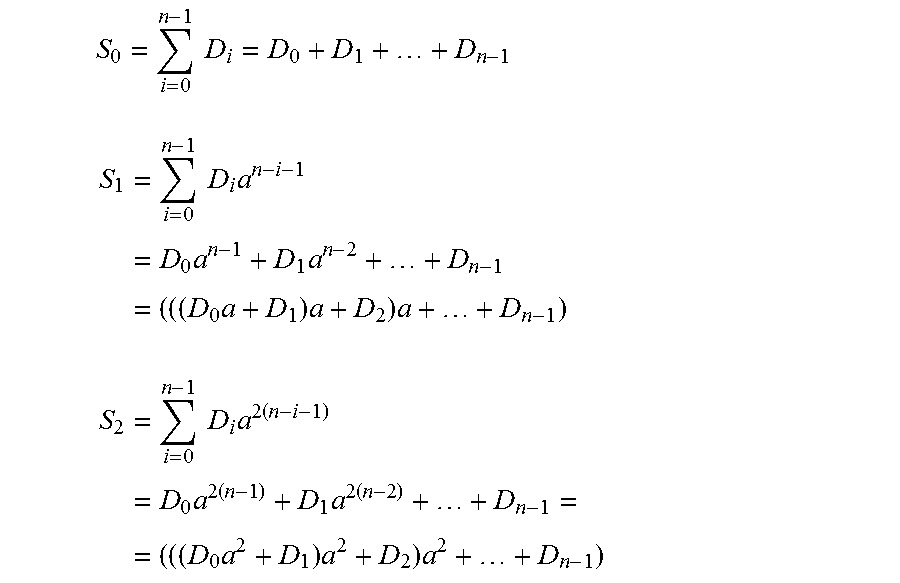Patents
Literature
32results about How to "Data recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
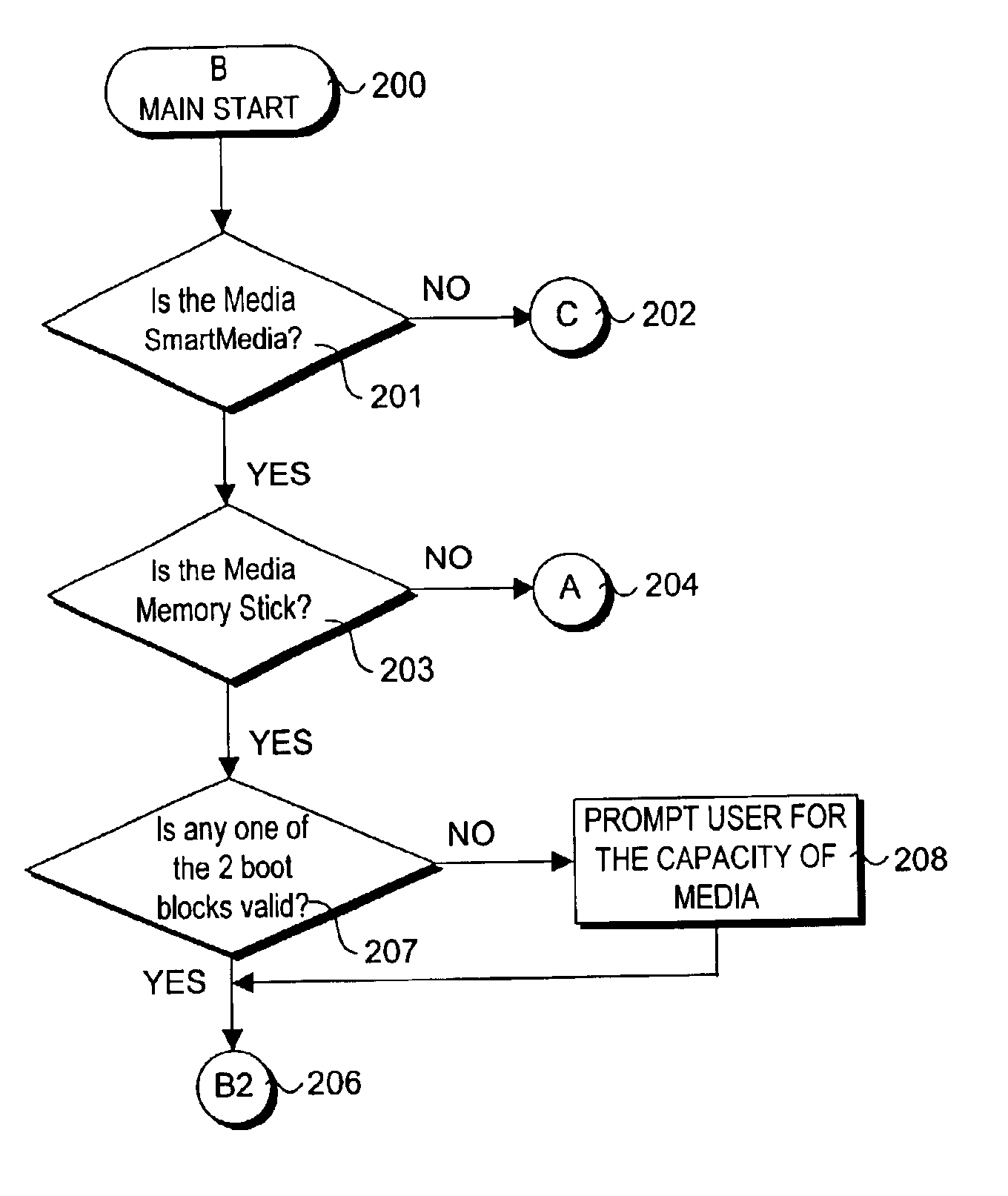
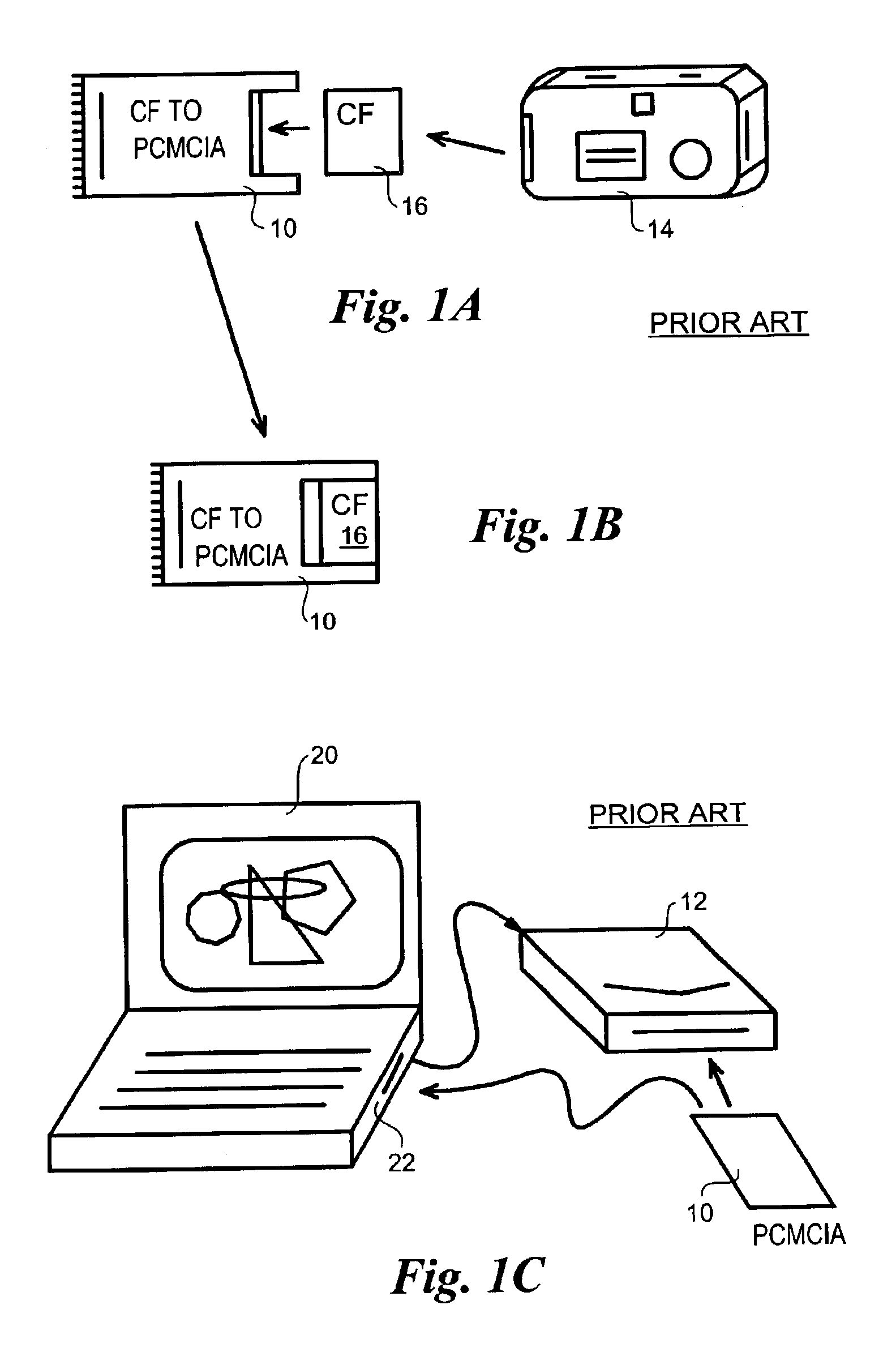
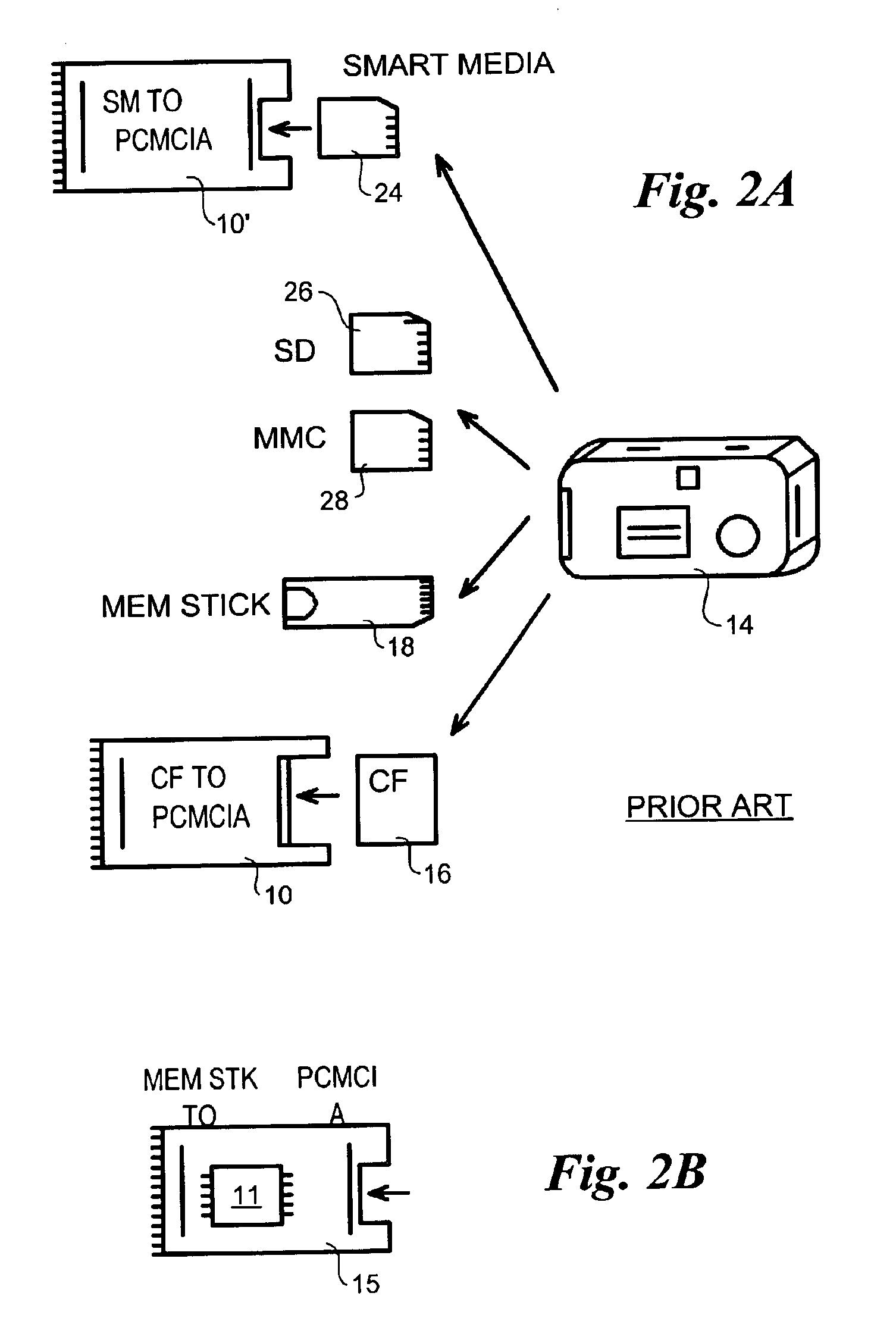
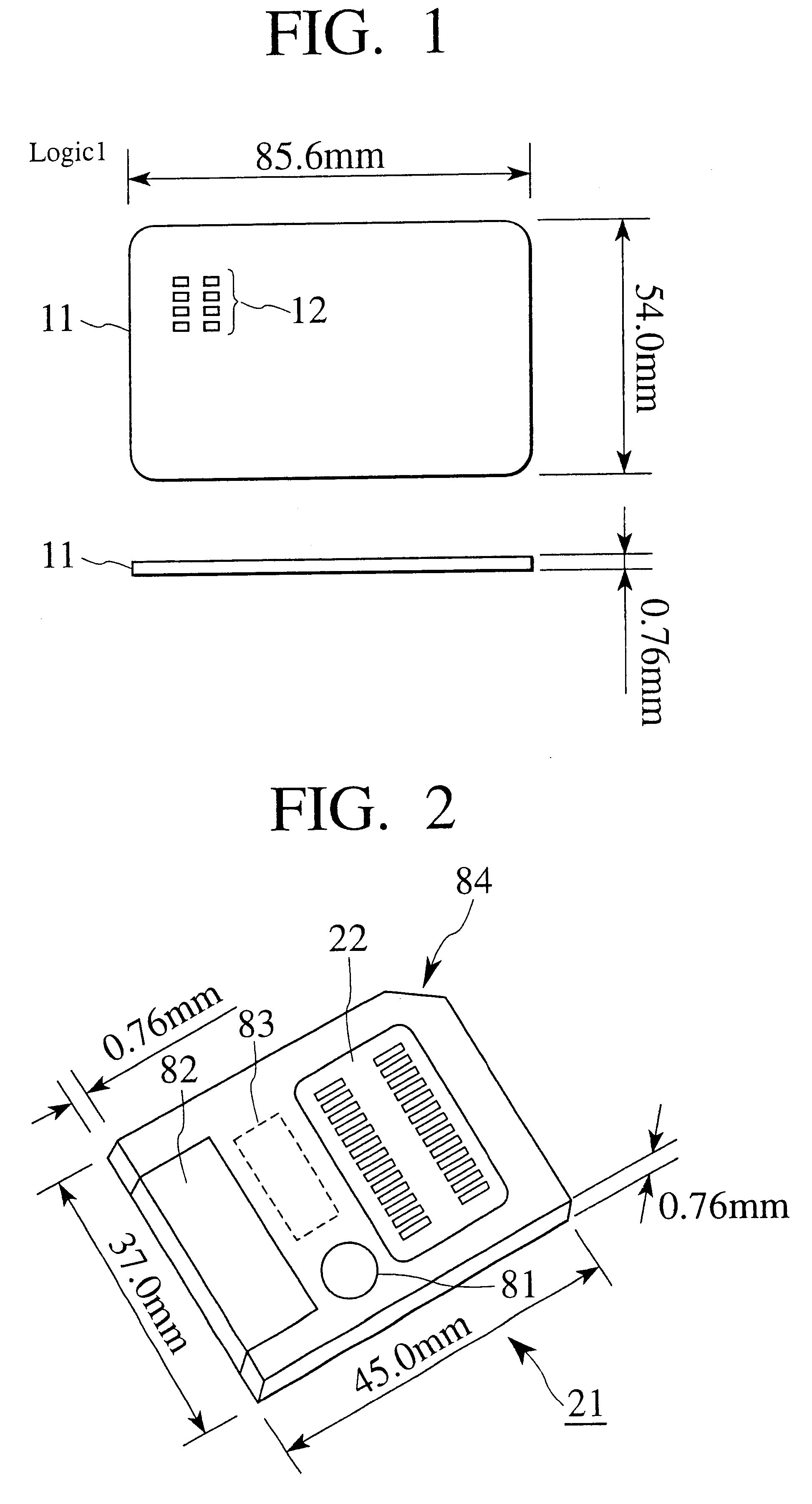
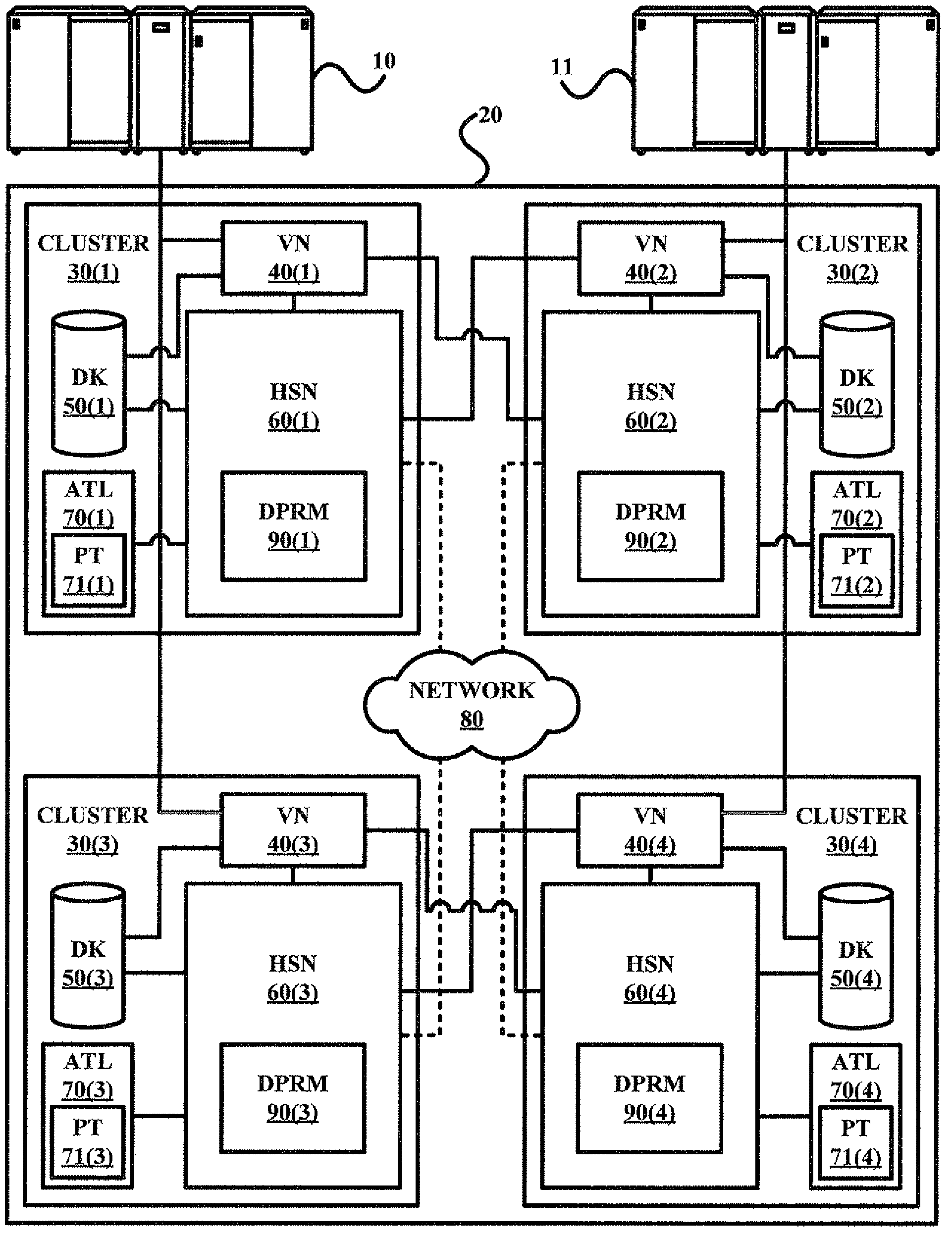
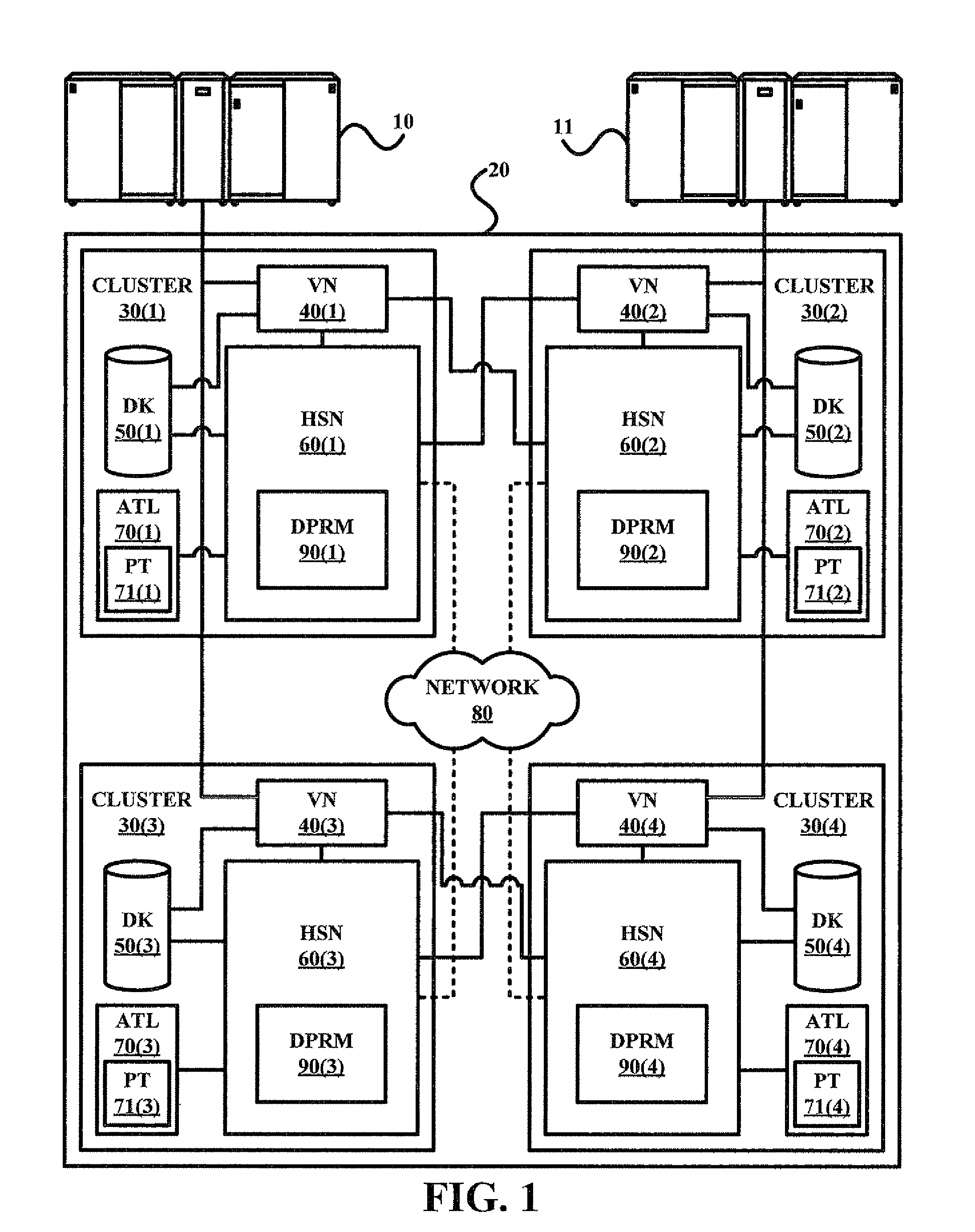
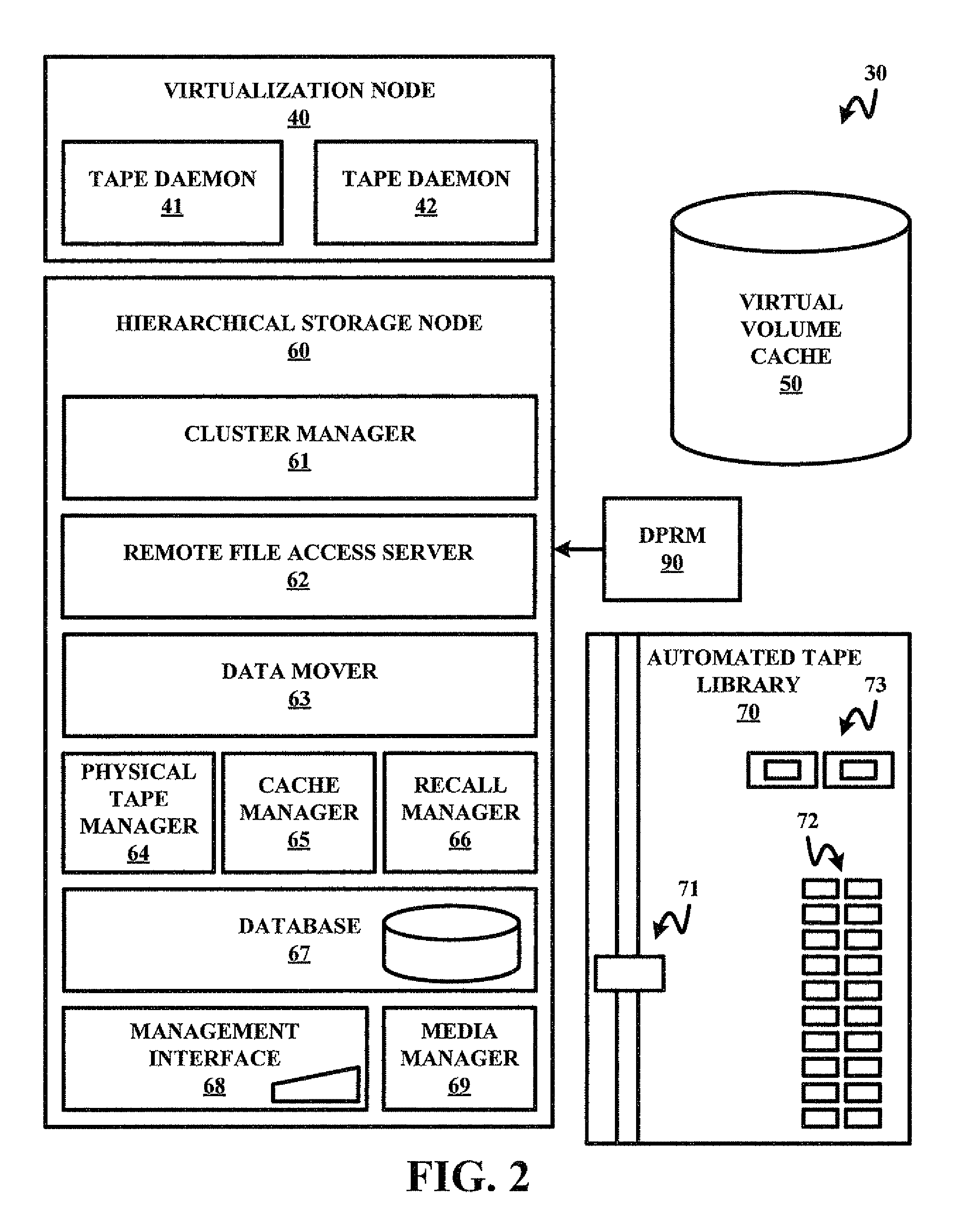
Field-operable, stand-alone apparatus for media recovery and regeneration
InactiveUS6839864B2Easy to carryData recoveryCo-operative working arrangementsSensing record carriersFile systemHigh level interface
A field-operable stand-alone apparatus for recovering data from corrupted flash media and regenerated damaged flash media. The apparatus enables users in the field to recover data from and / or regenerate damaged flash media without requiring the use of a computer. In one aspect, recovery comprises using a low-level access scheme that enables data to be recovered when high-level interfaces, such as file systems, are damaged. The type of flash media is determined, and a corresponding access scheme is employed. Depending on the type of damage to the media, a physical-to-logical table may be built and employed to sequentially access the flash media in search of indicia from which selectable file-types can be identified, or the media may be accessed using normal operating system commands. Once the file indicia are found, the location of corresponding file data is identified, whereupon the file data are read and stored. The apparatus may include a plurality of different connectors to interface with different media form factors, or a universal connector that employs various form-factor adaptors to interface with the different flash media configurations.
Owner:MCM PORTFOLIO LLC
Data storage medium with certification data
InactiveUS6651149B1Ensure safetyAvoid data duplicationDigital data processing detailsUser identity/authority verificationDigital dataData storing
A data storage medium has a first memory area that is read-only and stores first certification data that is unique to the data storage medium, a second memory area that stores data and second certification data supplied from the outside, an identity circuit for determining whether or not the first and second certification data are identical with each other, and a switch circuit for providing the data stored in the second memory area to the outside only when the identity circuit determines that the first and second certification data are identical with each other. If data is written into the data storage medium with illegal certification data, the data storage medium disables the reading of the written data from the data storage medium, thereby preventing the illegal copying of digital data.
Owner:KK TOSHIBA
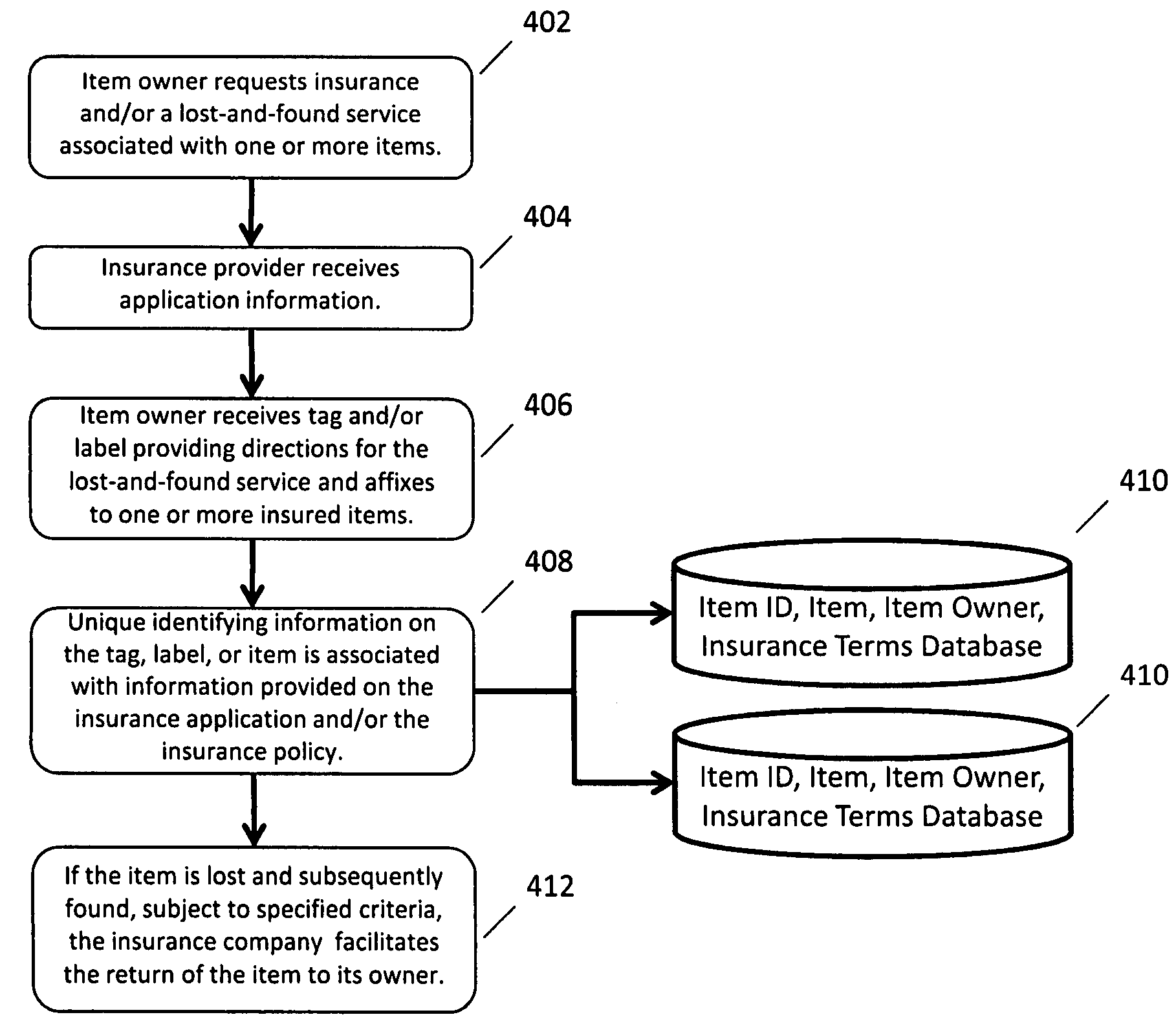
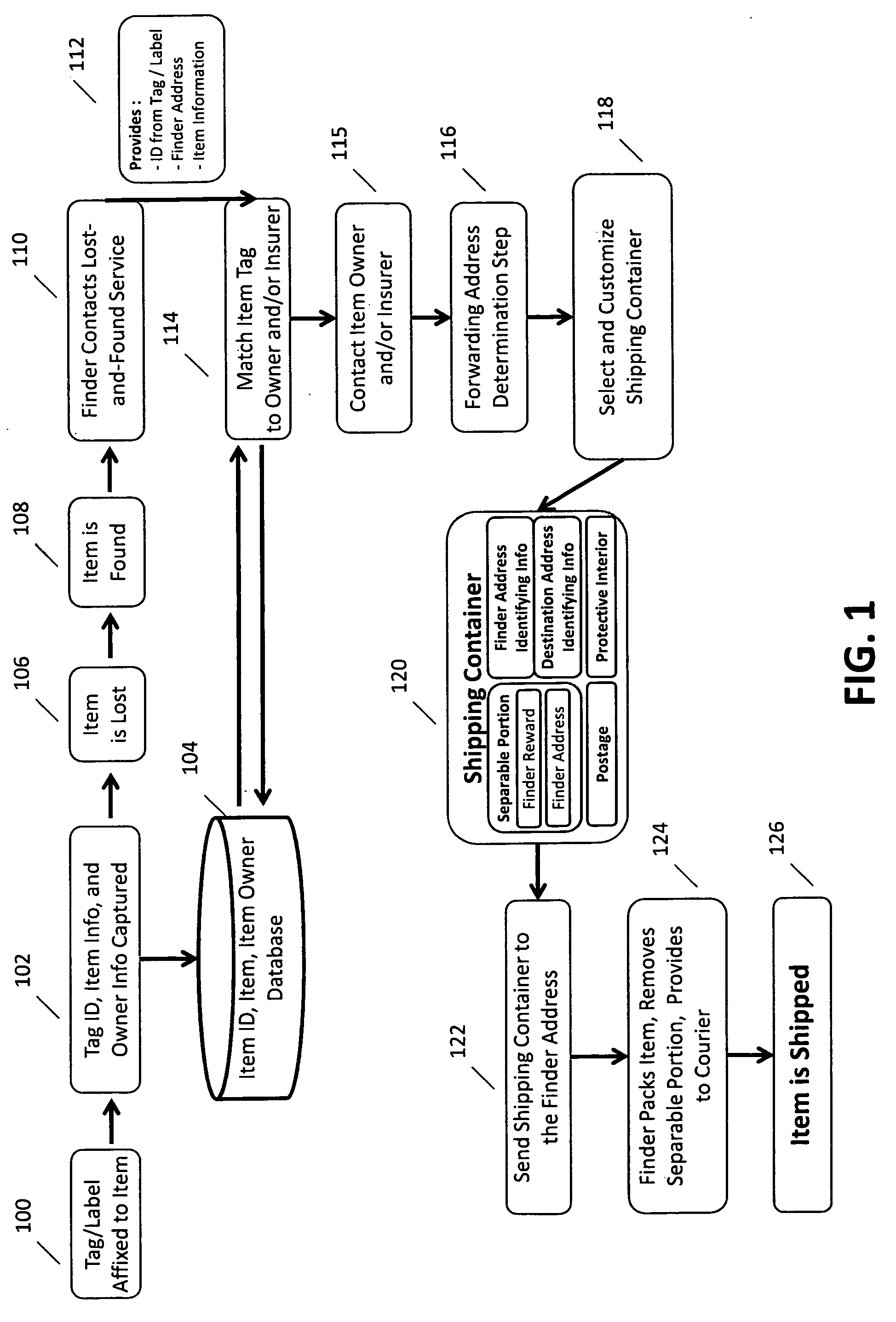
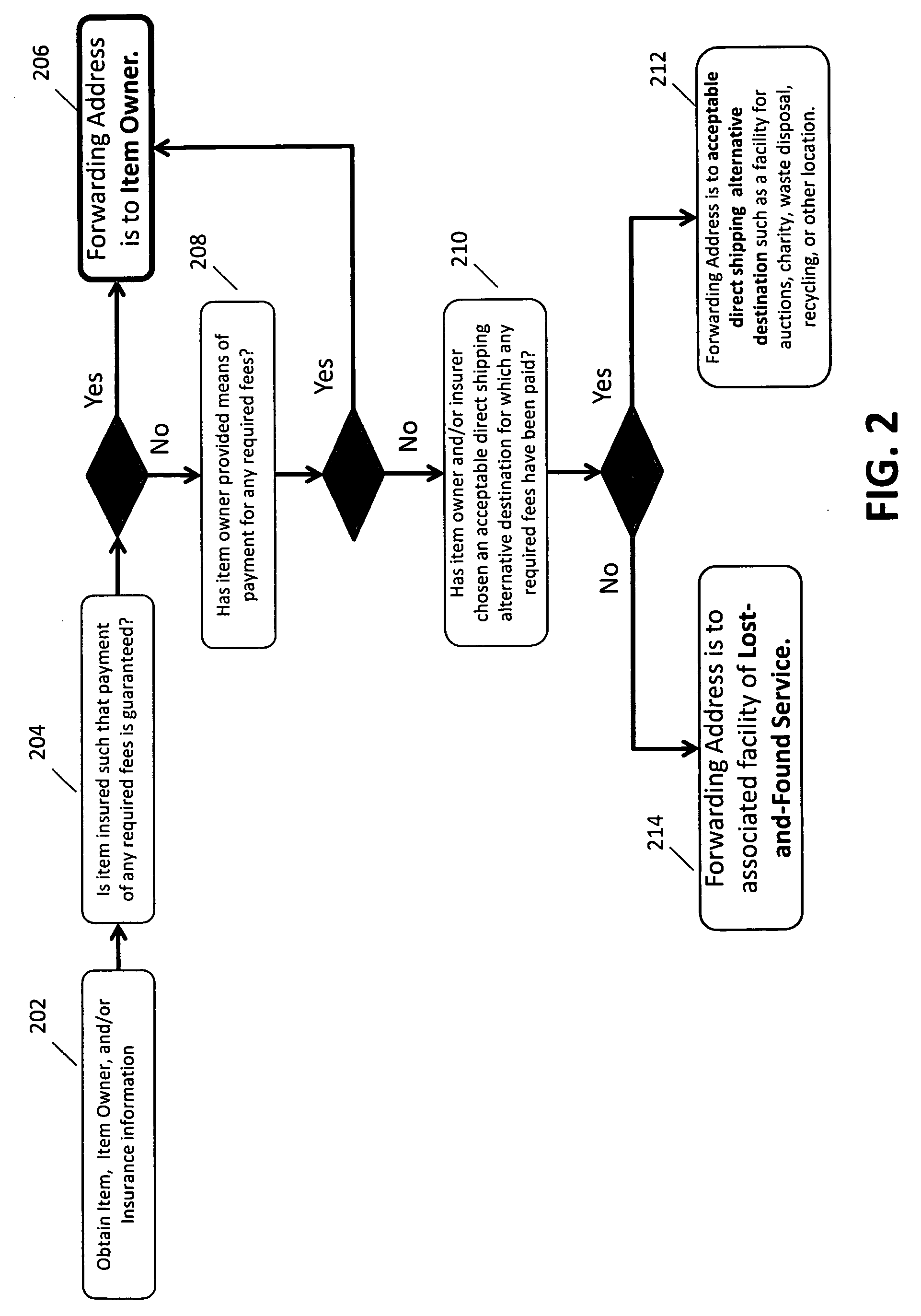
System for providing insurance associated with a lost-and-found service
A system for providing insurance associated with a lost-and-found service, according to which a person and / or item (the “insured”) is covered by an insurance policy that provides compensation in the event of at least one of loss, theft, damage, and / or destruction of an item, and in association with said insurance, also receives one or more services that facilitate the return of the item if it is lost or stolen. The insurance policy pays for the facilitation of the return of an item if it is lost by the insured and subsequently found and reported to a lost-and-found service provider. The insured pays the insurance provider a deductible for the return of the previously insured and / or lost item. Also, a lost-and-found service provider is reimbursed by the insurance provider when an item is lost in exchange for providing the services of identifying the insured using unique markings contained on a lost item owned by the insured, contacting the person associated with the item, contacting the insurance service provider (which may or may not be the same as the lost-and-found service provider), and / or facilitating the return of the lost item to the owner or insurance provider. Registering for an insurance policy also facilitates registering for the services of a lost-and-found service provider.
Owner:NUDD GEOFFREY H
Memory card
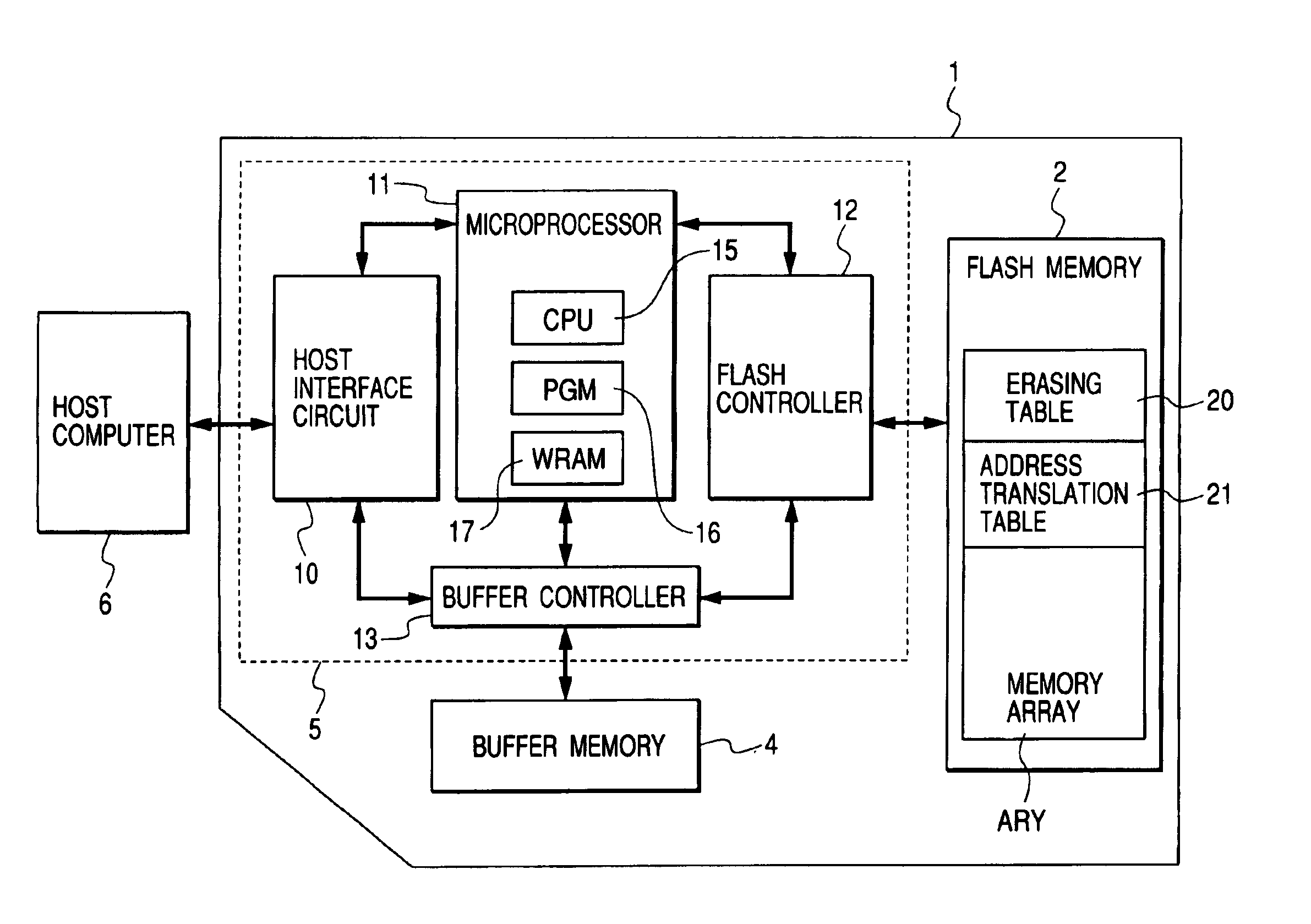
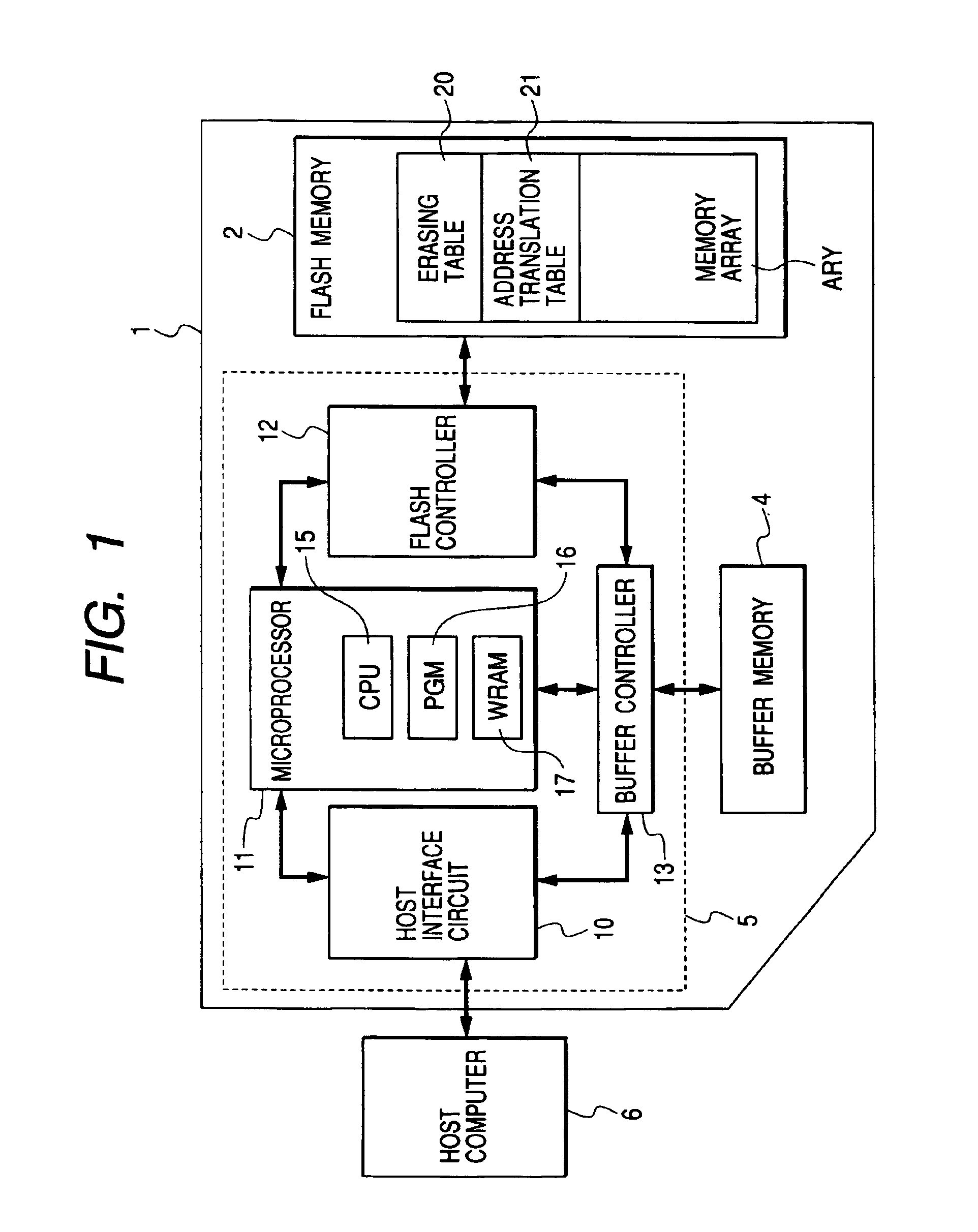
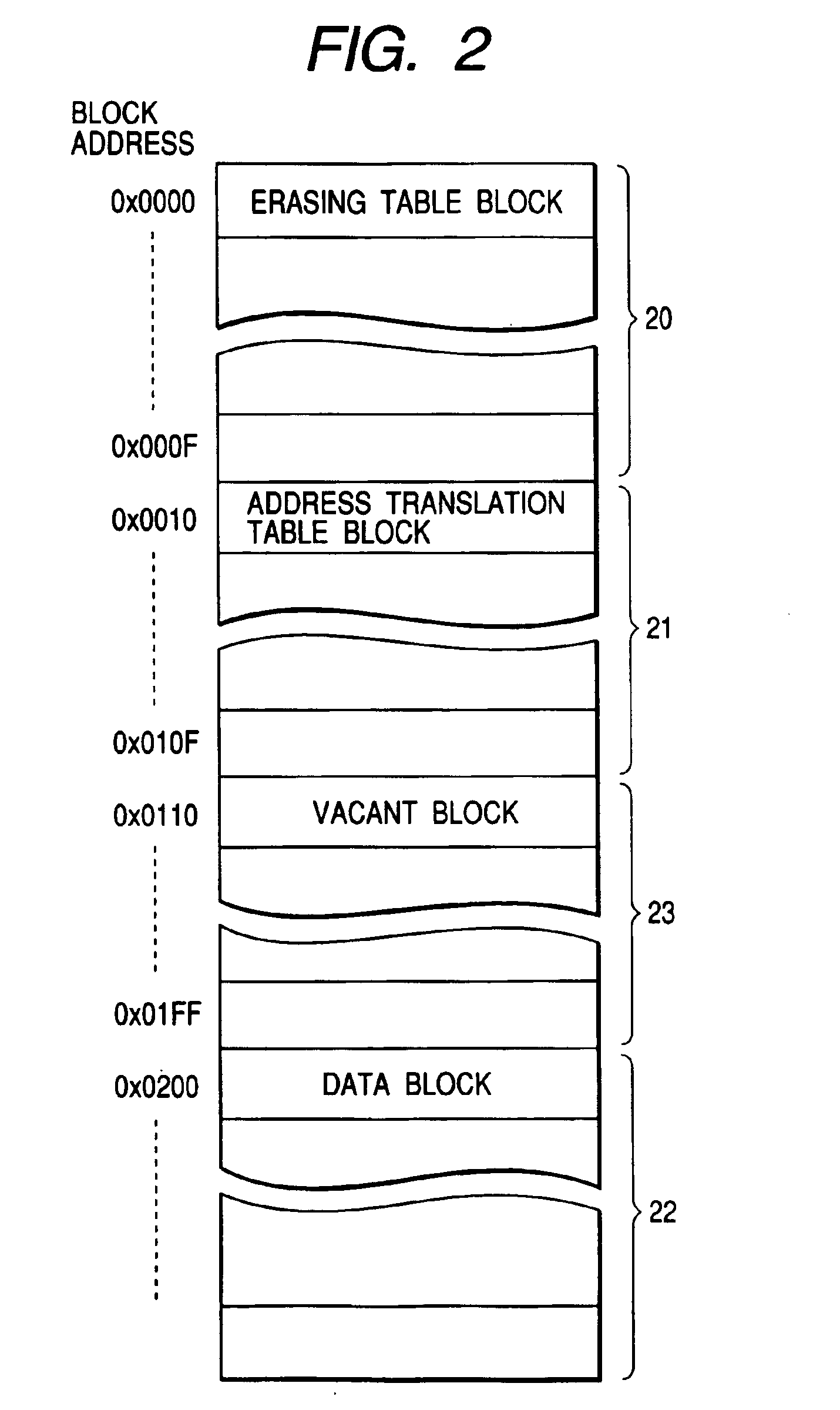
ActiveUS7061812B2High-speed data writing operationData recoveryMemory architecture accessing/allocationMemory adressing/allocation/relocationControl circuitMemory cards
Disclosed is a memory card which ensures high-speed data writing operations. The memory card is formed of an erasable and programmable nonvolatile memory and a control circuit. A memory array of the nonvolatile memory has an erasing table including a first flag designating whether a memory area is a vacant area or not in every erasing unit. The control circuit exercises, when the number of memory areas in which the erasable data is written becomes a constant value, pre-erasing control to previously erase the erasable data over the memory area depending on the first flag indicating a vacant area. Since the erasing process is previously executed to the vacant memory area, necessity for insertion of the erasing process just before the writing process using the vacant memory area can be reduced and thereby writing data to the memory card can be highly speeded.
Owner:RENESAS ELECTRONICS CORP
Method of and apparatus for reducing power consumption in a mobile telephony system
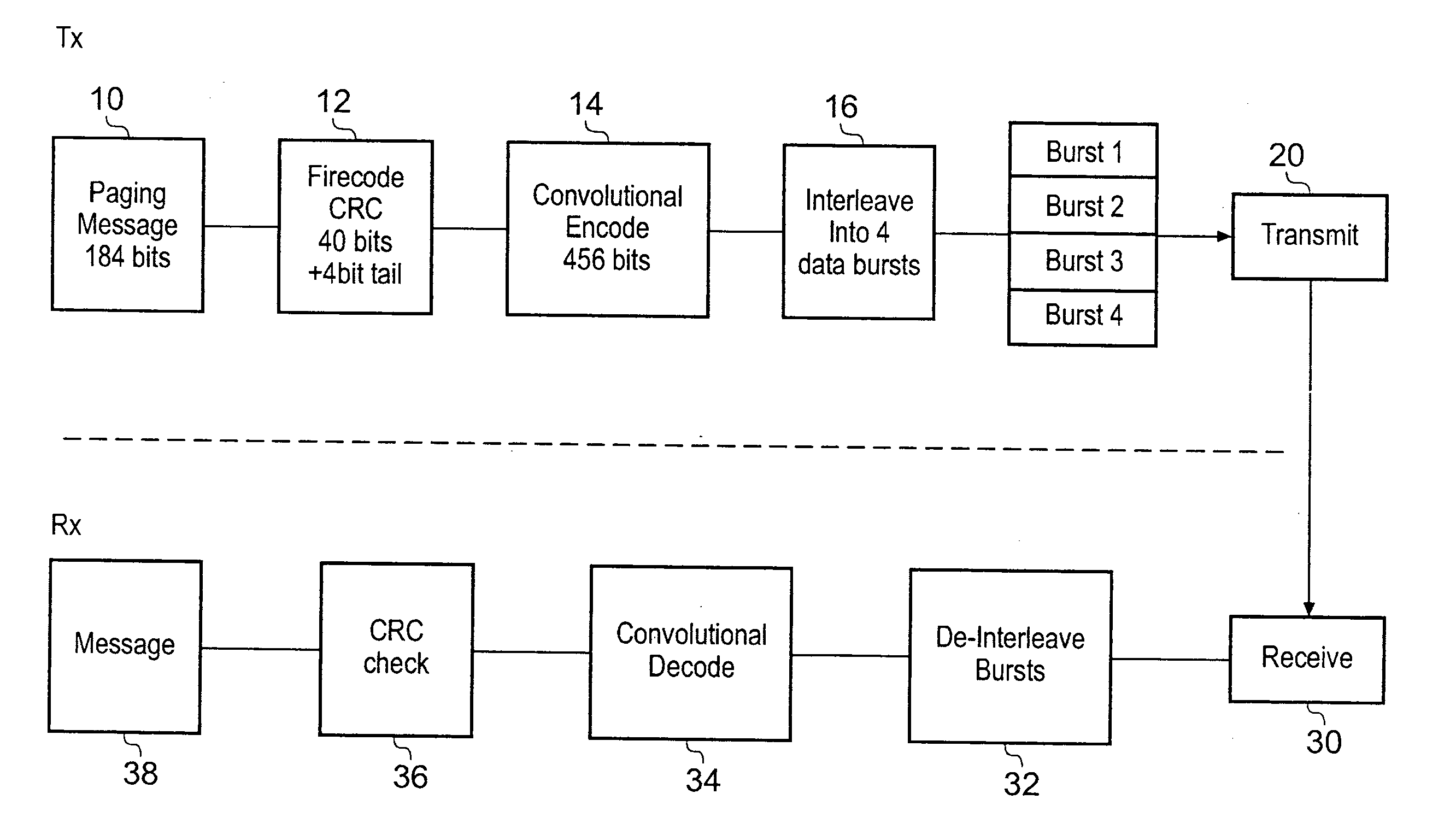
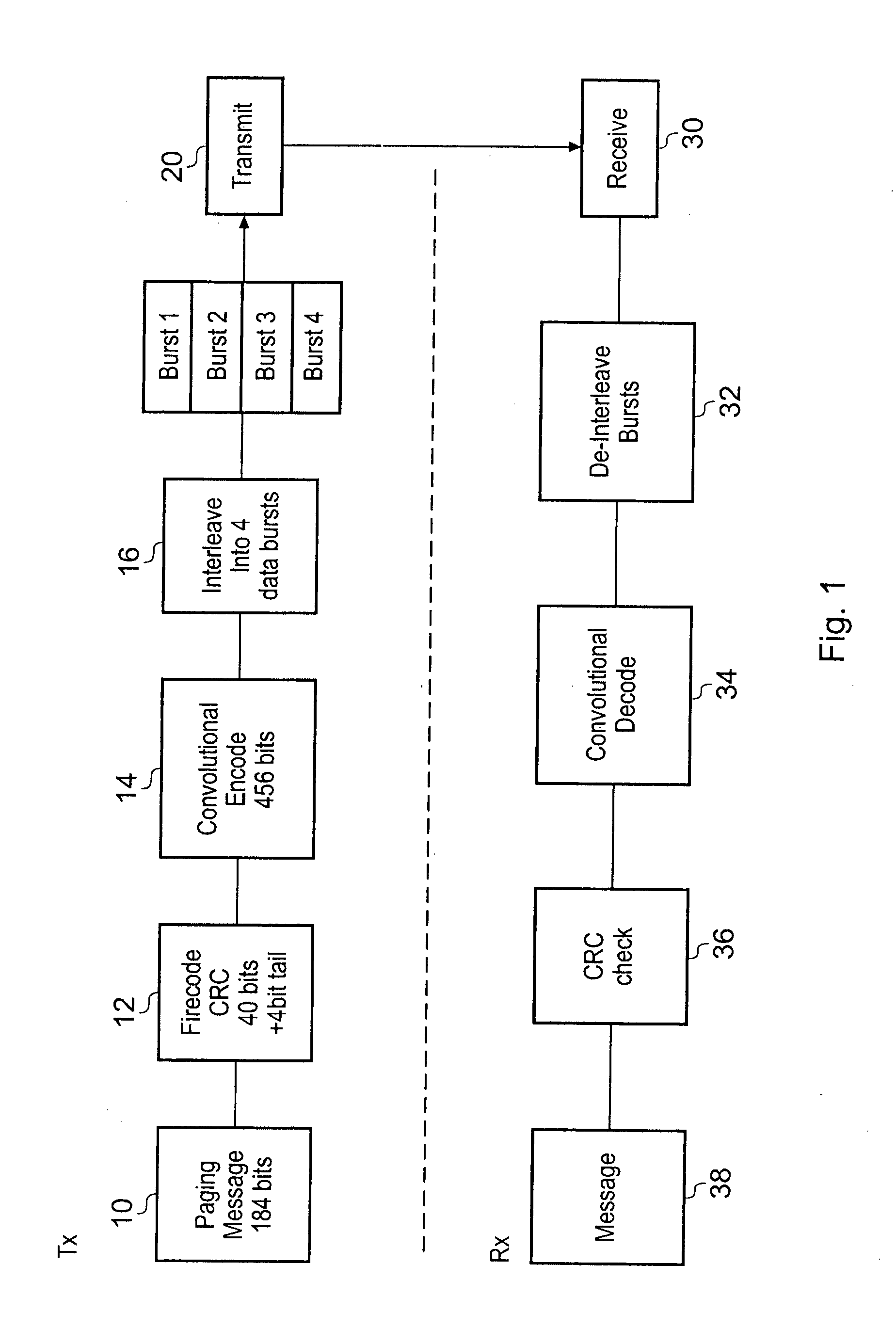
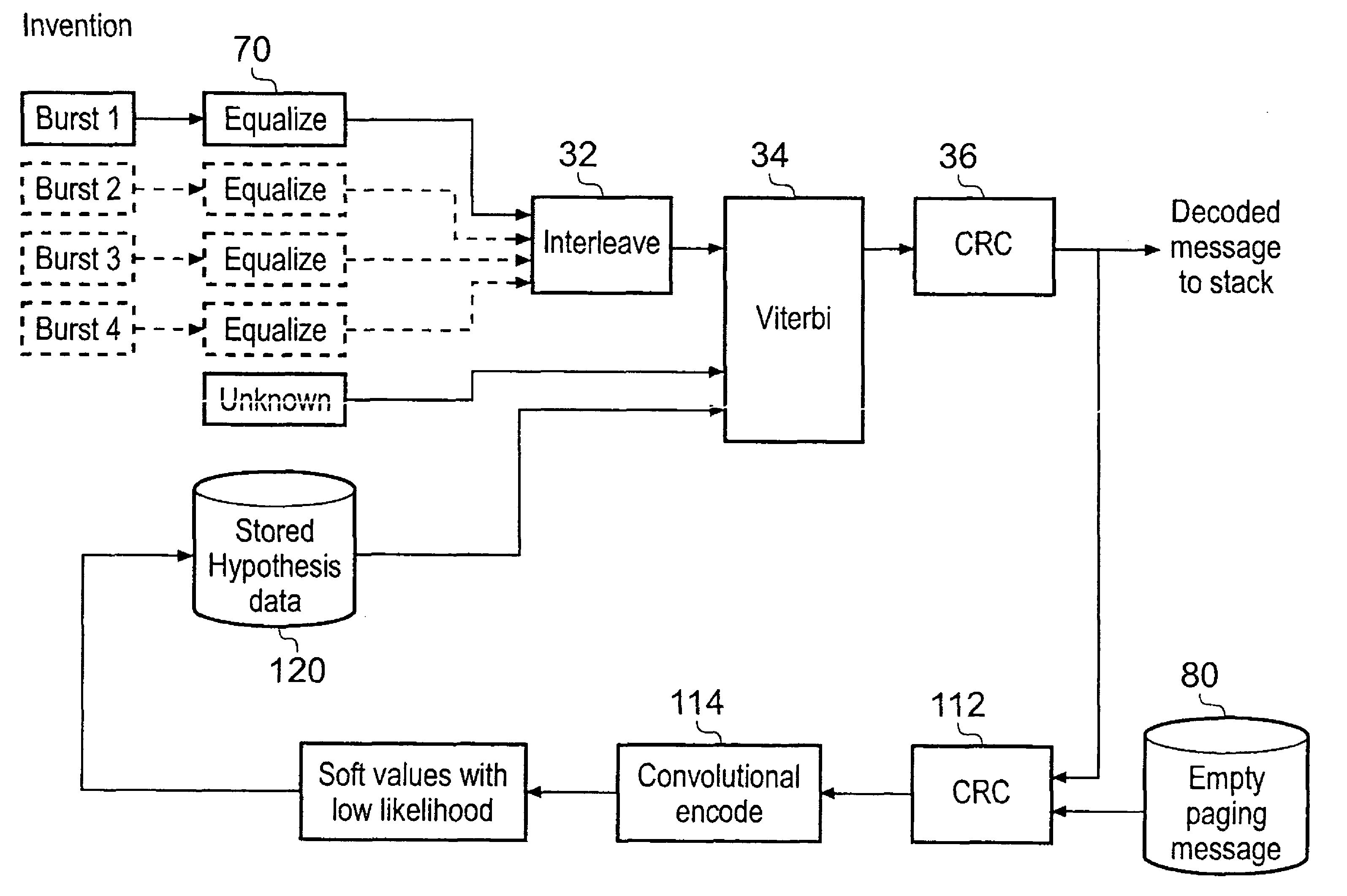
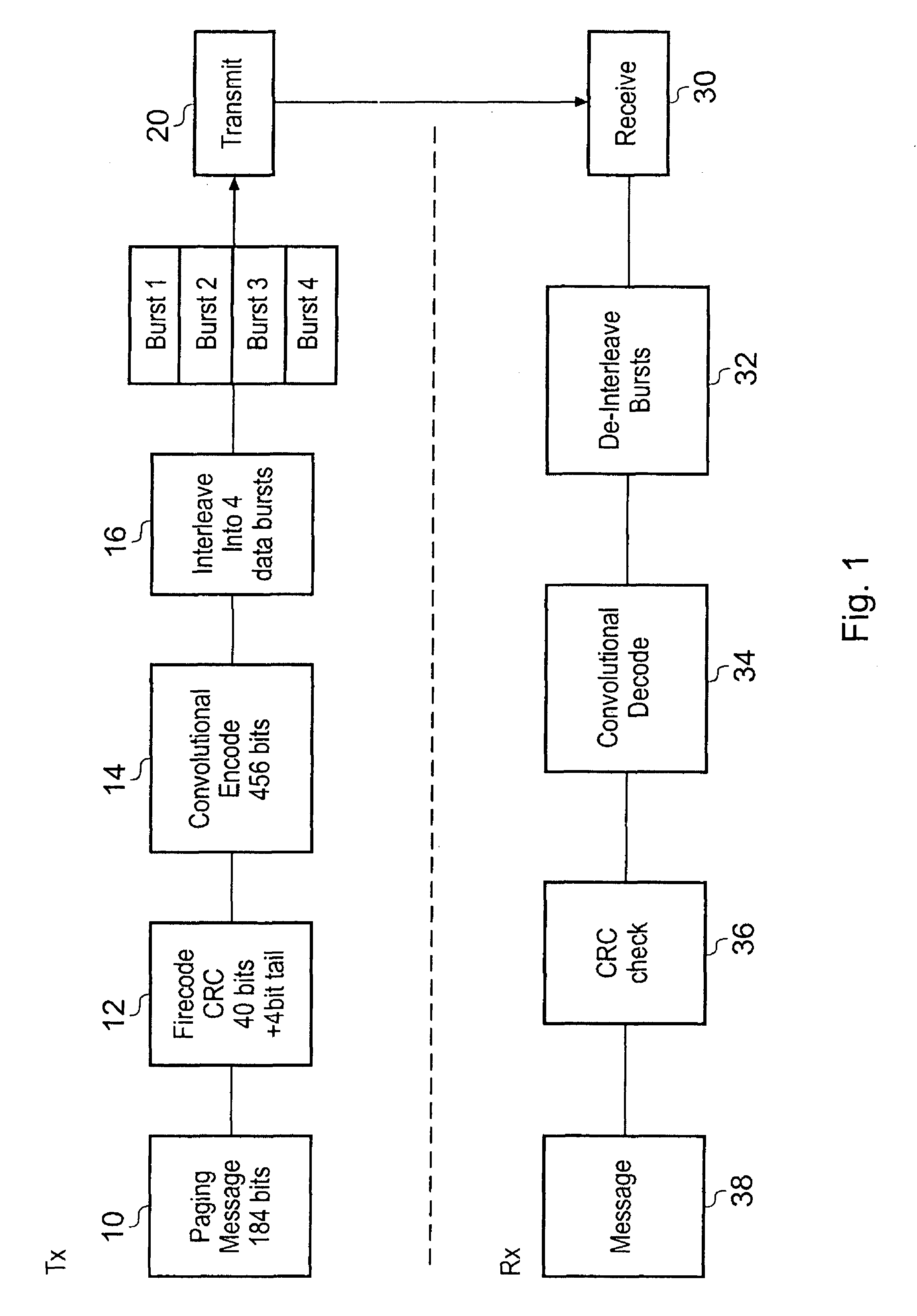
ActiveUS20080311947A1Great dealEnhanced resistance to error bursts occurringPower managementEnergy efficient ICTMobile Telephone ServiceComputer science
A method of decoding data comprising a plurality of data-bursts, comprising the steps of:i) receiving a first one of the data-bursts,ii) associating hypothesis data with the or each received data-bursts;iii) attempting to decode the data; andiv) if the decode is successful to power down the receiver, and if the decode is unsuccessful receiving a further one of the data-bursts and repeating steps ii) to iv), until all of the data has been received.
Owner:MEDIATEK INC
Method, medium and system for recovering data using a timeline-based computing environment
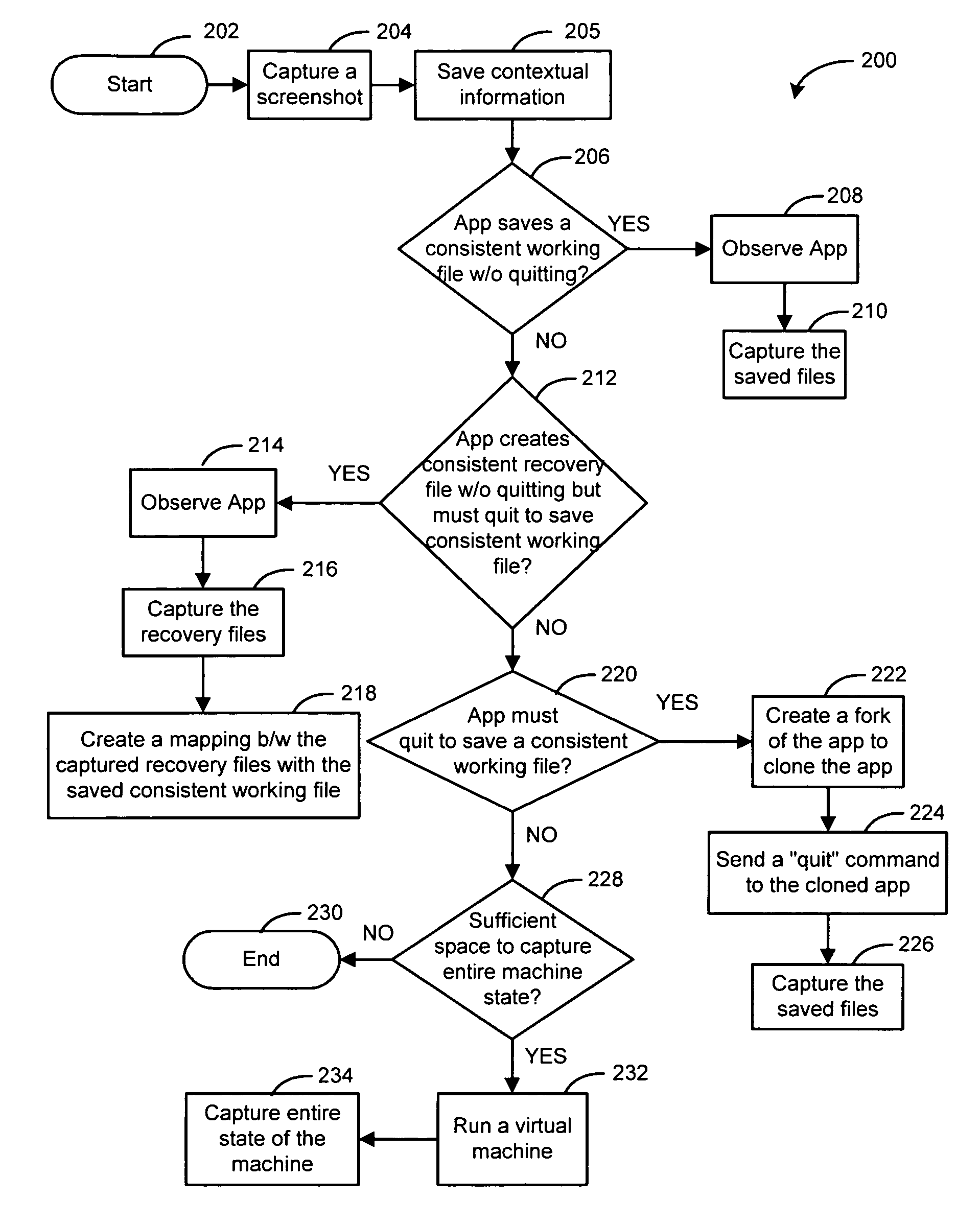
InactiveUS7353241B2User friendly, effective, and manageableSimple and intuitive graphical representationData processing applicationsProgram control using stored programsImproved methodApplication software
The present description discloses a technique for recovering data using a timeline-based computing environment. Data items of the application are periodically saved for recovery such that the saved data items can be used to recover the application at a point in time when the items are saved. As a result, a search through a time-based computing environment is provided to recover the application at different points in time. The application with the saved data items can then be recovered at a designated point in time. Each saved data item can also be indexed with metadata, which are used to conduct a search to generate a list of data items according to a match between the indexed metadata and a user selected variable. Moreover, when the application is a communication client having multiple messages, an index data to indicate whether a message in the communication client is spam is saved. Using this index data, a search that includes or excludes the spam messages can then be conducted. Thus, using a timeline-based computing environment, an improved method and system of recovering data that is more user friendly, effective, and manageable is thus provided.
Owner:MICROSOFT TECH LICENSING LLC
Data storage method and device
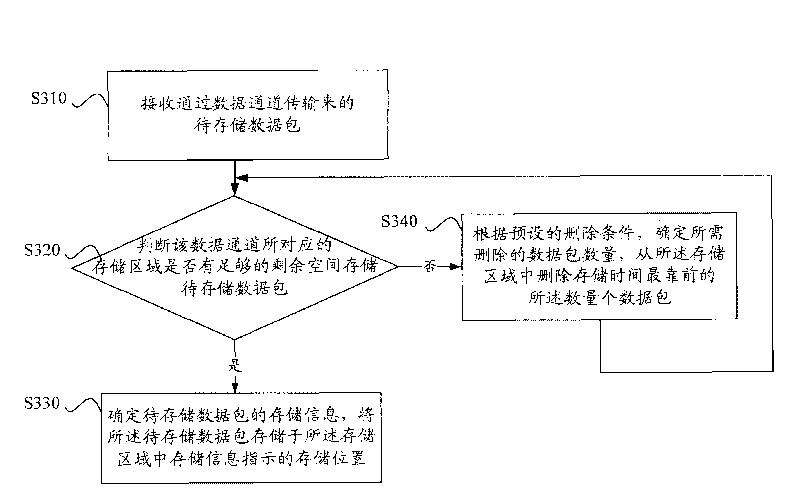
ActiveCN101714391AStable storageImprove data storage efficiencyElectronic editing digitised analogue information signalsCarrier indexing/addressing/timing/synchronisingNetwork packetStorage efficiency
The invention discloses a data storage method and device. The method comprises the following steps: receiving a data pack which is needed to be stored and transmitted from a data channel, judging whether enough residual space for storing the data pack to be stored is in a storage area corresponding to the data channel; if so, determining the storage information of the data pack, storing the data pack in the storage place of the storage area according to the indication of the storage information; if not, determining the number of data packs needed to deleted according to preset conditions, deleting the same number of data packs with earliest storage time in the storage area, and then executing the judgment operation. The data storage method and device can not generate fragment during the data storage process and increase the stability and efficiency of the data storage.
Owner:NETPOSA TECH
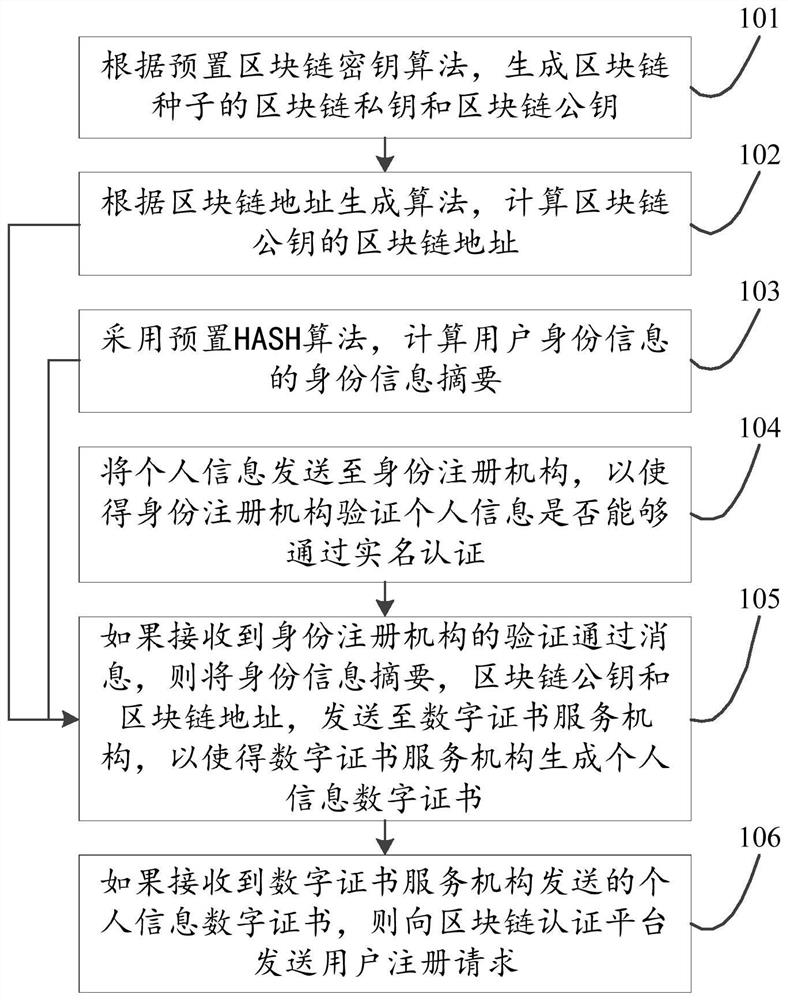
Identity authentication method and device based on user identification module and blockchain technology
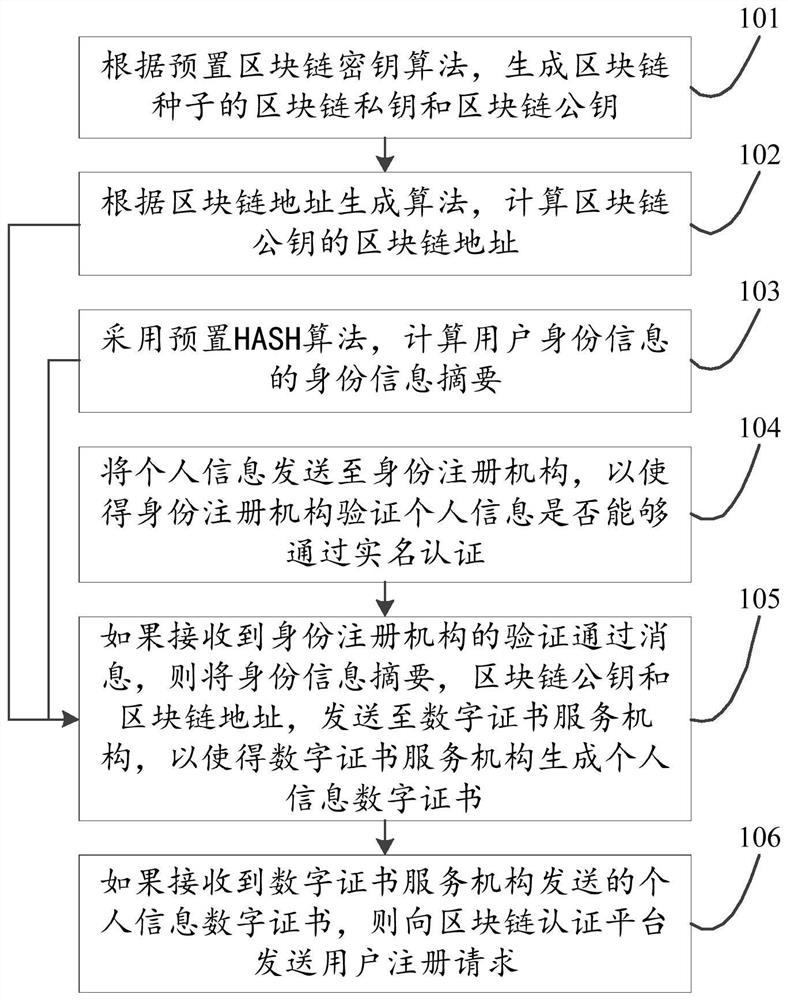
ActiveCN111859348AData RecoveryDigital data protectionDigital data authenticationRegistration authorityInternet privacy
The invention discloses an identity authentication method and device based on a user identification module and the blockchain technology, relates to the technical field of blockchain, and is inventedfor solving the problems of blockchain key storage and use security in the prior art. The method mainly comprises the following steps: generating a blockchain private key and a blockchain public key of a blockchain seed according to a preset blockchain key algorithm; calculating a blockchain address of the blockchain public key according to an address generation algorithm; calculating an identityinformation abstract of the user identity information by adopting a preset HASH algorithm; sending the personal information to an identity registration institution, so that the identity registration institution verifies whether the personal information can pass real-name authentication or not; if the verification is passed, sending the identity information abstract, the blockchain public key and the blockchain address to a digital certificate service institution; if the personal information digital certificate sent by the digital certificate service mechanism is received, sending a user registration request to the blockchain authentication platform. The method and the device are mainly applied to a blockchain user identity authentication process.
Owner:上海微位可信互联安全科技有限公司
Method and System for Insuring Data Integrity in Anticipation of a Disaster
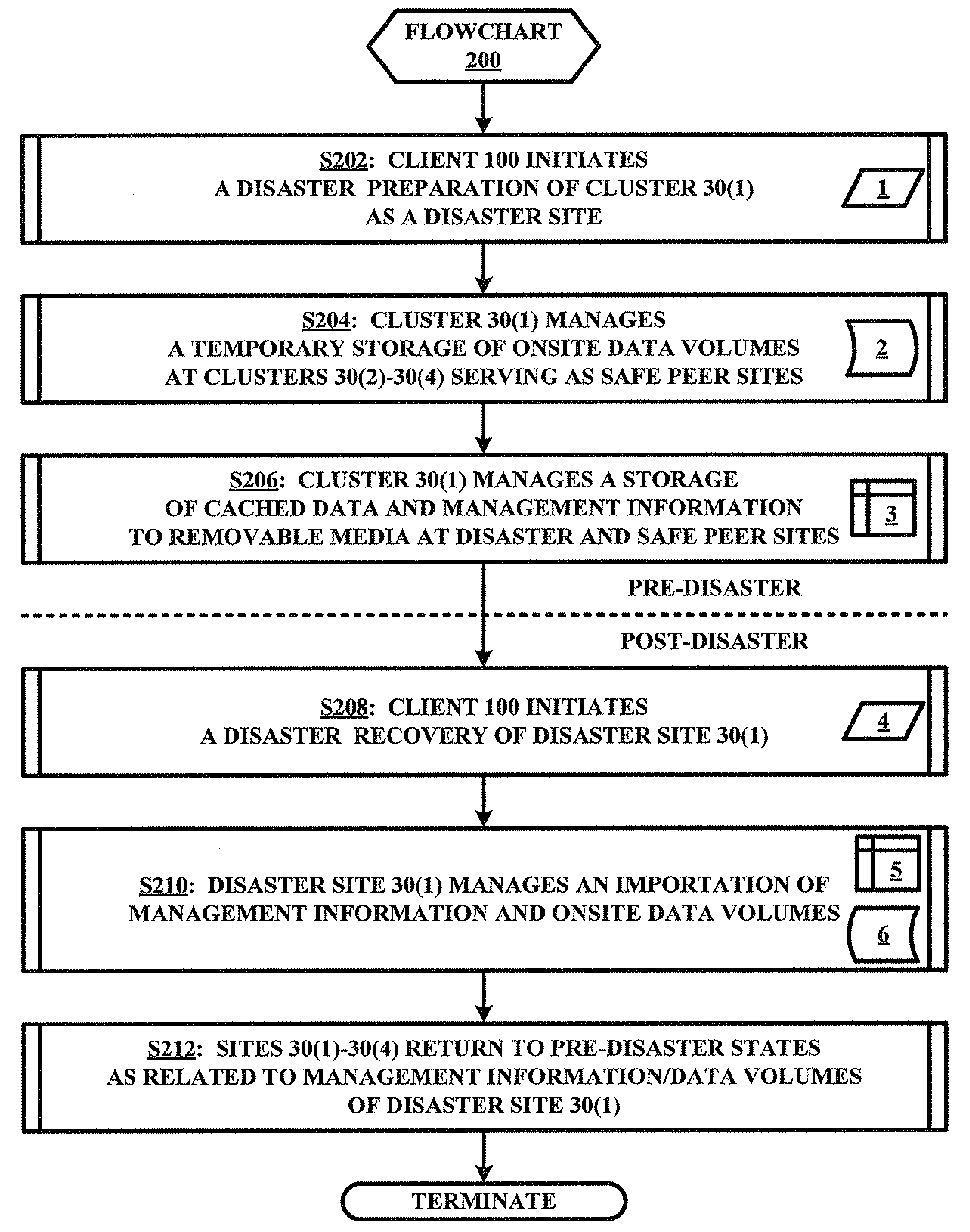
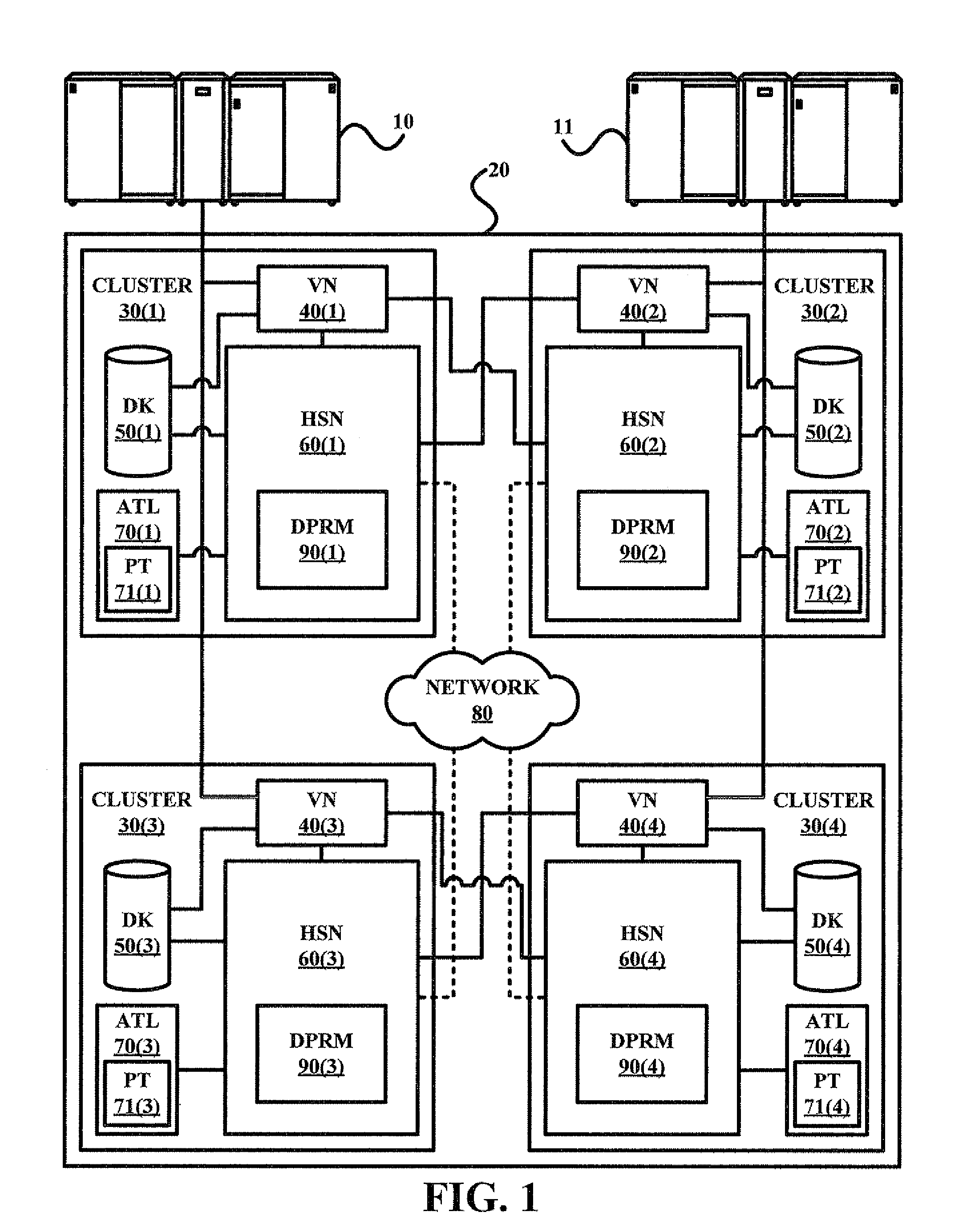
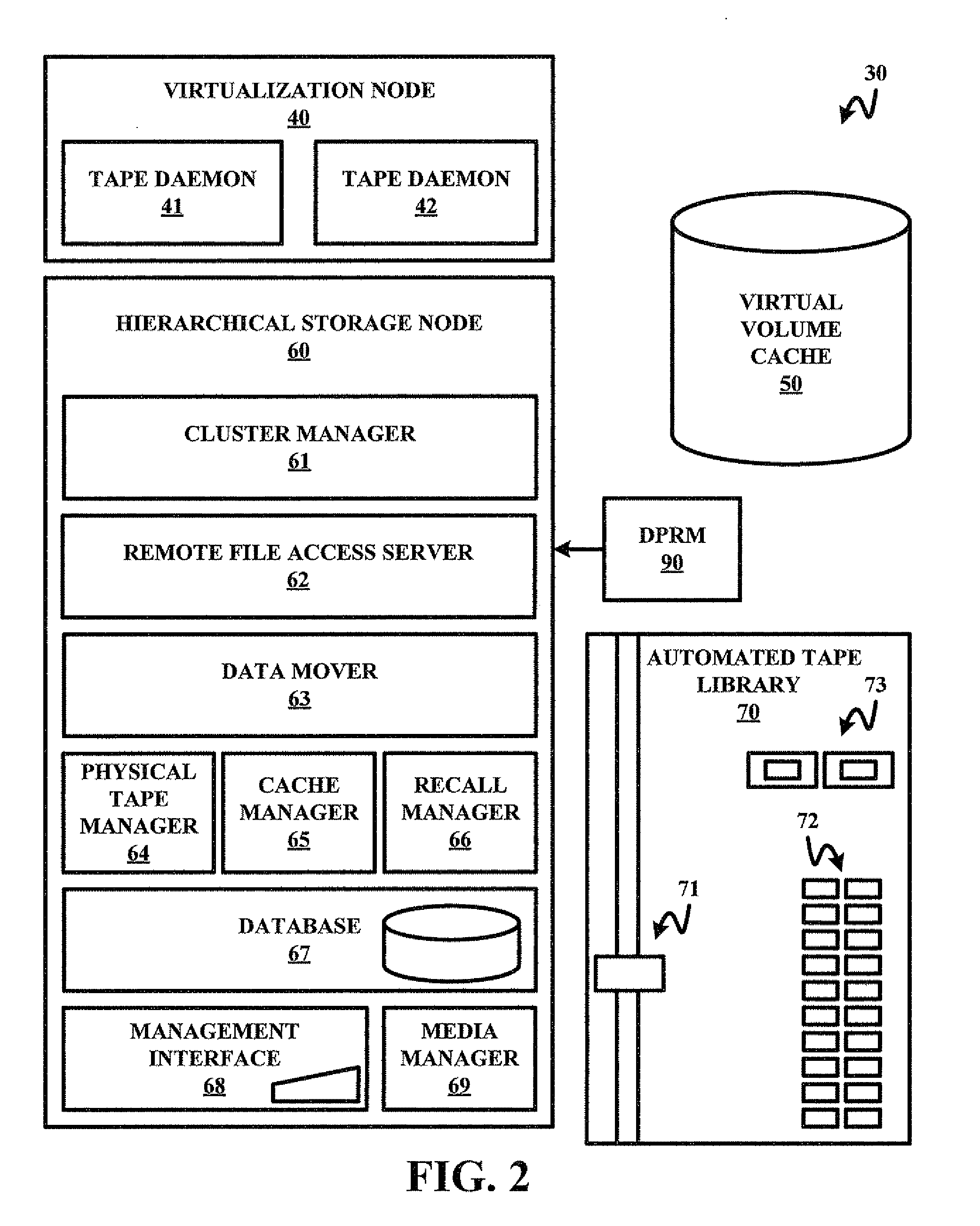
ActiveUS20080250214A1Data recoveryProtect dataError detection/correctionMemory systemsClient-sideRemovable media
A preparation of a storage system of a pending disaster at an onsite location of the storage system involves the storage system receiving a disaster preparation initiation from an offsite client. In response to receiving the disaster preparation initiation from the offsite client, the storage system to executes disaster preparation of onsite data including managing a temporary storage of onsite data volumes to at least one peer site, managing a storage of onsite cached data to a first onsite removable media, and / or managing a storage of onsite management information to a second onsite removable media.
Owner:TWITTER INC
Techniques for modifying image field data obtained using illumination sources
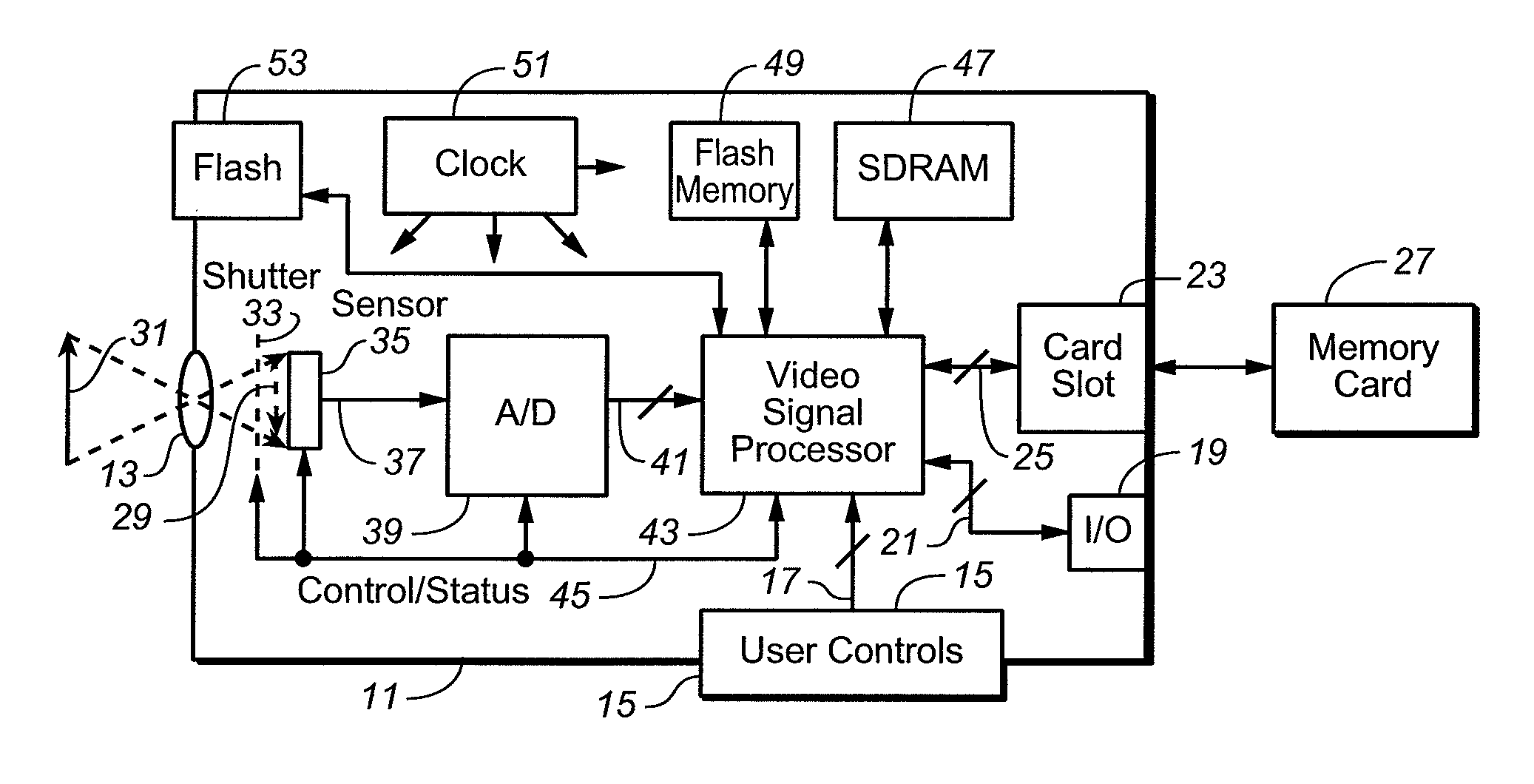
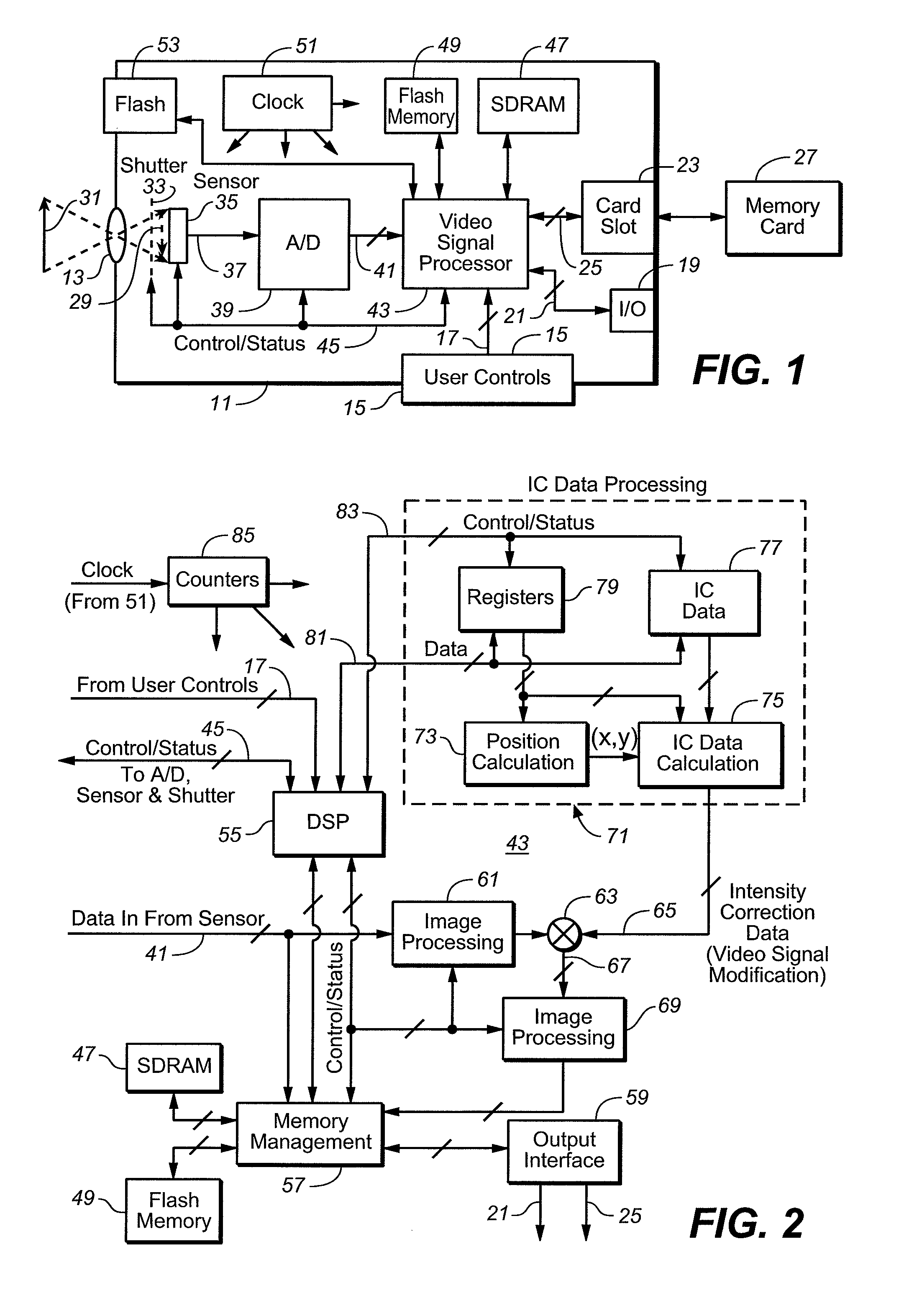
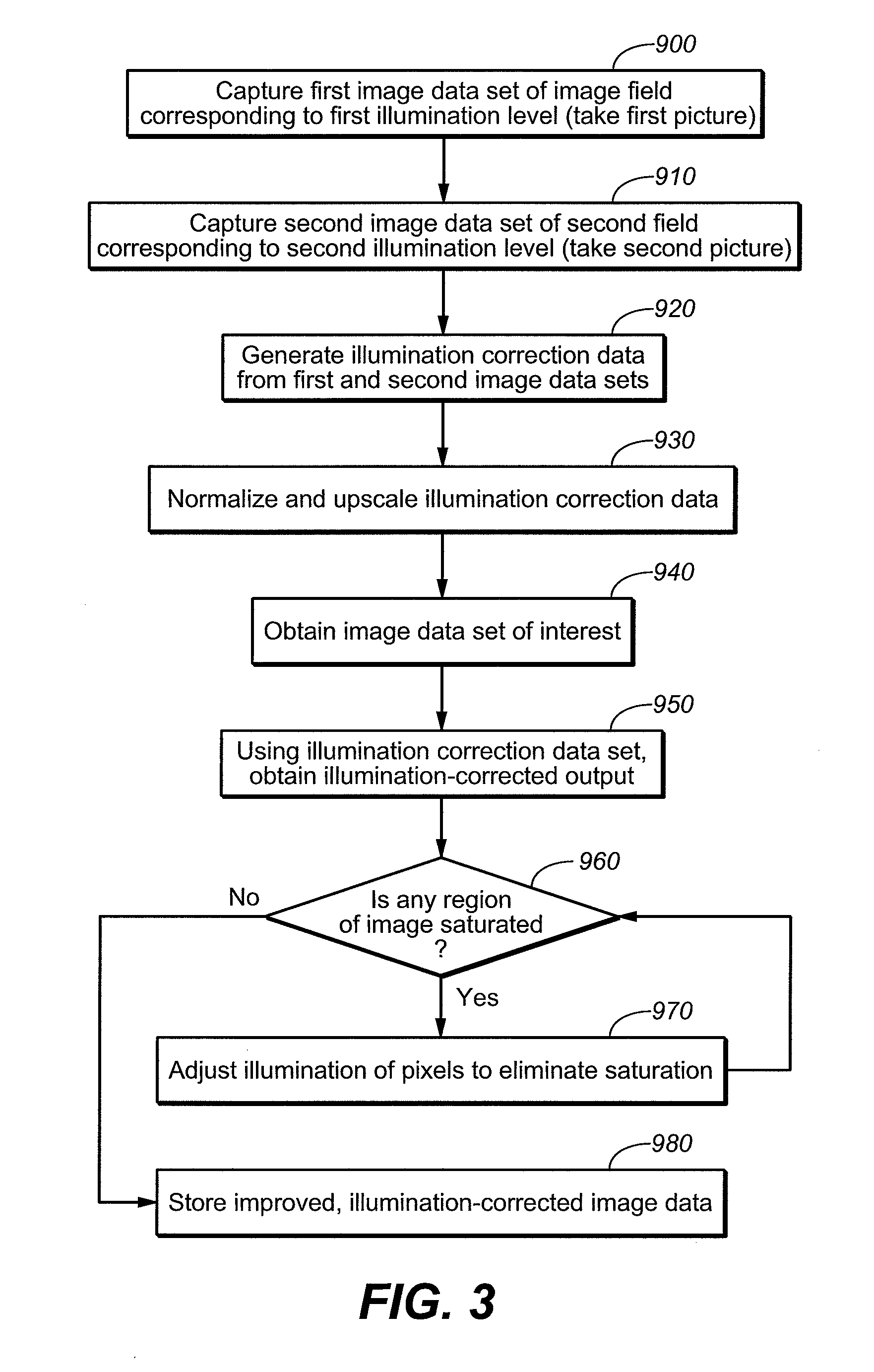
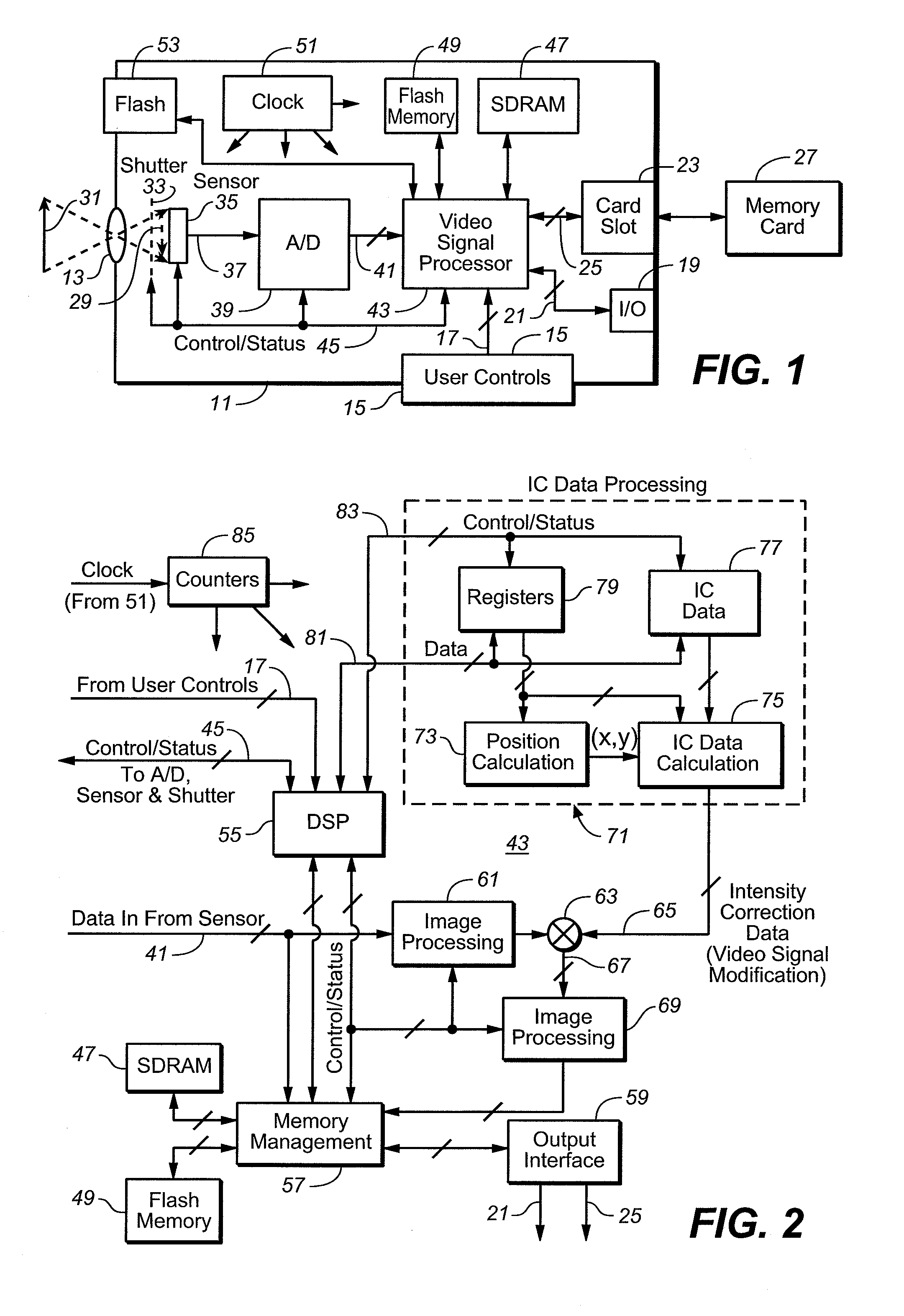
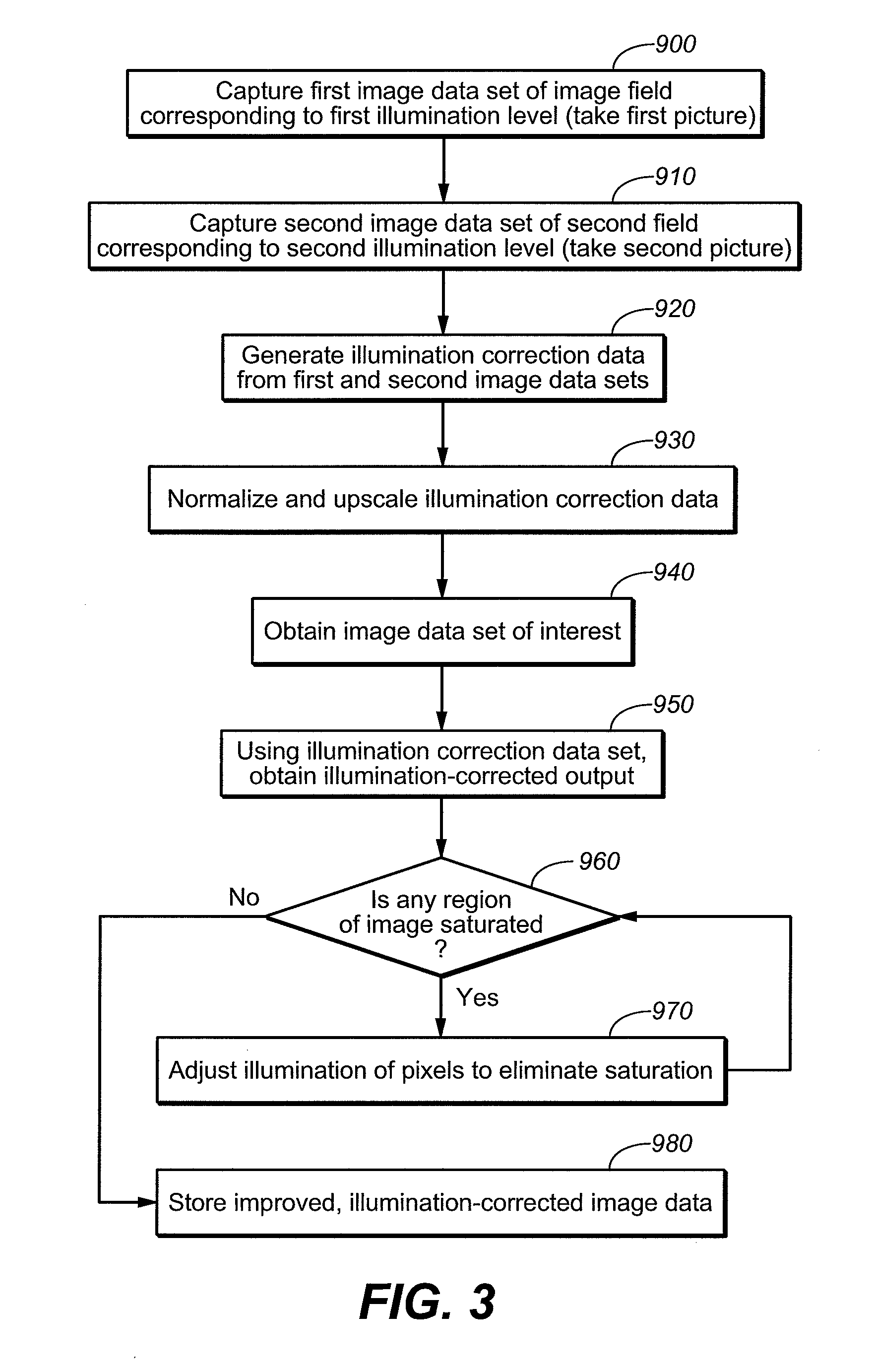
InactiveUS7755672B2Low costNot adversely performanceTelevision system detailsColor signal processing circuitsImage resolutionVideo image
Techniques for modifying data of an image that can be implemented in a digital camera, video image capturing device and other optical systems are provided to correct for non-uniform illumination and / or effects of saturation appearing in data obtained using one or more artificial illumination sources. In an implementation, correction factors are derived using data from at least two images that have been captured with different illumination levels of the object scene and close in time to the capture of the image of interest. Typically, the image of interest is of higher resolution than at least one of the at least two images.
Owner:QUALCOMM INC
Power failure recovery method
InactiveUS20060013085A1Data recoveryTelevision system detailsFilamentary/web record carriersComputer hardwareRecovery method
The present invention relates to a method of recovering blocks of data recorded on an optical record carrier in case of a power failure affecting a recording and reproducing device. Said device comprises means for writing a recording indication information on the optical record carrier to indicate that a recording has started, said recording indication information including a recording start address, and means for overwriting the recording indication information at a recording end. After a power failure, if a recording indication information is written on the optical record carrier, then the recording and reproducing device is able to determine that a recording has not ended properly. In these conditions, said device is able to parse the recorded data, starting from the recording start address, in order to find the end of the improperly ended recording.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
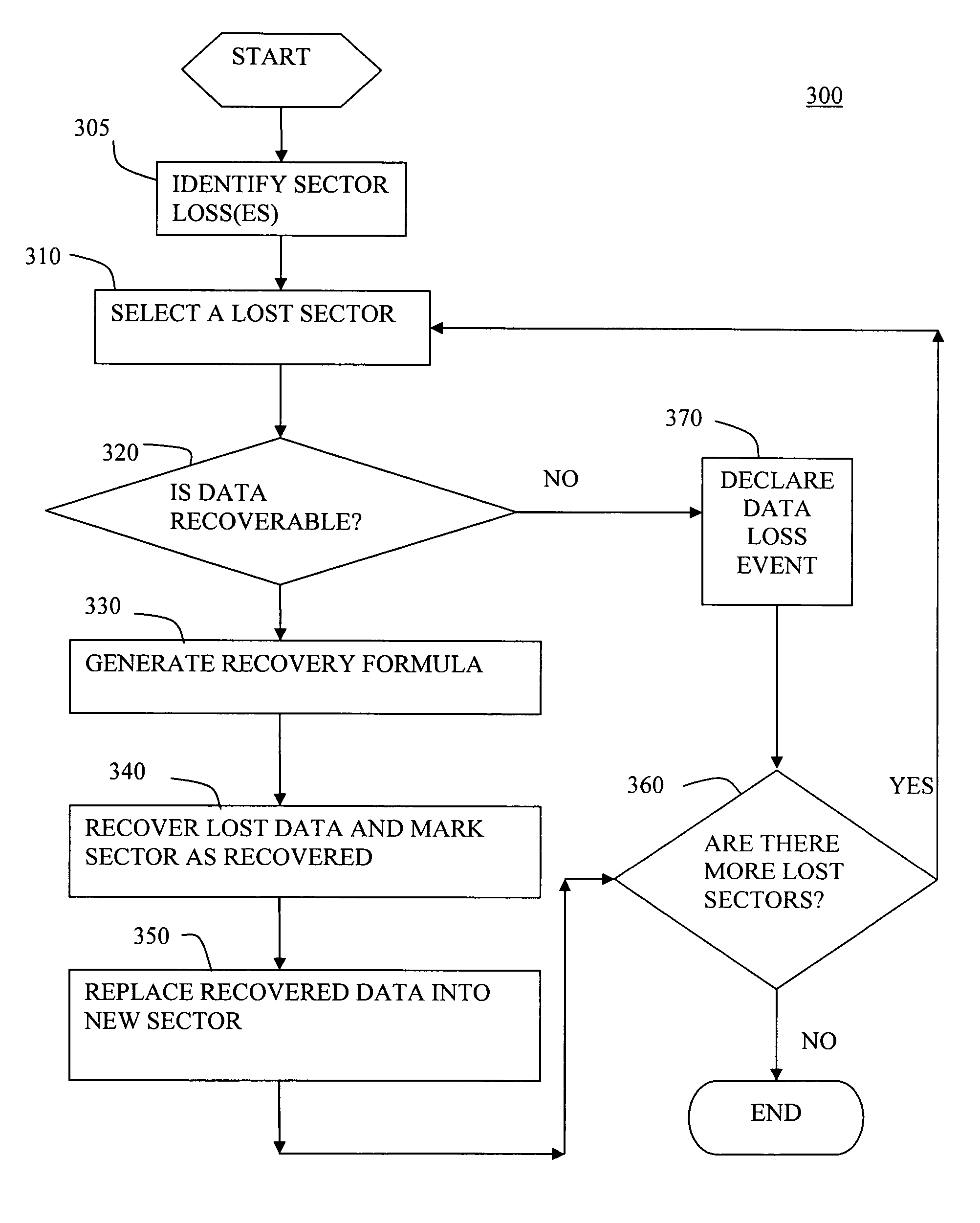
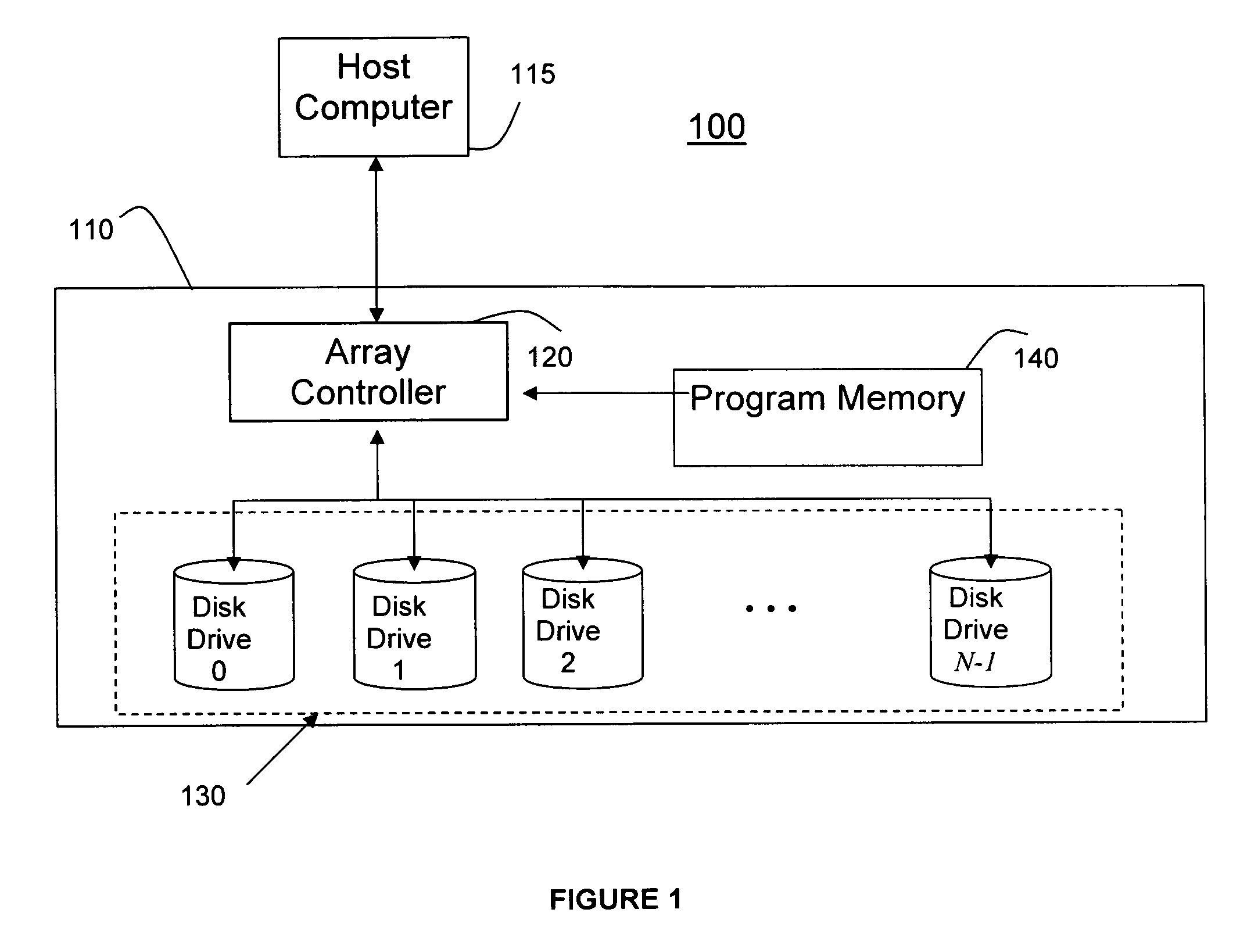
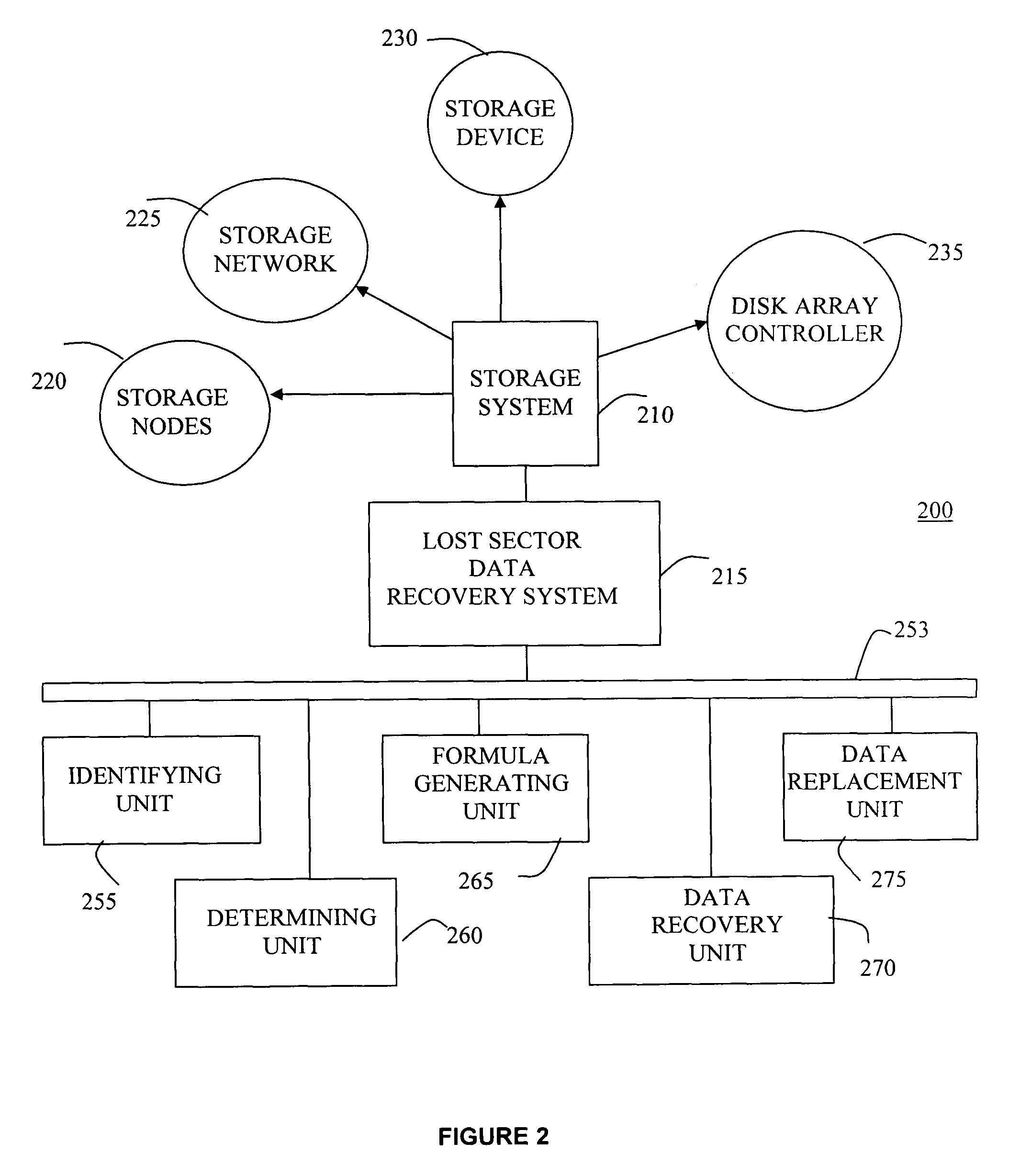
System and method for recovery of data for a lost sector in a storage system
InactiveUS7870464B2Data recoveryError detection/correctionCode conversionComputer scienceEmbedded system
A system (and method) for a recovery of data from a lost sector in a storage system, which includes a set of readable and lost sectors in a plurality of disks in the storage system, includes identifying a lost sector of at least one disk of the storage system, determining whether the data from the lost sector is capable of being recovered, and, if the data from the lost sector is capable of being recovered, generating a recovery formula for the lost sector and recovering the data from the lost sector based on the recovery formula.
Owner:GLOBALFOUNDRIES INC
Data storage medium with certification data
InactiveUS20040059884A1Ensure safetyAvoid data duplicationDigital data processing detailsRead-only memoriesDigital dataData storing
Owner:KK TOSHIBA
Techniques for Modifying Image Field Data Obtained Using Illumination Sources
InactiveUS20070262236A1Reduce intensityHigh strengthTelevision system detailsColor signal processing circuitsComputer graphics (images)Image resolution
Techniques for modifying data of an image that can be implemented in a digital camera, video image capturing device and other optical systems are provided to correct for non-uniform illumination and / or effects of saturation appearing in data obtained using one or more artificial illumination sources. In an implementation, correction factors are derived using data from at least two images that have been captured with different illumination levels of the object scene and close in time to the capture of the image of interest. Typically, the image of interest is of higher resolution than at least one of the at least two images.
Owner:QUALCOMM INC
Method of recovering data in asynchronous applications
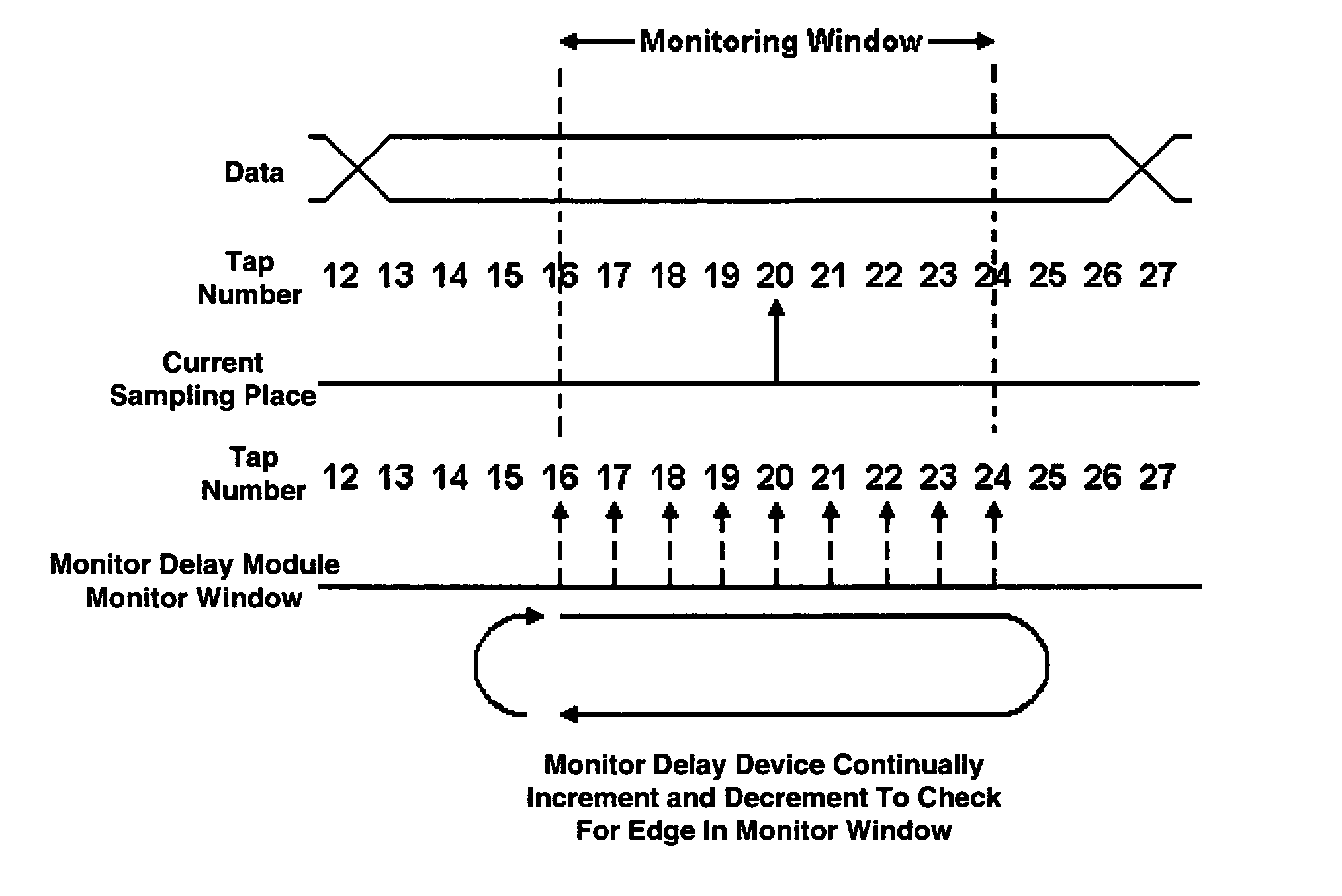
ActiveUS7515664B1Data recoveryMultiple-port networksSynchronisation information channelsAsynchronous communicationData delay
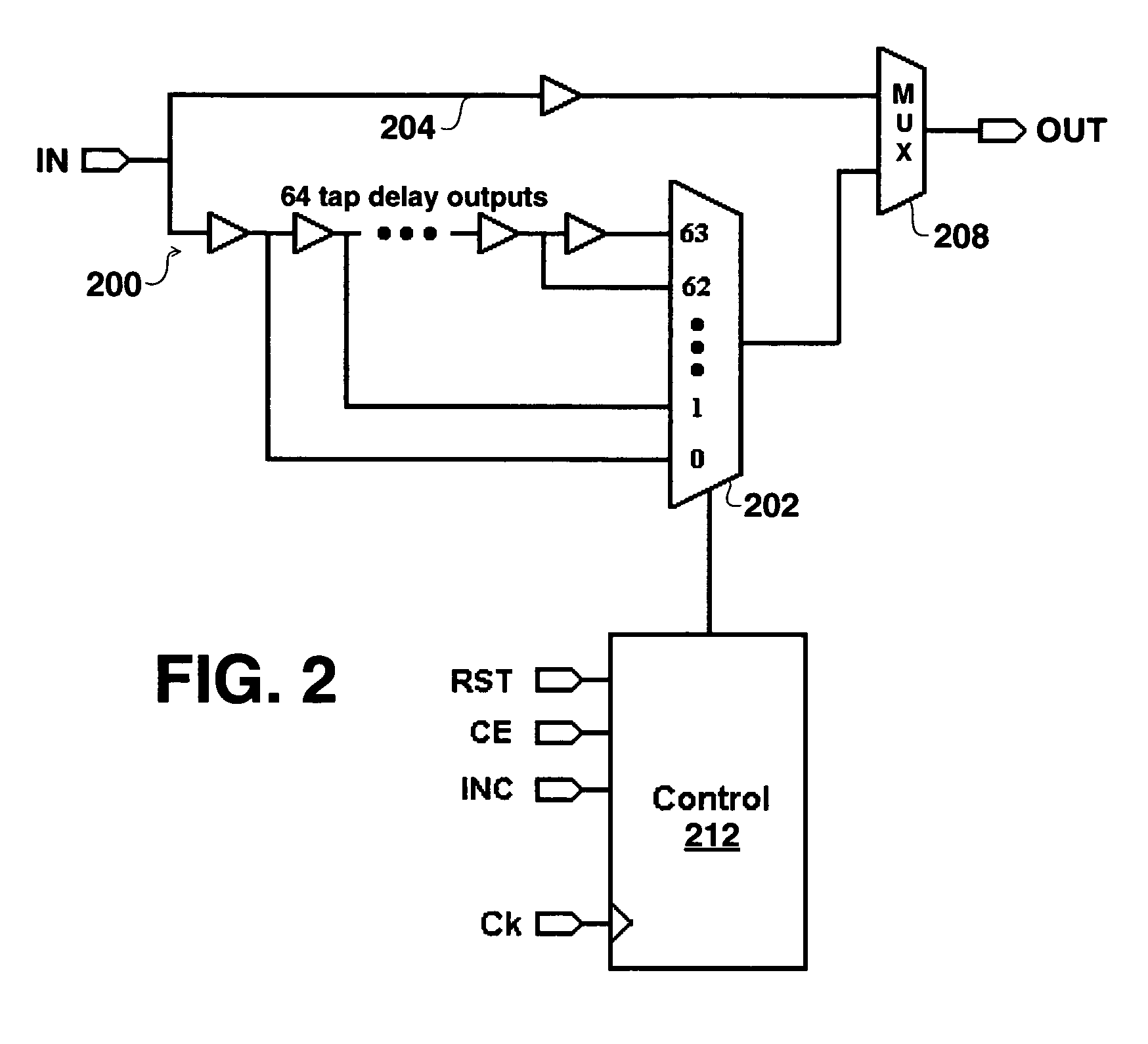
Data is recovered in an asynchronous environment where a sampling clock is generated internally, and is not externally frequency locked, by using programmable delay modules each providing a number of delay tap outputs. To recover data, two of the delay modules are used with a first delay module designated as a monitor delay module to monitor the clock edge transitions, while a second delay module is designated as a data delay module that provides a data output. A controller provides for incrementing or decrementing the tap delay of both delay modules to assure clock data falls at the center of the monitoring window as determined using the monitor delay module. The controller further selects between the two delay modules as to which provides data and which is used as for clock edge monitoring when the clock edge transitions drifts to an edge of the monitoring window.
Owner:XILINX INC
Method of and apparatus for reducing power consumption in a mobile telephony system
ActiveUS7957758B2Great dealEnhanced resistance to error bursts occurringPower managementEnergy efficient ICTMobile Telephone ServiceHypothesis
A method of decoding data comprising a plurality of data-bursts, comprising the steps of:i) receiving a first one of the data-bursts,ii) associating hypothesis data with the or each received data-bursts;iii) attempting to decode the data; andiv) if the decode is successful to power down the receiver, and if the decode is unsuccessful receiving a further one of the data-bursts and repeating steps ii) to iv), until all of the data has been received.
Owner:MEDIATEK INC
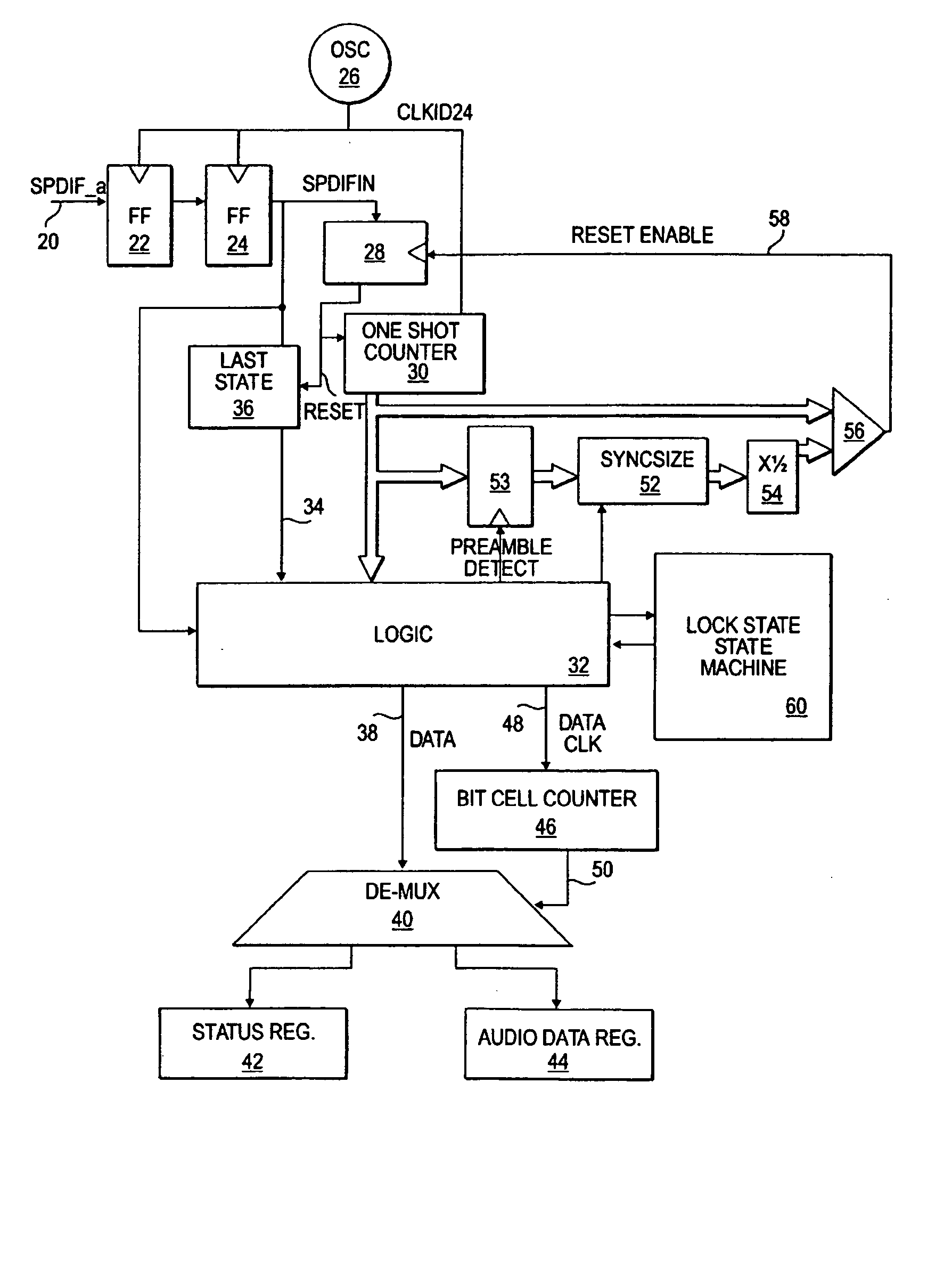
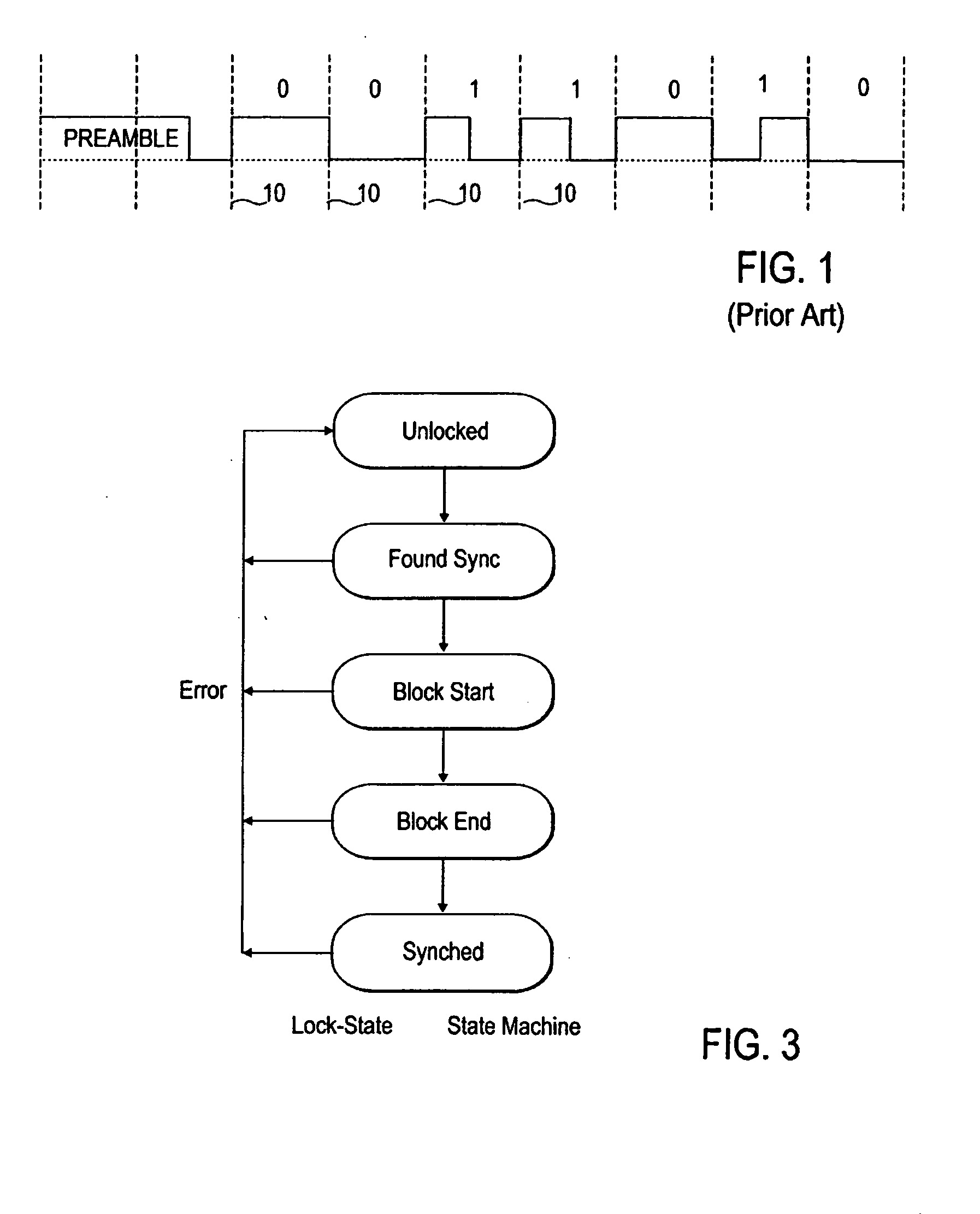
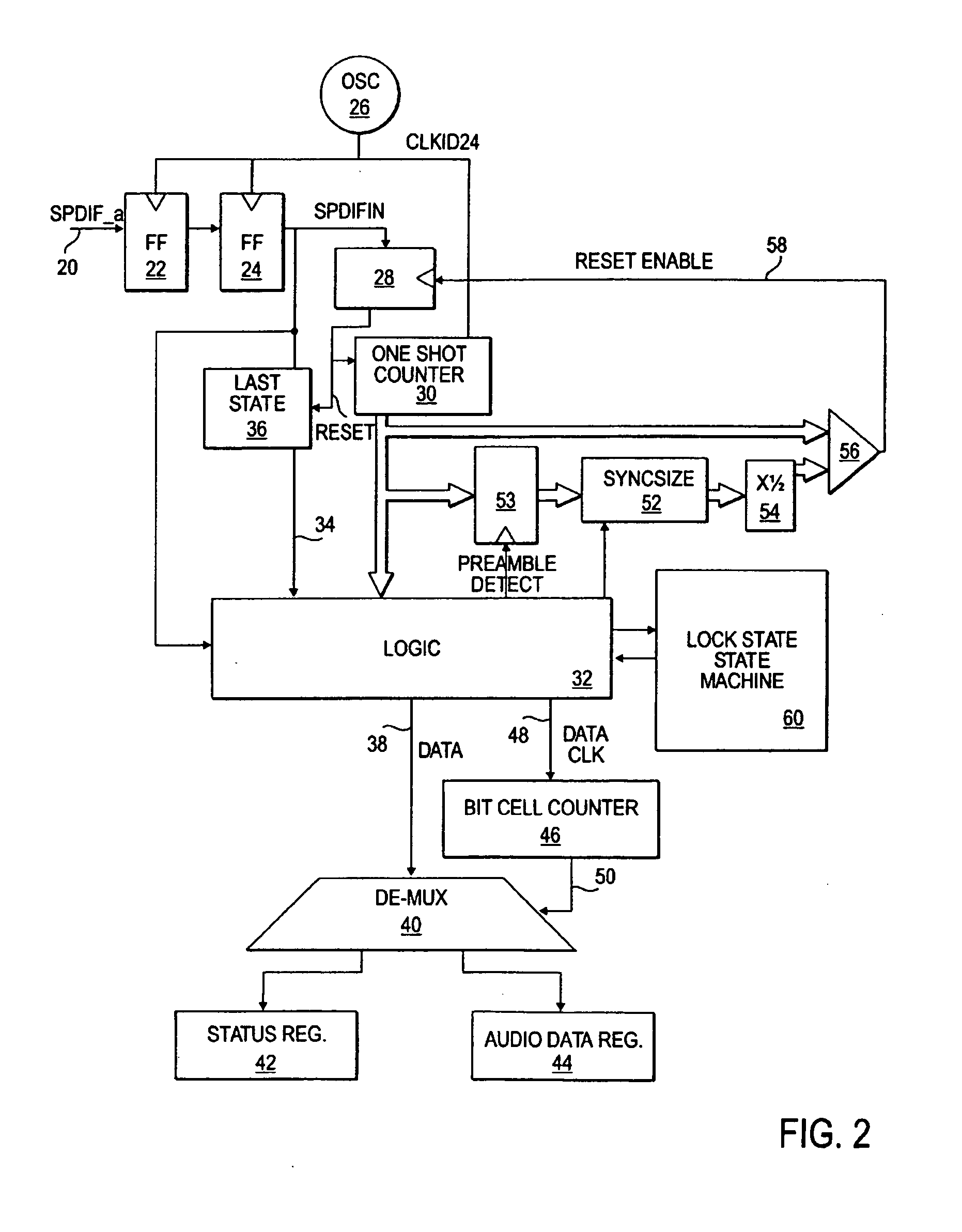
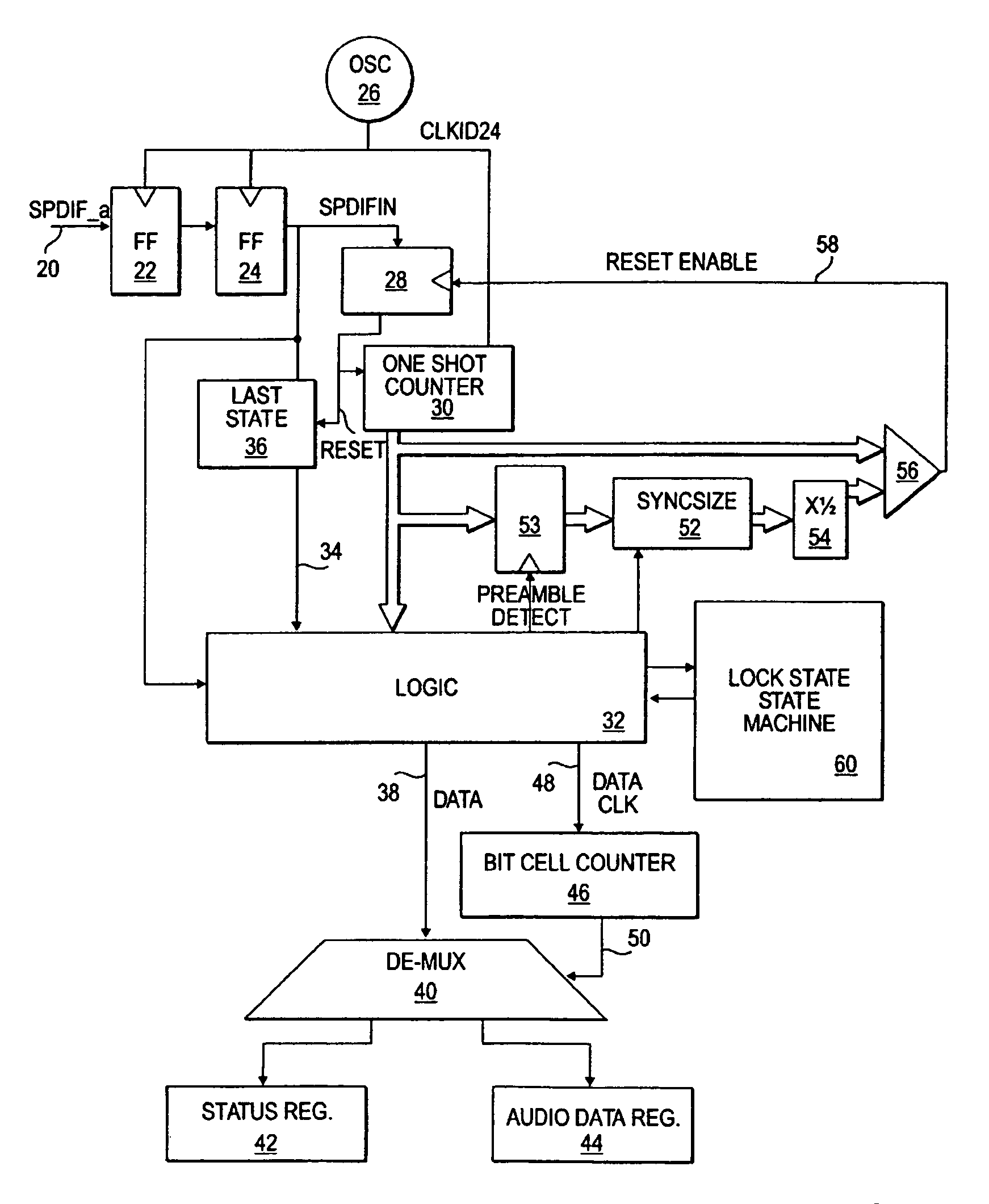
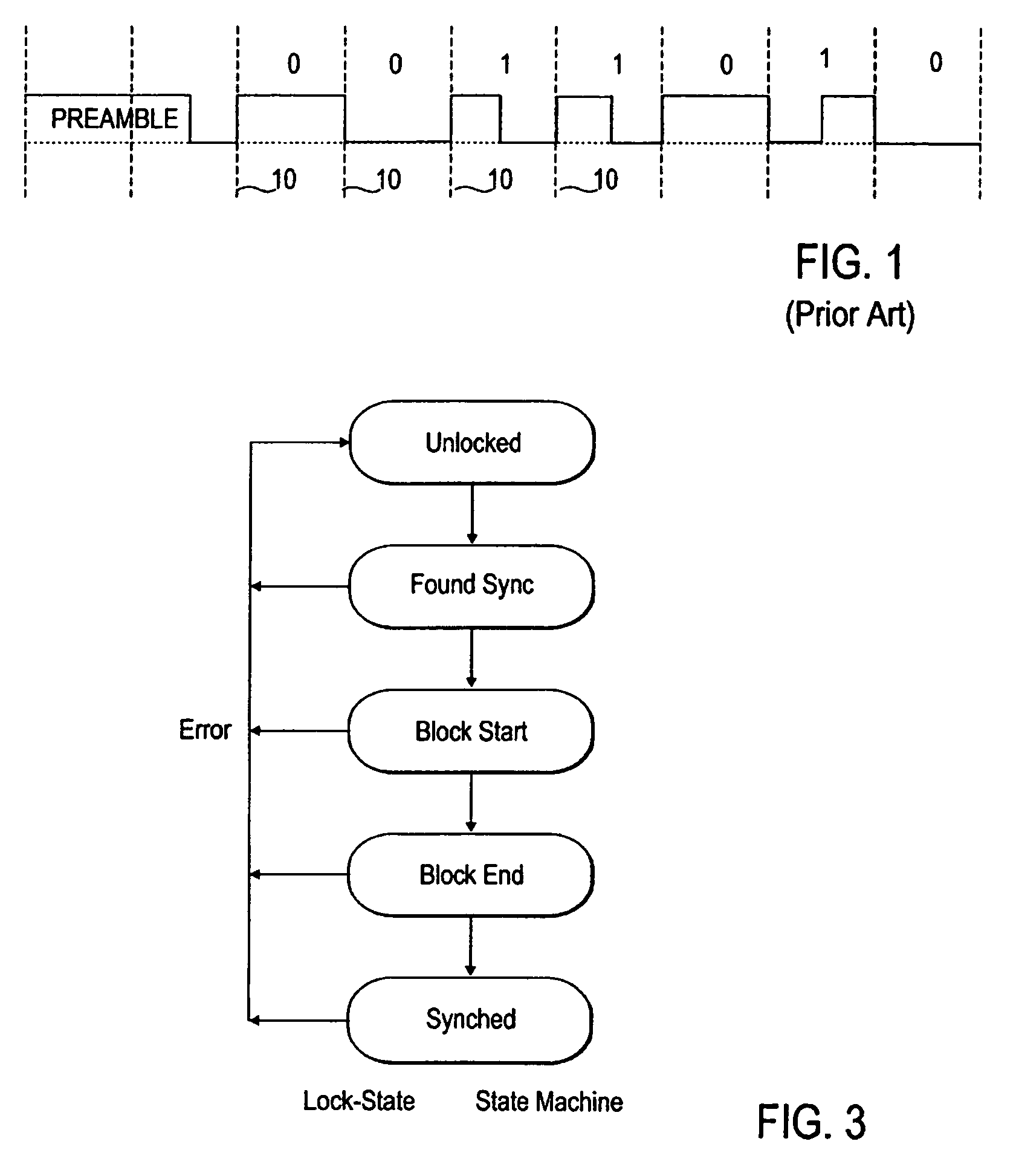
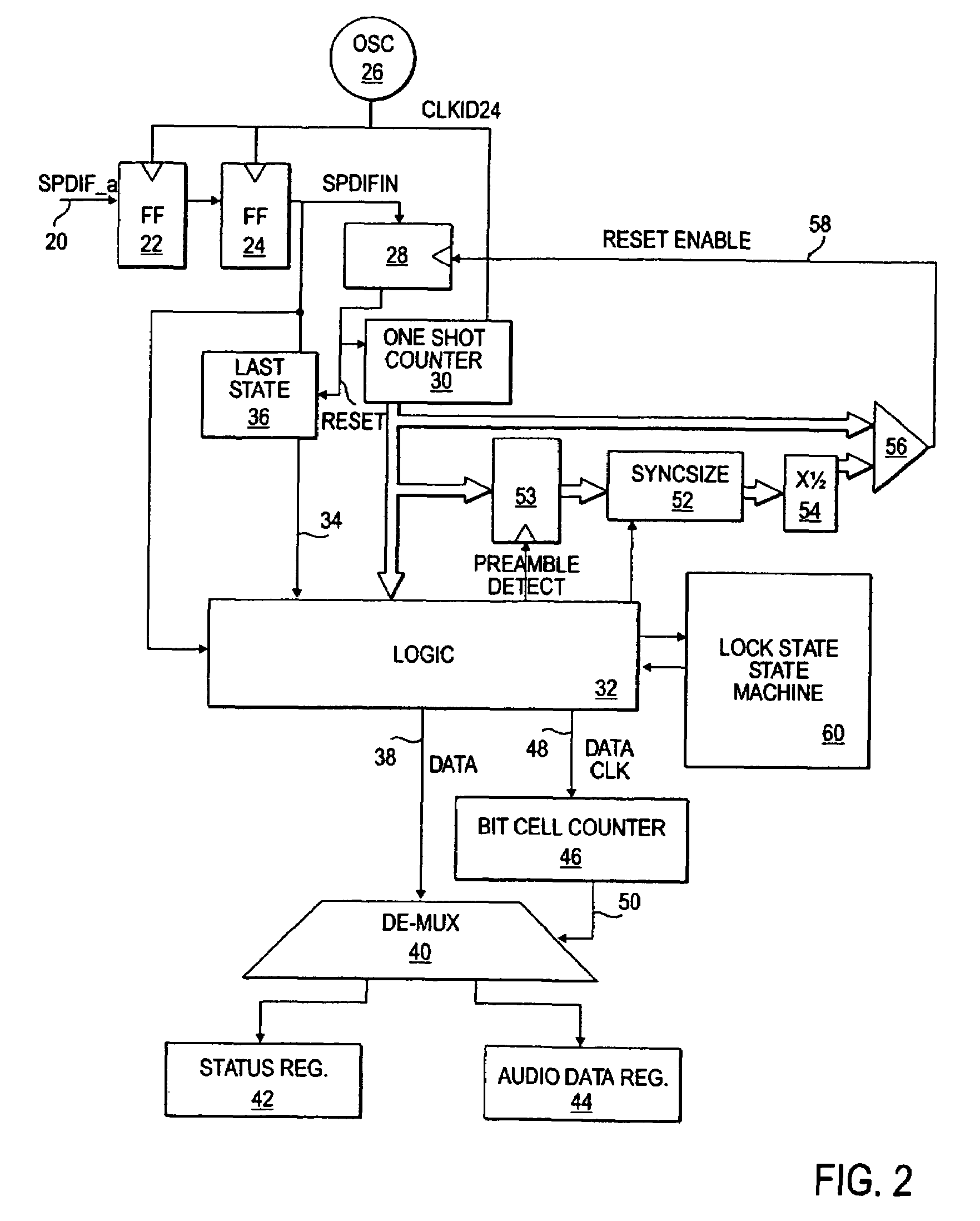
Digital audio data receiver without synchronized clock generator
InactiveUS20050060052A1Easily recovers dataSimple circuitDc level restoring means or bias distort correctionSpecial data processing applicationsClock rateClock generator
A method and apparatus for receiving digital audio data which does not require the recovery of a clock from the data. Instead, the digital audio data is sampled at a rate greater than a clock rate of the digital audio data. Appropriate transitions in the digital audio data are detected to allow reconstruction of digital values represented by the digital audio data.
Owner:CREATIVE TECH CORP
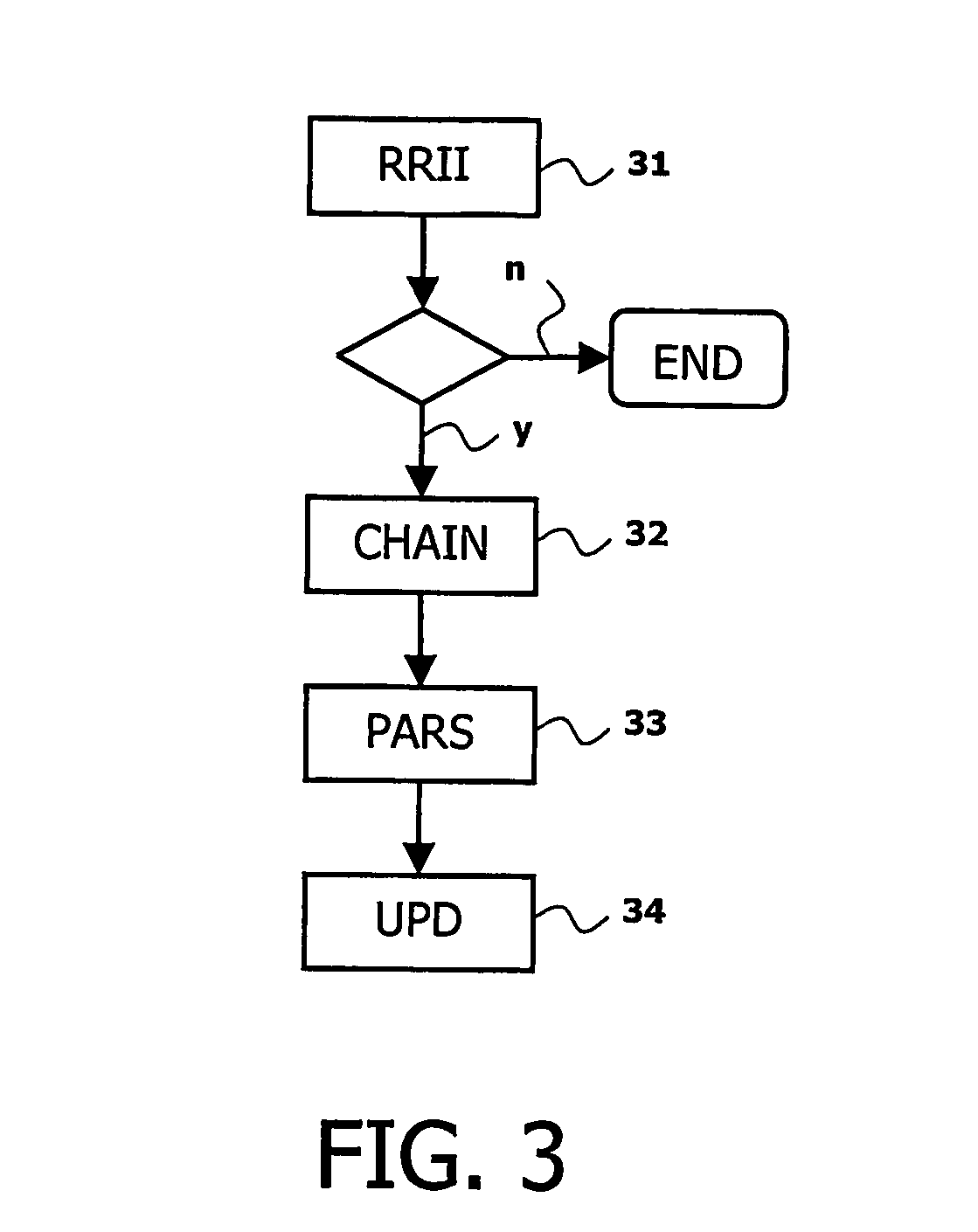
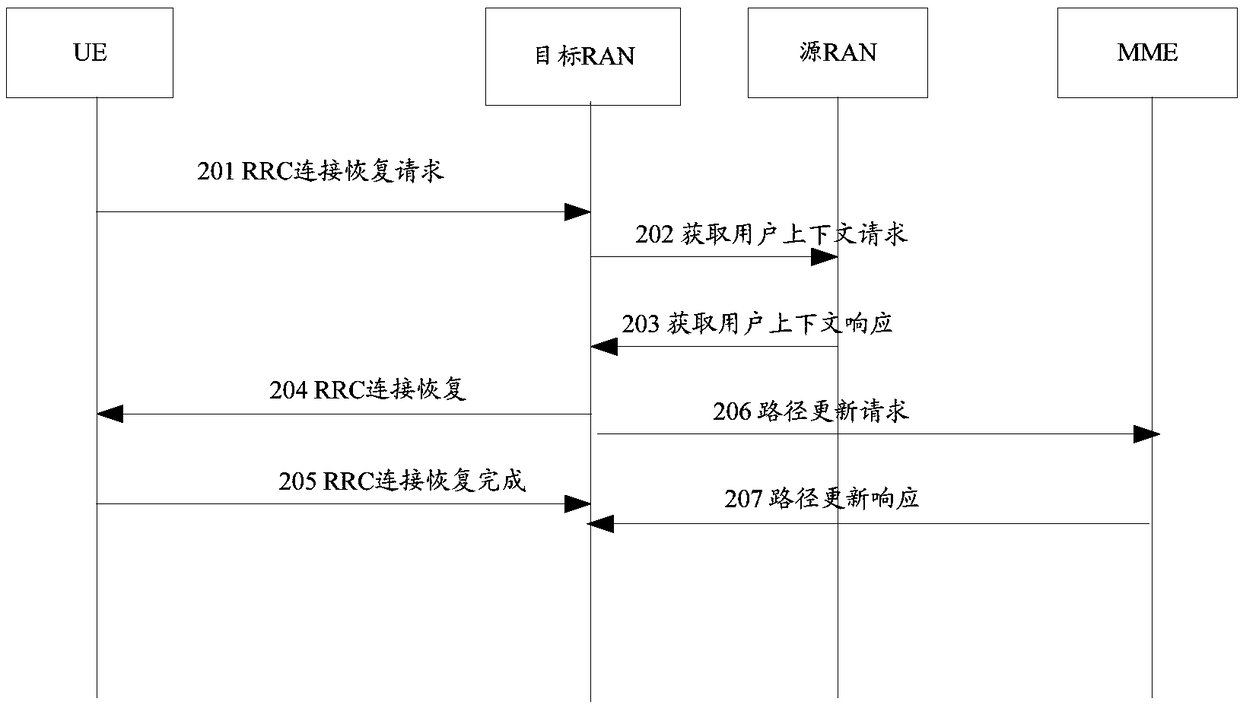
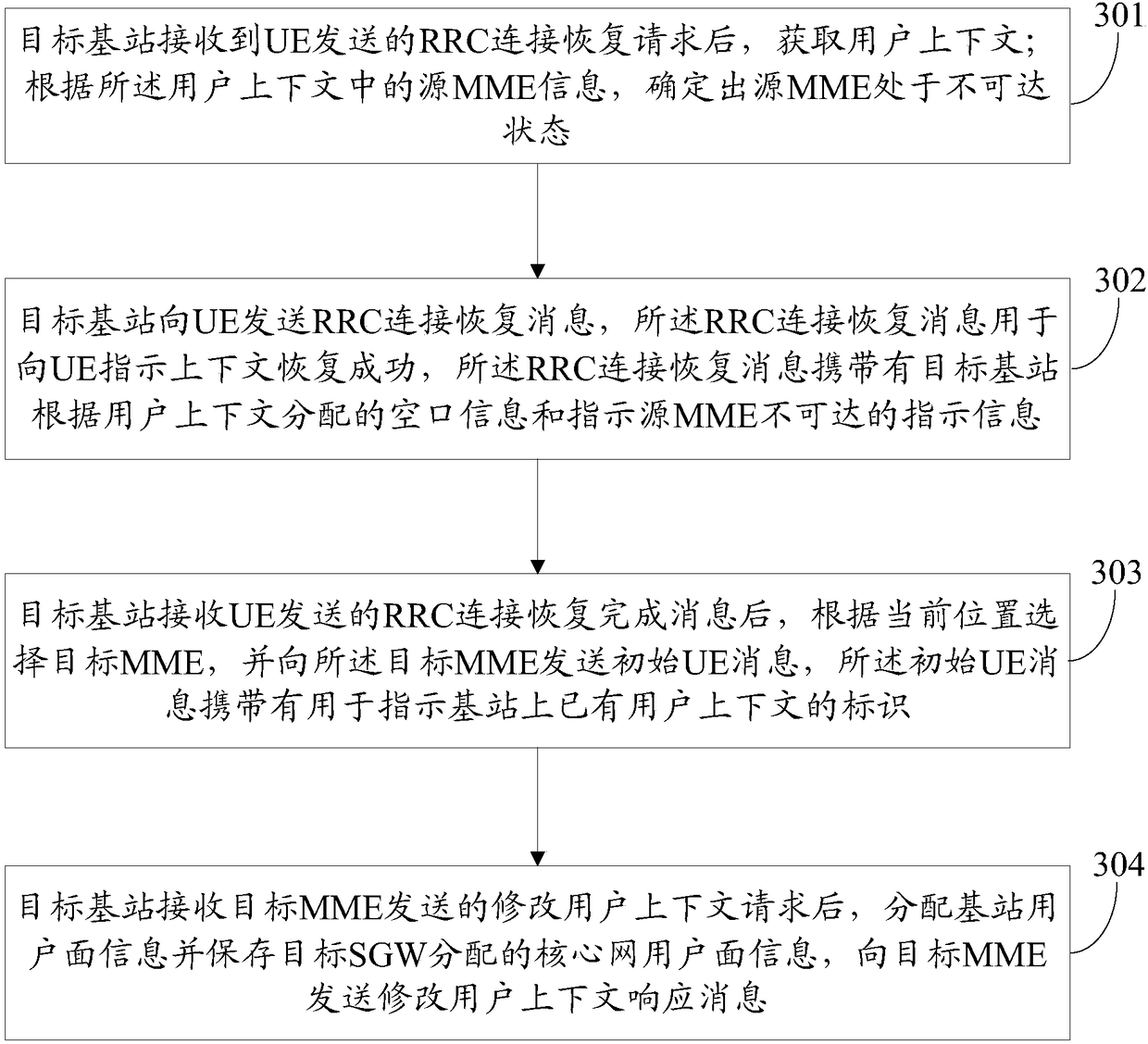
Base station user data recovery method and device
InactiveCN108307429AData recoveryNetwork traffic/resource managementConnection managementData recoveryCore network
The invention discloses a base station user data recovery method and device. The method comprises the following steps: when receiving an RRC connection recovery request sent by UE, a target base station acquires a user context and determines that a source MME is unreachable; the target base station sends an RRC connection recovery message to the UE; after receiving an RRC connection recovery completion message sent by the UE, the target base station selects a target core network control plane network element according to a current position, and sends an initial UE message to the target core network control plane network element, wherein the initial UE message carries an identifier used for indicating an existing user context of the base station; and after receiving a user context modification request sent by the target core network control plane network element, the target base station allocates base station user plane information, saves core network user plane information, and sends auser context modification response message to the target core network control plane network element.
Owner:ZTE CORP
Wide window decoder circuit for dual phase pulse modulation
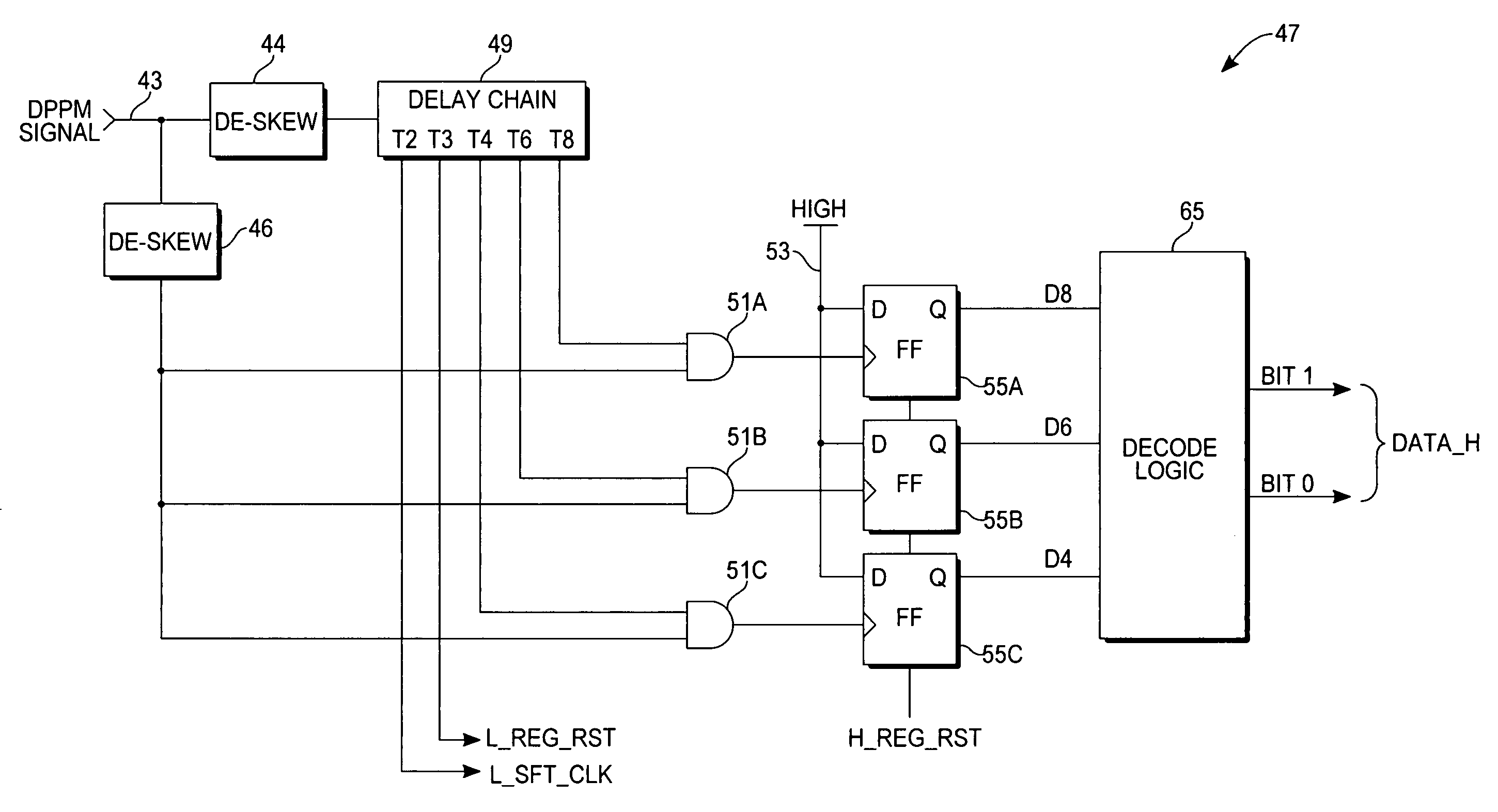
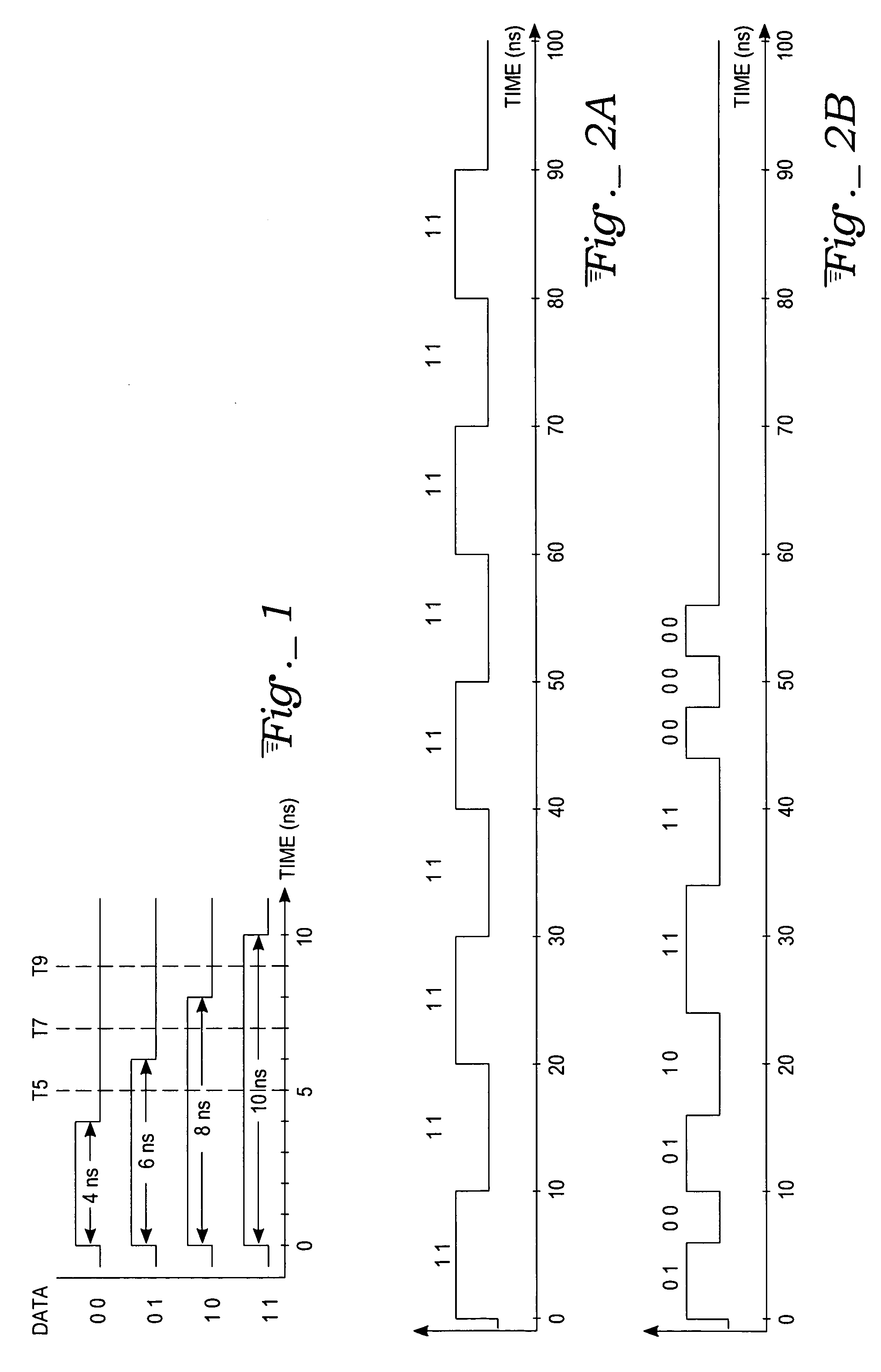
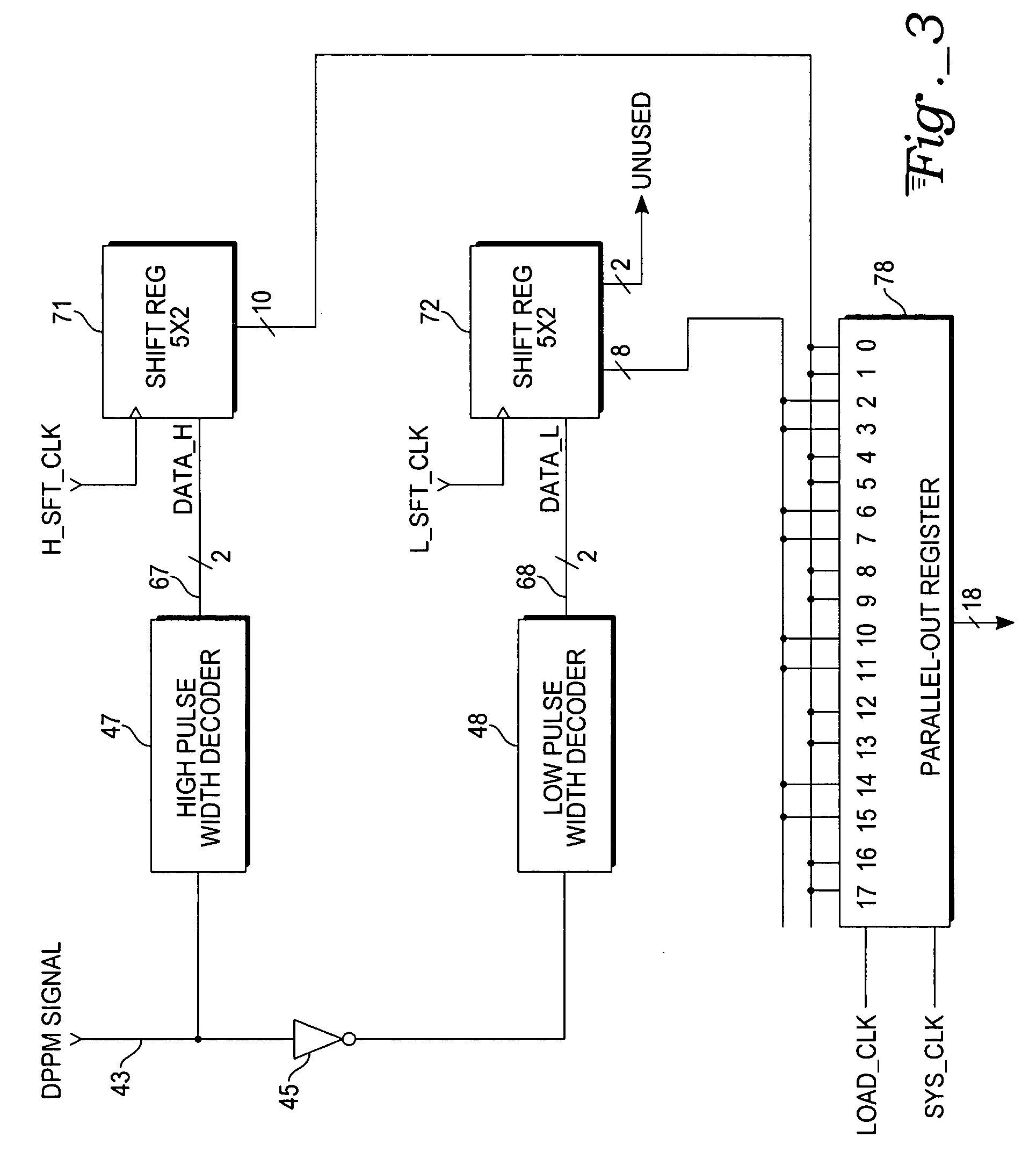
ActiveUS20060050777A1Data recoveryParallel/series conversionMultiplex communicationLogic gateData value
A dual phase pulse modulation (DPPM) decoder circuit processes a DPPM signal, which is in the form of a series of high and low pulses whose pulse widths represent successive groups of M data bits, so as to recover data carried by the signal. Each of the 2M possible data values of an M-bit group corresponds to one of 2M distinct pulse widths. Circuit blocks determine the width of each pulse by piping the DPPM signal through a short delay chain and inputting the delayed outputs and the non-delayed signal into AND logic gates, whose outputs are used to clock flip-flop registers. The registers are reset to a known state at the start of each signal pulse and toggled to an opposite state if clocked. The registered outputs are interpreted by logic to obtain the corresponding M-bit groups.
Owner:ATMEL CORP
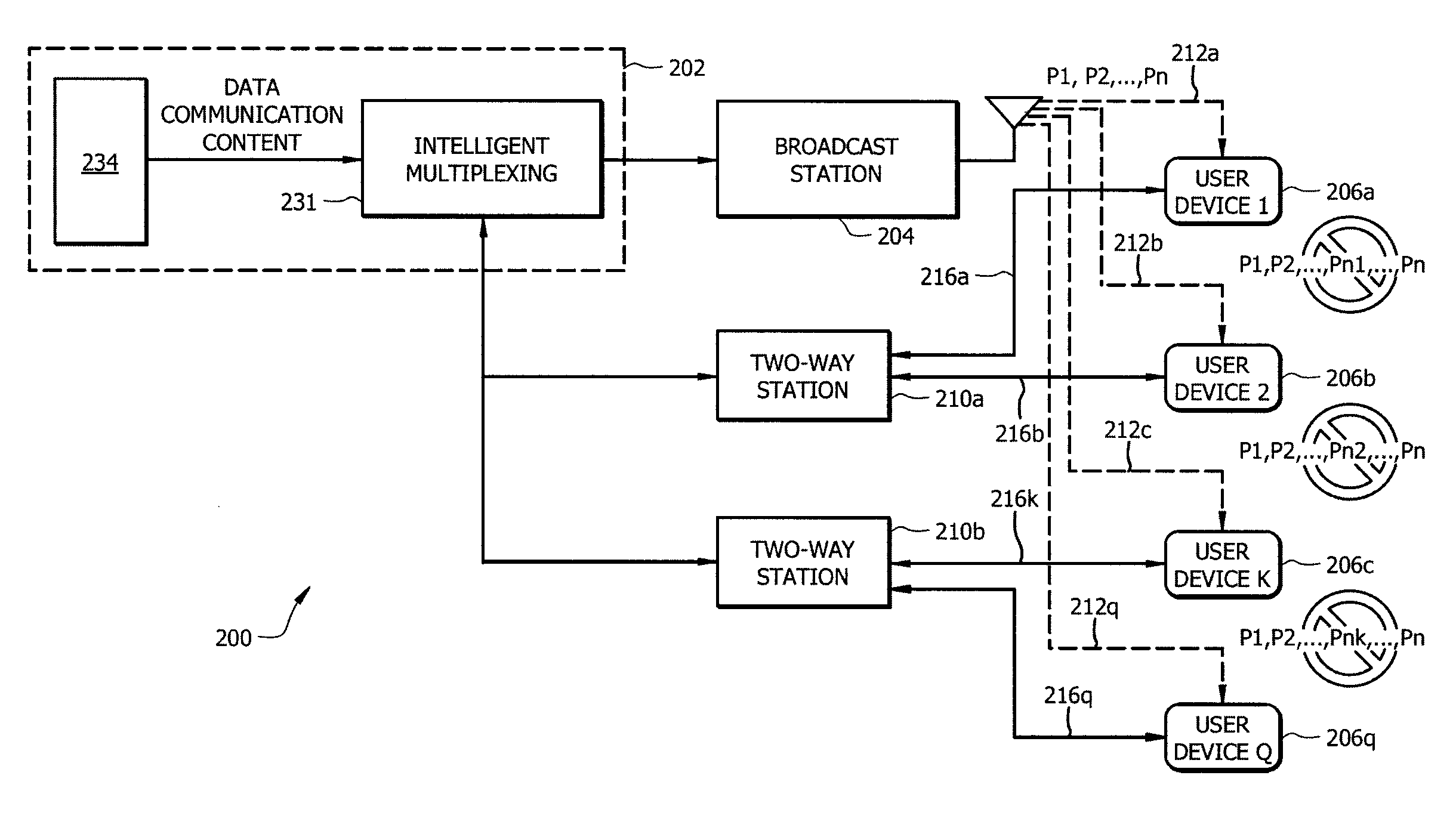
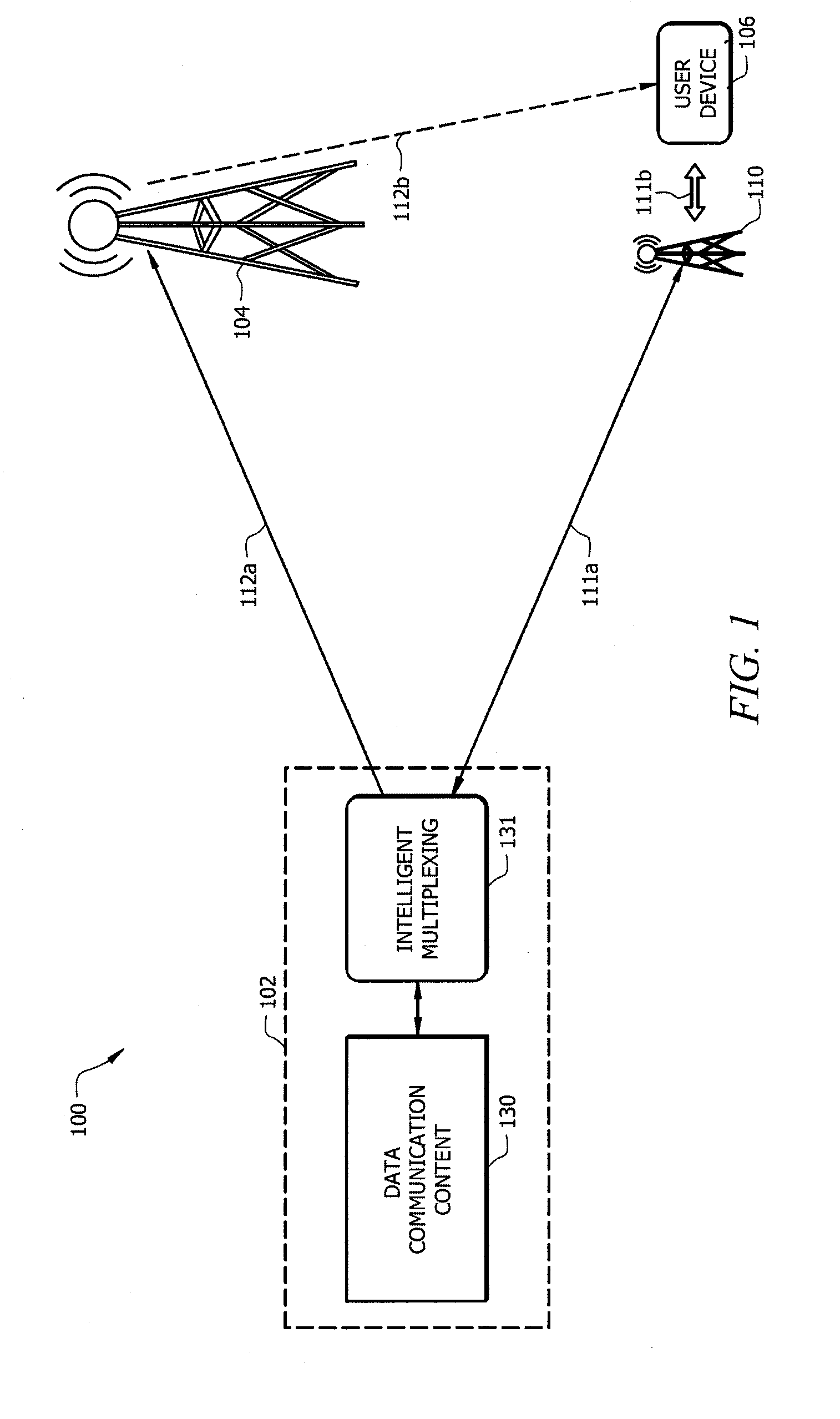
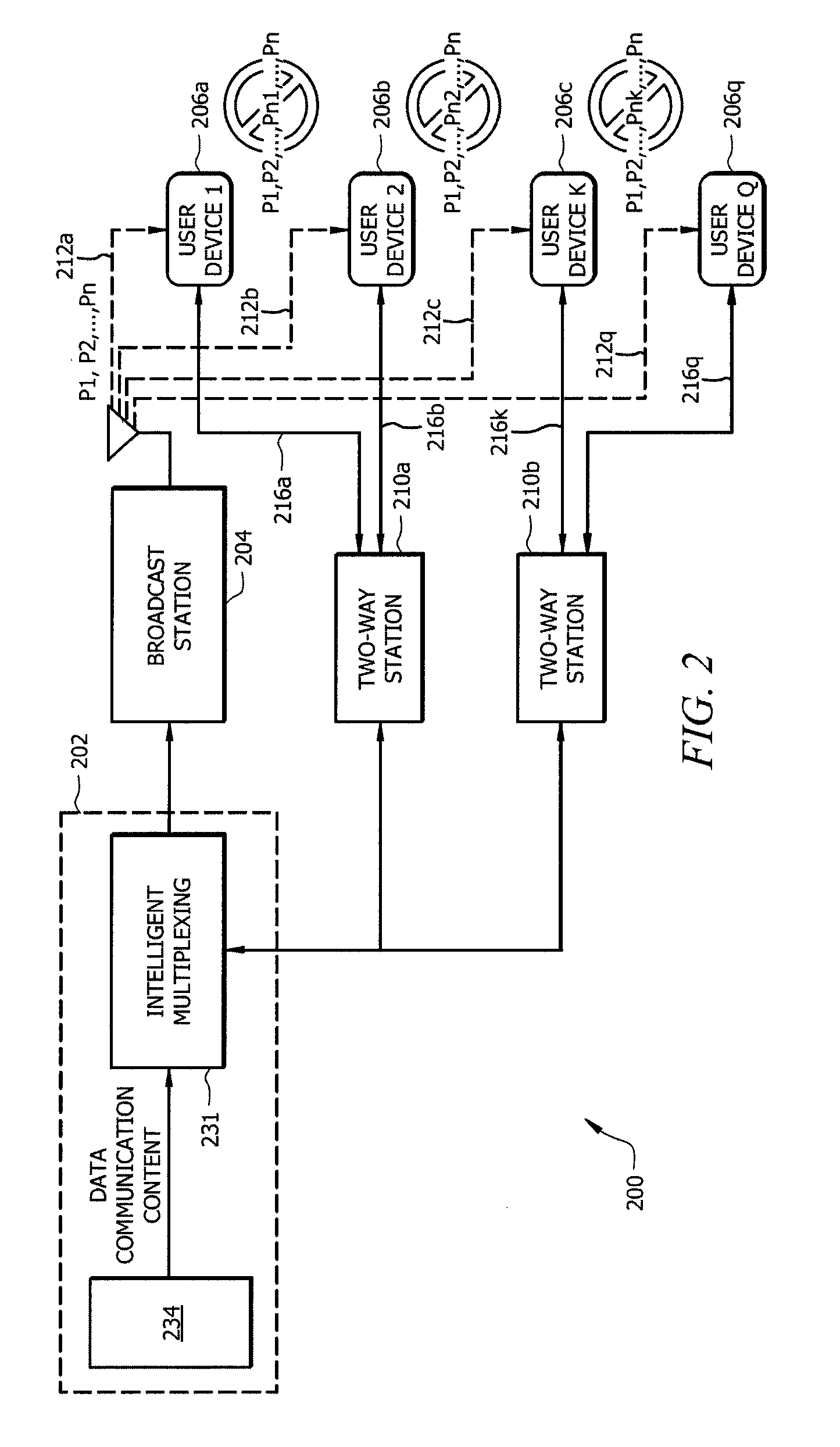
Distributed storage and sharing of data packets in hybrid networks
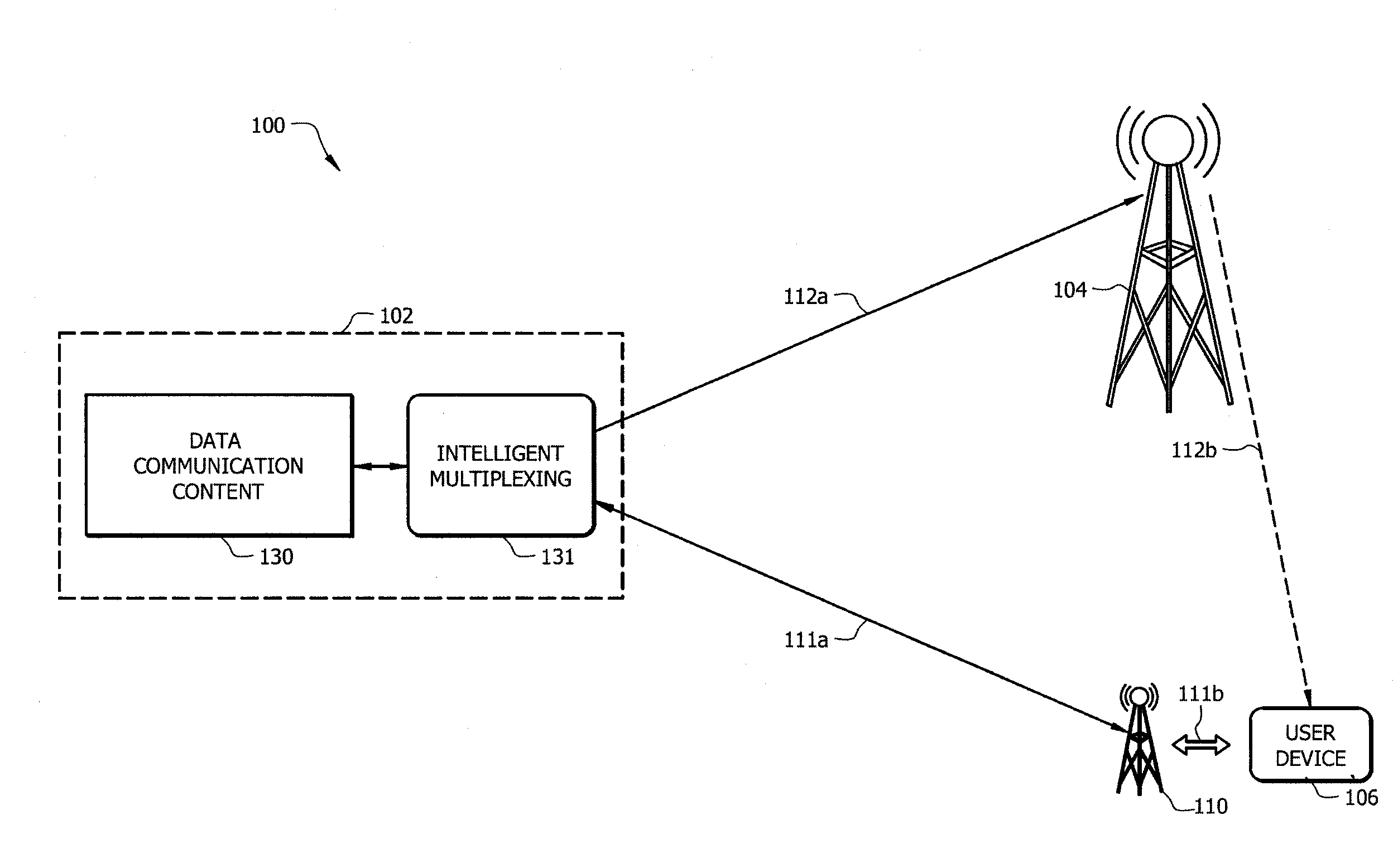
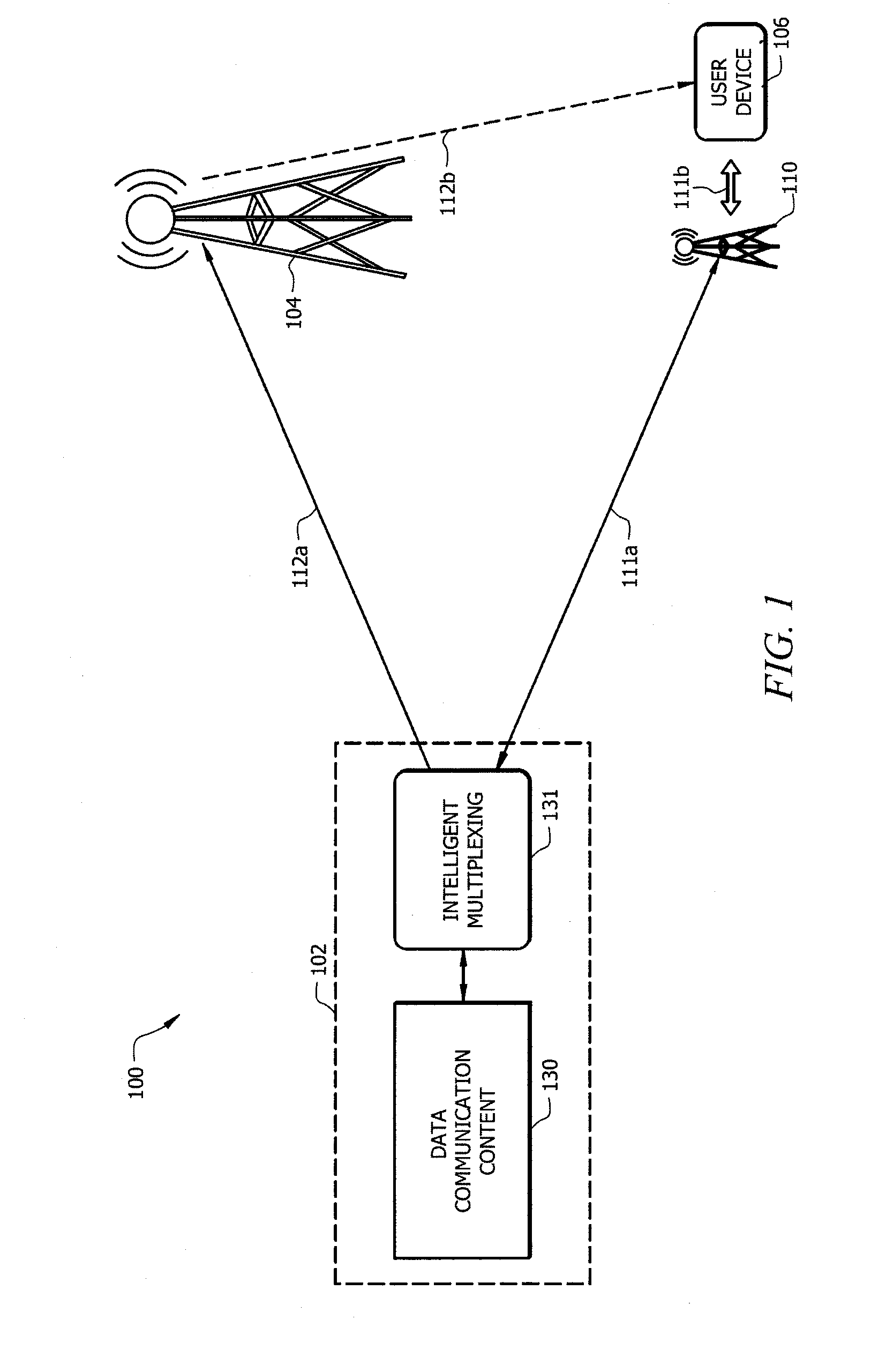
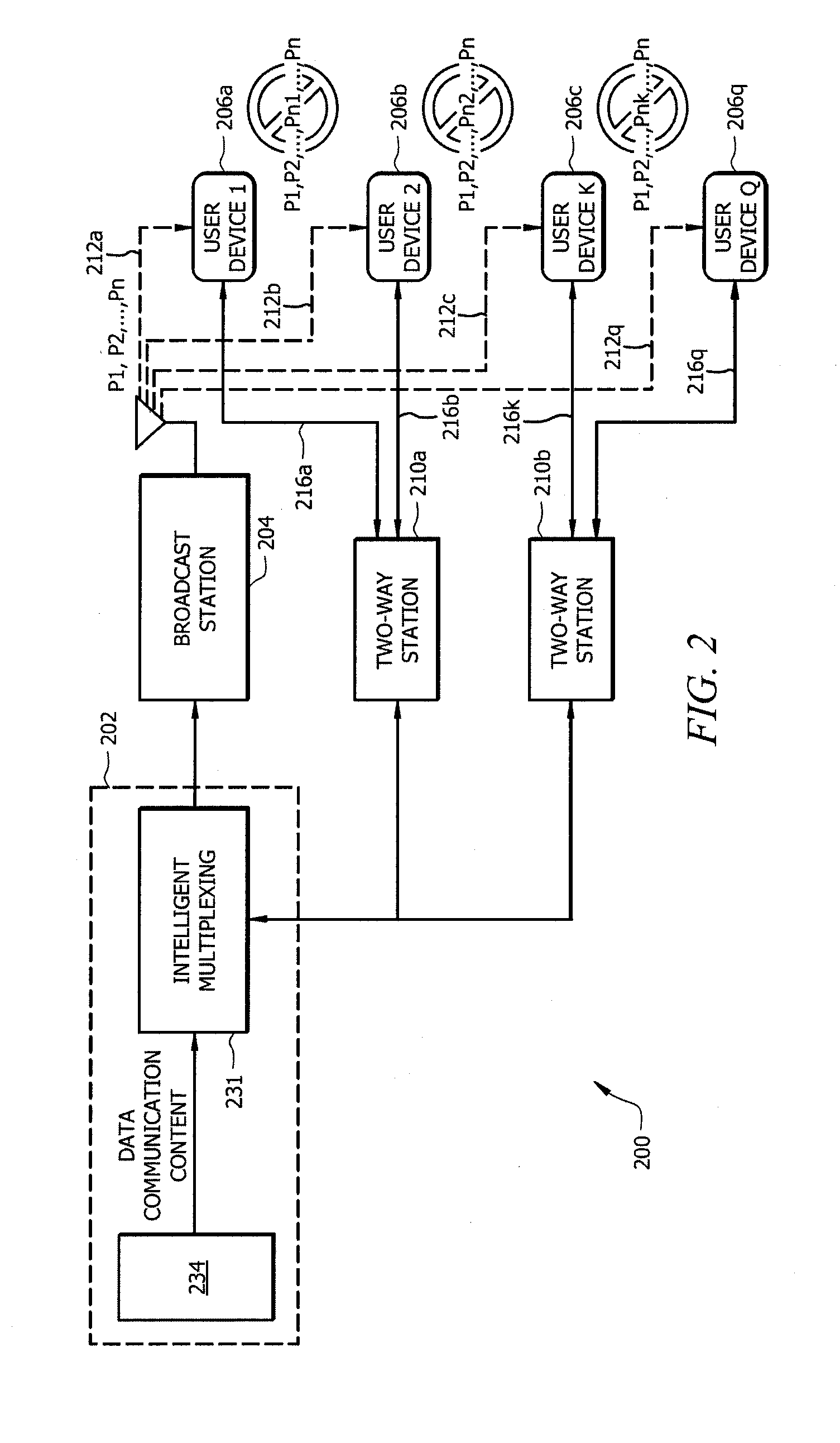
ActiveUS20130286813A1Optimize broadcast resourceResource optimizationError preventionFrequency-division multiplex detailsMix networkComputer terminal
Systems and methods provide distributed storage and sharing of data packets in hybrid networks to enable user devices (e.g., mobile terminals) to cooperate to recover lost data packets. According to embodiments, a centralized system operable to provide data transmission may optimize broadcast resources by adjusting redundancy in data packet transmission to enable a desired or a predetermined percentage of user devices to either successfully receive transmitted data packets using transmitted redundancies or to recover lost data packets relying on the distributed storage and sharing scheme.
Owner:CMMB VISION USA
Method and system for insuring data integrity in anticipation of a disaster
A preparation of a storage system of a pending disaster at an onsite location of the storage system involves the storage system receiving a disaster preparation initiation from an offsite client. In response to receiving the disaster preparation initiation from the offsite client, the storage system to executes disaster preparation of onsite data including managing a temporary storage of onsite data volumes to at least one peer site, managing a storage of onsite cached data to a first onsite removable media, and / or managing a storage of onsite management information to a second onsite removable media.
Owner:TWITTER INC
Digital audio data receiver without synchronized clock generator
InactiveUS7668609B2Easily recovers dataData recoveryDc level restoring means or bias distort correctionSpecial data processing applicationsClock rateDigital Audio Tape
Owner:CREATIVE TECH CORP
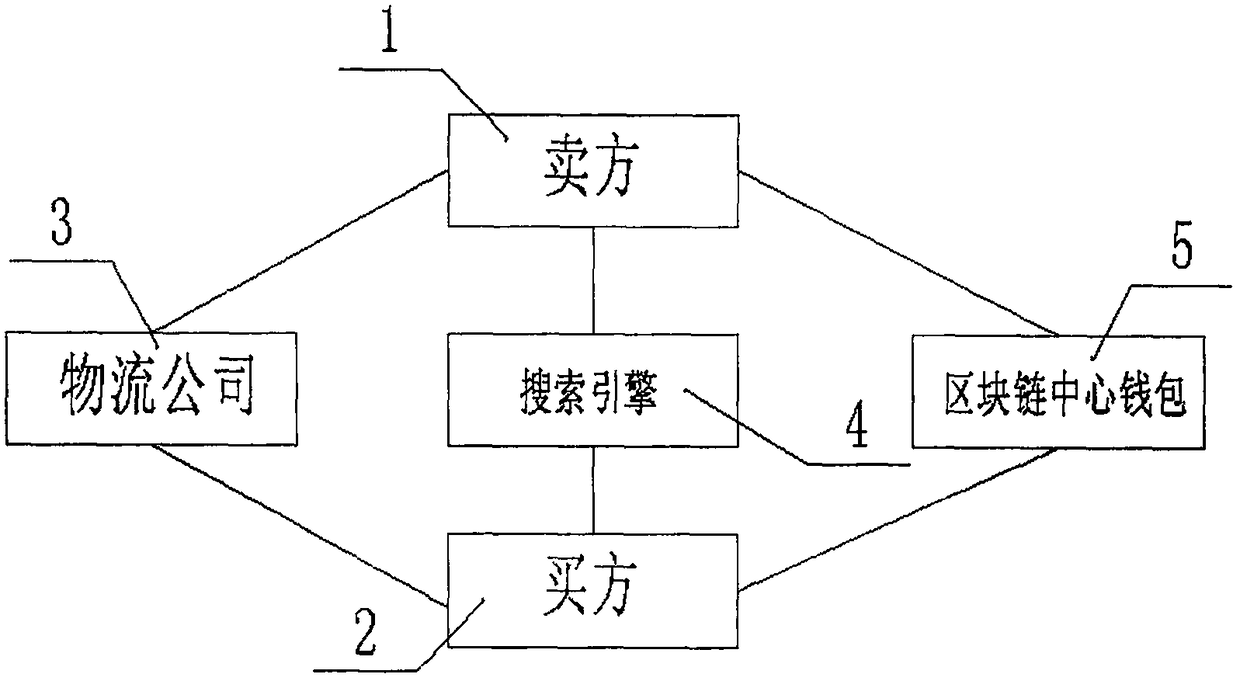
E-commerce method based on blockchain technology
InactiveCN108154419ASafety of tradementProperty securityPayment architectureBuying/selling/leasing transactionsDigital currencyLogistics management
The invention discloses an e-commerce method based on a blockchain technology. According to the method, sellers, buyers and logistics companies are involved, each seller can build a website, the decentralization of websites is formed, the other websites cannot be chained when one website is attacked, all the seller websites and transaction products are searched for through special e-commerce search engines, and the buyers purchase goods and then pay digital currency to blockchain center wallets; the blockchain center wallets serve as intermediate guarantors with the similar functions of Alipay, and the digital currency is released to seller wallets after it is confirmed that the goods are received; the logistics companies achieve the function of logistics express transportation and do notget involved in the transaction and payment of the sellers and the buyers. According to the e-commerce method, through different search engines, different block center wallets and different logisticstransportation companies, the isolation of transactions is achieved, data is not centralized any longer, and therefore the internet transactions are safer. Moreover, by means of a centralized accounting mode of the blockchain technology, the data can be recovered, and therefore the property is safer.
Owner:路亚鹏
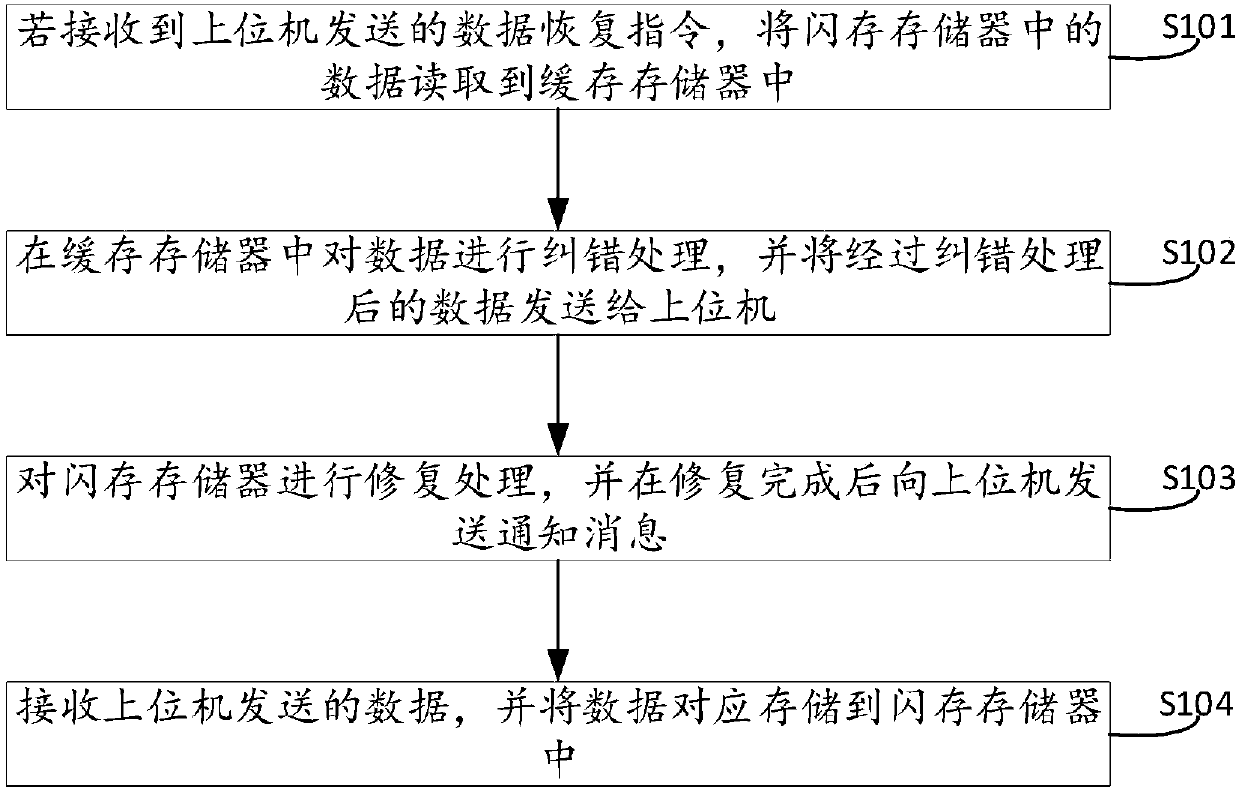
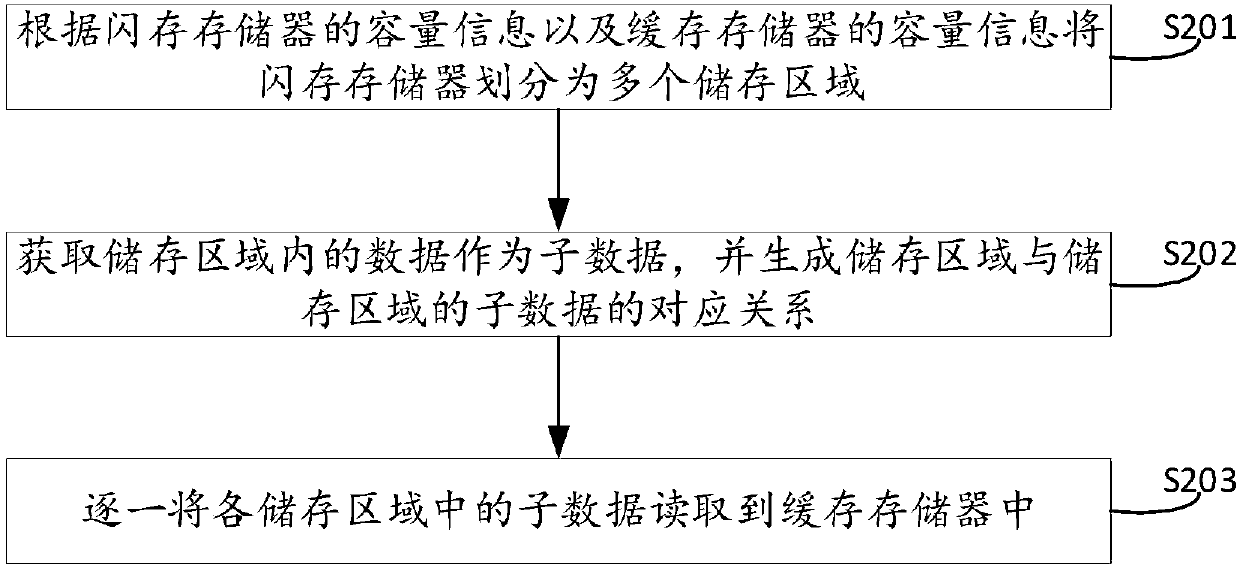
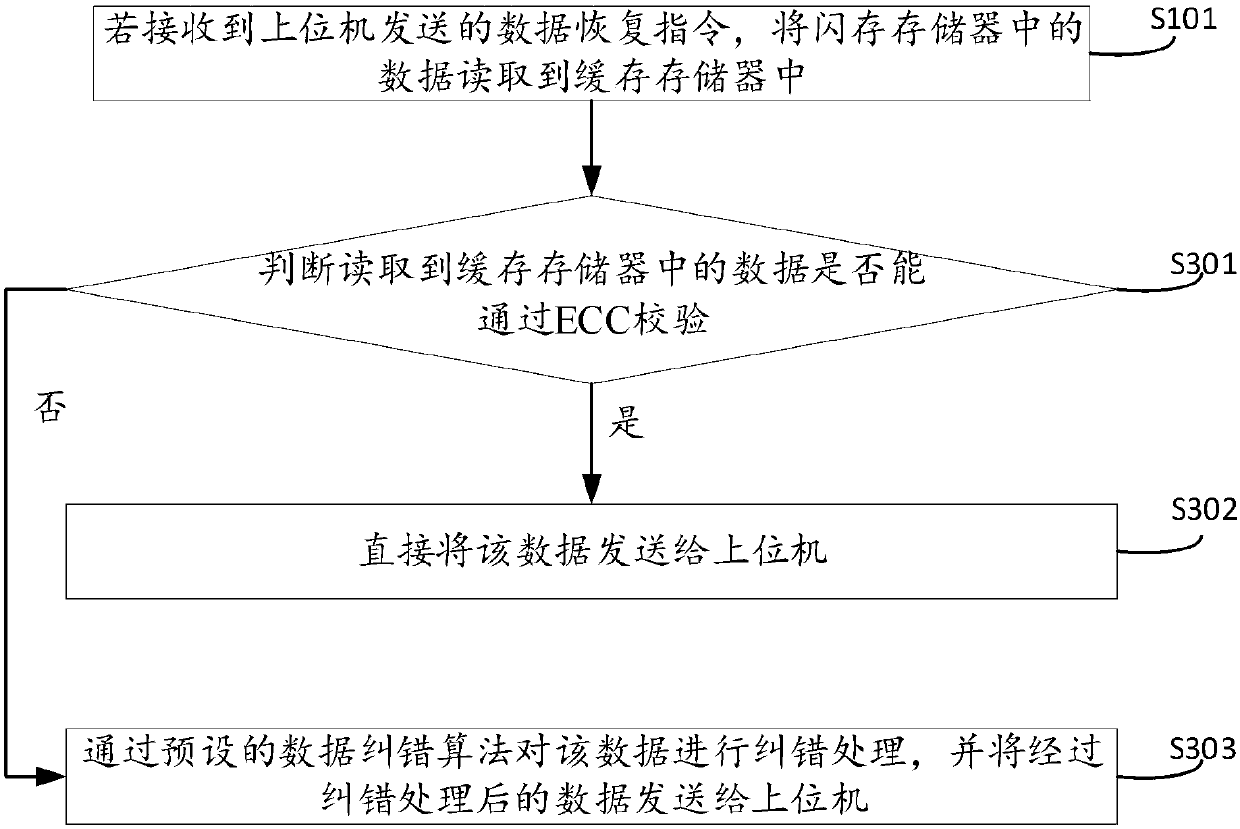
Data recovery method, data recovery system and solid state disk
PendingCN110083478AData RecoveryAchieve fixRedundant data error correctionRedundant operation error correctionRecovery methodSolid-state drive
The embodiment of the invention discloses a data recovery method, a data recovery system and a solid state disk. The method is applied to the solid state disk in the data recovery system. The data recovery system further comprises an upper computer. The solid state disk comprises a control unit, a flash memory and a cache memory, and the method comprises the steps of if a data recovery instructionsent by an upper computer is received, reading data in the flash memory into the cache memory; performing error correction processing on data in the cache memory, and sending the data subjected to the error correction processing to the upper computer; repairing the flash memory, and a notification message is sent to the upper computer after repairing is completed; and receiving the data sent by the upper computer, and correspondingly storing the data into a flash memory. By applying the technical scheme provided by the embodiment of the invention, the data in the flash memory is recovered sothat the reliability of the data in the flash memory is ensured. The repair of the flash memory is realized.
Owner:力瑞信(深圳)科技有限公司
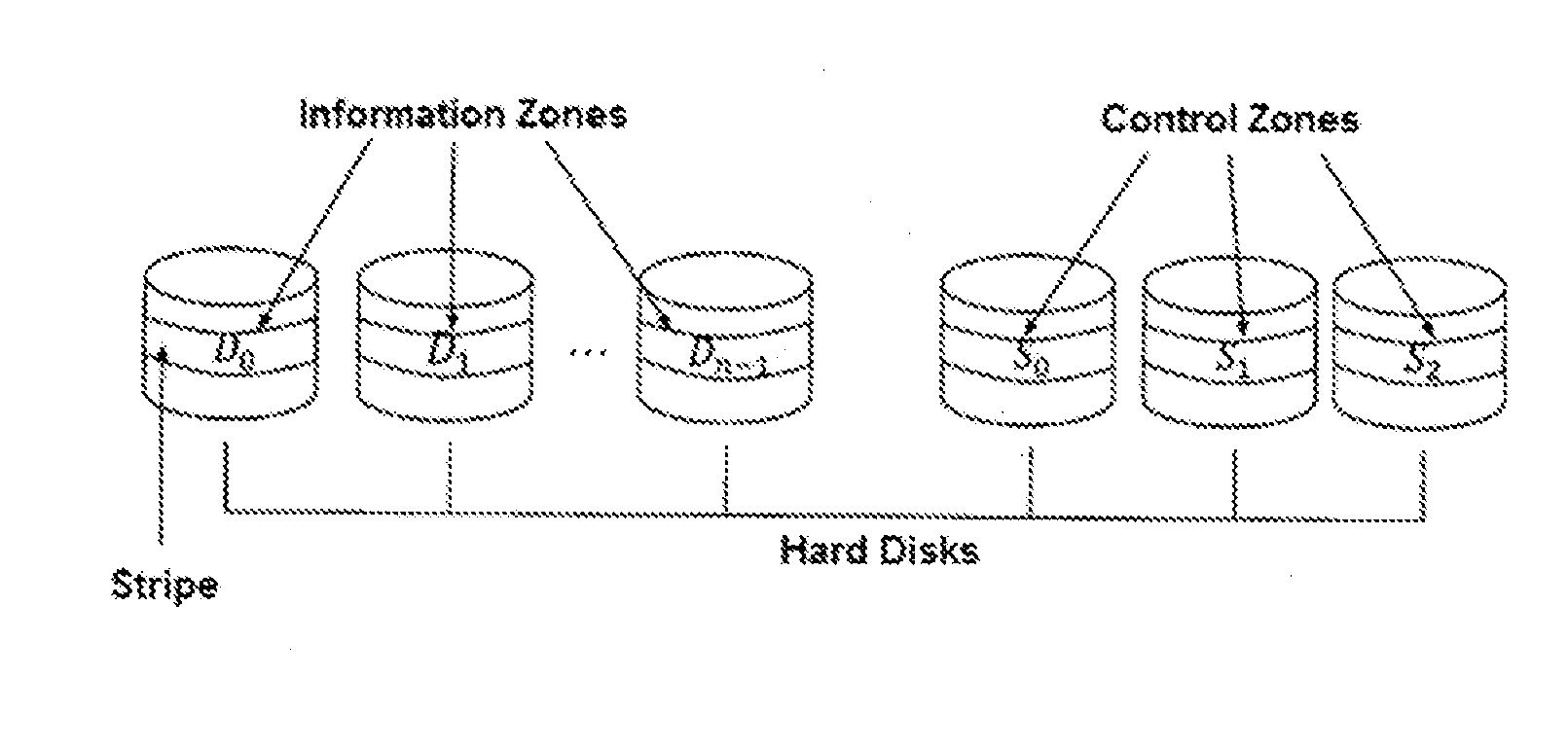
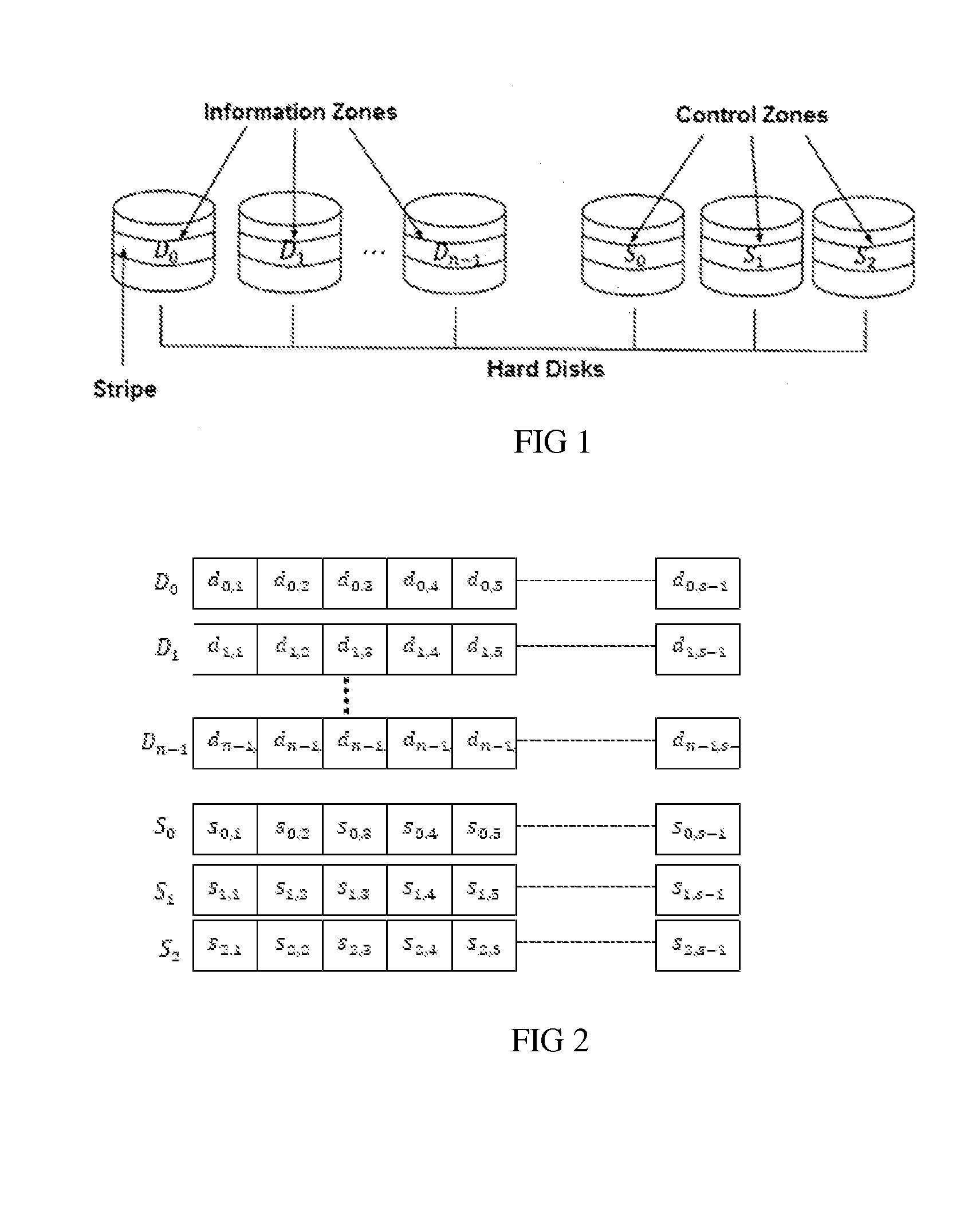
Method for Recovering Recordings in a Storage Device and System for Implementing Same
InactiveUS20150178162A1Reduce the amount of memoryImprove performanceNon-binary linear block codesRead-only memoriesControl zoneEmbedded system
The memory of the storage device is divided into information areas of identical size selected from different parts of the storage device, and control zones are selected from different parts of the device. Each group of data is a set of code words written to a corresponding information zone. Three reference control sums S0, S1, S2, each according to a corresponding preset formula, are established by a computation unit. The reference control sums are written as a code word with the same number to a corresponding control zone. If a part of the storage device fails and data becomes corrupted, the current control sums are calculated with the aid of the computation unit. The values of the stored reference control sums and the current control sums are used for recovering lost data. The number of equations depends on the number of failed or faulty zones in the storage device.
Owner:RAIDIX
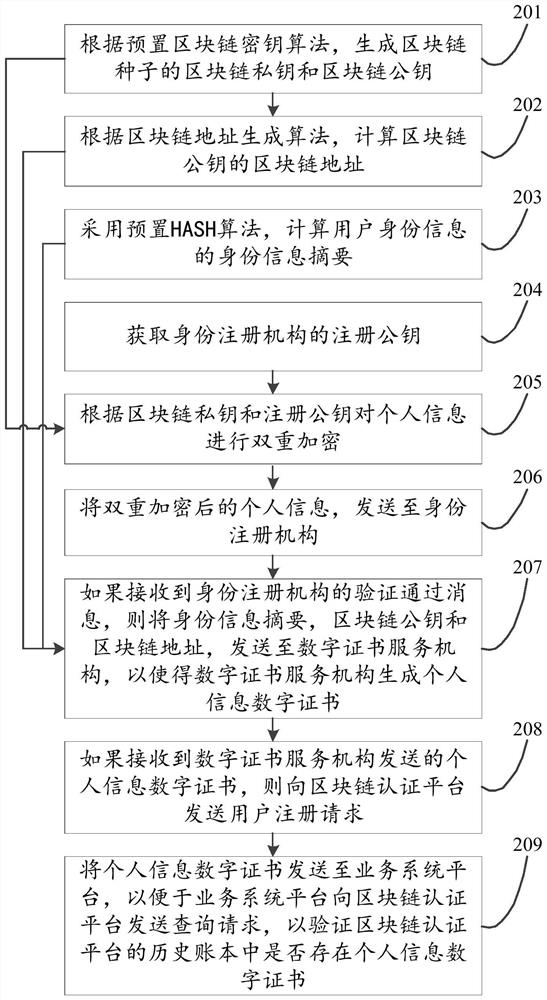
An identity authentication method and device based on user identification module and blockchain technology
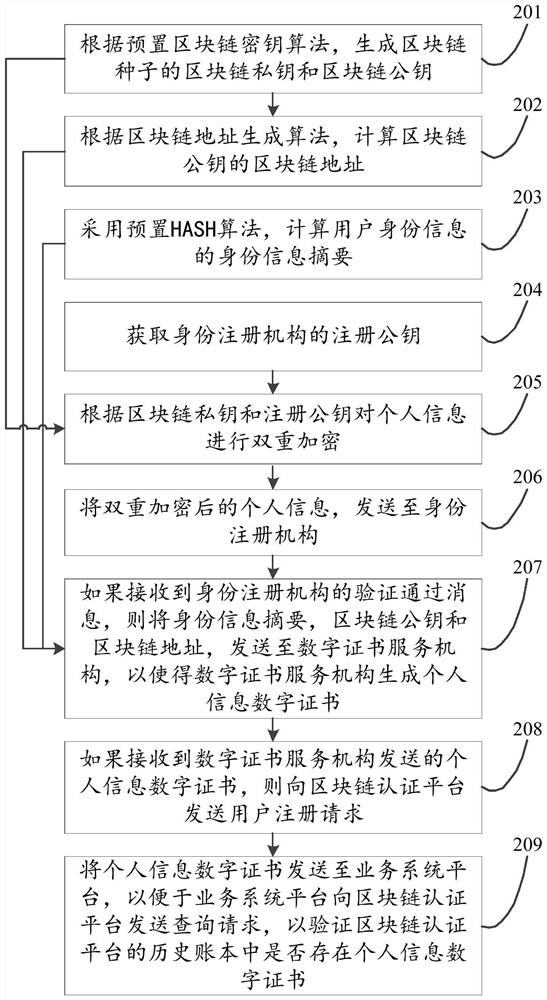
ActiveCN111859348BData RecoveryDigital data protectionDigital data authenticationRegistration authorityInternet privacy
The invention discloses an identity authentication method and device based on a user identification module and block chain technology, relates to the field of block chain technology, and is invented to solve the security problems of block chain key storage and use in the prior art. The main methods include: generating the blockchain private key and the blockchain public key of the blockchain seed according to the preset blockchain key algorithm; calculating the blockchain address of the blockchain public key according to the address generation algorithm; using The HASH algorithm is preset to calculate the identity information digest of the user's identity information; the personal information is sent to the identity registration agency, so that the identity registration agency can verify whether the personal information can pass the real-name authentication; The public key and blockchain address are sent to the digital certificate service agency; if the personal information digital certificate sent by the digital certificate service agency is received, a user registration request is sent to the blockchain authentication platform. The present invention is mainly applied to the process of blockchain user identity authentication.
Owner:上海微位可信互联安全科技有限公司
Intelligent set top box
InactiveCN107948745AOut of timeSupport installationSelective content distributionInteraction controlComputer module
The invention belongs to the technical field of set top boxes and particularly relates to an intelligent set top box, which comprises a network access unit, an intelligent interaction control unit anda power supply unit, wherein the intelligent interaction control unit comprises a control module for processing information, a storage module for storing data and a correcting module for ensuring theprogram of the set top box goes normal; the intelligent interaction control unit further comprises an abnormity recovery module; the network access unit is connected with the control module; the control module is connected with the storage module, the abnormity recovery module and the correcting module; and the power supply unit is connected with the control module. The set top box has an automatic recovery function so as to avoid the situation that the set top box goes abnormal; and the functions of the set top box are expanded, so that the set top box is more intelligent.
Owner:常州浩瀚万康纳米材料有限公司
High-assurance processor active memory content protection
ActiveUS8656185B2Avoid compromiseMinimizing data remanenceVolume/mass flow measurementUnauthorized memory use protectionActive memoryTerm memory
Owner:THALES DIS CPL USA INC
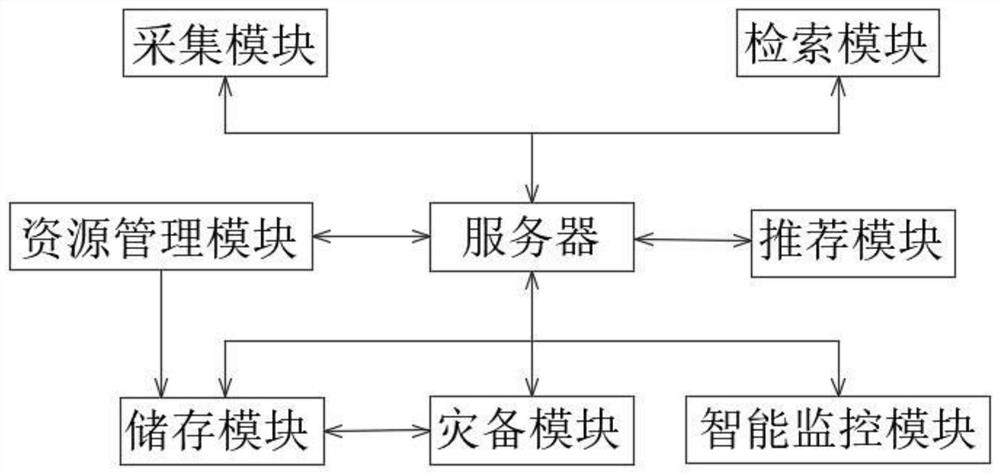
Cloud calculation management system
InactiveCN113282549AEasy to planEasy accessFile metadata searchingFile/folder operationsResource managementCustomer information
The invention discloses a cloud calculation management system, belongs to the technical field of cloud calculation management, and aims to solve the problem that an existing cloud calculation management system still has a large improvement space in the aspects of information recommendation and file management. The system comprises an collection module, a resource management module, an intelligent monitoring module, a disaster recovery module, a recommendation module, a server, a storage module and a retrieval module, the customer information comprises the company working field, the company scale, the company value and the company management level average age, the customer company is helped to better plan the next plan by knowing the company stage targets of similar companies, and in the development process of the similar companies, which needs to be noticed and learned by the company in the future development is found, and the customer company is helped to plan the next plan. Management modes of similar companies are known, and whether the management modes of the companies need to be improved or not is observed.
Owner:惠州迅云数字信息技术有限公司
Distributed storage and sharing of data packets in hybrid networks
ActiveUS9215568B2Resource optimizationReduce redundancyError preventionTransmission systemsMix networkUser device
Systems and methods provide distributed storage and sharing of data packets in hybrid networks to enable user devices (e.g., mobile terminals) to cooperate to recover lost data packets. According to embodiments, a centralized system operable to provide data transmission may optimize broadcast resources by adjusting redundancy in data packet transmission to enable a desired or a predetermined percentage of user devices to either successfully receive transmitted data packets using transmitted redundancies or to recover lost data packets relying on the distributed storage and sharing scheme.
Owner:CMMB VISION USA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com