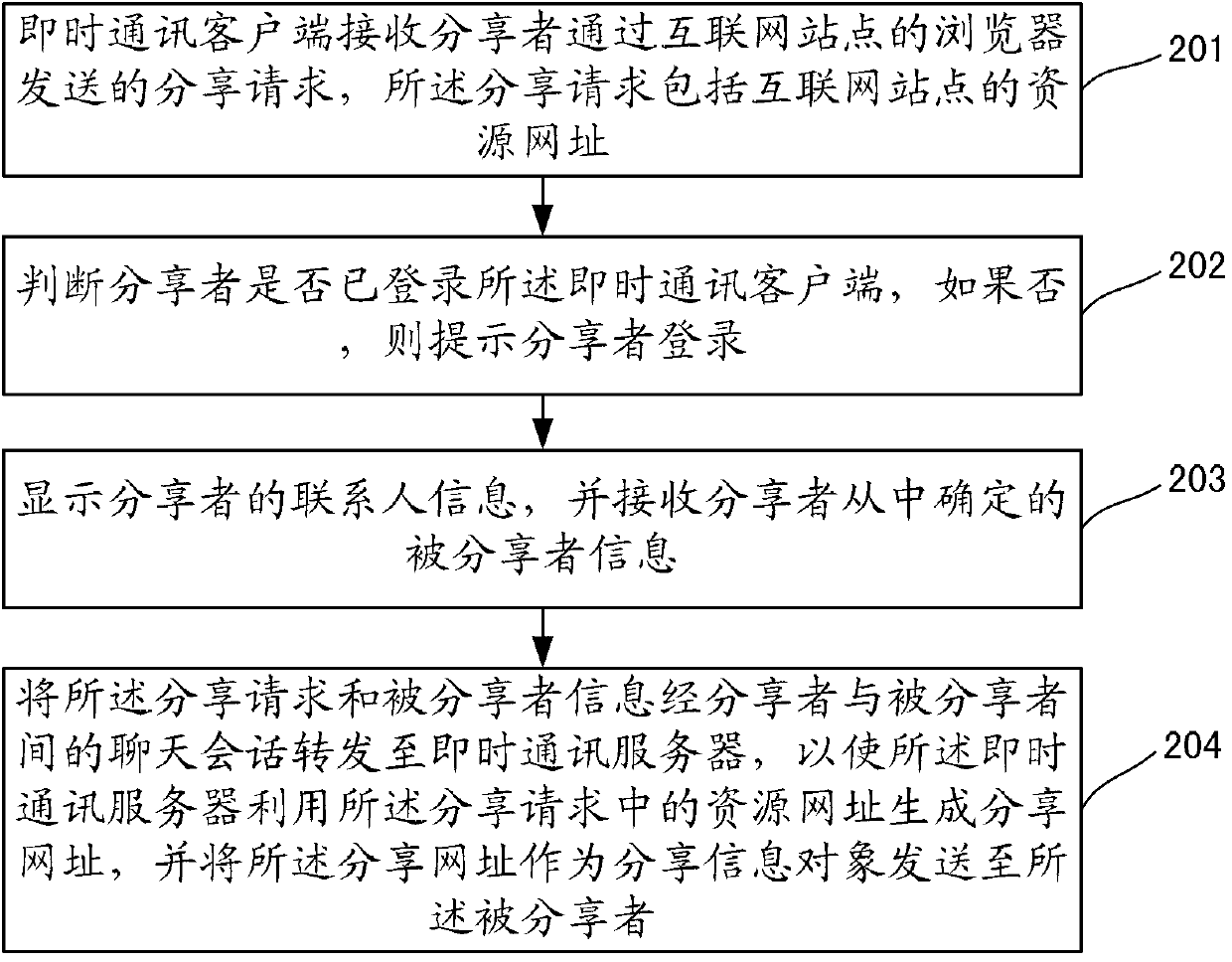
Information sharing method and system and instant messaging (IM) client and server
The invention provides an information sharing method and a system and an IM client and a server. The method includes that the IM client receives sharing requests sent by a sharer through a browser of a web site, wherein the sharing requests comprise resource websites of the web site; contact information of the sharer is displayed, and shared person information determined by the sharer is received; the sharing requests and the shared person information are transmitted to the IM server through a chat conversation between the sharer and the shared person, so that the IM server generates a sharing website by using the resource websites in the sharing requests, and the sharing website serves as a sharing information object to be sent to the shared person. The information sharing method and the system and the IM client and the server aim to provide a novel information sharing scheme, and further, statistics of sharing page views, tracking of information transmission paths, monitoring of user access behaviors and the like are achieved on the basis of the scheme.
Owner:HUAWEI TECH CO LTD
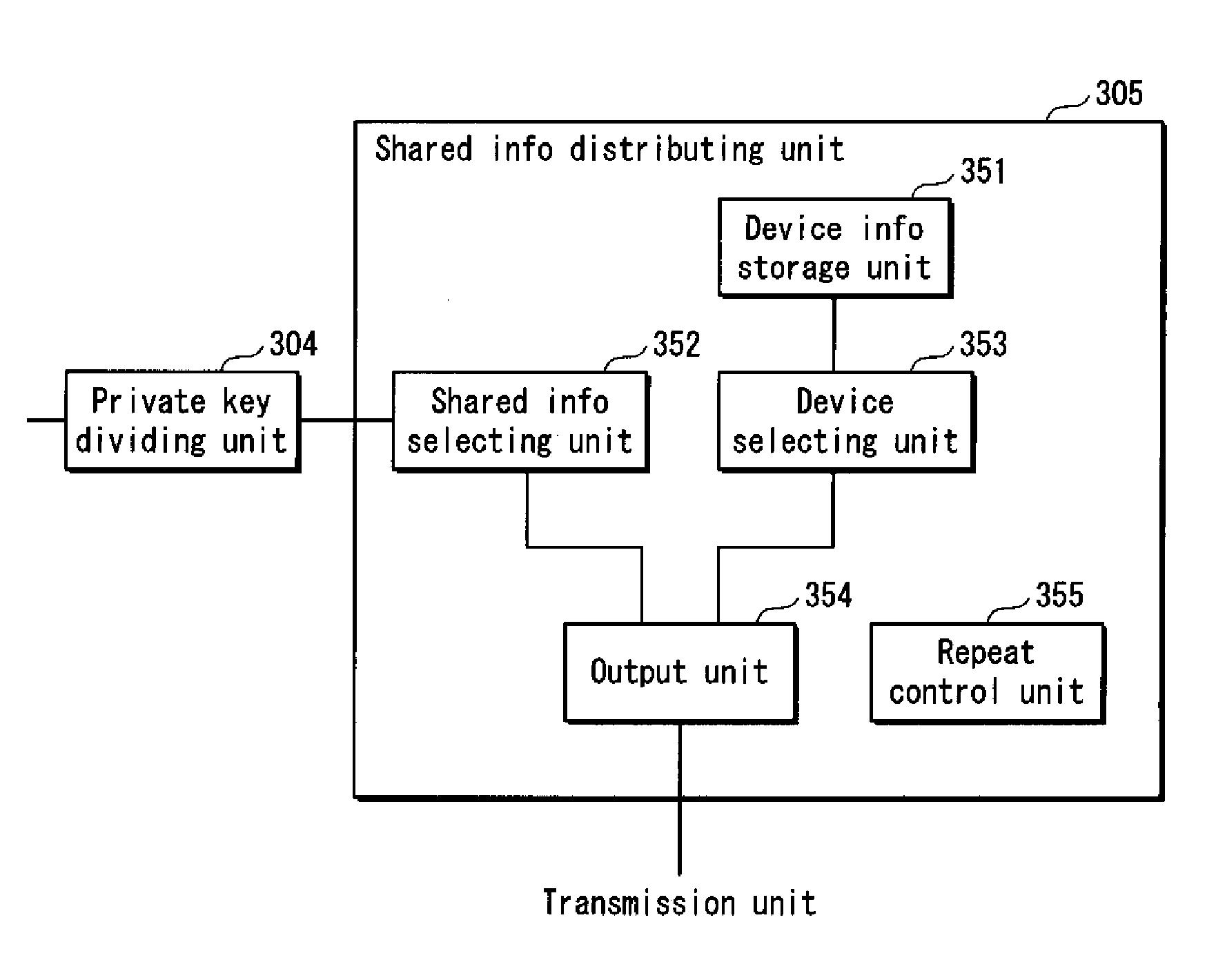
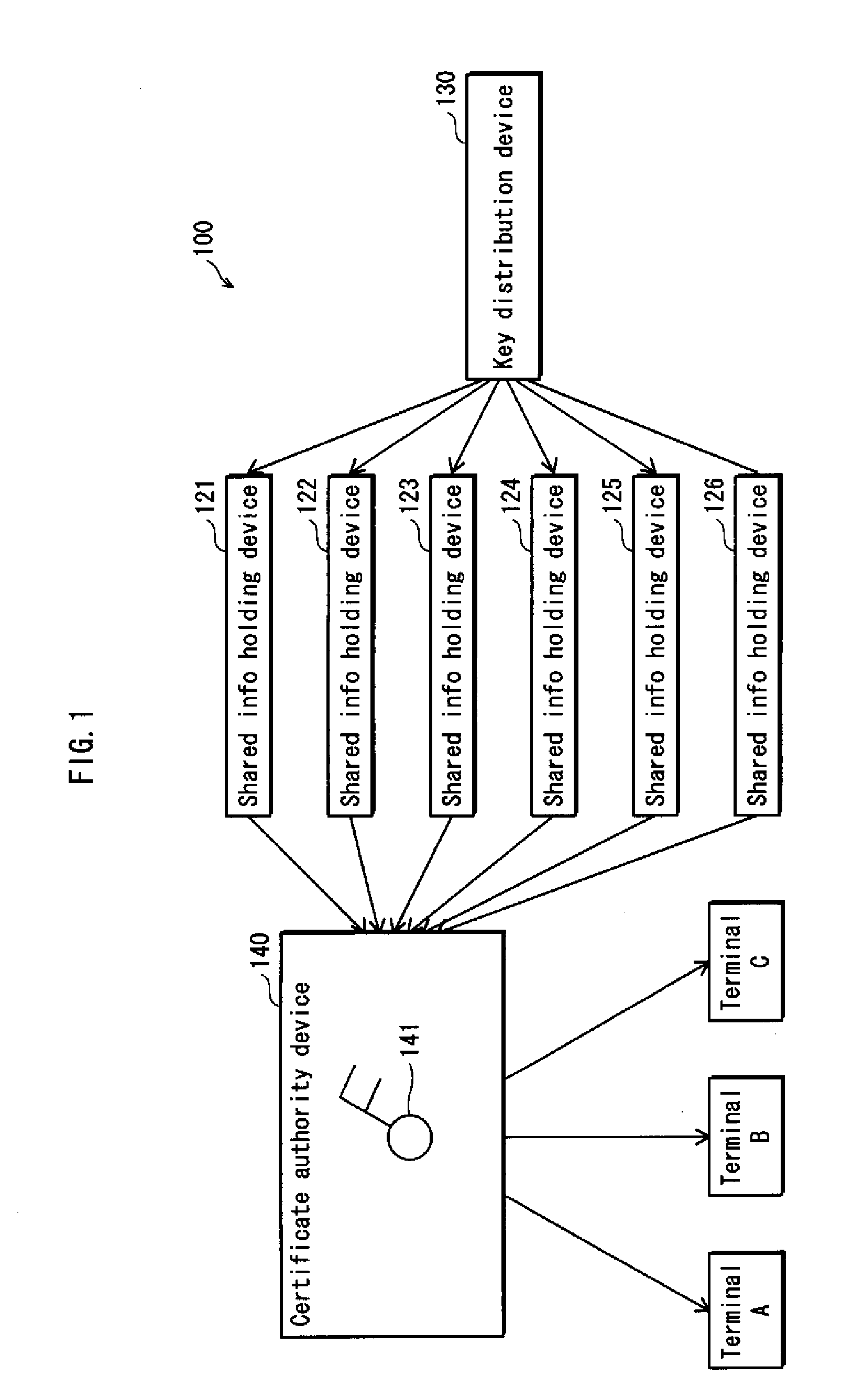
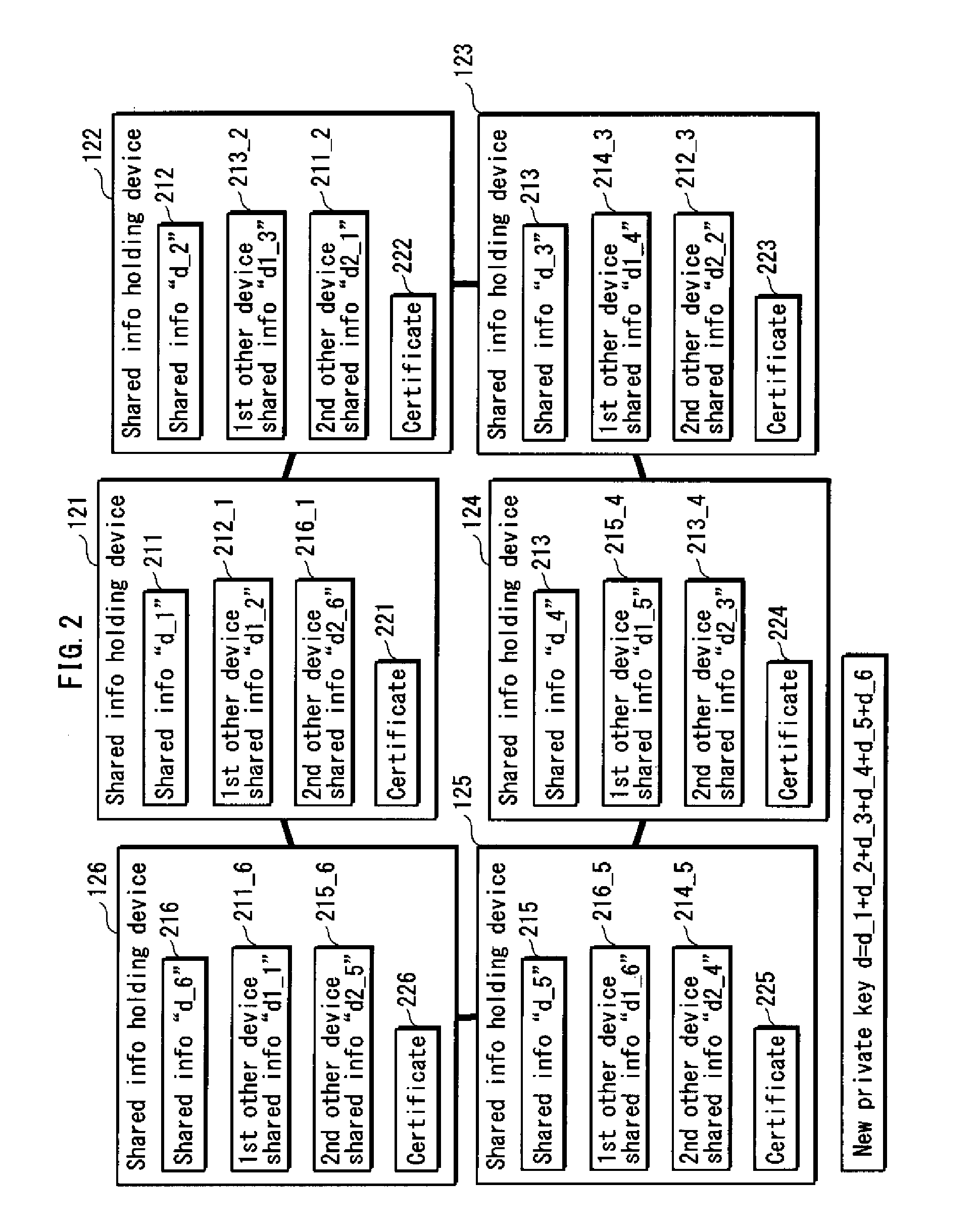
Shared information distributing device, holding device, certificate authority device, and system
ActiveUS20100235588A1Increase redundancySure easyMemory adressing/allocation/relocationSecuring communicationCertificate authorityComputer security
A distributing device for generating private information correctly even if shared information is destroyed or tampered with. A shared information distributing device for use in a system for managing private information by a secret sharing method, including: segmenting unit that segments private information into a first through an nth pieces of shared information; first distribution unit that distributes the n pieces of shared information to n holding devices on a one-to-one basis; and second distribution unit that distributes the n pieces of shared information to the n holding devices so that each holding device holds an ith piece of shared information distributed by the first distribution unit, as well as a pieces of shared information being different from the ith piece of shared information in ordinal position among n pieces of shared information, “i” being an integer in a range from 1 to n.
Owner:PANASONIC CORP
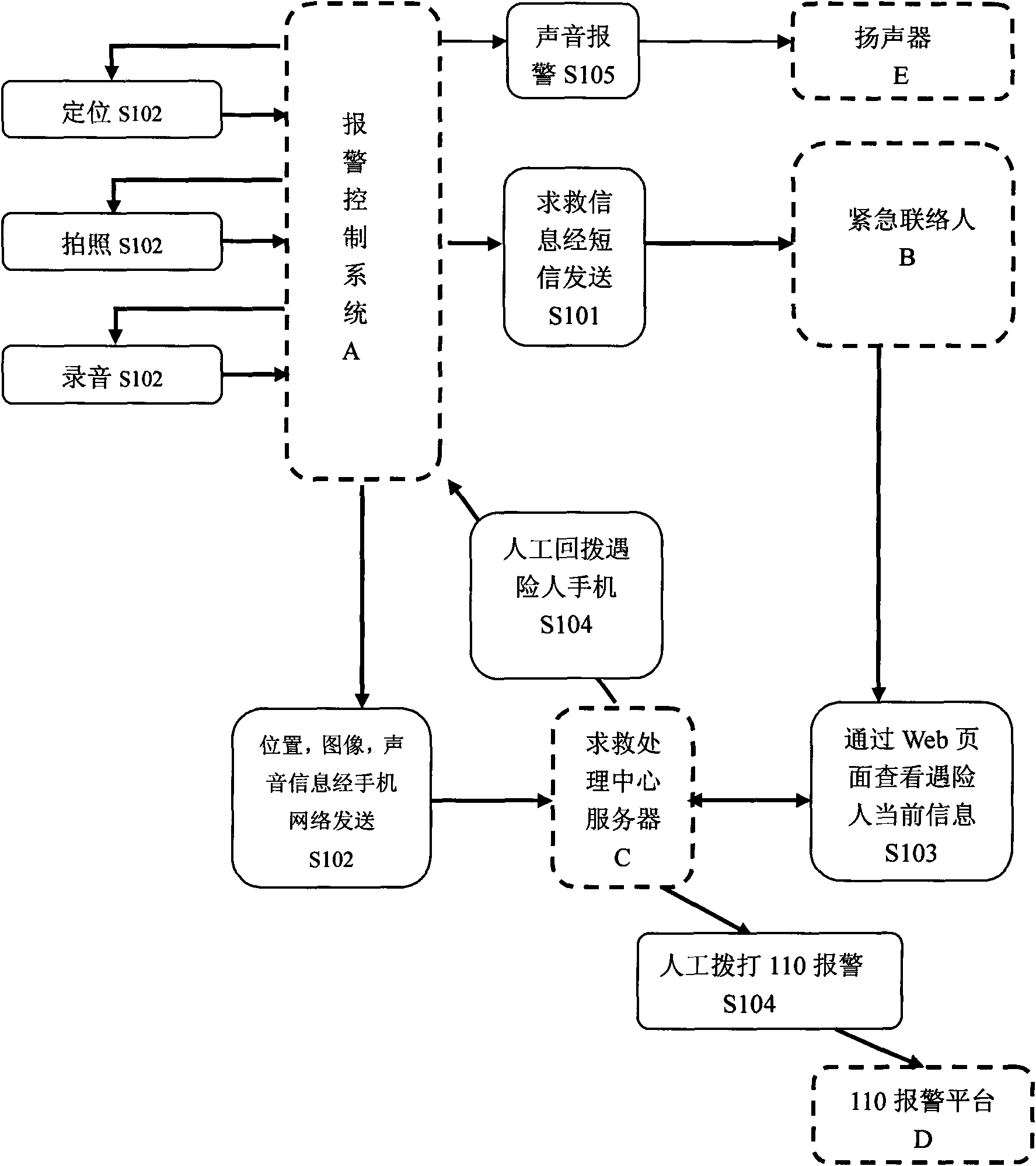
Method for seeking help by phone and phone system thereof
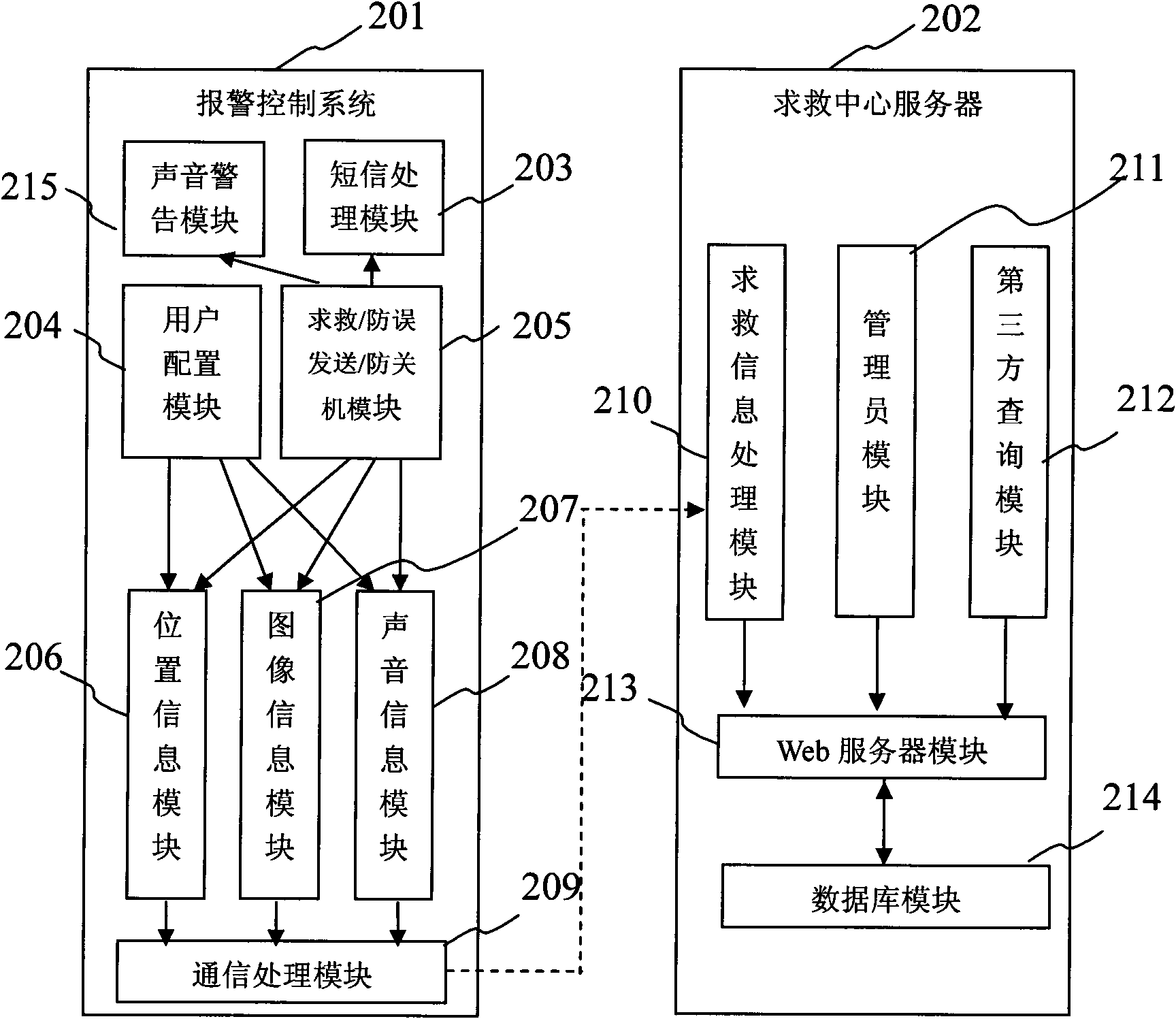
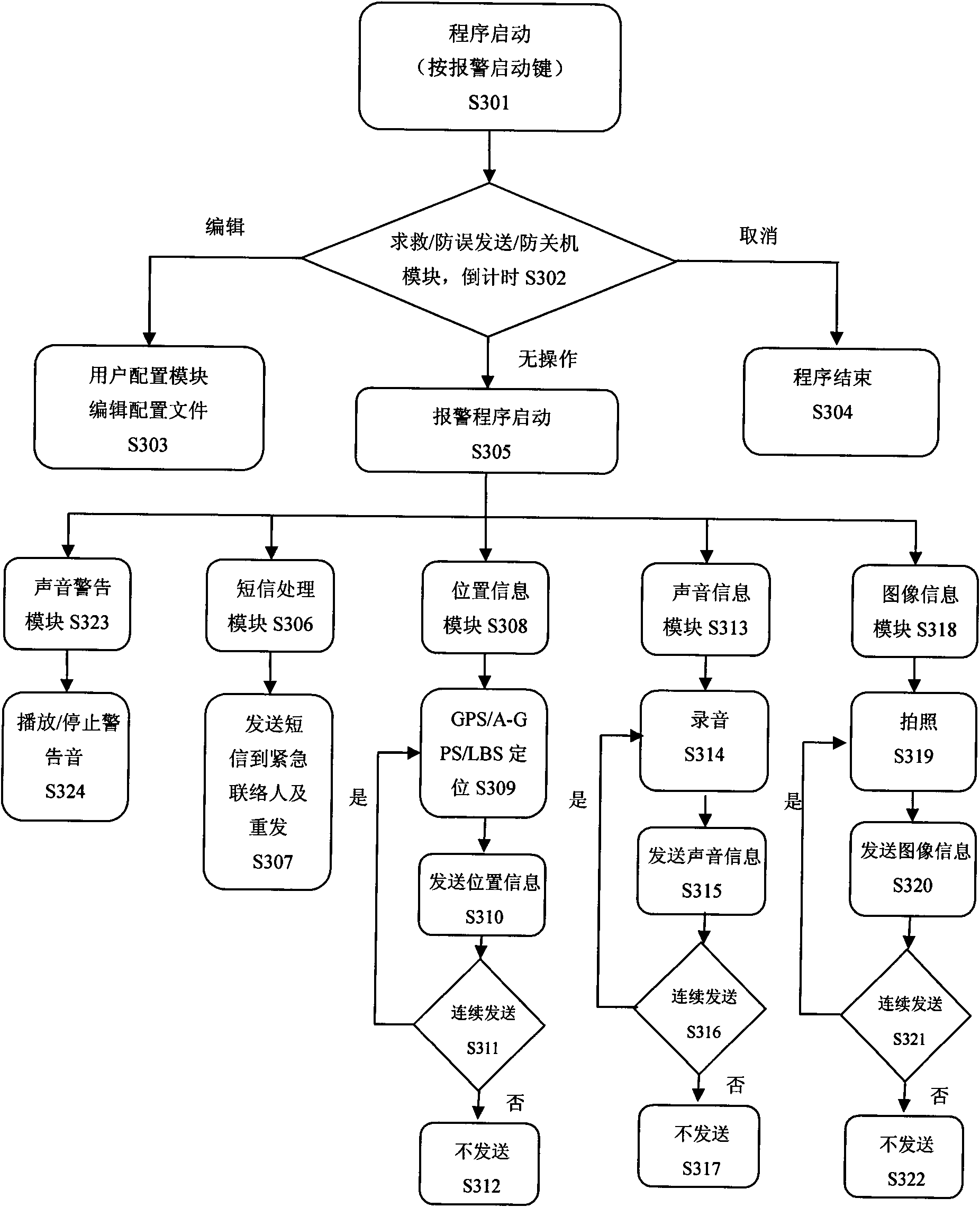
ActiveCN101616357AEasy to solvePrecise positioningMessaging/mailboxes/announcementsAlarmsControl systemInformation Harvesting
The invention provides a method for seeking help by a phone and a phone system thereof. The method comprises the following steps: when encountering such emergencies such as danger, a user presses down a warning start key on the phone to start a warning control system installed inside the phone to send short messages for seeking help to a preset emergency contact person; the warning control system controls the phone to collect the current position, image and acoustic information of the person at risk and sends the above collected information to a server of a remote help processing center via the existing phone network; after receiving the short messages for seeking help, the emergency contact person enters a website on which the information of the person at risk is stored on the server of the help processing center and check the information sent by the phone of the person at risk. The invention realizes exact positioning, rapid help seeking, instant case information collecting and sending when the user is in danger, thus providing guarantees for safety of phone users and case solving by tracking.
Owner:TAIZHOU PINGAN INFORMATION TECH
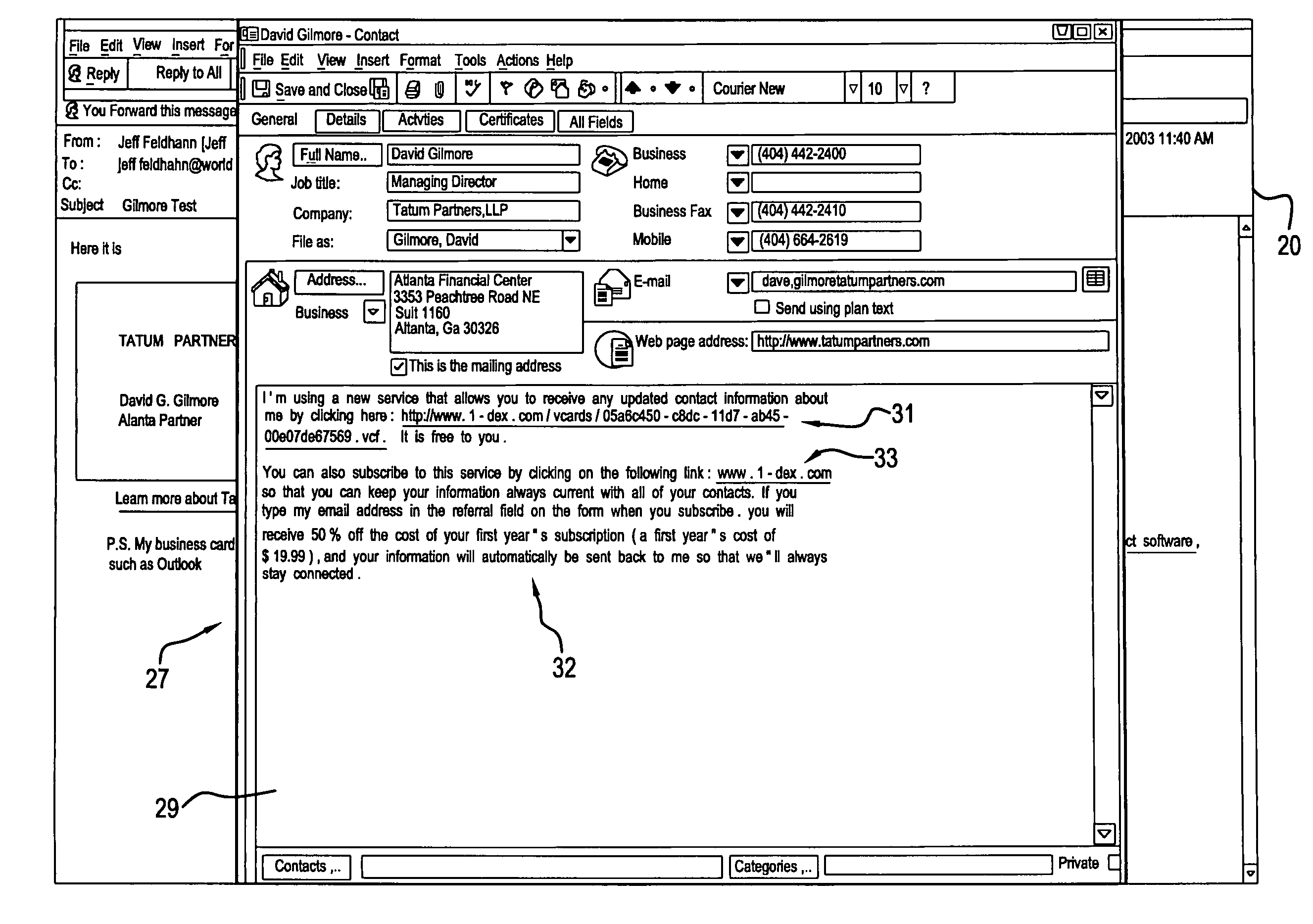
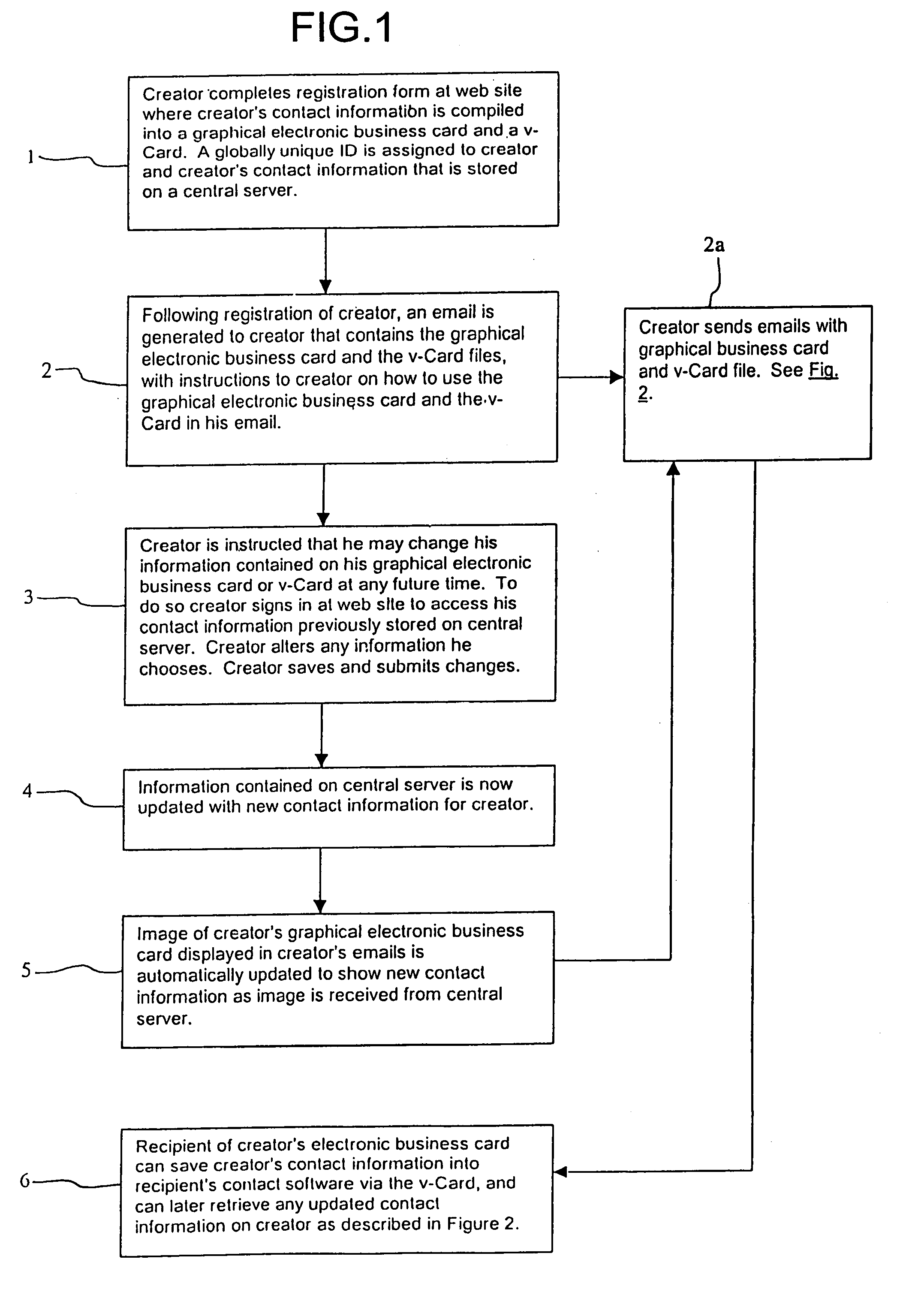
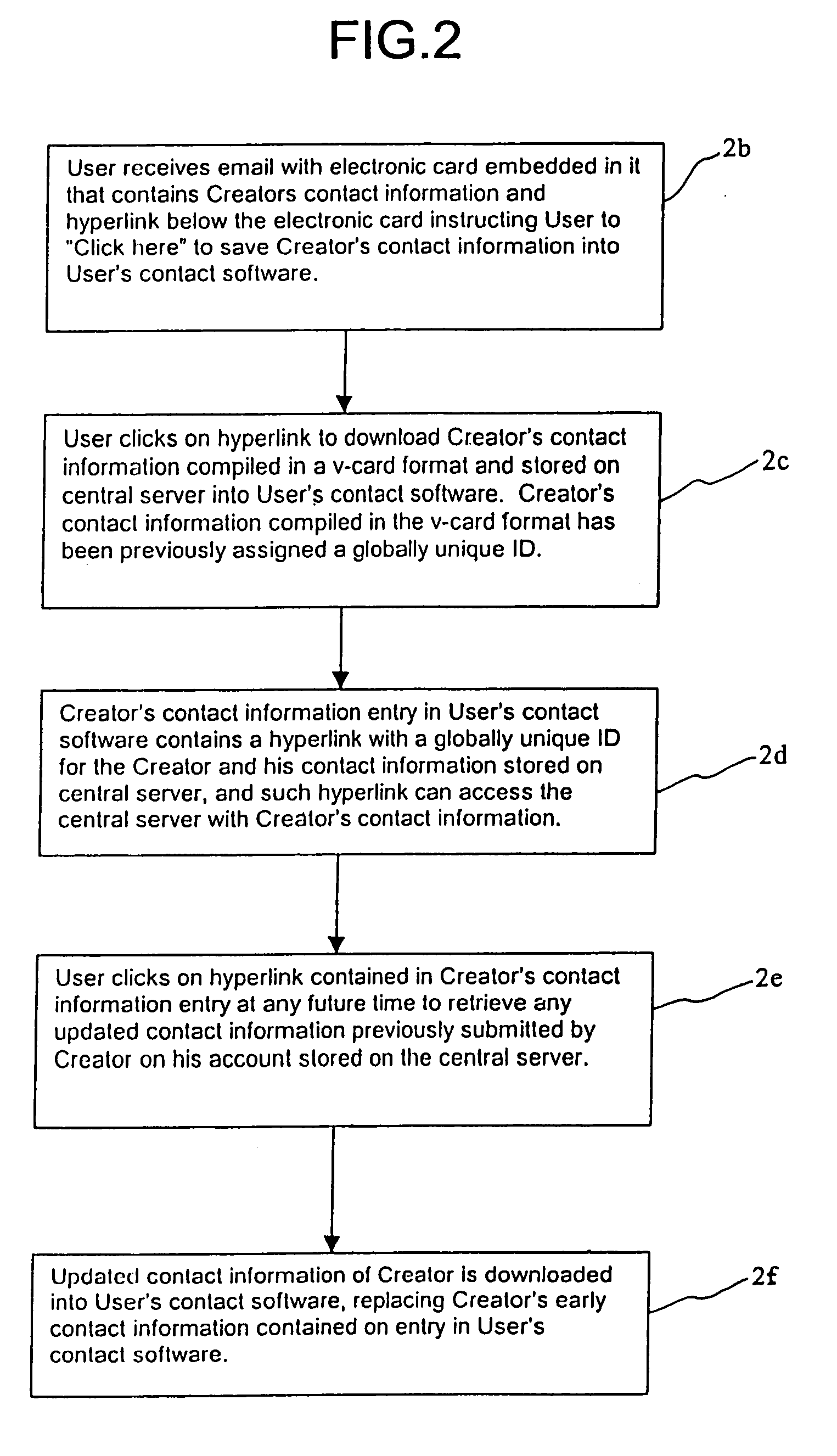
Method and system for updating electronic business cards
InactiveUS7246099B2Simple methodPayment architectureSpecial data processing applicationsDatabaseSoftware
The present invention provides a method and system that allows individuals to maintain current contact information in another individual's contact software without having to individually notify the receiving individual or manually resend the updated contact information to the individual. The invention does this by utilizing an existing platform for the distribution of static contact information (the v-Card platform), and through the means of storing static contact information for an individual on a central server and then assigning a globally unique ID to the individual and his information. The invention includes in the static contact information created by an individual, a dynamic link containing a creator's globally unique ID that may be utilized by recipients of the contact information to retrieve updated contact information at any future time.
Owner:FELDHAHN JEFFREY M
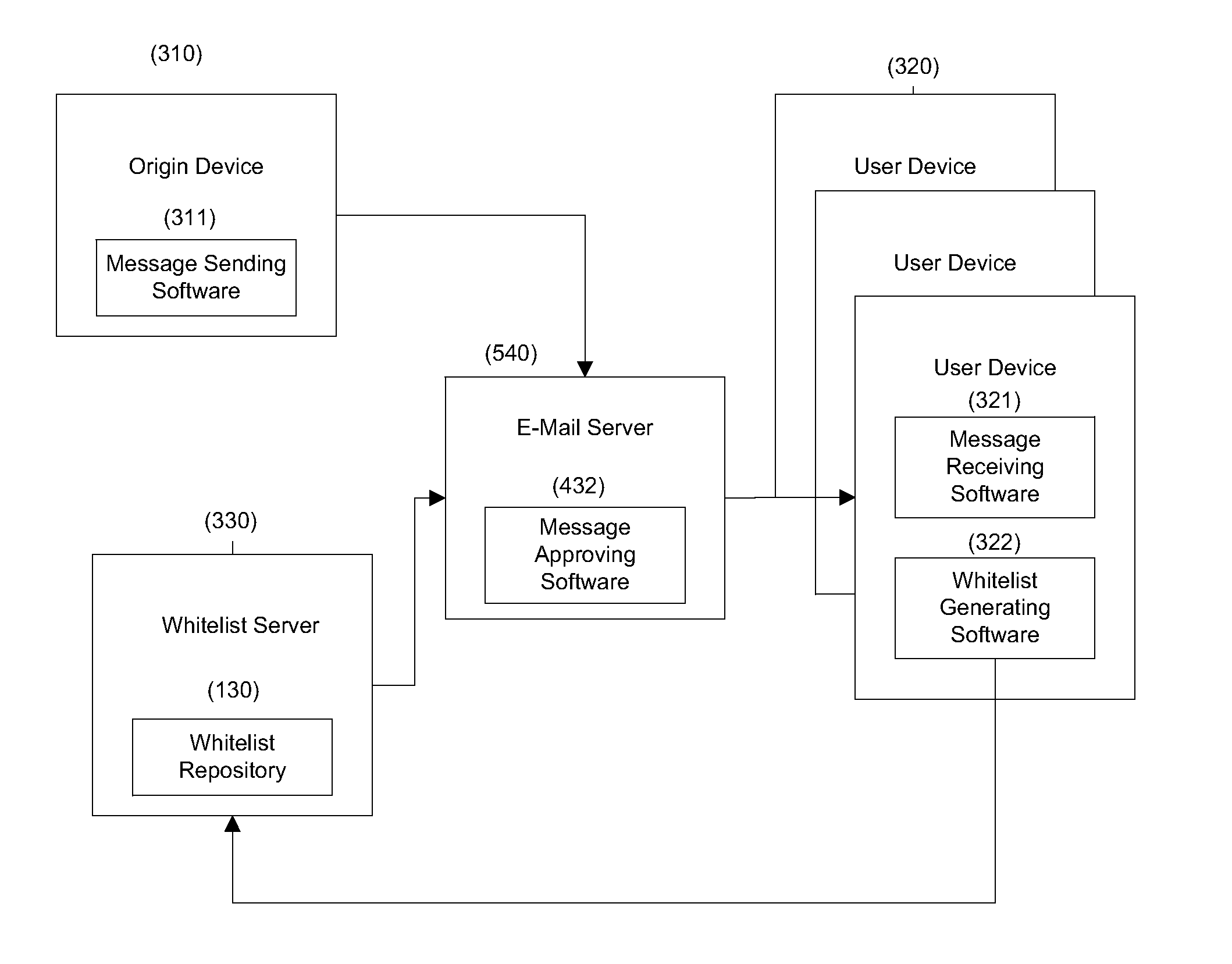
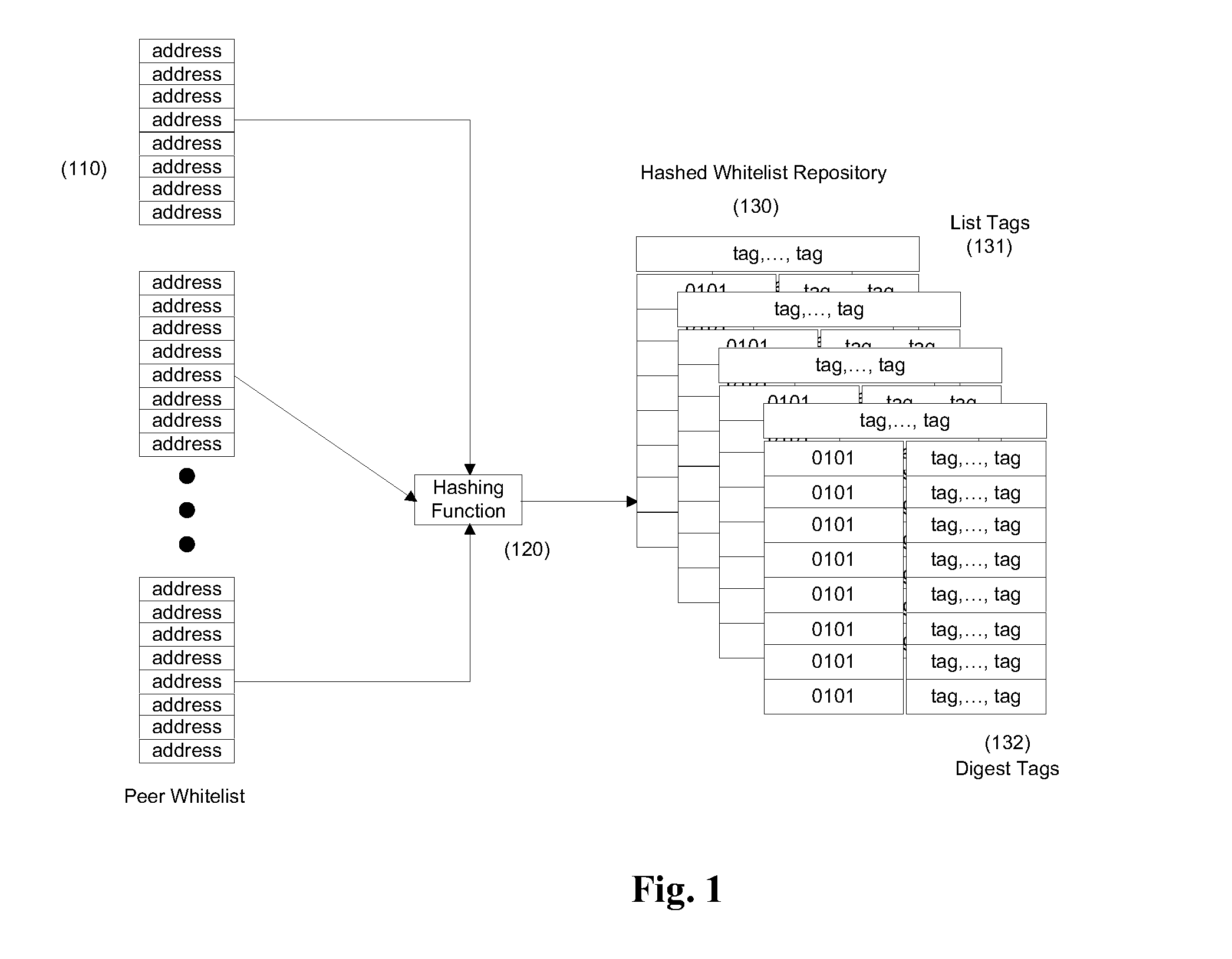
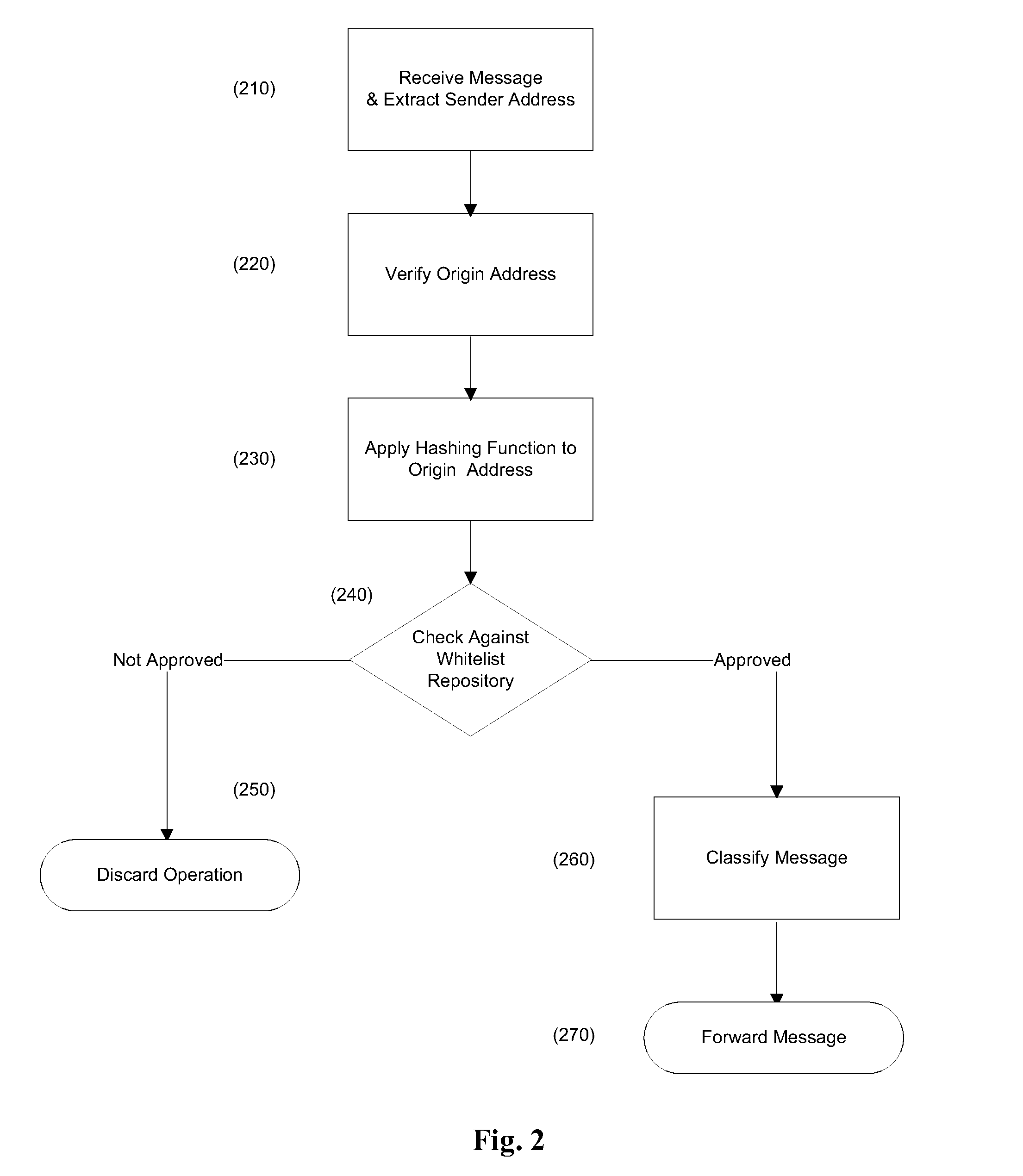
Method and system for sharing trusted contact information
InactiveUS20110113249A1User identity/authority verificationData switching networksWhitelistEncryption
A method and system for sharing trusted contact information between trusted, known and unknown parties, without revealing the contact information itself, thus protecting the party defined in the contact from possible unsolicited messages known as “Spam”. Addresses of trusted senders are encrypted using a one-way encryption and stored in a whitelist repository that can be shared by different users. When a message is received, its senders address is extracted, encrypted using the same encryption method, and compared if it is found in the whitelist repository.
Owner:GELBARD ROY +1
Video customized to include person-of-interest
InactiveUS20090153654A1Increasing customization optionAdd optionsTelevision system detailsElectronic editing digitised analogue information signalsComputer graphics (images)Video sequence
One or more input video sequences and a set of person-of-interest (“POI”) information are received. The set of POI information identifies at least one person-of-interest. A particular video sequence is identified that prominently or relatively prominently displays at least the person-of-interest. The particular video sequence is identified from (a) the input video sequence(s), or (b) a portion of the input video sequence, if only one was received, or a portion of one of the input video sequences, if more than one was received. Then, a customized output video is generated from at least a portion or portions of the input video sequence(s), the customized output video being generated based at least upon the set of POI information to include at least the particular video sequence.
Owner:EASTMAN KODAK CO
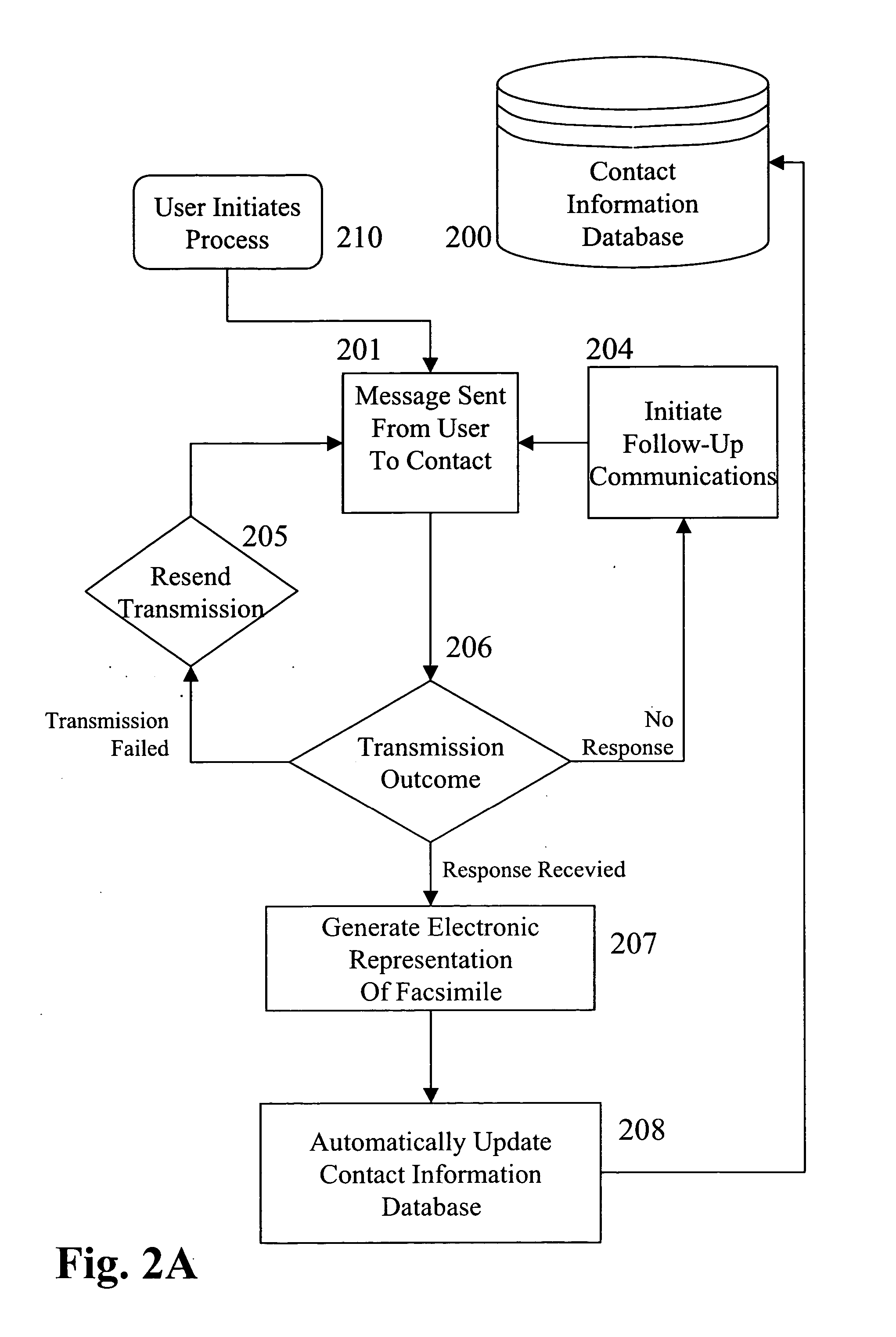
Method and system for automatically updating contact information within a contact database
InactiveUS20070150542A1Multiple digital computer combinationsElectric digital data processingData miningData library
Owner:MYLIFE COM
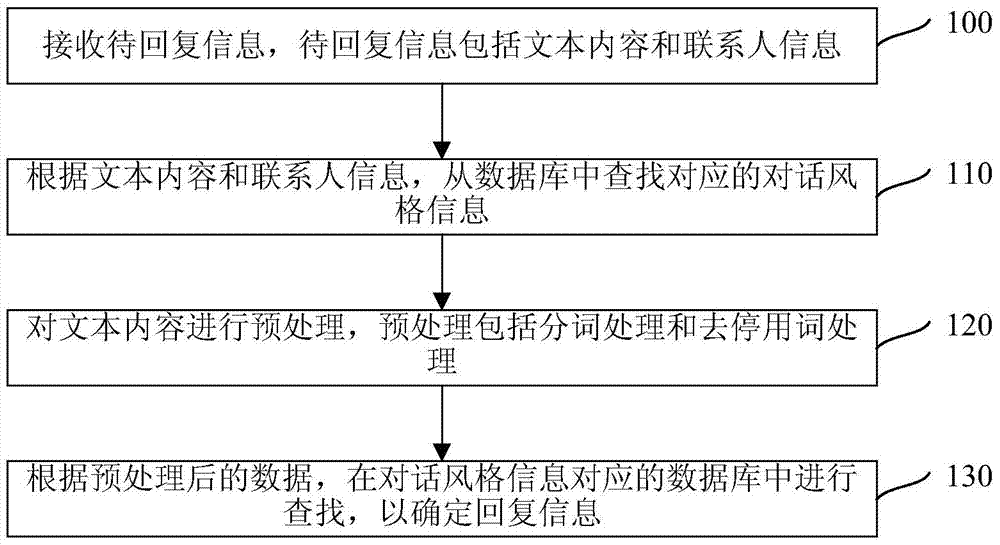
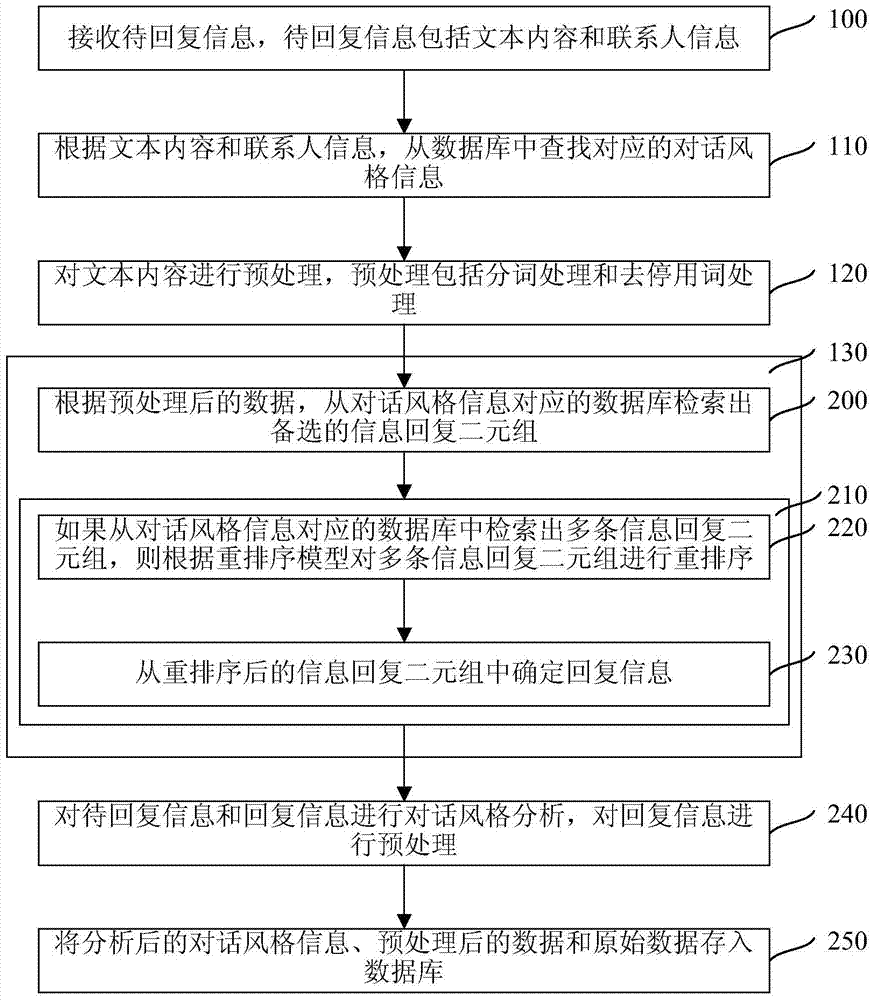
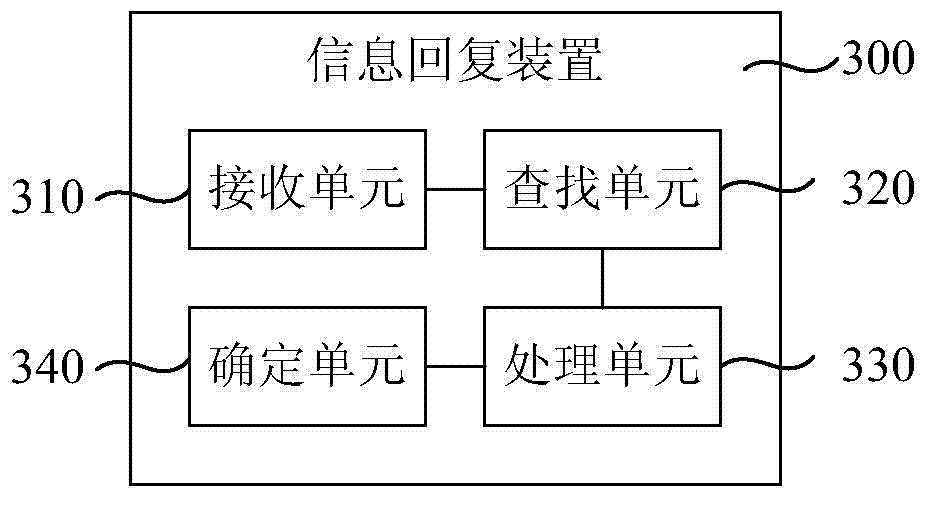
Information returning method and device
ActiveCN104750705AShorten the timeImprove experienceWeb data indexingMachine learningWorld Wide WebData mining
The present invention relates to an information reply method and an apparatus, wherein the information reply method comprises: receiving information to be replied, wherein the information to be replied comprises text content and contact information; based on the text content and the contact information, querying corresponding dialog style information from a database; performing preprocessing on the text content, wherein the preprocessing comprises segmentation processing and stop word removal processing; and based on data after the preprocessing, performing query in a database corresponding to the dialog style information so as to determine reply information. A dialog style is determined through the information to be replied and the proper reply information is queried in the database corresponding to the dialog style based on the data after the preprocessing for a user to select, which can shorten time for the user to reply information and improve user experience.
Owner:HUAWEI TECH CO LTD
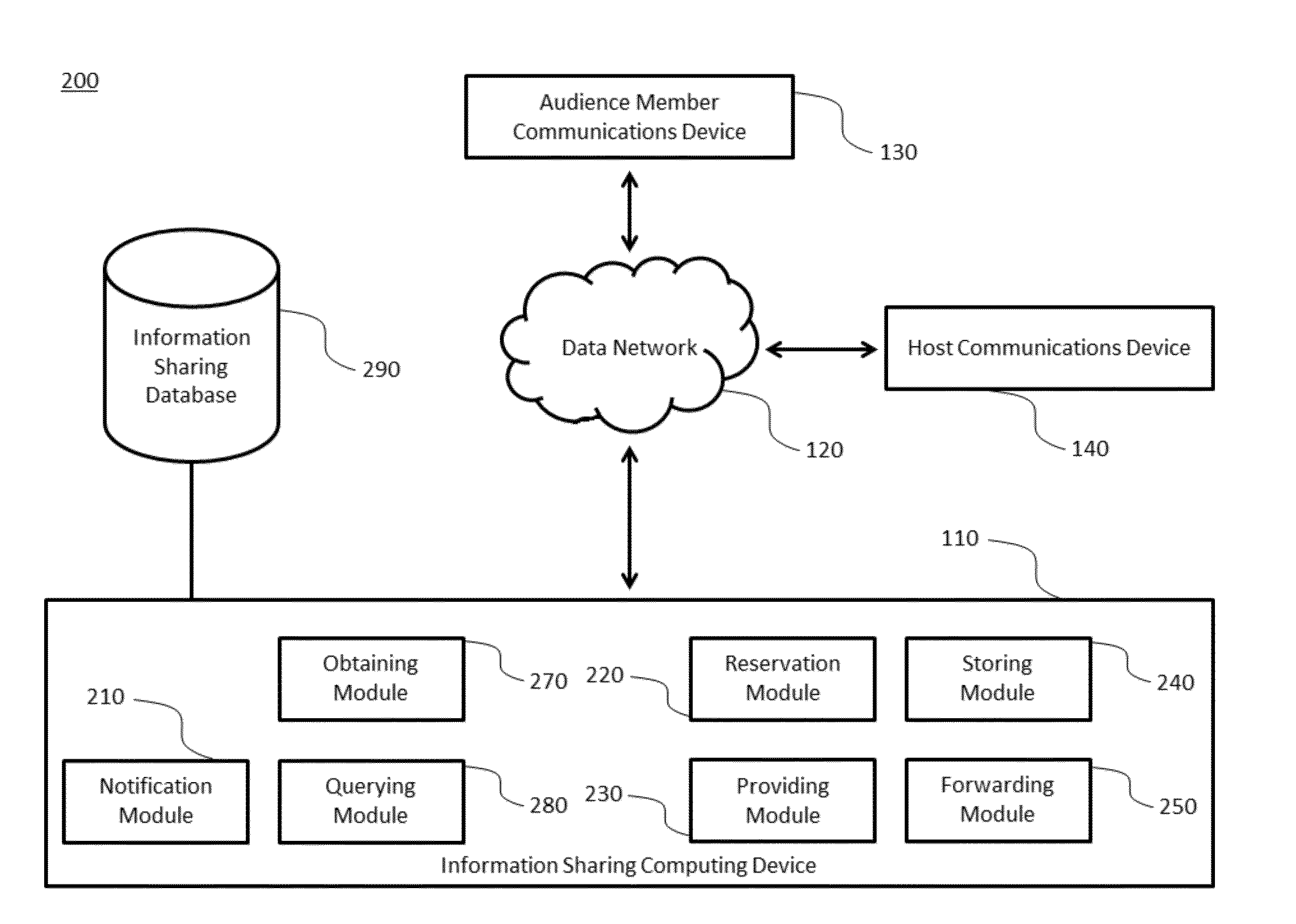
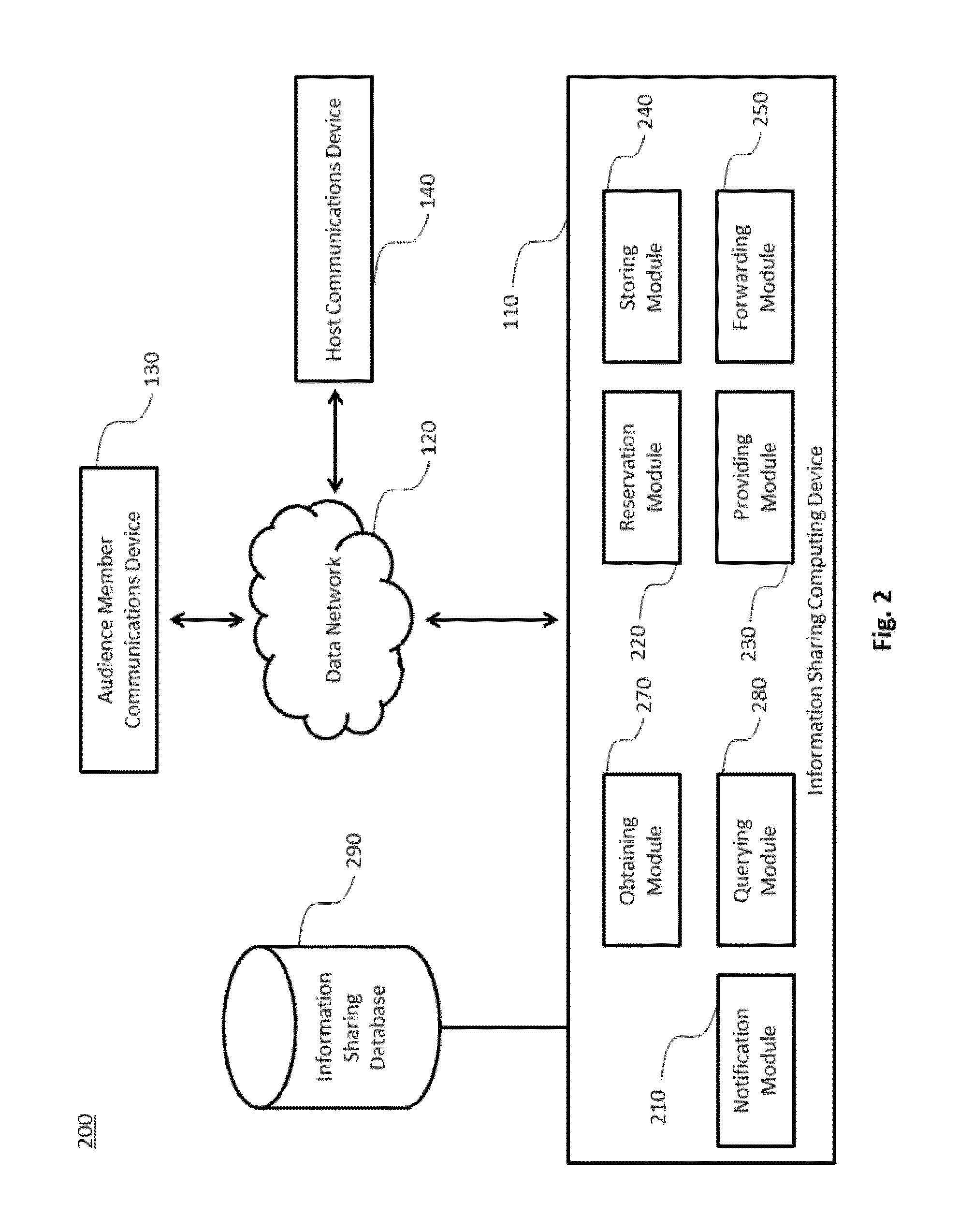
Information sharing between a host and an audience
InactiveUS20150081734A1Digital data processing detailsOffice automationInformation sharingCommunication device
A system for sharing information from a host to an audience based on a keyword that links the host to the audience includes a processor and a memory coupled with the processor, where the memory includes instructions that when executed by the processor, cause the processor to: (a) obtain host information from a host communications device for an information sharing service, wherein the information sharing service includes an interface for sharing information between the host and the audience; (b) reserve a host keyword associated with the host information; (c) store the host information associated with the host keyword in an information sharing database associated with the information sharing service; (d) receive, by the information sharing service, a keyword matching the host keyword from an audience member communications device via a data network; (e) prompt, by the information sharing service, the audience member communications device to provide audience member contact information; (f) query the information sharing database for the host information when an audience member communications device provides the matching keyword and the audience member contact information to the information sharing service; and (g) provide the host information to the audience member communications device via the information sharing service
Owner:FERN EXPOSITION SERVICES LLC
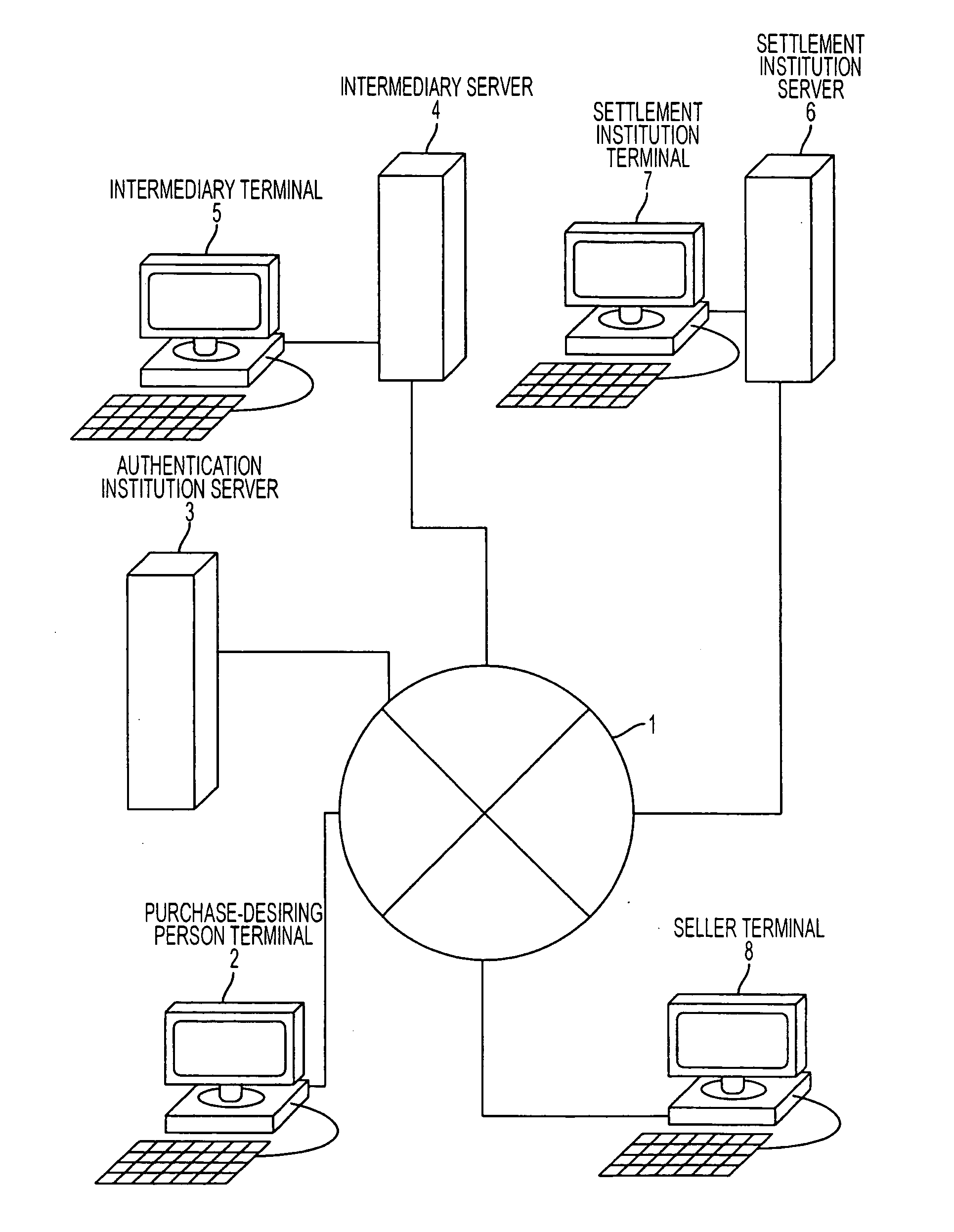
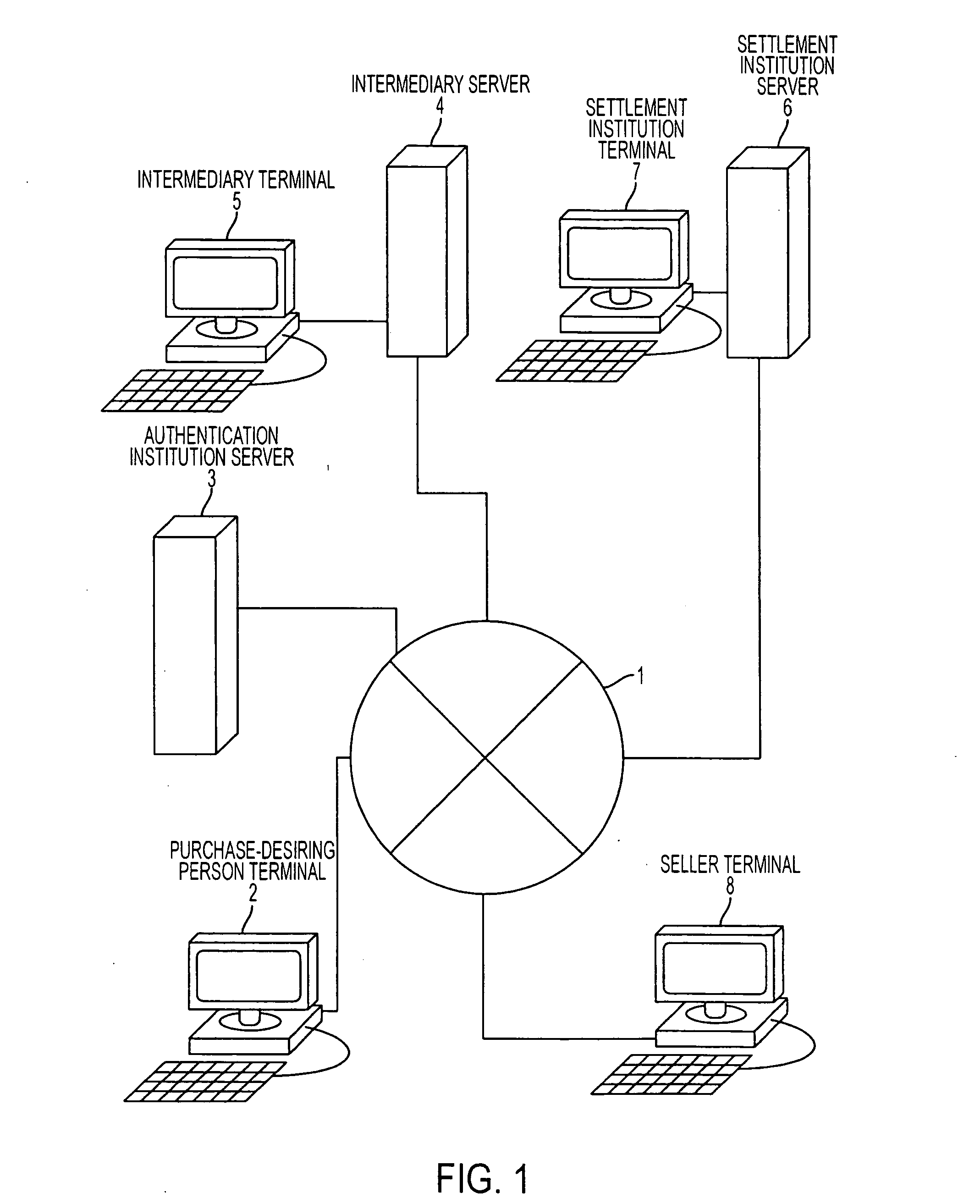
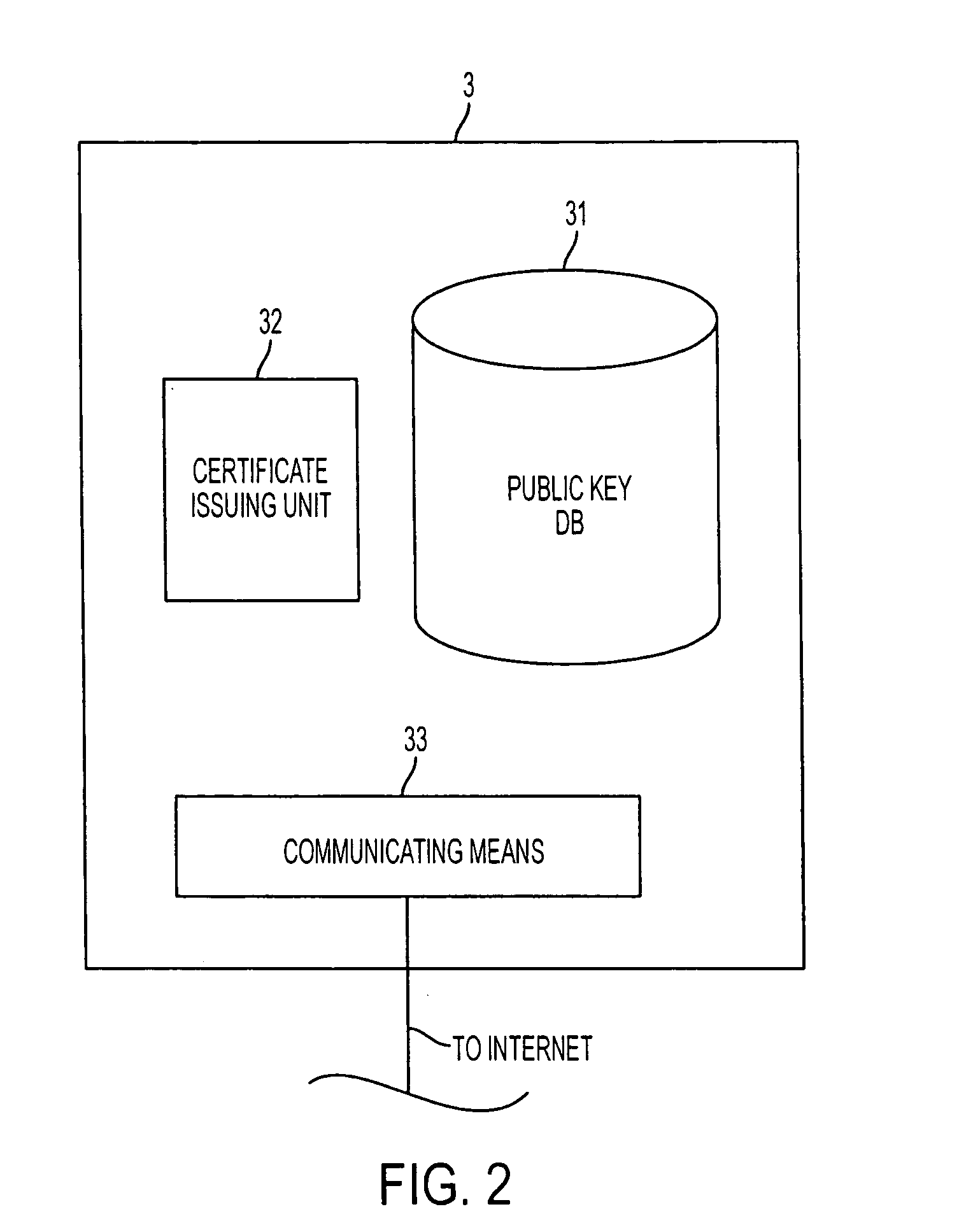
Personal information verification program, method and apparatus
InactiveUS20070145123A1User identity/authority verificationComputer security arrangementsPaymentComputer terminal
A personal information verification system using an intermediary server and a settlement institution server, where personal information with an electronic signature, showing a desired purchase and a first version of item hash information are received from a person terminal. Then, the intermediary server generates a second version of item hash information by hiding the purchase item and adding an electronic signature, and transmits the second version of the item hash information to the settlement institution server. The settlement institution server sends a payment bill to a seller, generates the third version of the item hash information, and transmits the third version of the item hash information together with the amended personal information. The intermediary server generates a fourth version of the item hash information and transmits the personal information and the first to fourth versions of the item hash information to the seller terminal.
Owner:FUJITSU LTD
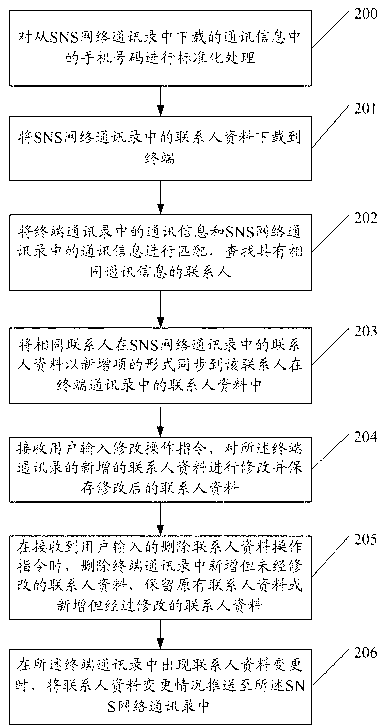
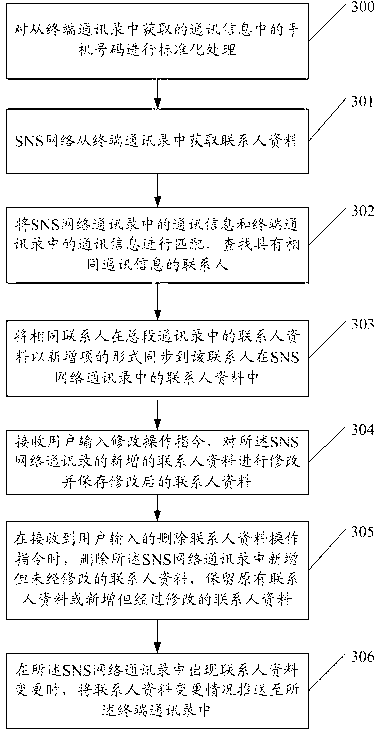
Contact data synchronization method, terminal and Social Network Site (SNS) network friends management module
InactiveCN103067427AEasy to manageDatabase distribution/replicationSubstation equipmentData synchronizationAddress book
The invention provides a contact data synchronization method, a terminal and a Social Network Site (SNS) network friend management device, wherein the contact data synchronization method includes the following steps of matching communication information of a terminal address book up with the communication information of an SNS network address book to find a contact with the same communication information, and synchronizing contact data of the contact in the terminal address book with the contact data of the contact in the SNS network address book after the contact with the same communication information is found. According to the embedment, a mutual communication between the address book in the SNS network and the address book in the terminal can be achieved and a one-stop management is achieved. The efficiency of managing contacts of a user can be improved greatly.
Owner:TENCENT TECH (SHENZHEN) CO LTD
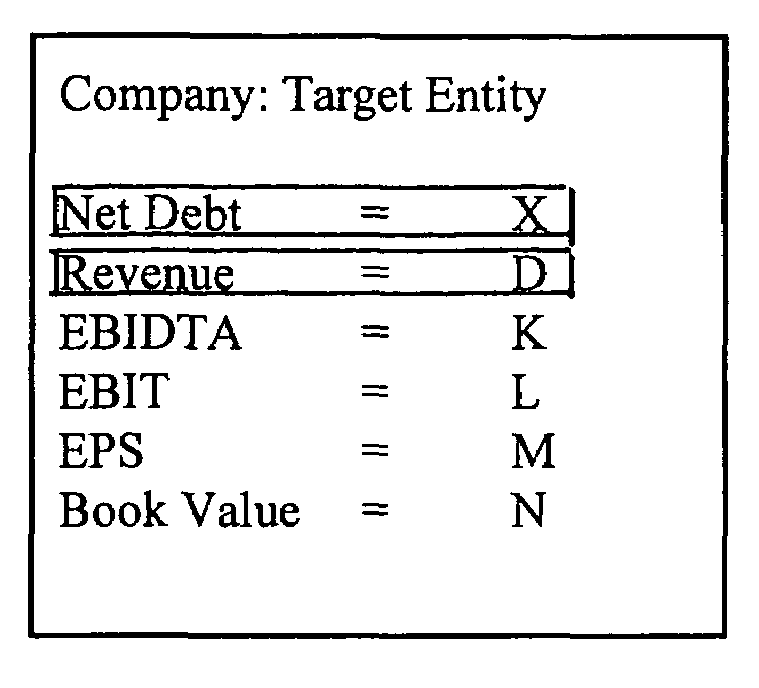
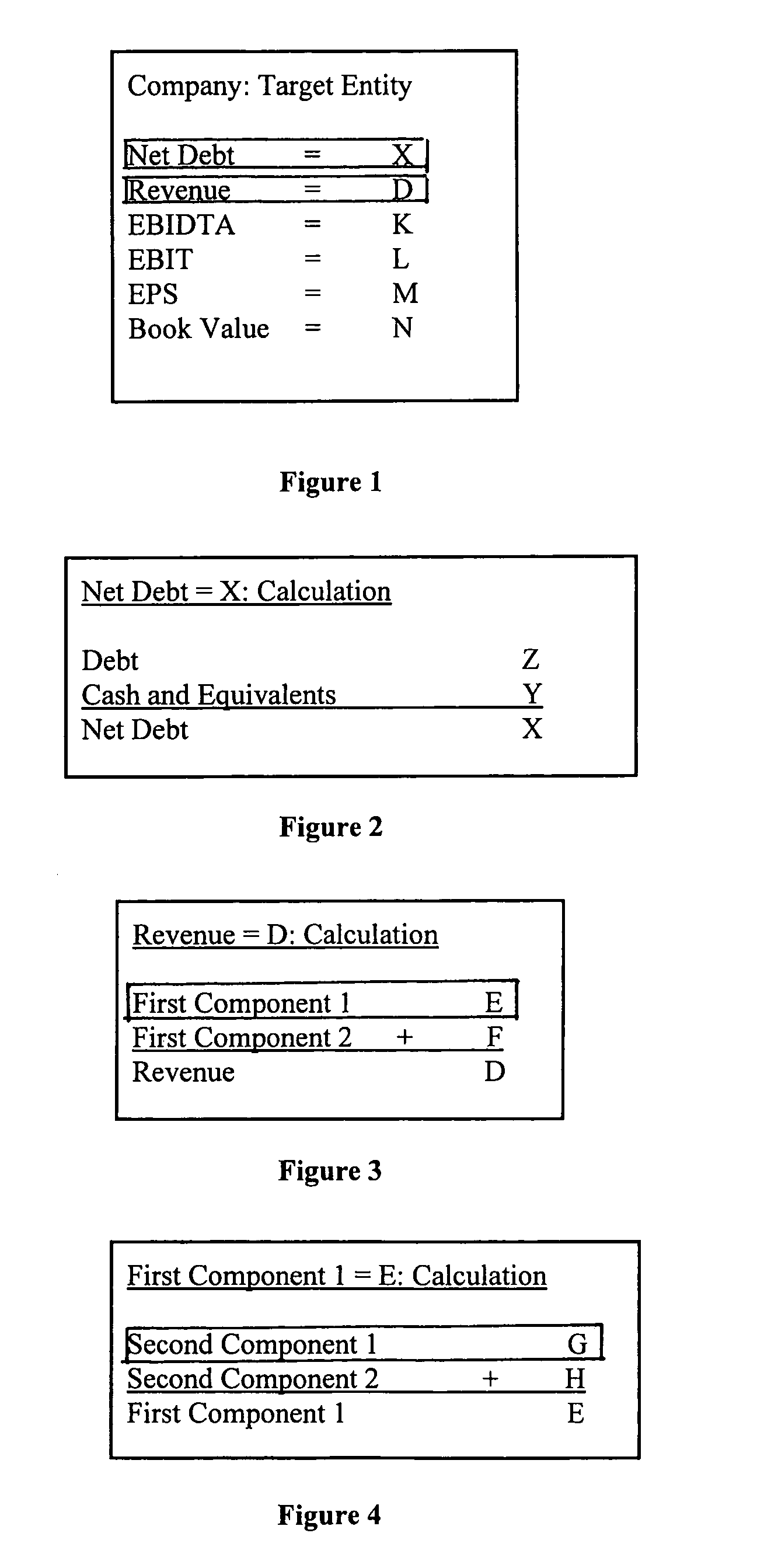
System and method for locating a document containing a selected number and displaying the number as it appears in the document
InactiveUS7089229B2The process is convenient and fastFinanceSpecial data processing applicationsCentral databaseDocumentation
A system and method for locating a number in a source document by presenting and manipulating data on private and public companies. A central database of combined public and private information comprising a plurality of financial information is established. A target entity is entered within the central database by a user, and financial information of the target entity from the central database is displayed. Once a number within the display of financial information is clicked on, the system and method determines which document is the source document containing the numbers, searches through the source document for the number, identifies the location of the number in the source document and highlights and displays the number as it appears in the source document to the user.
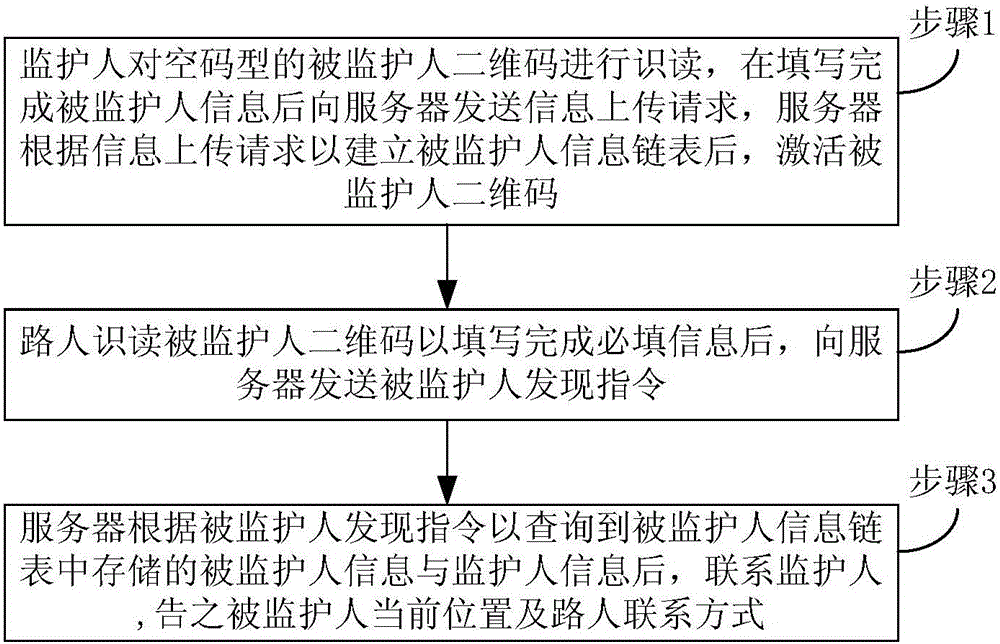
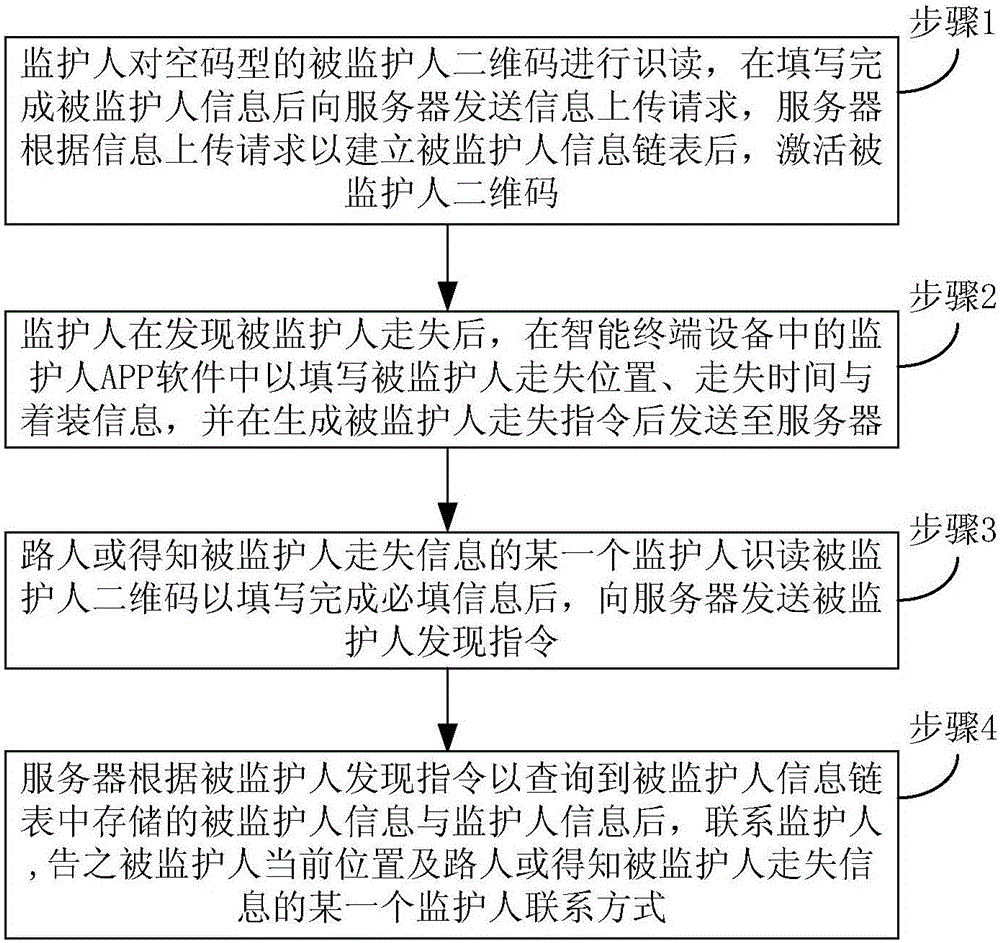
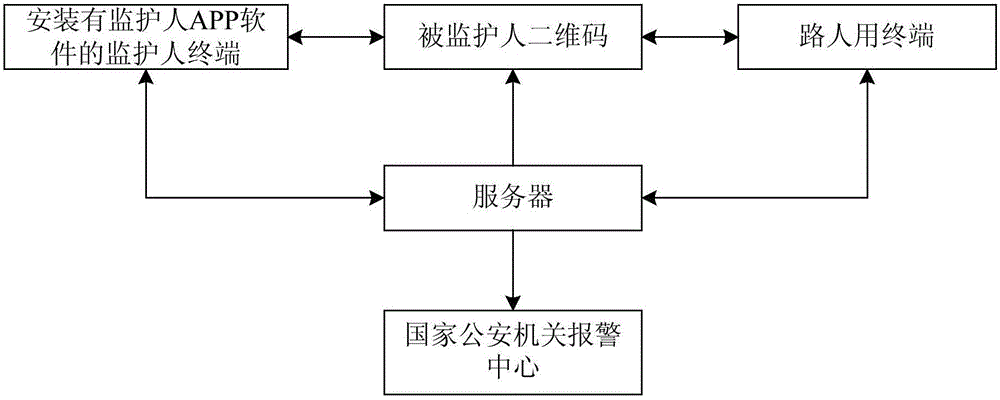
Method and system for seeking person under guardianship based on two-dimension code
InactiveCN105721610ALook for asapFunction increaseData processing applicationsTransmissionContact methodComputer science
The invention provides a method for seeking a person under guardianship based on a two-dimension code. The method comprises that a guardian reads the vacant code type two-dimension code of the person under guardianship; after the information of the person under guardianship is filled out, an uploading request of the information of the person under guardianship is sent to a server; after the server builds the information linked list of the person under guardianship according to the uploading request of the information of the person under guardianship, the two-dimension code of the person under guardianship is activated; after a passerby reads the two-dimension code of the person under guardianship so as to fill out the required information, a discovery instruction of the person under guardianship is sent to the server; after the server inquires the information of the person under guardianship and the information of the guardian according to the discovery instruction of the person under guardianship, the server contacts with the guardian and informs the guardian of the current position of the person under guardianship and the contact way of the passerby. A system for applying the method comprises the two-dimension code of the person under guardianship, a guardian terminal installed with guardian APP software, the server and a passerby terminal. According to the method and the system, a new way is provided for the guardian to seek the lost person under guardianship or the alone person under guardianship; and therefore, the guardian can find the person under guardianship as soon as possible.
Owner:LEADER TECH BEIJING DIGITAL TECH
Privacy server for protecting personally identifiable information
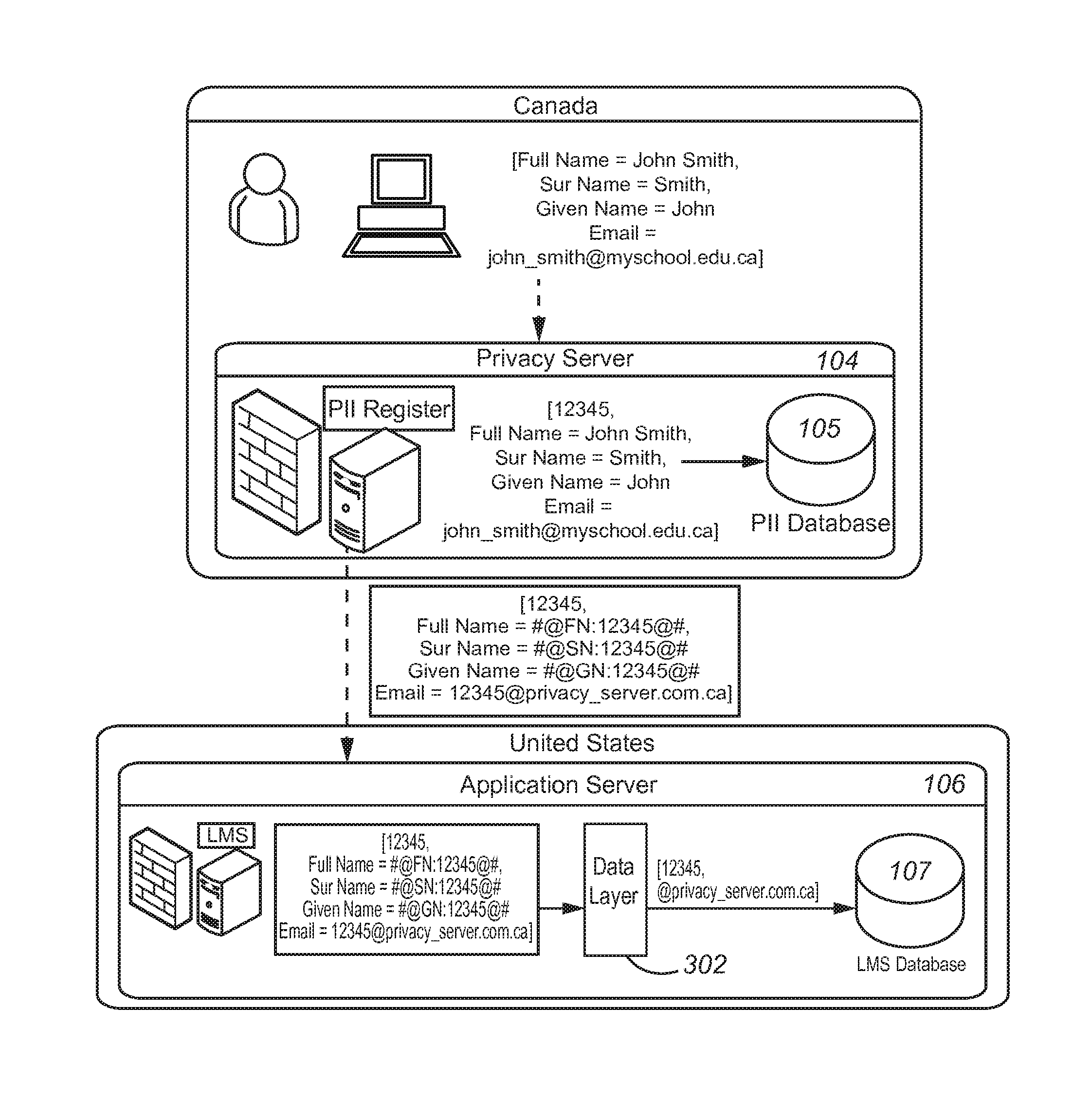
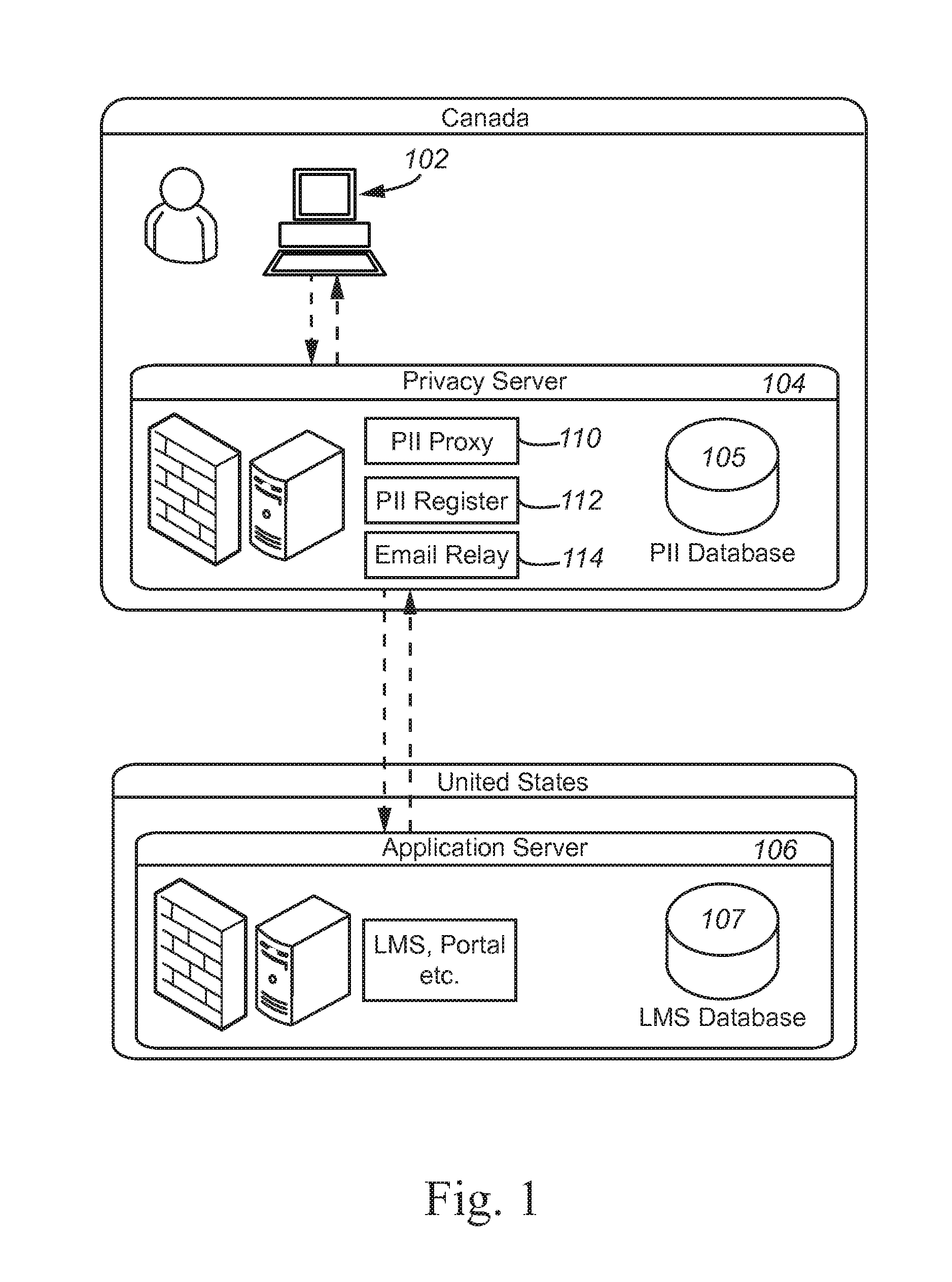
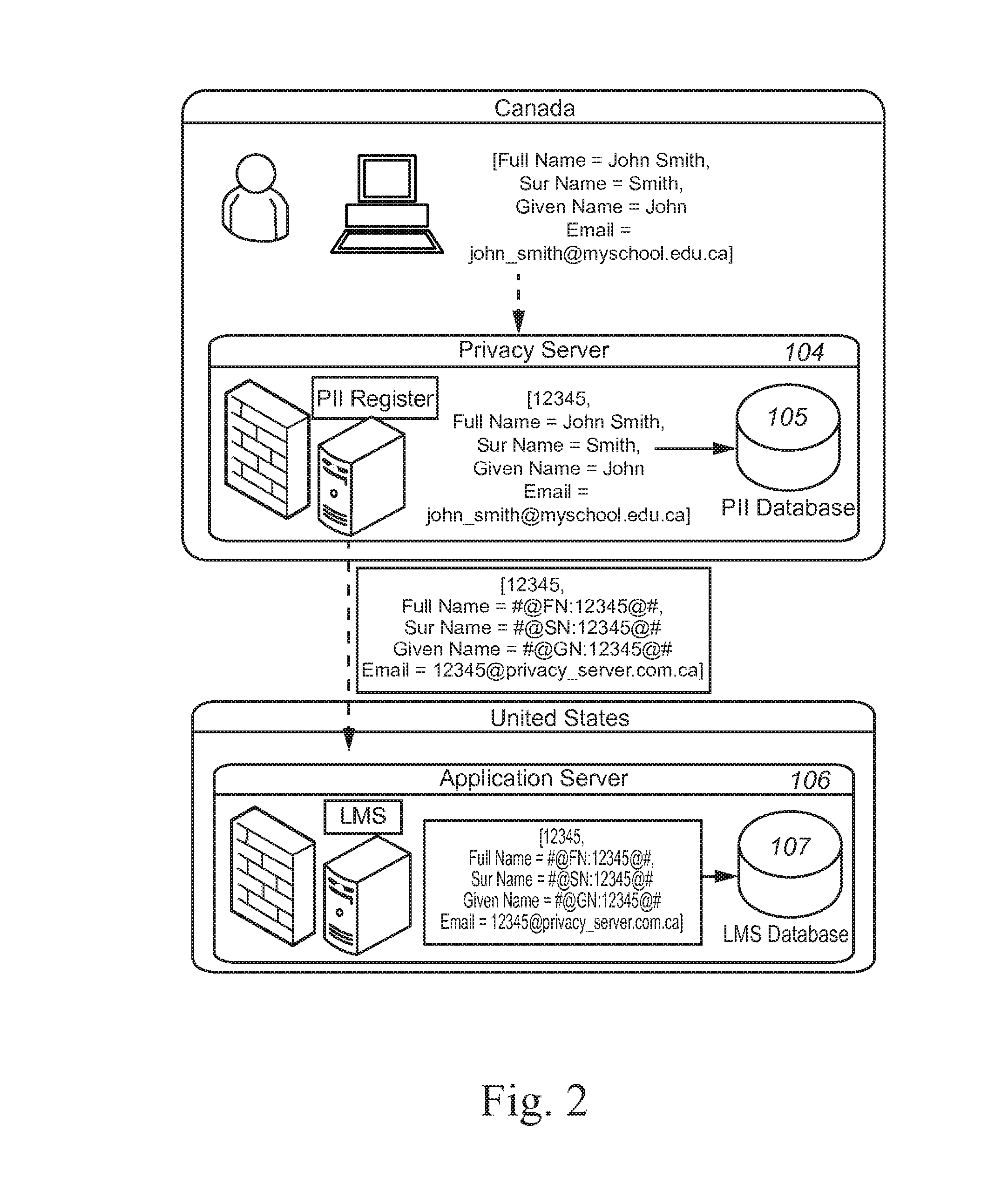
ActiveUS20150150144A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyPersonally identifiable information
A privacy server protects private information by substituting a token or an identifier for the private information. The privacy server recognizes that a communication includes private information and intercepts the communication. The privacy server replaces the private information with a random or pseudo-random token or identifier. The privacy server maintains the private information in a local database and associates the private information for a particular person with the token or identifier for that person.
Owner:PEARSON EDUCATION
Method and system for storing contact information in a network contact database
The invention provides a method comprising, receiving an indication of a desire for contact information associated with given media content, obtaining the contact information associated with the given media content in response to the indication and causing the obtained contact information to be stored in a database associated with a given party.
Owner:BCE
Method and device for protecting mobile terminal address list contact person information
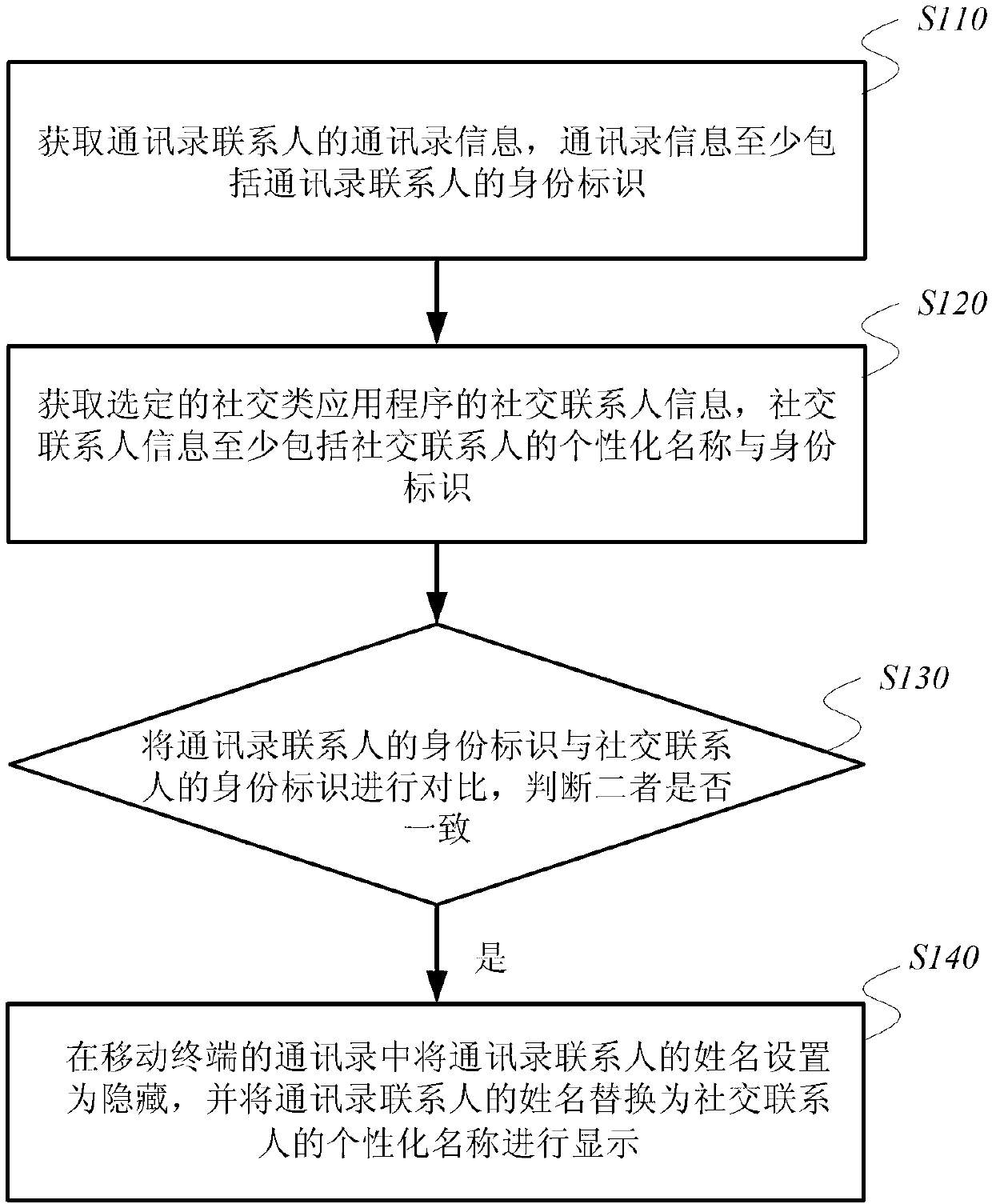
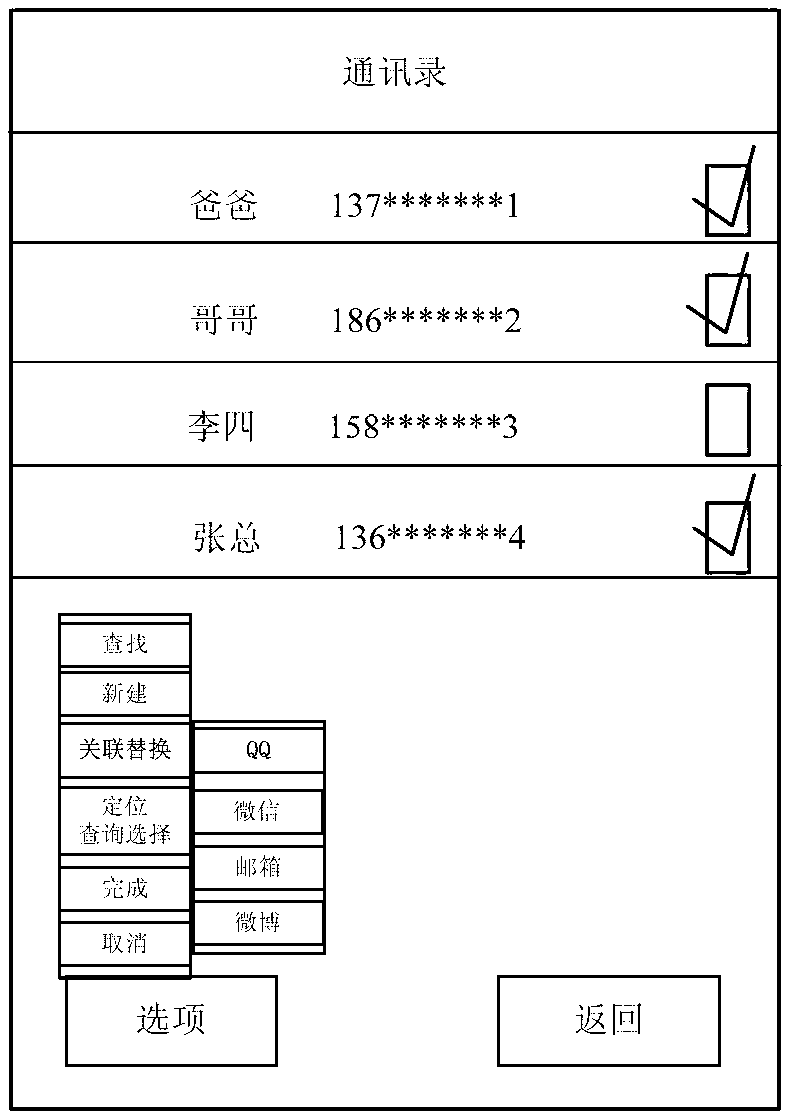
InactiveCN103345606AEffective protectionEasy accessDigital data protectionPersonalizationInternet privacy
The invention discloses a method and device for protecting mobile terminal address list contact person information. Matching and dependence mapping are carried out on identity labels of contact persons to be protected in an address list and identity labels of contact persons in a social contact application program, then names of the contact persons in the address list can be replaced and displayed as individualized names of the contact persons in the social contact application program, therefore, the contact person information can be protected effectively, a user does not need to input passwords when looking up for the contact persons each time, the user can visit the address list more conveniently and quickly, and practicability is improved. Positioning search labels are set, the user can look up for the contact persons with lower protection grades according to names of the contact persons while the method of searching according to the names is limited in searching the contact persons with higher protection grades, therefore, the user can still find the contact person information when confused about the individualized names of a plurality of contact persons, protection of privacy of the important contact person information is improved, and compared with a method of setting private contact persons, the method and device for protecting the mobile terminal address list contact person information are higher in safety.
Owner:DONGGUAN YULONG COMM TECH +1
Internet-based intelligent health compass APP service system and method
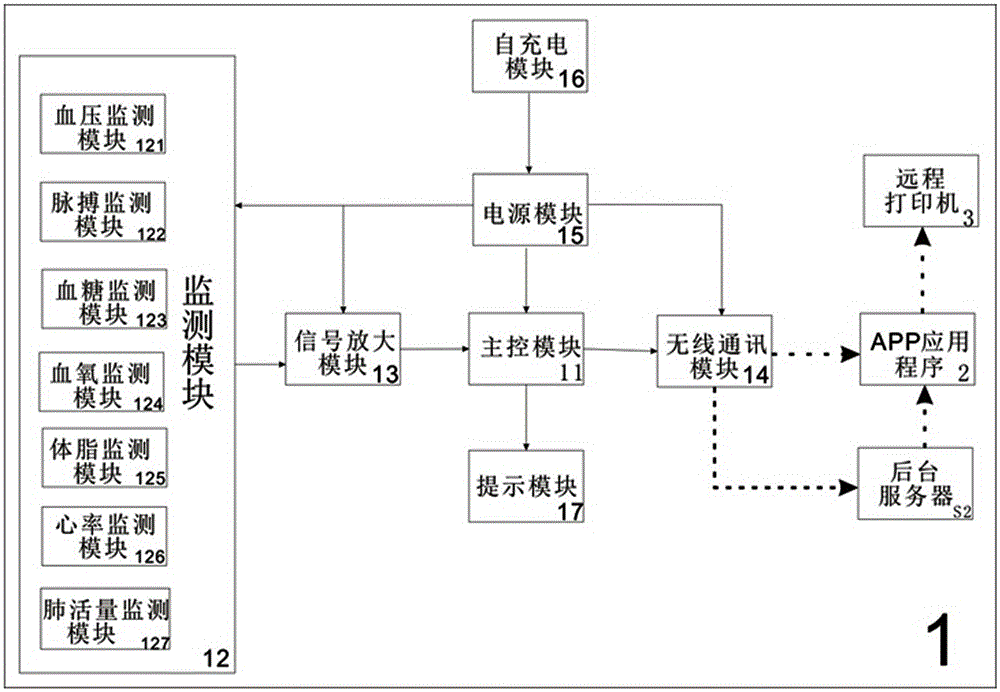
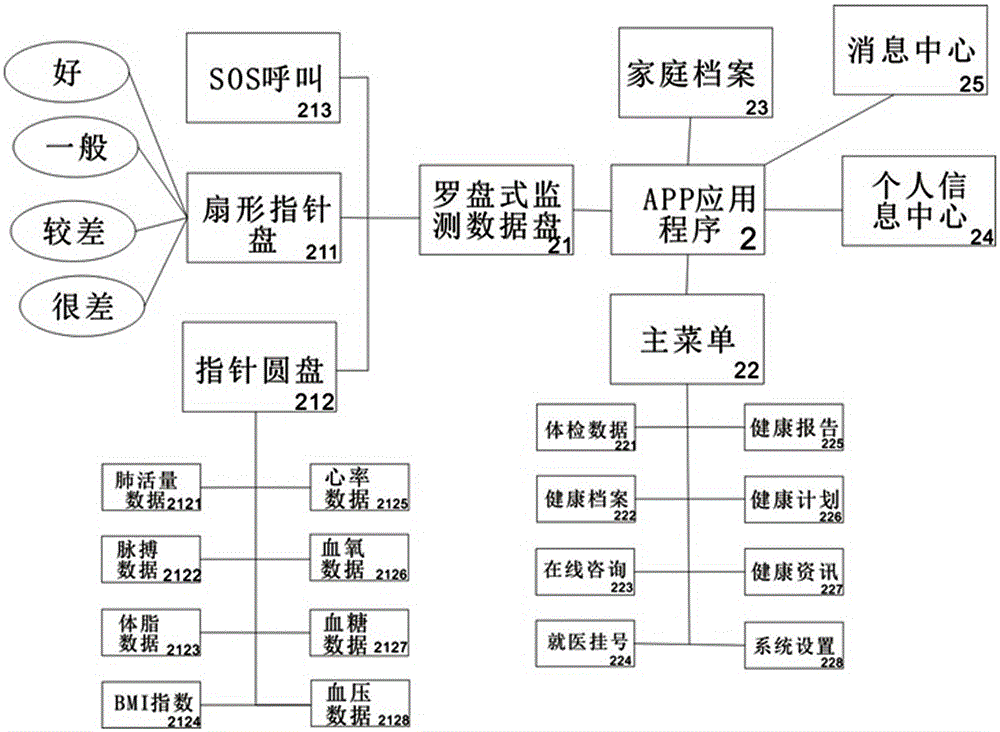
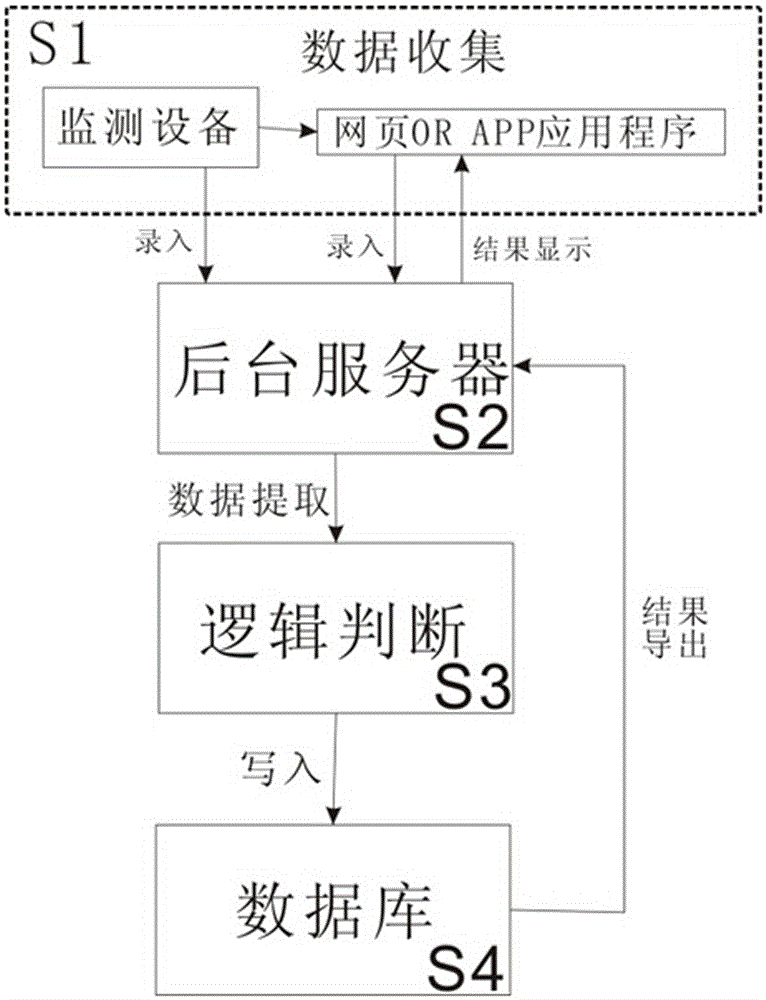
InactiveCN105266777ASimple structureEasy to carrySensorsBlood characterising devicesService systemMonitoring data
The invention discloses an Internet-based intelligent health compass APP service system and a method. The system mainly comprises a monitoring device and an APP application program, wherein the monitoring device comprises a main control module, a monitoring module, a signal amplification module, a power supply module, a wireless communication module, a self-charging module and a prompting module; and the APP application program comprises a compass-type monitoring data disc, a main menu, a personal information center, a message center and a family file. The service method comprises steps of data collection, backstage server, logic judgment, database storage and exporting. Compared with the prior art, the structure is simple and convenient, carrying is convenient, functions are various, and more importantly, the system and the method of the invention are based on internet of things, monitoring records can be stored via the APP, the monitoring data are automatically analyzed, a health report and a health file are generated automatically, online consulting is set, the patient can communicate with the doctor timely wherever the patient is, and life or a holiday can be enjoyed peacefully.
Owner:SHENZHEN HENGTAIKANG MEDICAL TECH CO LTD
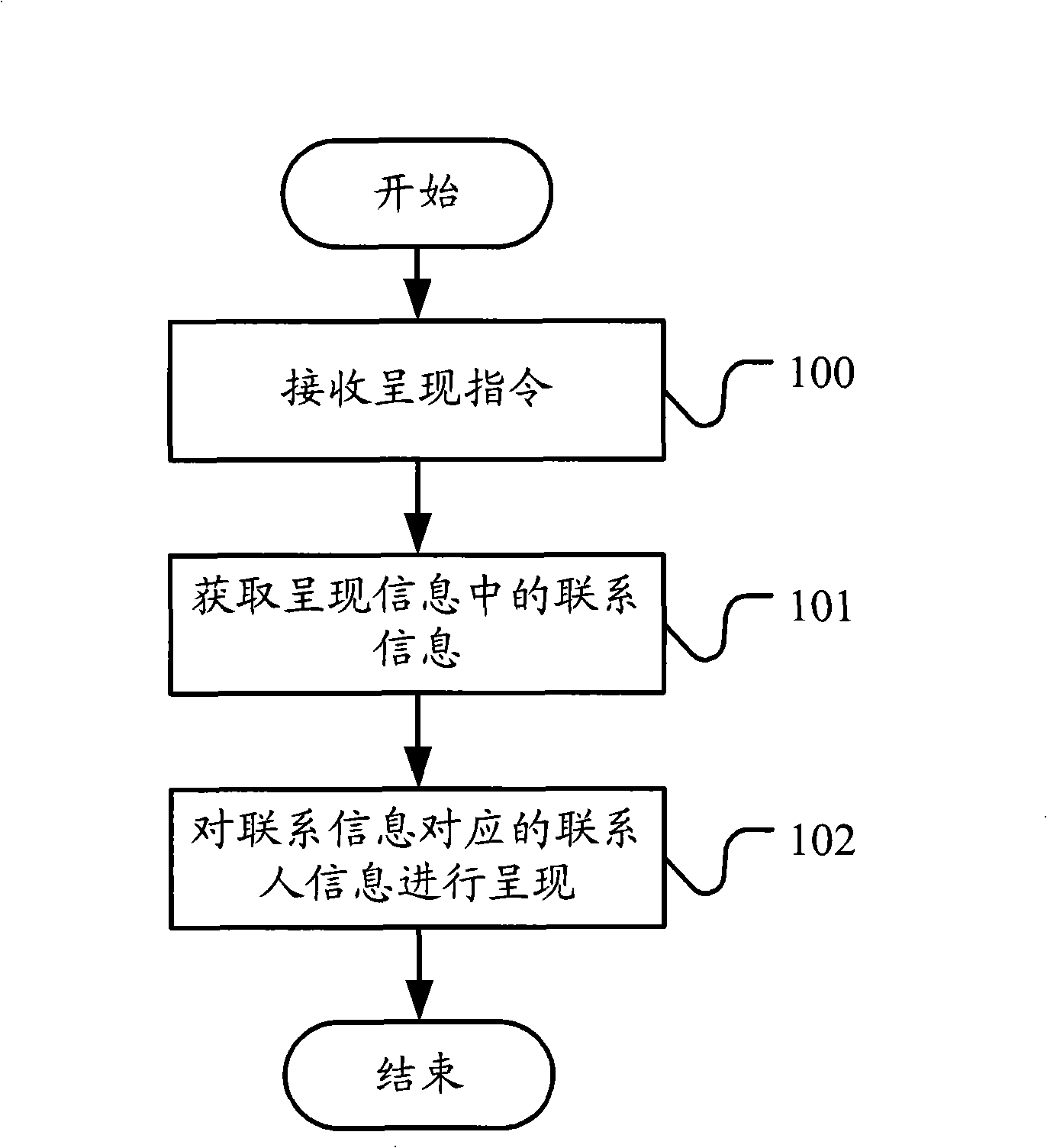
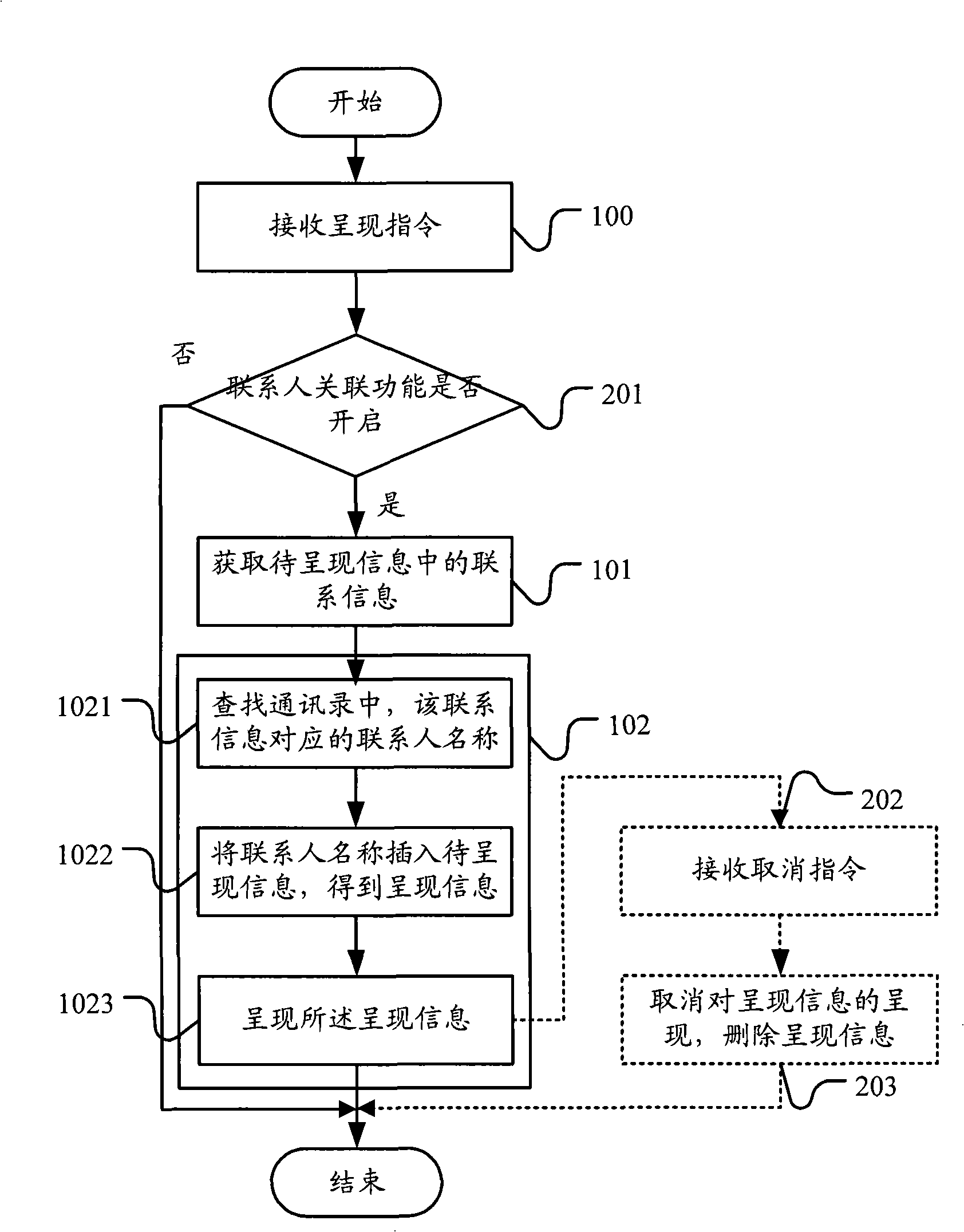
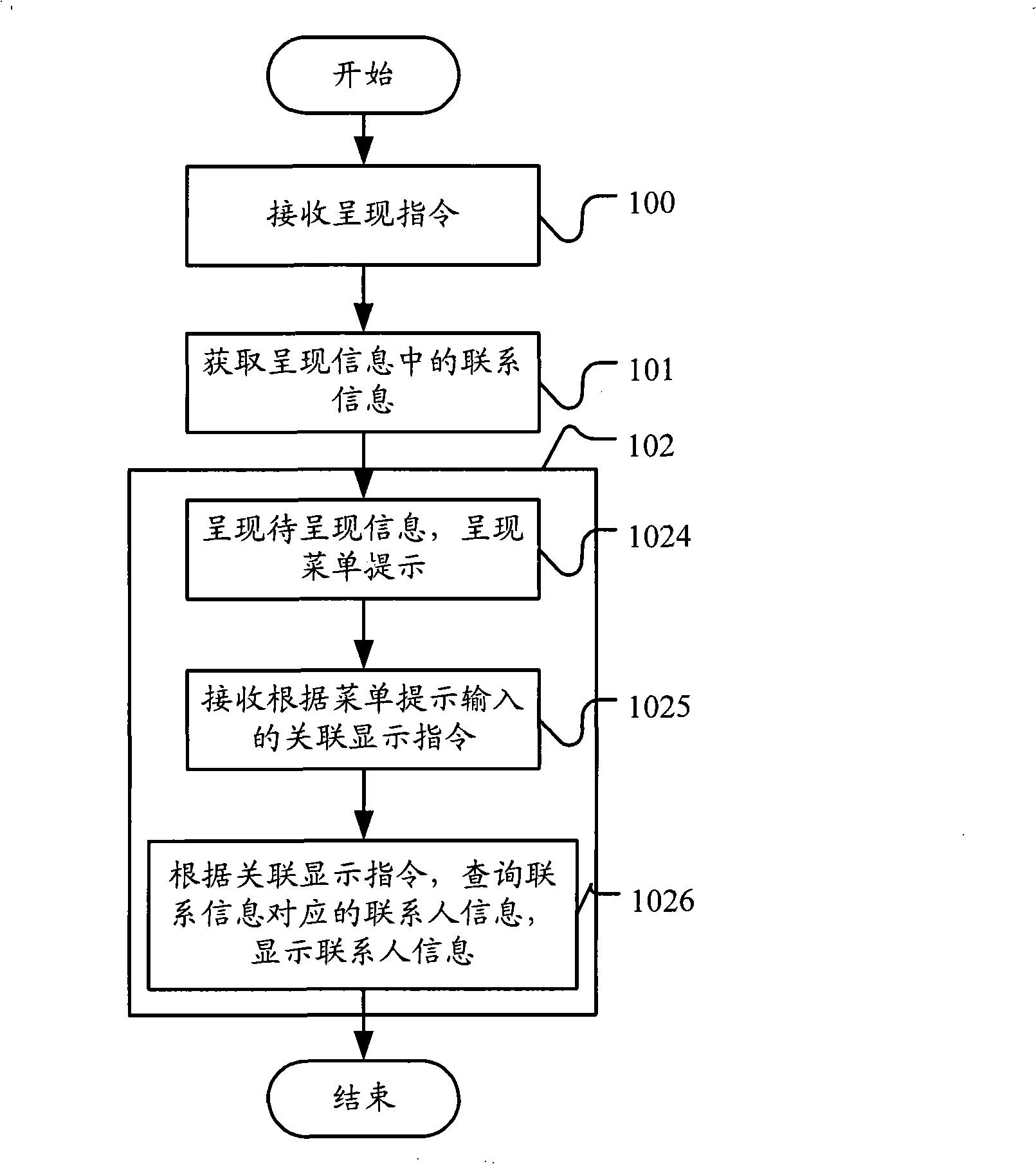
Method for showing information and communication terminal
InactiveCN101351000AEasy to identifyEasy to handleCalling susbscriber number recording/indicationRadio/inductive link selection arrangementsInformation presentationWorld Wide Web
The invention provides an information presentation method and a communication terminal. The information presentation method adopts the following technical proposal: receiving a presentation instruction presenting the information to be presented; obtaining contact information in the information to be presented according to the presentation instruction and presenting the contact person information corresponding to the contact information. In the technical proposal, when a user looks at information, the communication terminal extracts the contact information in the information and presents the contact person information corresponding to the contact information to the user, which facilitates identifying and processing on contact information for the user.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
Contact person information managing method and managing device
ActiveCN102984357ASave storage spaceImprove experienceSubstation equipmentManagement objectComputer science
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
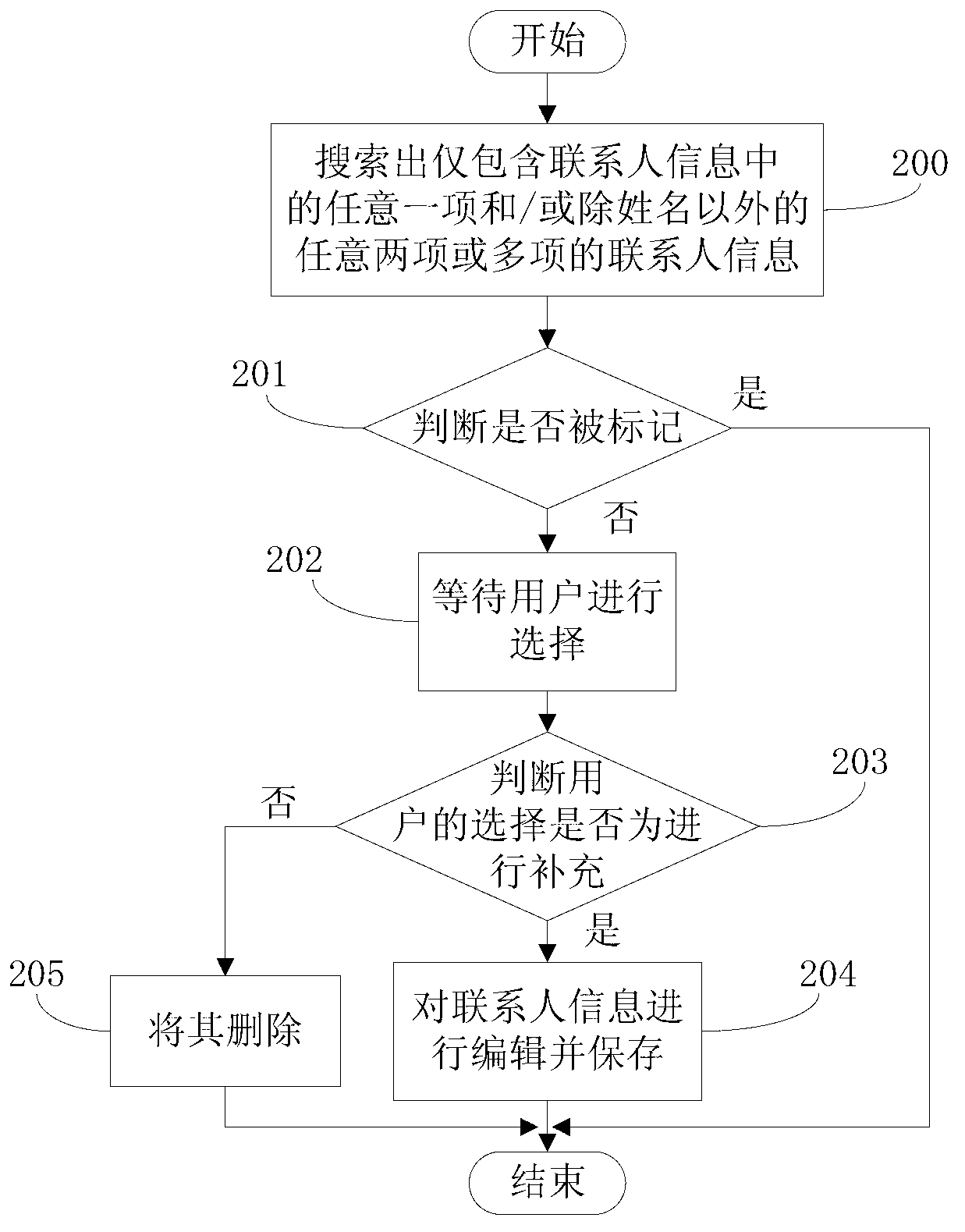
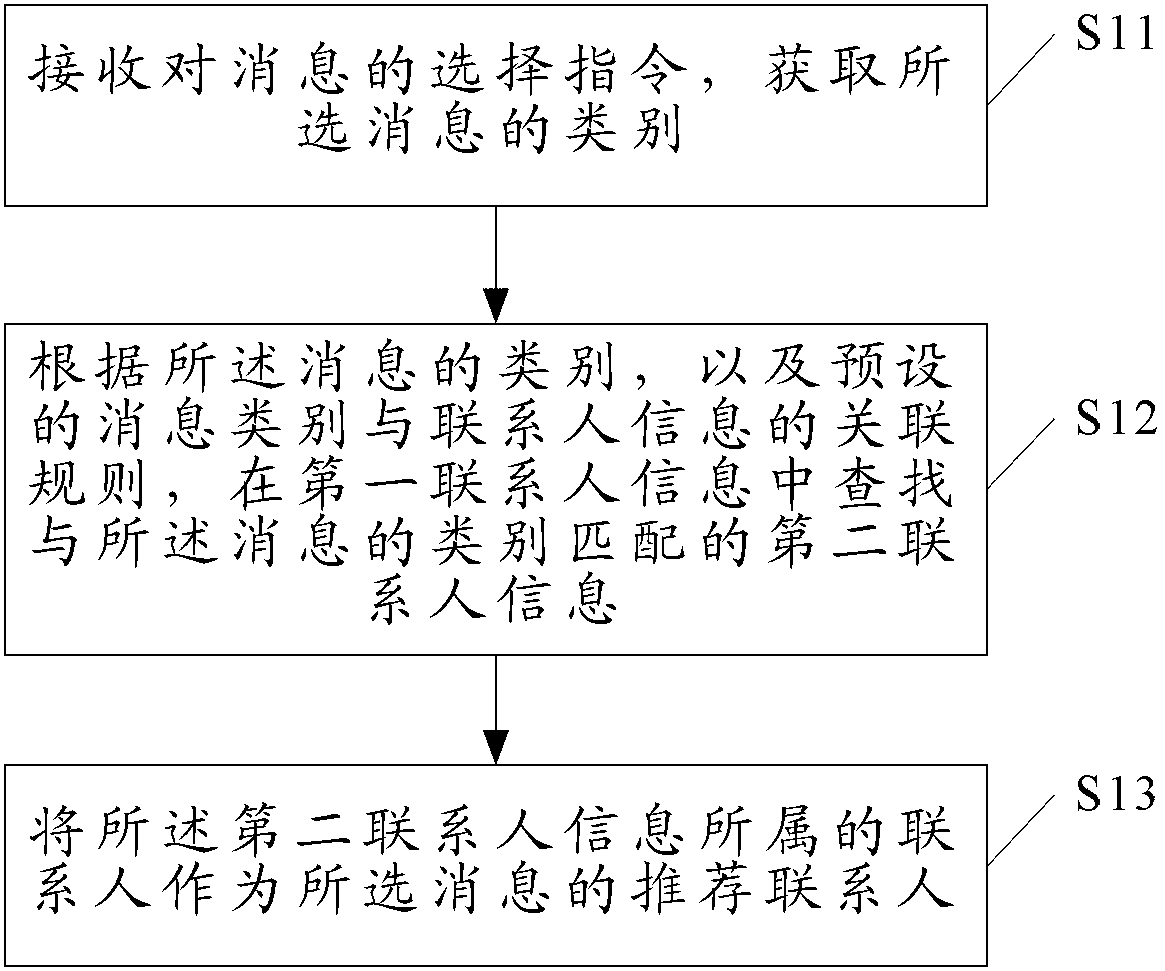
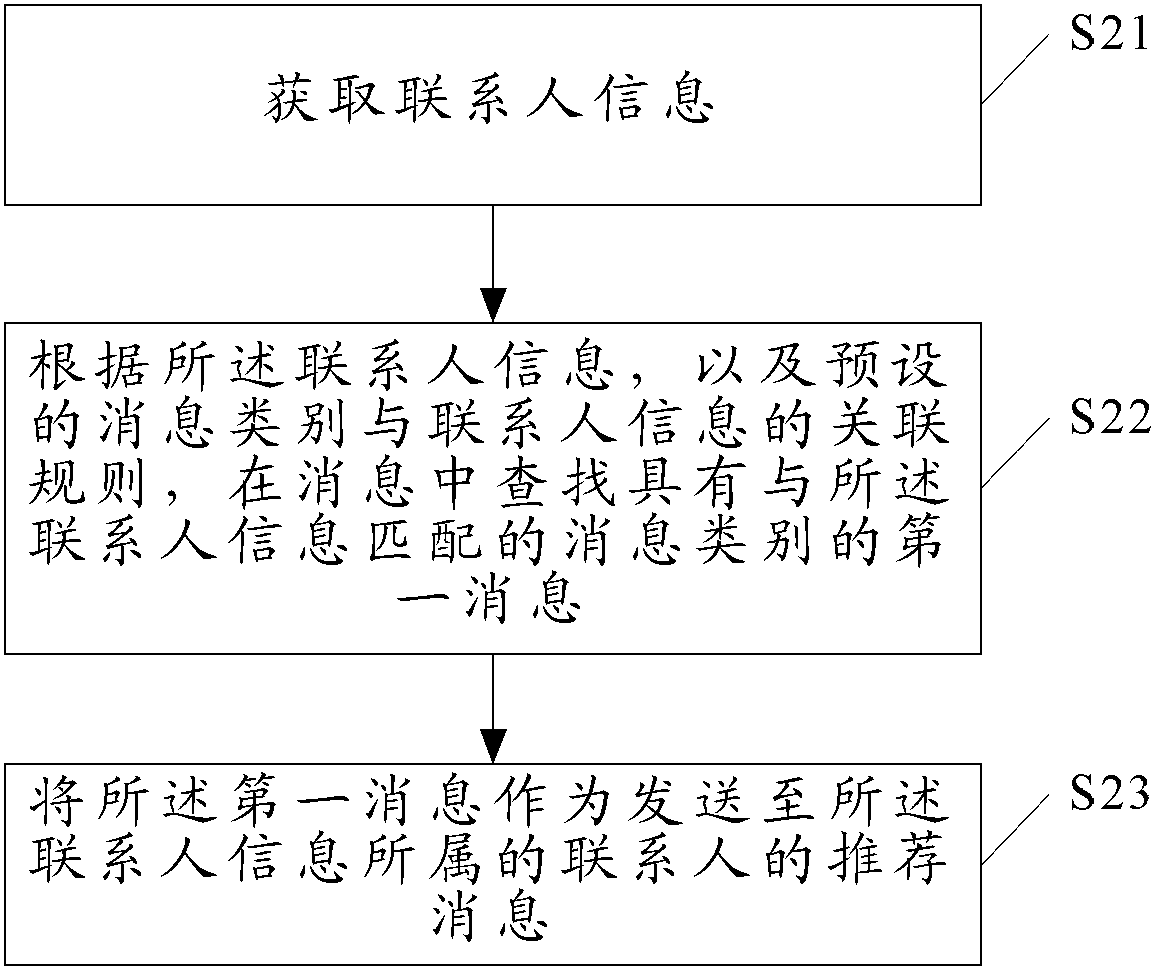
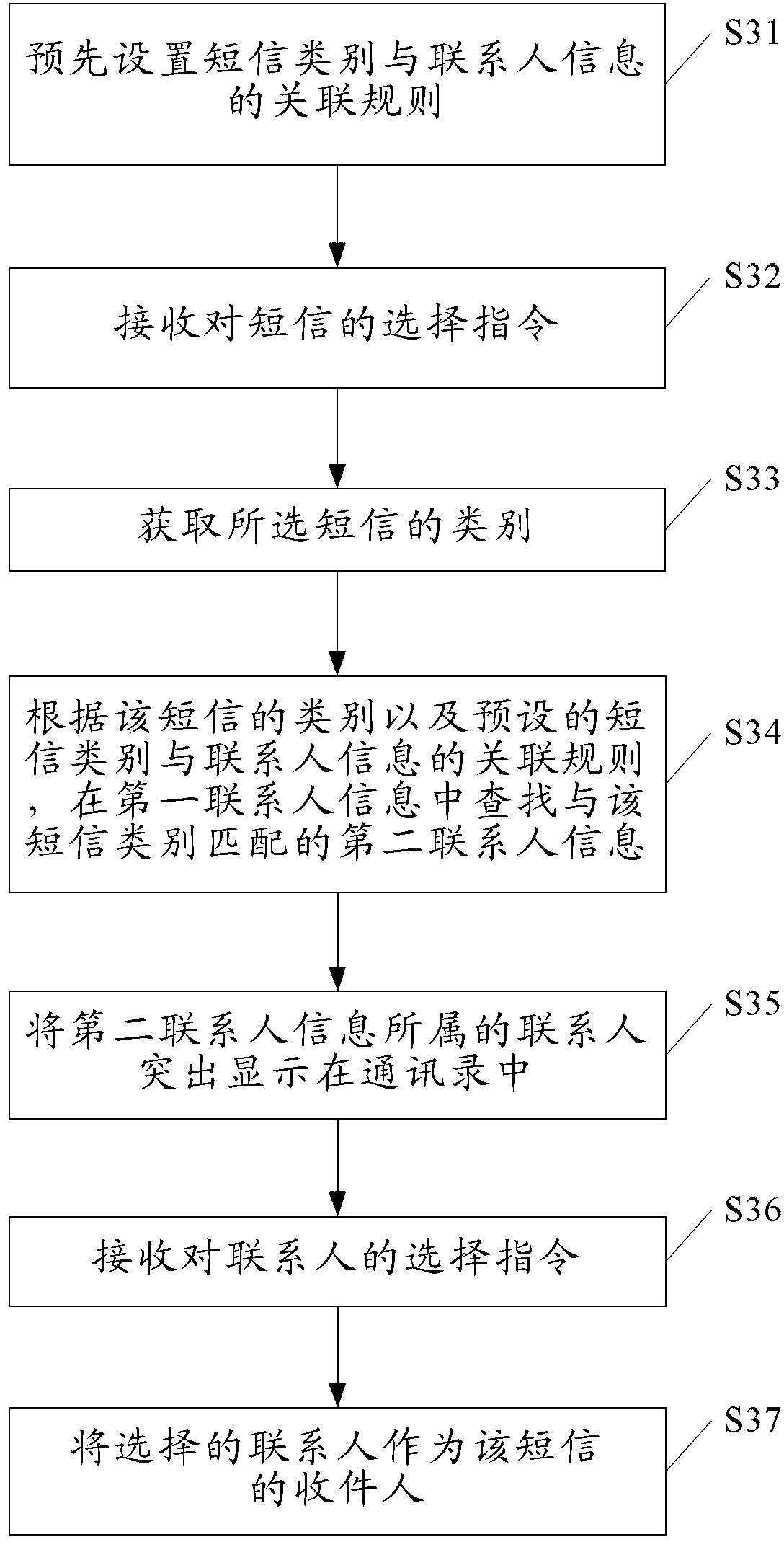
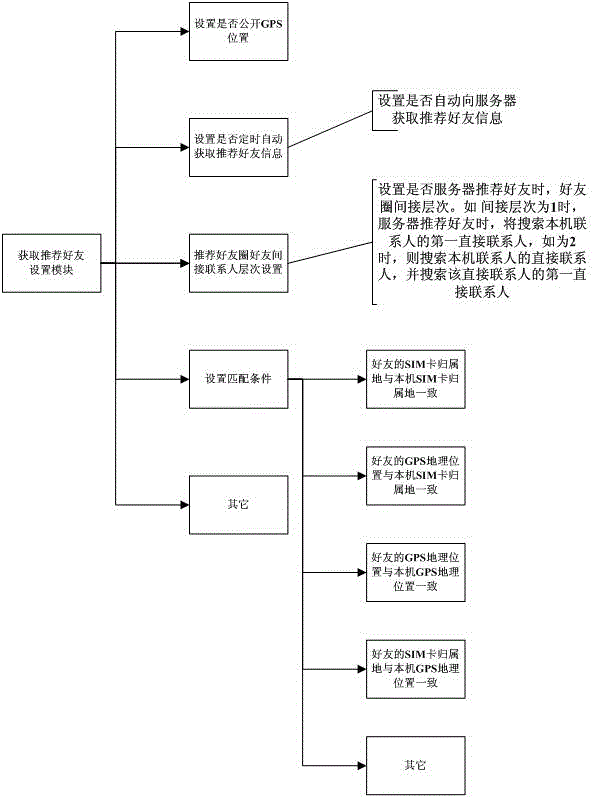
Method and device for recommending contact person and message
The invention discloses a method and device for recommending contact person and message. The method and device for recommending contact person and message includes the following steps of receiving a selection instruction for the message, and obtaining the type of the message; searching for second contact person information which is matched with the type of the message in first contact person information according to the type of the message and an association rule between a preset message type and the contact person information; and enabling a contact person to which the second contact person information belongs to serve as the recommended contact person of the message. According to the method and device for recommending contact person and message, matched contact person information is found out through the selected message type, the contact person to which the second contact person information belongs serves as the recommended contact person of the message, and a user does not need to search for the contact person in a contact book, so that the efficiency of sending messages is increased, and the usage experience of the user is improved.
Owner:XIAOMI INC
Identity authentication method and device based on user identification module and blockchain technology
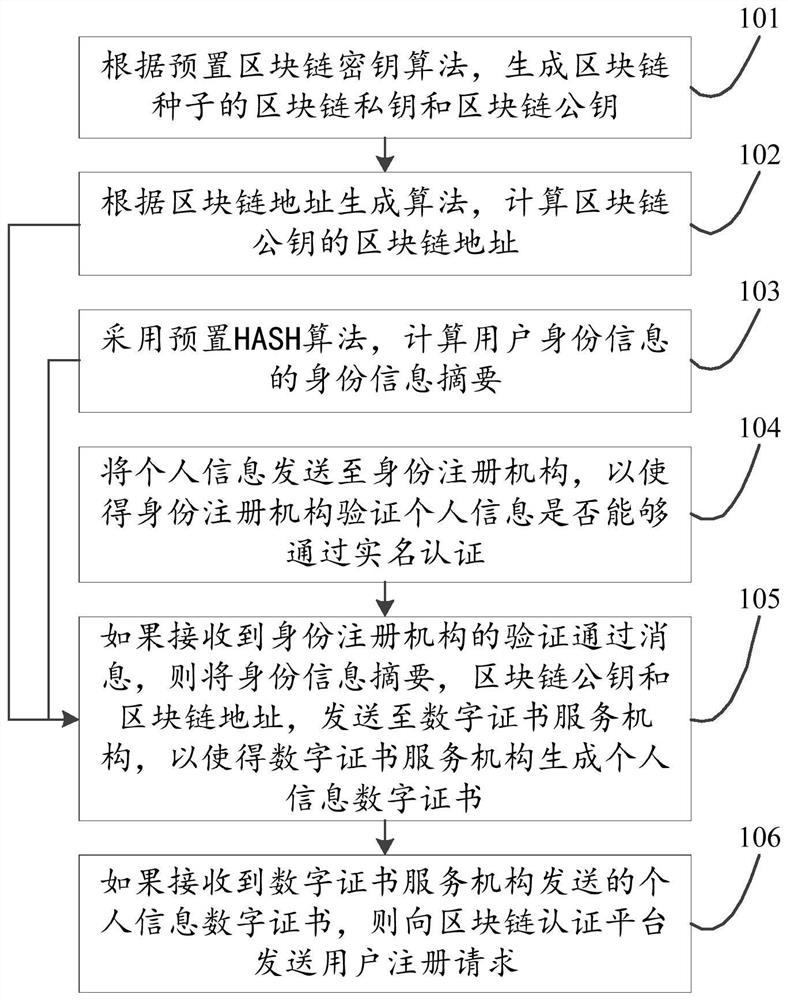
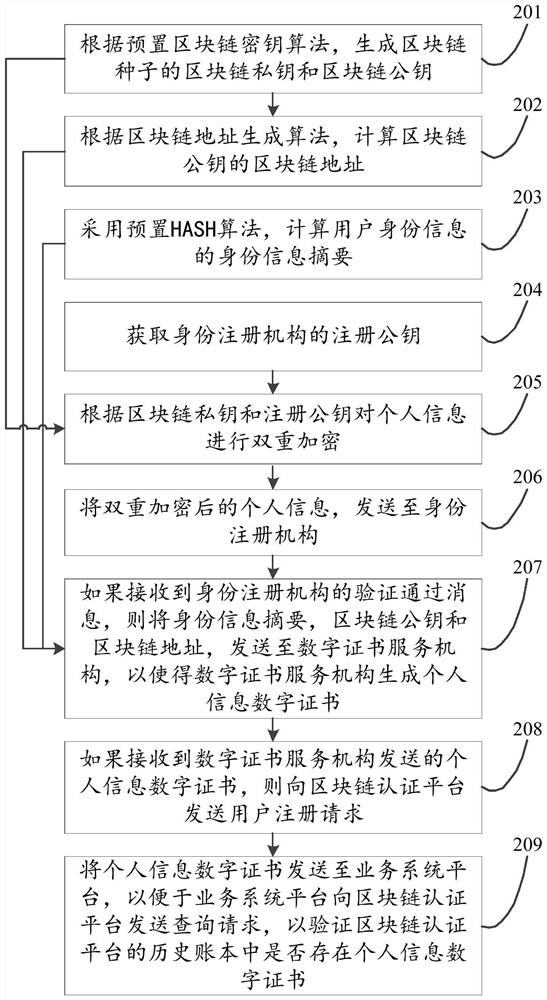
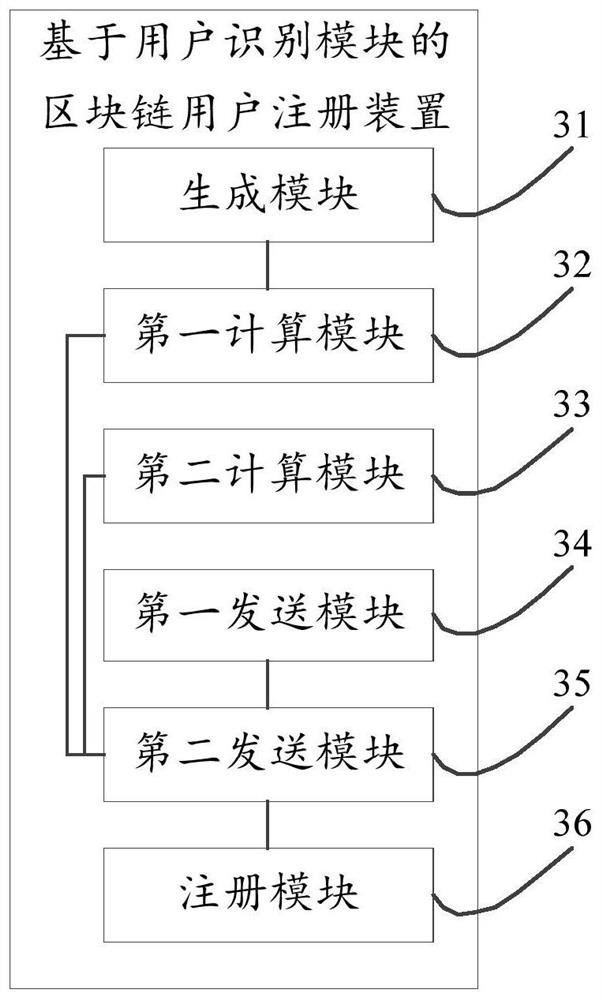
ActiveCN111859348AData RecoveryDigital data protectionDigital data authenticationRegistration authorityInternet privacy
The invention discloses an identity authentication method and device based on a user identification module and the blockchain technology, relates to the technical field of blockchain, and is inventedfor solving the problems of blockchain key storage and use security in the prior art. The method mainly comprises the following steps: generating a blockchain private key and a blockchain public key of a blockchain seed according to a preset blockchain key algorithm; calculating a blockchain address of the blockchain public key according to an address generation algorithm; calculating an identityinformation abstract of the user identity information by adopting a preset HASH algorithm; sending the personal information to an identity registration institution, so that the identity registration institution verifies whether the personal information can pass real-name authentication or not; if the verification is passed, sending the identity information abstract, the blockchain public key and the blockchain address to a digital certificate service institution; if the personal information digital certificate sent by the digital certificate service mechanism is received, sending a user registration request to the blockchain authentication platform. The method and the device are mainly applied to a blockchain user identity authentication process.
Owner:上海微位可信互联安全科技有限公司
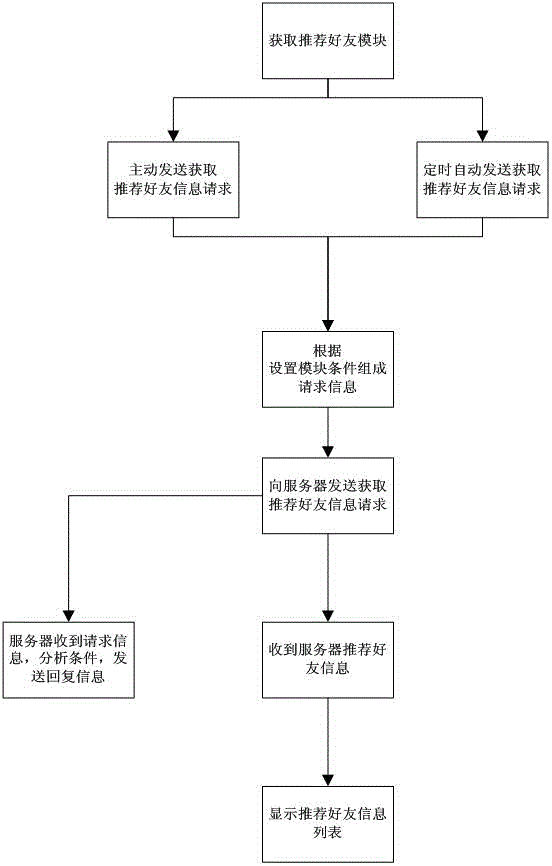
Method and system for recommending friends by mobile terminals
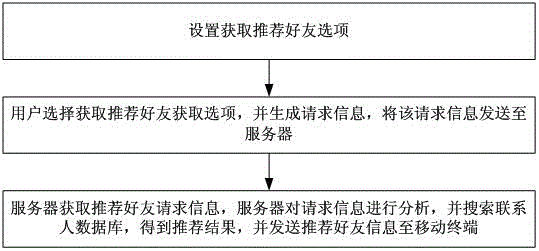
InactiveCN102984247AFacilitate communicationIncrease sociabilitySubstation equipmentTransmissionInternet privacyEngineering
The invention discloses a method and a system for recommending friends by mobile terminals. The method includes that a user selects access options for accessing recommended friends to generate request information, and the request information is sent to a server; and the server obtains the request information for accessing the recommended friends, and the server analyzes the request information, searches a contact database to obtain recommendation results, and sends friend recommending information to a mobile terminal. The method further includes that friend recommending options are obtained, update information is sent to the server when the user updates contact information, and the server updates the contact database. Compared with the prior art, the method and the system enlarge friend making circles of users, and the friend making reliability is improved; and the friend making circles can be maintained according to different requirements of users, and the purpose is enhanced and the friend making range is controlled.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Voucher management system and method, and medium
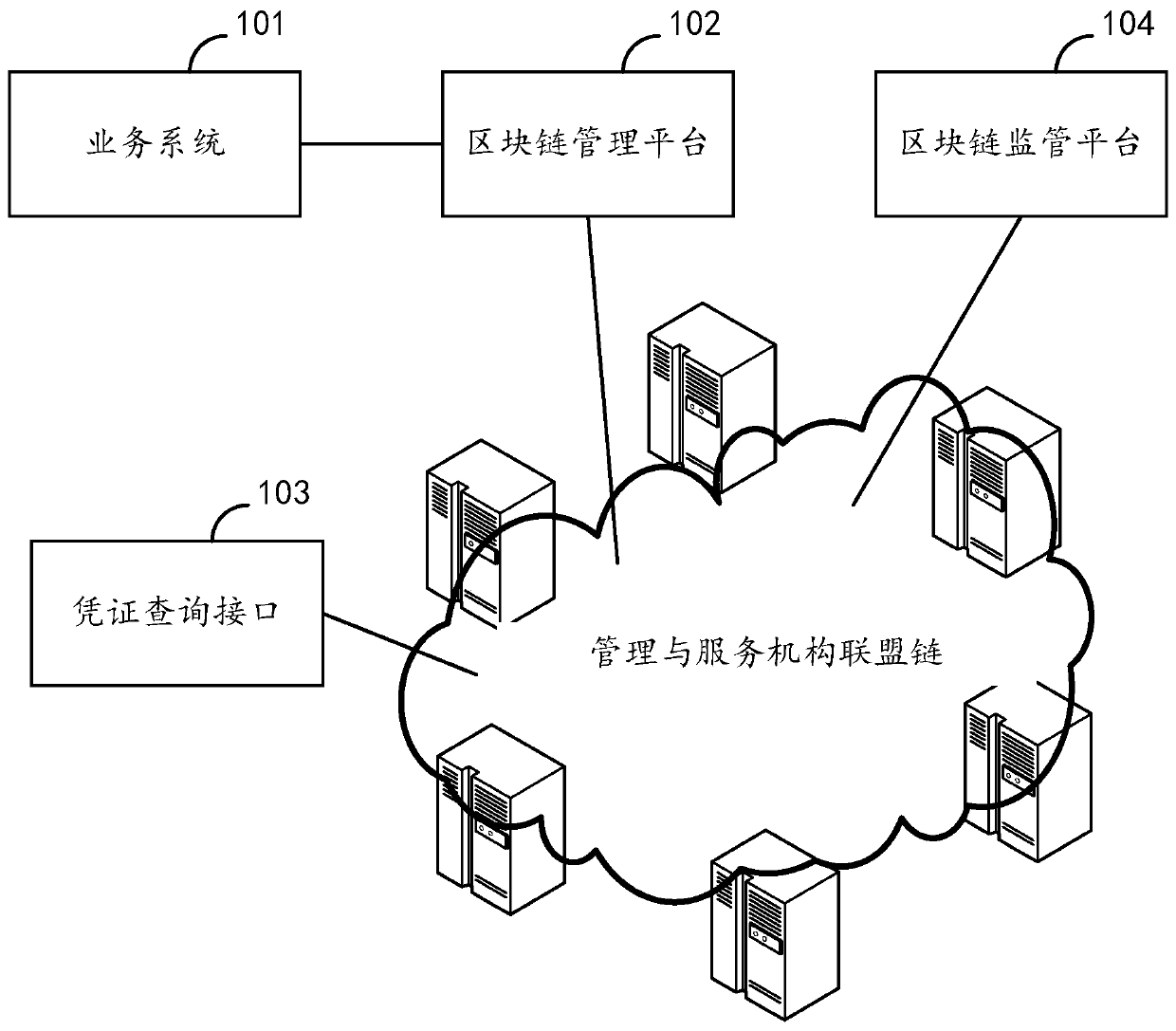
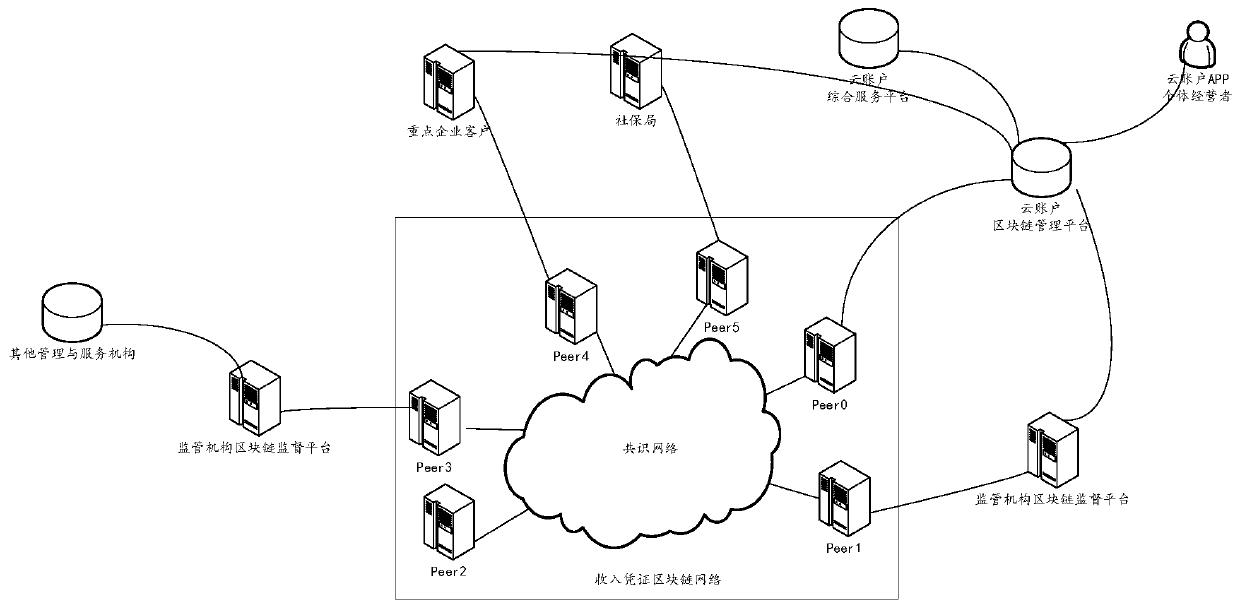
PendingCN111598436AEffective Privacy ProtectionEffectively provide privacy protectionDatabase distribution/replicationDigital data protectionEngineeringVoucher
The invention discloses a voucher management system and method, and a medium, and the voucher management system comprises a business system which is used for generating a voucher and synchronizing thegenerated voucher to a blockchain management platform; a blockchain management platform which is used for storing the voucher to a management and service institution alliance chain after the synchronized voucher passes verification and auditing, wherein a management and service institution alliance chain is a unique blockchain corresponding to the management and service institution identity information; and a voucher query interface which is used for a user to acquire vouchers from the management and service institution alliance chain according to authority. By the adoption of the voucher management system and method, full-cycle sensitive data privacy guarantee can be effectively provided, and each user can only obtain the certificate from the alliance chain according to the authority, and it can be guaranteed that each user obtains own data but cannot obtain information of other people. Furthermore, a blockchain supervision platform is provided for related departments to use, so thatpenetration type supervision can be realized.
Owner:云账户技术(天津)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com