A Trusted Computing Platform with Parallel Dual Architecture of Computing and Protection
A technology of trusted computing and architecture, applied in the field of trusted computing, can solve the problems of failure to prevent Wannacry ransomware virus attack, failure to realize computer dynamic measurement, and inability to play, so as to achieve the effect of active defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
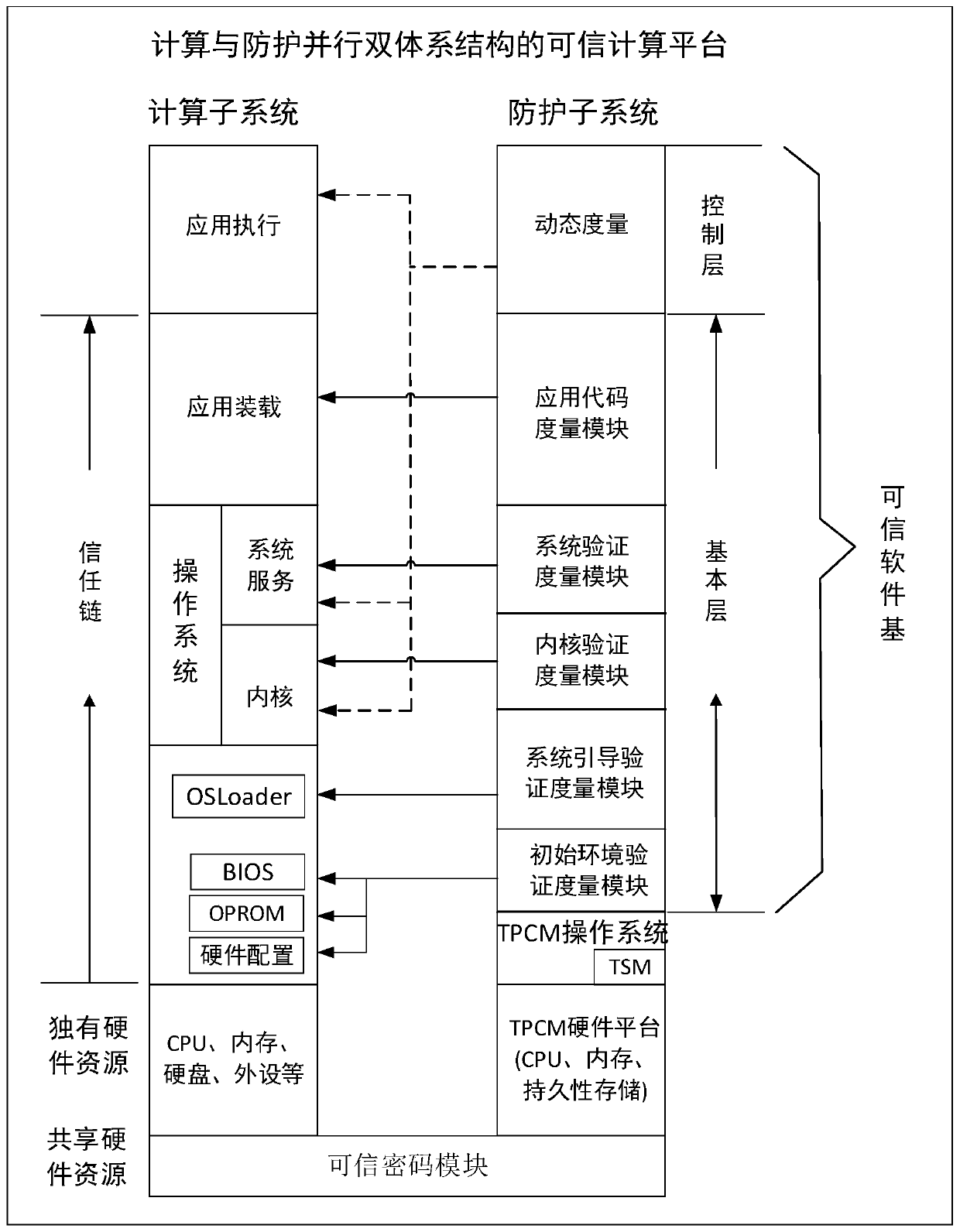
[0035] At present, the trusted computing chip TPM proposed by the international TCG organization is used as an external device of the computer. There are limitations in access and control, and its security capabilities are completely dependent on the security of the host system. It is difficult to defend against attacks by hackers who exploit the vulnerabilities of the host system, and it cannot substantially improve the active defense capabilities of the computer system.
[0036] The invention proposes a trusted computing platform with parallel dual architecture of computing and protection. The trusted computing platform includes parallel computing subsystems and protection subsystems. The protection subsystem and the computing subsystem are running in parallel, and their safety and reliability do not depend on the computing subsyste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com