Encryption transmission method and a quantum encryption method
A technology of quantum encryption and encrypted transmission, which is applied in transmission systems, photon quantum communication, and key distribution, and can solve problems such as increased power consumption and increased risk of encrypted data cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
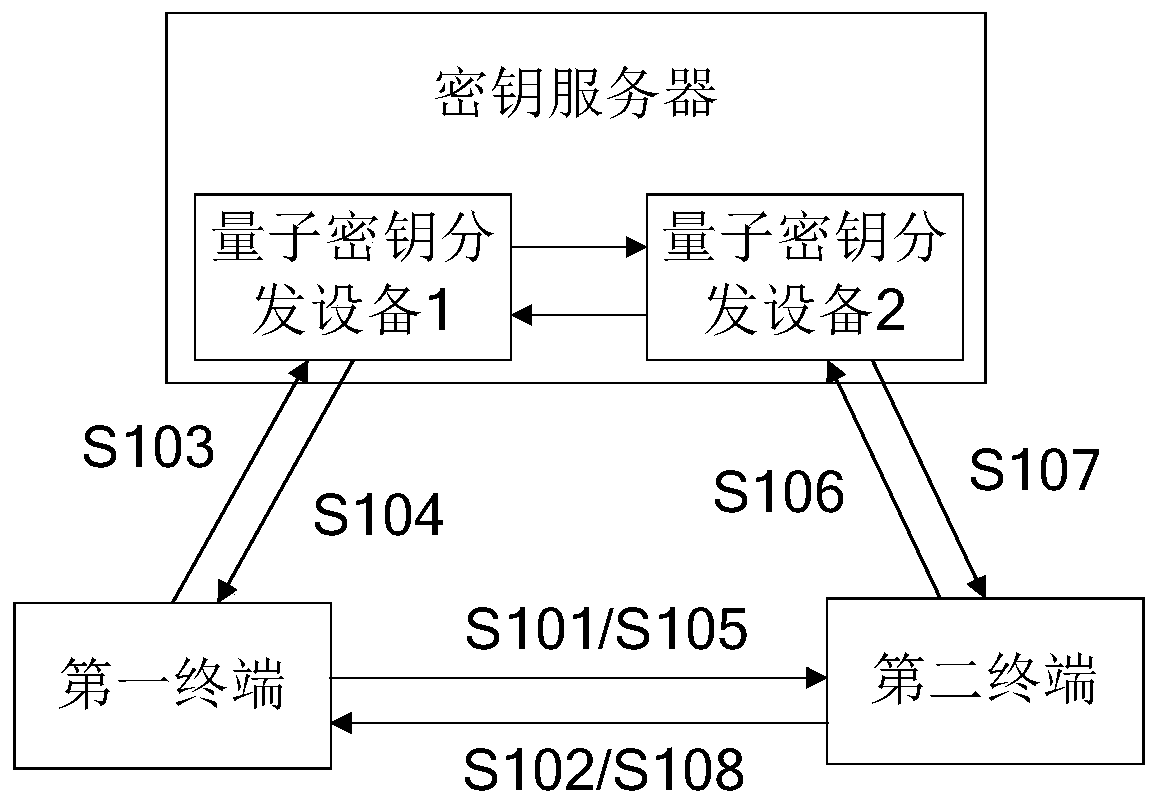
[0052] Such as figure 1 As shown, it is a schematic diagram of an encrypted transmission method provided by an embodiment of the present invention; see figure 1 , figure 1 Include the following steps:
[0053] S101. The first terminal sends an encryption start request to the second terminal.
[0054] It should be noted that, in this embodiment, the first terminal and the second terminal may be converted to each other under one condition.
[0055] S102. The second terminal receives the encryption start request, and returns encryption response information to the first terminal.
[0056] After receiving the encryption start request, the second terminal determines whether to agree to encrypted transmission with the first terminal, and then sends the encrypted response information to the first terminal. It can be understood that the returned encrypted corresponding information includes not only the second terminal's The confirmation information may also include some communicati...
no. 2 example
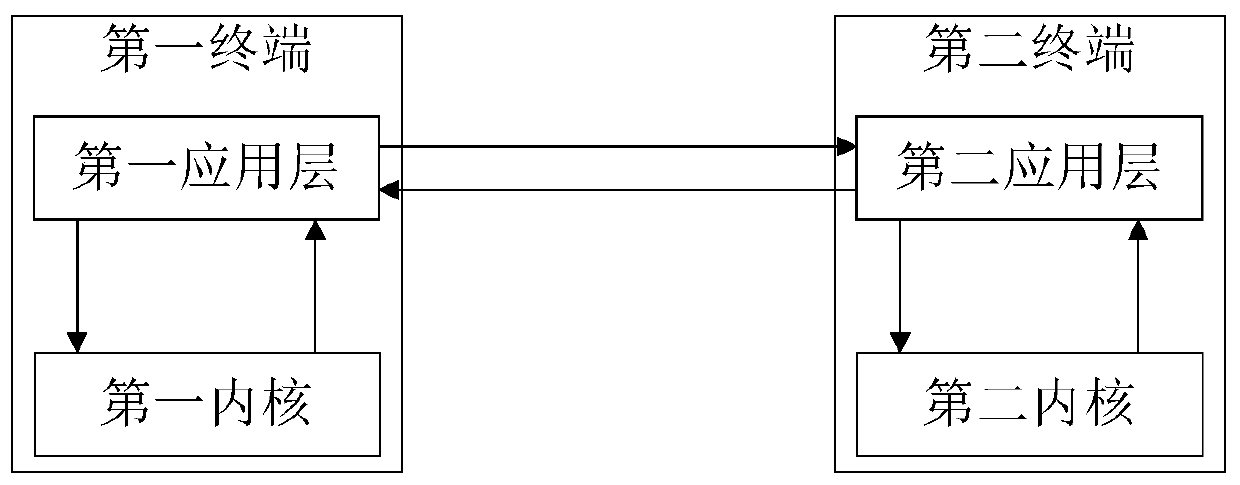
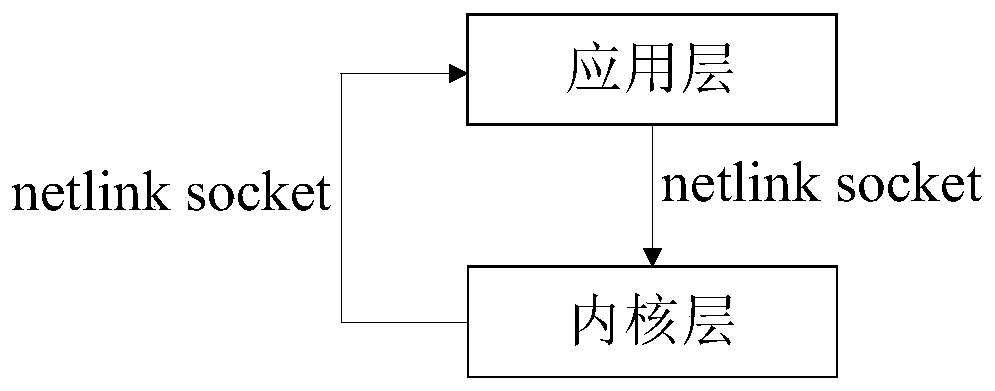
[0075] Such as figure 2 As shown, it is a quantum encryption method provided by the embodiment of the present invention. The quantum encryption method is applied in the process of quantum encryption transmission. The quantum encryption method includes: the first application layer of the first terminal obtains the first quantum from the key server The key information is sent to the first kernel, and the first quantum key information is configured to the first kernel through a preset encryption algorithm, and the first quantum key configuration information corresponding to the first kernel is updated; The key configuration information is returned to the first application layer and sent to the second application layer of the second terminal; the second application layer sends the corresponding first quantum key configuration information to the second kernel, and the corresponding The configuration information of the first quantum key is decrypted.
[0076] For ease of understan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com